Continuous Compliance in SAP Environments
|
|
|
- Noel Hensley
- 6 years ago
- Views:
Transcription
1 July 2014, HAPPIEST MINDS TECHNOLOGIES Continuous Compliance in SAP Environments Author Shirish Thadla SHARING. MINDFUL. INTEGRITY. LEARNING. EXCELLENCE. SOCIAL RESPONSIBILITY.
2 Copyright Information This document is exclusive property of Happiest Minds Technologies Pvt. Ltd. It is intended for limited circulation. 2
3 Contents Introduction... 4 Essential Data for Revalidation... 4 Roles Revalidation and Documentation for Analysis... 6 Outcome Appendix
4 Introduction Today, organizations are advancing at an exceptional rate. While this expansion creates significant opportunity, it also entails tremendous risk, which is unavoidable, but can be managed. With governance, risk, and compliance (GRC), businesses can strategically balance risk and opportunity. As global markets continue to impose new regulations, GRC help businesses: Better manage compliance and risk Better protect value proactively avoid risk events; reduce cost of violations The goal of the continuous compliance phase in the authorization field is mainly to ensure that all the users and roles are validated for the respective owners. This phase is not always simple to prepare because you are documenting the authorization concept so that business owners can scrutinize the authorization of their users. There are no tools that can accomplish these tasks as smoothly as SAP Business Objects governance, risk, and compliance solutions (SAP GRC). However, it s still essential to have a good authorization concept with few technical mistakes or oversights. Given below are some procedures which we recommend to achieve compliance when no GRC tools are deployed within the landscape. Essential Data for Revalidation Every day, user managers perform many actions on the user master record. To guarantee the appropriate compliance, the organization must periodically (at least once a year) perform a user revalidation. The goal of this activity is to keep the people involved in security processes (user data manager and business process owner) informed regarding the main users data. Due to organizational changes, it s possible that a user s authorizations don t match the current organization. If the business owner is kept informed, he could follow up on this misalignment. Every user responsible for a department has to confirm that the users assigned to him (and the corresponding authorizations) stand correct. When you have hundreds or thousands of users, it s difficult to dispatch a huge amount of data to the people responsible for analyzing this. The following procedures will help anyone to quickly set up user master records attributes and use a query to produce the user revalidation file. A user revalidation should be an easy process if every responsible user (manager) receives a list of assigned users (with related data) and has to confirm (or not) that the data are still correct. But the question is, which users data are relevant for user revalidation? 4
5 Defining Data for User Revalidation Here are some suggestions: User ID Last name First name Last logon date Company Function Department Cost center Assigned authorizations HR personnel number (CID) Users responsible for a specific business area Job Working with HR Some of these data should be generally available in the HR department. Unfortunately, the relationship between HR data and user master record data is not so easy. In some companies, the HR system is not an SAP solution. In many companies, the HR system is an SAP solution but is not in the same instance as the other business processes (and related SAP modules FI, CO, MM, and SD). You should involve the HR department to make a link between their data and the user master record. Manage User Master Record We suggest that you analyze all available fields in all tabs of Transaction SU01 to map all of the necessary data for user revalidation. The best solution is to create an interface (e.g., using HR triggers) that automatically aligns HR data with user master record data. Another good solution is to implement Identity Management. One of the biggest problems in user revalidation is related to authorizations. In many companies, a strong authorization concept based on roles is not well defined. Indeed, when there are many roles (not specifically manual profiles) assigned to users, it s crucial that they are somehow related to a job. In this case, composite roles are a good SAP standard solution. 5
6 Roles Revalidation and Documentation for Analysis To increase your authorization governance, it is recommended to periodically revalidate all roles and provide a clear documentation which the target audience can analyze. Many times, security administrators limit their attention to a role name and description without going into a deeper level of analysis. It is best practice to perform roles revalidation once in a year, with the goal to confirm that each role s content stands correct. Roles revalidation can be split into two different goals, which we look at in the following subsections. Technical Revalidation With this step, you certify that a role is correct from a technical point of view. This means that it s compliant with the authorization concept you ve adopted. This not only certifies the content but also certifies physically with Transaction PFCG (role maintenance). Business Revalidation When all roles are correct from the technical point of view, you have to document them to be validated. In an RBAC approach, the roles content will be used also in user management. In fact, the junction point between user processes and role processes is the role. When business area owners have to assign authorizations to their users, they are likely to use the roles documentation to find the best choice. The goal of the business revalidation is to certify that each role s content is correct against the implemented process and organization. Identify Misalignments between Organizational-Level Pop-Ups and Authorization Data in Derived Roles You can optimize your authorization role concept and governance by using derived roles. Derived roles can enhance your governance and simplify daily authorization maintenance. Without using derived roles, you have to manage several simple roles separately. By using derived roles, you can maintain parent roles and specify the data domain into all derived roles. However, you can create a gap in governance if you don t use this type of role properly. When a parent role is created and its transactions contain authorization objects with organizational-level fields, an organizational tab pop-up appears when you go into the Transaction PFCG Authorization tab. From a governance point of view, a manual change to an organizational-level field must be avoided to avoid overwriting the authorization value. 6
7 You can remediate this situation by easily finding these noncompliant situations through a targeted query. All values entered through the organizational panel are stored in Table AGR_1252. If an organizational field is manually changed, this value is stored in Table AGR_1251 instead of Table AGR_1252. To find these values, you can perform the query on Table AGR_1251. Identify Manually Added Authorizations in a Role s Authorization Tree You can find a role s authorizations that don t seem to be related to any transaction codes or that have been manually created. It s important that all authorizations present in a role s authorization tree are logically related to the transaction codes granted with the role itself. Otherwise, you risk losing control of your security concept. Each manual authorization added into the authorization tree is not linked to the transaction in the role menu. That means when you remove a transaction from the role menu, the manual authorization objects present in the authorization tree will not automatically be removed. Finding Non-standard or Manual Authorizations If you want to retrieve all manually inserted authorizations, you can do so through Transaction SE16 by browsing Table AGR_1251 (Authorization Data for the Activity Group). Ensuring Users are assigned only to the Roles and Transactions they Use You can determine whether a user has too many roles assigned to him by exporting statistical data to a spreadsheet. It s normal to find roles with hundreds (or even thousands) of transactions defined in a role s menu. If you ask your business users to tell you which transactions they need, they will probably ask for all available transactions. However, security guidelines indicate that each user should only be authorized for the minimum transactions he needs (the principle of least privilege). While Transaction ST03N (workload and performance statistics) is mainly used to verify an instance s performance, it s a fantastic resource for security managers as well. If you want to extract all Transaction ST03N data, you can use a specific function module. Using Transaction SE37 (ABAP function modules), you can execute a function called SWNC_GET_WORKLOAD_STATISTIC. Indirect Role Assignment to Simplify User Maintenance and Reporting You can use the HR organizational structure (HR-OM) to distribute authorizations to users. The classical approach to assigning a role to a user is direct assignment via Transactions SU01 (user maintenance) or PFCG (role maintenance). However, there s a more powerful scenario you can consider: indirect assignment of roles to users using an organizational structure as a bridge between users and roles. With this scenario, it will be much easier to share security documentation with business contacts who technically own the data and users but often have very limited technical knowledge. 7
8 One of the most difficult decisions a user manager has to make is how to delegate duties among business contacts. This is because they speak a different language security and authorization managers are often very technical, whereas business references are not necessarily SAP experts. For instance, when you make a pivot table from data stored in Table AGR_USERS to document the link between the roles and users, the result will be similar to the one shown in the figure below (with roles in the rows and users in the columns). Business contacts will find it very difficult to match this output with their organization. Instead of using a direct assignment (of roles to users), you can take advantage of the HR- OM component. You can assign the role (AG object) and users (US object) to the position (S object). Identify Business Owners By understanding each type of owner that s present in a business, you can easily determine which person manages what data or responsibility to ensure proper governance. Defining the owners of a company is not very clear, especially during periodical revalidations (users and roles). Often, an owner receives a document to be validated and he has difficulties because the goal and the responsibilities are not well defined. In security processes, many different areas are involved. For each area, one or more owners have to be identified. Divide the authorization processes for owners into (at least) two main areas: User processes Role processes 8
9 The typical situation where it s not clear how to proceed occurs when a user asks for a new transaction. The requested transaction could be added to a role not yet assigned to the user, or a new role (containing the transaction) could be assigned to the user. In recent years, the Segregation of Duties (SoD) logic has added a new level of complexity. When a new request causes an SoD conflict, a new set of owners are involved. Unfortunately, when the responsibilities aren t well addressed, the security team becomes responsible for all mistakes and misunderstandings. A proposal containing details of responsibilities held by different owners follow: Business area owner Responsible for the users in his area or department. Every user must be assigned to a responsible person who will manage each change of the user s data. Business process owner Responsible for defining the sequence of all activities that are mandatory in his processes. The decisions made by a business process owner should be valid across all company departments. For each business process, there is one process owner. Data owner Responsible for the most important information of the process: the data. Each data owner must assure that the data are correctly created and maintained. Every time a data is involved, data owners must validate the request. Role owner Responsible for the content (transactions and authorizations) of roles. He must communicate with data owners and process owners to guarantee the final integrity for each role s change. SoD rules owner Responsible for physically maintaining the set of rules necessary to perform risk analysis. SoD risk owner Responsible for defining a risk in terms of content and level of severity (critical, high, medium, low). SoD mitigation control owner Responsible for mitigation actions. Many other people can also be relevant to maintain a high level of governance such as internal controllers, business process analysts, and so on. All security and authorization 9
10 processes should be well designed and written with a clear indication of the owners involvement and responsibilities. When all owners have been identified, it s important to formally communicate this fact in the company to avoid misunderstanding. Outcome Though the above procedure is time consuming and requires manual effort, the organization can be assured of achieving: Minimizing Access Risk and Preventing Fraud Enabling a Secure, Global Supply Chain The above procedure can be automated by implementing/integrating the SAP GRC application within the landscape which not only reduce the efforts, cost but also brings in a continuous automated monitoring control framework. Appendix Most important User Tables Table Description How it helps USR01 Transaction SU01 DEFAULT Tab data Verifies the default data tab of users USR02 USR05 USR07 User login data, date of creation, last logon, user status Parameter ID and value for each user Last failed authorization check Finds users not assigned to any user group Provides the list of parameter IDs which can be restored in case of an accidental deletion Enables you to enquire on last failed authorization checks ADR6 addresses Extracts the mail address TPARA User master data Parameter ID tables Finds a Parameter ID 10
11 Most important Role Tables Table Description How it helps AGR_1016 AGR_1250 AGR_1251 AGR_1252 AGR_AGRS AGR_DEFINE AGR_FAVOS AGR_FLAGS AGR_NUM_2 AGR_TCODES AGR_TEXTS AGR_USERS List of all generated profiles linked to a role List of all authorization objects inserted into a role (without authorization value detail) List of all authorization objects inserted into a role (with authorization value detail) List of organizational values inserted into a role List of all simple roles in a composite role List of all roles defined in a system Personal Profile Generator roles favourites Role Attributes Last number of generated profile List of all transactions inserted into a role menu List of all descriptions of a role List of all users assigned to a role Provides the role's name by looking at the profile Provides all authorization objects inserted into a role without authorization object value detail Provides information on whether a critical authorization object is inactive in all roles except certain ones Provides the allowed organizational data domain where a role can work Provides how many simple roles are inserted in a composite role Provides a list of all roles defined in the system Lists the favourite roles for a user in transaction PFCG Contains several flag attributes, including whether a role is collective and what the role master language is Tells the last number of the generated profile Tells in which role menus Transaction MM03 is inserted Tells how many language descriptions a role has Tells how many users are assigned to a role 11
SEC302 Umoja Security GRC Analysis. Umoja Security GRC Analysis Version 8 1
 SEC302 Umoja Security GRC Analysis Umoja Security GRC Analysis Version 8 Last Copyright Modified: United 16-August-13 Nations 1 Agenda Course Introduction Module 1: User Access Risk Analysis Overview Module
SEC302 Umoja Security GRC Analysis Umoja Security GRC Analysis Version 8 Last Copyright Modified: United 16-August-13 Nations 1 Agenda Course Introduction Module 1: User Access Risk Analysis Overview Module
Configuration: Emergency Access Management for SAP Access Control 12.0
 CONFIGURATION GUIDE PUBLIC Document Version: 1.0.1 2018-08-31 Configuration: Emergency Access Management for SAP Access Control 12.0 2018 SAP SE or an SAP affiliate company. All rights reserved. THE BEST
CONFIGURATION GUIDE PUBLIC Document Version: 1.0.1 2018-08-31 Configuration: Emergency Access Management for SAP Access Control 12.0 2018 SAP SE or an SAP affiliate company. All rights reserved. THE BEST
Simplify and Secure: Managing User Identities Throughout their Lifecycles
 PRODUCT FAMILY BRIEF: CA SOLUTIONS FOR IDENTITY LIFECYCLE MANAGEMENT Simplify and Secure: Managing User Identities Throughout their Lifecycles CA Identity & Access Management (IAM) Identity Lifecycle Management
PRODUCT FAMILY BRIEF: CA SOLUTIONS FOR IDENTITY LIFECYCLE MANAGEMENT Simplify and Secure: Managing User Identities Throughout their Lifecycles CA Identity & Access Management (IAM) Identity Lifecycle Management
... Preface Acknowledgments SAP Governance, Risk, and Compliance Overview Planning SAP GRC Implementations...
 ... Preface... 19... Structure of This Book... 20... Target Audience... 20... How to Use This Book... 21... Conclusion... 21... Acknowledgments... 23 1... SAP Governance, Risk, and Compliance Overview...
... Preface... 19... Structure of This Book... 20... Target Audience... 20... How to Use This Book... 21... Conclusion... 21... Acknowledgments... 23 1... SAP Governance, Risk, and Compliance Overview...
SAP BusinessObjects Access Control 5.3 Support Pack 9. Functional Overview SAP BusinessObjects Access Control Solution Management September 30, 2009
 SAP BusinessObjects Access Control 5.3 Support Pack 9 Functional Overview SAP BusinessObjects Access Control Solution Management September 30, 2009 Disclaimer The information in this presentation/document
SAP BusinessObjects Access Control 5.3 Support Pack 9 Functional Overview SAP BusinessObjects Access Control Solution Management September 30, 2009 Disclaimer The information in this presentation/document
SAP GRC Risk Identification and Remediation
 September 26, 2007 English SAP GRC Risk Identification and Remediation Business Scenario Script for Discovery System version 3 SAP AG Neurottstr. 16 69190 Walldorf Germany Contents Introduction... 3 Statistical
September 26, 2007 English SAP GRC Risk Identification and Remediation Business Scenario Script for Discovery System version 3 SAP AG Neurottstr. 16 69190 Walldorf Germany Contents Introduction... 3 Statistical
SAP Segregation of Duties Internal Audit
 SAP Segregation of Duties Internal Audit February 2018 Bernalillo County Internal Audit SAP Segregation of Duties Executive Summary Summary of Procedures REDW performed internal audit procedures over the
SAP Segregation of Duties Internal Audit February 2018 Bernalillo County Internal Audit SAP Segregation of Duties Executive Summary Summary of Procedures REDW performed internal audit procedures over the
Segregation of Duties: Best Practices for Cybersecurity and More
 WHITE PAPER Segregation of Duties: Best Practices for Cybersecurity and More The news is filled with stories of alarming cybersecurity breaches, networks being hacked, and malware running amok. However,
WHITE PAPER Segregation of Duties: Best Practices for Cybersecurity and More The news is filled with stories of alarming cybersecurity breaches, networks being hacked, and malware running amok. However,
GOVERNANCE AES 2012 INFORMATION TECHNOLOGY GENERAL COMPUTING CONTROLS (ITGC) CATALOG. Aut. / Man. Control ID # Key SOX Control. Prev. / Det.
 GOVERNANCE 8.A.1 - Objective: Information Technology strategies, plans, personnel and budgets are consistent with AES' business and strategic requirements and goals. Objective Risk Statement(s): - IT Projects,
GOVERNANCE 8.A.1 - Objective: Information Technology strategies, plans, personnel and budgets are consistent with AES' business and strategic requirements and goals. Objective Risk Statement(s): - IT Projects,
Product Documentation SAP Business ByDesign February Business Configuration
 Product Documentation PUBLIC Business Configuration Table Of Contents 1 Business Configuration.... 4 2 Business Background... 5 2.1 Configuring Your SAP Solution... 5 2.2 Watermark... 7 2.3 Scoping...
Product Documentation PUBLIC Business Configuration Table Of Contents 1 Business Configuration.... 4 2 Business Background... 5 2.1 Configuring Your SAP Solution... 5 2.2 Watermark... 7 2.3 Scoping...
Making intelligent decisions about identities and their access
 Making intelligent decisions about identities and their access Provision users and mitigate risks with Identity Governance and Intelligence Highlights Provide a business-centric approach to risk-based
Making intelligent decisions about identities and their access Provision users and mitigate risks with Identity Governance and Intelligence Highlights Provide a business-centric approach to risk-based
Migration of DIR (Document Info Record) with Attachments - DMS
 Migration of DIR (Document Info Record) with Attachments - DMS Applies to: This document applies to Document Info Records in Document Management System module. For more information, visit the ABAP homepage.
Migration of DIR (Document Info Record) with Attachments - DMS Applies to: This document applies to Document Info Records in Document Management System module. For more information, visit the ABAP homepage.
Authorizations in SAP8 Software
 Volker Lehnert, Katharina Bonitz, and Larry Justice Authorizations in SAP8 Software Design and Configuration, ^ ^». Galileo Press. Bonn Boston Foreword 19 Acknowledgments 22 PART I Business Concepts 2.1
Volker Lehnert, Katharina Bonitz, and Larry Justice Authorizations in SAP8 Software Design and Configuration, ^ ^». Galileo Press. Bonn Boston Foreword 19 Acknowledgments 22 PART I Business Concepts 2.1
Secure Your ERP Environment with Automated Controls Naomi Iseri,Sr. GRC Solution Consultant
 Secure Your ERP Environment with Automated Controls Naomi Iseri,Sr. GRC Solution Consultant Agenda Introductions & Objectives Why Automate Controls What types of Automation Controls Do I Need When to Implement
Secure Your ERP Environment with Automated Controls Naomi Iseri,Sr. GRC Solution Consultant Agenda Introductions & Objectives Why Automate Controls What types of Automation Controls Do I Need When to Implement
GRC300. SAP BusinessObjects Access Control Implementation and Configuration COURSE OUTLINE. Course Version: 15 Course Duration: 5 Day(s)
 GRC300 SAP BusinessObjects Access Control 10.0 - Implementation and Configuration. COURSE OUTLINE Course Version: 15 Course Duration: 5 Day(s) SAP Copyrights and Trademarks 2017 SAP SE or an SAP affiliate
GRC300 SAP BusinessObjects Access Control 10.0 - Implementation and Configuration. COURSE OUTLINE Course Version: 15 Course Duration: 5 Day(s) SAP Copyrights and Trademarks 2017 SAP SE or an SAP affiliate
10/18/2018. London Governance, Risk, and Compliance
 10/18/2018 Governance, Risk, and Compliance Contents Contents... 4 Applications and integrations supporting GRC workflow... 6 GRC terminology... 7 Domain separation in... 9 Policy and Compliance Management...11
10/18/2018 Governance, Risk, and Compliance Contents Contents... 4 Applications and integrations supporting GRC workflow... 6 GRC terminology... 7 Domain separation in... 9 Policy and Compliance Management...11
Administrator Guide ANU Recruit HRMS Onboarding. Version: 7.1 Version Date: 05/09/2017 Author: Varghese Cherian
 Administrator Guide ANU Recruit HRMS Onboarding Version: 7.1 Version Date: 05/09/2017 Author: Varghese Cherian Contents 1. Background... 3 1.1 Key features of the ANU Recruit Onboarding process include:...
Administrator Guide ANU Recruit HRMS Onboarding Version: 7.1 Version Date: 05/09/2017 Author: Varghese Cherian Contents 1. Background... 3 1.1 Key features of the ANU Recruit Onboarding process include:...
WSIPC Guide to Time Off
 WSIPC Guide to Time Off Contents Contents i About This Guide 1 What You Should Know Before You Start 2 Be Sure You re Signed In 2 How to Use This Guide 2 Navigation Paths 2 Getting Around 2 Screen Shots
WSIPC Guide to Time Off Contents Contents i About This Guide 1 What You Should Know Before You Start 2 Be Sure You re Signed In 2 How to Use This Guide 2 Navigation Paths 2 Getting Around 2 Screen Shots
Browse the Book. Purchase Requisitions. Table of Contents. Index. The Authors
 First-hand knowledge. Browse the Book This chapter describes the process for creating a new document type for a purchase requisition and assigning a newly defined number range. Next, the chapter covers
First-hand knowledge. Browse the Book This chapter describes the process for creating a new document type for a purchase requisition and assigning a newly defined number range. Next, the chapter covers
Access Manager. Authorization management for SAP Systems. Release 2016
 Access Manager Release 2016 The Access Manger is a component of our software package SUIM-AIM and is SAP certified. Authorization management for SAP Systems The Big Picture The Access Manger (AM) is a
Access Manager Release 2016 The Access Manger is a component of our software package SUIM-AIM and is SAP certified. Authorization management for SAP Systems The Big Picture The Access Manger (AM) is a
Attribute Based Access Control for SAP
 WHITE PAPER Attribute Based Access Control for SAP INTRODUCTION Data security has become one of the most significant challenges in global businesses. Requirements are driven by a variety of sources including
WHITE PAPER Attribute Based Access Control for SAP INTRODUCTION Data security has become one of the most significant challenges in global businesses. Requirements are driven by a variety of sources including
Lloyds Bank Commercial Cards CCDM User Guide
 Lloyds Bank Commercial Cards CCDM User Guide Reporting for Administrators Version 1.1, 22082017 Please note that this document is for guidance only and as such not all screenshots will mirror your view
Lloyds Bank Commercial Cards CCDM User Guide Reporting for Administrators Version 1.1, 22082017 Please note that this document is for guidance only and as such not all screenshots will mirror your view
Securing Your Business in the Digital Age
 SAP Solution in Detail SAP GRC Solutions SAP Access Control Securing Your Business in the Digital Age 1 / 13 Table of Contents 3 Quick Facts 4 Governing Access Efficiently in a Hyperconnected World 7 Analyzing
SAP Solution in Detail SAP GRC Solutions SAP Access Control Securing Your Business in the Digital Age 1 / 13 Table of Contents 3 Quick Facts 4 Governing Access Efficiently in a Hyperconnected World 7 Analyzing
Personnel Master Data & Terminal
 Personnel Master Data & Terminal Explanation on beas Personnel Master Data & Terminal Boyum Solutions IT A/S Beas Tutorial TABLE OF CONTENTS 1. INTRODUCTION... 3 2. PROCESS... 3 2.1. Header from Master
Personnel Master Data & Terminal Explanation on beas Personnel Master Data & Terminal Boyum Solutions IT A/S Beas Tutorial TABLE OF CONTENTS 1. INTRODUCTION... 3 2. PROCESS... 3 2.1. Header from Master
Complete Guide to Learn Organizational Plan & Role Resolution in Workflow
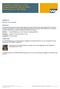 Complete Guide to Learn Organizational Plan & Role Resolution in Workflow Applies to: SAP ECC 6.0 and onwards. Summary Through this document the reader will be able to get a basic idea about the Organizational
Complete Guide to Learn Organizational Plan & Role Resolution in Workflow Applies to: SAP ECC 6.0 and onwards. Summary Through this document the reader will be able to get a basic idea about the Organizational
Business Portal for Microsoft Dynamics GP. Human Resources Management Self Service Suite Administrator s Guide Release 10.0
 Business Portal for Microsoft Dynamics GP Human Resources Management Self Service Suite Administrator s Guide Release 10.0 Copyright Copyright 2007 Microsoft Corporation. All rights reserved. Complying
Business Portal for Microsoft Dynamics GP Human Resources Management Self Service Suite Administrator s Guide Release 10.0 Copyright Copyright 2007 Microsoft Corporation. All rights reserved. Complying
NERC Internal Controls Evaluations
 NERC Internal Controls Evaluations Common Practices, Approaches, and Other Control Ideas April 11, 2017 Introductions Archer Energy Solutions acquires compliance division of Utility System Efficiencies
NERC Internal Controls Evaluations Common Practices, Approaches, and Other Control Ideas April 11, 2017 Introductions Archer Energy Solutions acquires compliance division of Utility System Efficiencies
Brainwave USER ACCESS REVIEW CERTIFICATION AND RECERTIFICATION IN A NUTSHELL
 Brainwave Identity Analytics USER ACCESS REVIEW CERTIFICATION AND RECERTIFICATION IN A NUTSHELL NEXT-GENERATION IDENTITY ANALYTICS REDUCES THE COST AND BURDEN OF THE USER ACCESS REVIEW PROCESS FOR ACCESS
Brainwave Identity Analytics USER ACCESS REVIEW CERTIFICATION AND RECERTIFICATION IN A NUTSHELL NEXT-GENERATION IDENTITY ANALYTICS REDUCES THE COST AND BURDEN OF THE USER ACCESS REVIEW PROCESS FOR ACCESS
Procedure for Transferring Documents from Financial Accounting to Controlling
 Procedure for Transferring Documents from Financial Accounting to Controlling Applies to: SAP R/3 4.6, ECC5.0 and ECC 6.0 For more information, visit the Enterprise Resource Planning homepage. Summary
Procedure for Transferring Documents from Financial Accounting to Controlling Applies to: SAP R/3 4.6, ECC5.0 and ECC 6.0 For more information, visit the Enterprise Resource Planning homepage. Summary
Sustainable Identity and Access Governance
 Business White Paper IDENTITY AND SECURITY Sustainable Identity and Access Governance Sustainable Identity and Access Governance Table of Contents: 2..... Enterprise Access Governance: Some Assembly Required
Business White Paper IDENTITY AND SECURITY Sustainable Identity and Access Governance Sustainable Identity and Access Governance Table of Contents: 2..... Enterprise Access Governance: Some Assembly Required
SAP GRC Global Trade Services 7.2 Preferred Practice US Automated Export Systems (AES)
 SAP GRC Global Trade Services 7.2 Preferred Practice US Automated Export Systems (AES) SAP GRC Updated September 2010 2 1. Table of Contents 1. Introduction...3 2. Prerequisites...4 3. Scenario Description...5
SAP GRC Global Trade Services 7.2 Preferred Practice US Automated Export Systems (AES) SAP GRC Updated September 2010 2 1. Table of Contents 1. Introduction...3 2. Prerequisites...4 3. Scenario Description...5
Effective Test Automation of SAP Implementations
 Effective Test Automation of SAP Implementations Vipin Kumar Managing Director & Software Engineering Evangelist Astra Infotech Pvt Ltd vk@astrainfotech.com QM15 2009 IBM Corporation Agenda Introduction
Effective Test Automation of SAP Implementations Vipin Kumar Managing Director & Software Engineering Evangelist Astra Infotech Pvt Ltd vk@astrainfotech.com QM15 2009 IBM Corporation Agenda Introduction
SAP Certified Application Professional Management Accounting (CO) with SAP ERP 6.0 EHP4 print view
 SAP EDUCATION PREP GUIDE: P_FINMGT_64 SAP Certified Application Professional Management Accounting (CO) with SAP ERP 6.0 EHP4 print view Disclaimer: These sample questions are for self-evaluation purposes
SAP EDUCATION PREP GUIDE: P_FINMGT_64 SAP Certified Application Professional Management Accounting (CO) with SAP ERP 6.0 EHP4 print view Disclaimer: These sample questions are for self-evaluation purposes
Integration of SAP EWM with SAP BusinessObjects Global Trade
 Integration of SAP EWM with SAP BusinessObjects Global Trade CUSTOMER Document Version: 2012_SP35 January 25, 2013 Integration of SAP EWM with SAP BusinessObjects Global Trade 2012_SP35 1 Copyright Copyright
Integration of SAP EWM with SAP BusinessObjects Global Trade CUSTOMER Document Version: 2012_SP35 January 25, 2013 Integration of SAP EWM with SAP BusinessObjects Global Trade 2012_SP35 1 Copyright Copyright
Audit Controls for Infor-Lawson Software Transactions, Security, Segregation of Duties
 1 Audit Controls for Infor-Lawson Software Transactions, Security, Segregation of Duties Agenda Audit Controls for Infor-Lawson Software 2 Agenda About Us Objectives Audit Requirements Solutions About
1 Audit Controls for Infor-Lawson Software Transactions, Security, Segregation of Duties Agenda Audit Controls for Infor-Lawson Software 2 Agenda About Us Objectives Audit Requirements Solutions About
Start your SAP Optimization Effort Yesterday: A 10-minute guide to the SAP Optimization process for an Enterprise
 Start your SAP Optimization Effort Yesterday: A 10-minute guide to the SAP Optimization process for an Enterprise EXECUTIVE SUMMARY If you just completed your annual LAW submission to SAP, you should immediately
Start your SAP Optimization Effort Yesterday: A 10-minute guide to the SAP Optimization process for an Enterprise EXECUTIVE SUMMARY If you just completed your annual LAW submission to SAP, you should immediately
INTELLIGENT IAM FOR DUMMIES. SecureAuth Special Edition
 INTELLIGENT IAM FOR DUMMIES SecureAuth Special Edition TABLE OF CONTENTS Introduction... 3 Introducing Intelligent Identity and Access Management (IIAM)... 4 What Can IIAM Do for You?... 7 Analyzing Account
INTELLIGENT IAM FOR DUMMIES SecureAuth Special Edition TABLE OF CONTENTS Introduction... 3 Introducing Intelligent Identity and Access Management (IIAM)... 4 What Can IIAM Do for You?... 7 Analyzing Account
Reading Sample. SAP Risk Management Implementation. Contents. Index. The Authors. First-hand knowledge.
 First-hand knowledge. Reading Sample This excerpt highlights how a properly implemented risk management solution can help you keep pace with risk. Learn how to automate and coordinate risk management activities
First-hand knowledge. Reading Sample This excerpt highlights how a properly implemented risk management solution can help you keep pace with risk. Learn how to automate and coordinate risk management activities
How to Perform Benefits Checks using Participation Monitor
 How to Perform Benefits Checks using Participation Monitor Applies to: SAP ECC 6.0 and above. Summary Participation monitor is use to manage the employees benefits in the HR scenario. It is used to ensure
How to Perform Benefits Checks using Participation Monitor Applies to: SAP ECC 6.0 and above. Summary Participation monitor is use to manage the employees benefits in the HR scenario. It is used to ensure
live date has finally come and all of your HR functionality is perfect!
 Page 1 February 2003 Volume I Issue 1 www..com Editor s Note: It s not a heck of a lot of fun to do costly custom programming in the HR module, especially when you know you re going to lose all that work
Page 1 February 2003 Volume I Issue 1 www..com Editor s Note: It s not a heck of a lot of fun to do costly custom programming in the HR module, especially when you know you re going to lose all that work
EASY HELP DESK REFERENCE GUIDE
 EASY HELP DESK REFERENCE GUIDE Last Updated: May 18, 2017 Contents Chapter 1: Introduction and Solution Overview... 3 Learning Objectives... 4 Navigation and Tool Bars... 4 Accessing Easy Help Desk in
EASY HELP DESK REFERENCE GUIDE Last Updated: May 18, 2017 Contents Chapter 1: Introduction and Solution Overview... 3 Learning Objectives... 4 Navigation and Tool Bars... 4 Accessing Easy Help Desk in
Be Remarkable. CONTRACT LIFECYCLE MANAGEMENT SOFTWARE. Software Overview OVERVIEW. Additional Available Professional Services
 Be Remarkable. CONTRACT LIFECYCLE MANAGEMENT SOFTWARE Software Overview Greatly improves management of contracts and business agreements across your entire enterprise, maximizing the value of each and
Be Remarkable. CONTRACT LIFECYCLE MANAGEMENT SOFTWARE Software Overview Greatly improves management of contracts and business agreements across your entire enterprise, maximizing the value of each and
Getting Started. Enter your Username and Password and click Logon.
 Introduction The object of this manual is to provide you with the necessary Client Segmentation module navigational support in order to give you the ability to apply/update; Servicing Arrangements, Marketing
Introduction The object of this manual is to provide you with the necessary Client Segmentation module navigational support in order to give you the ability to apply/update; Servicing Arrangements, Marketing
Copyright Basware Corporation. All rights reserved.. Permissions Guide Basware P2P 18.1
 Copyright 1999-2017 Basware Corporation. All rights reserved.. Permissions Guide Basware P2P 18.1 1 General Permissions 1.1 General Access System (0) This permission gives a user/group access to the system.
Copyright 1999-2017 Basware Corporation. All rights reserved.. Permissions Guide Basware P2P 18.1 1 General Permissions 1.1 General Access System (0) This permission gives a user/group access to the system.
HRIS Import Guide. Instructions on how to use Trakstar s HRIS Import Tool.
 HRIS Import Guide Instructions on how to use Trakstar s HRIS Import Tool. Introduction Trakstar s HRIS Import feature allows administrators to import Trakstar data with a spreadsheet exported from another
HRIS Import Guide Instructions on how to use Trakstar s HRIS Import Tool. Introduction Trakstar s HRIS Import feature allows administrators to import Trakstar data with a spreadsheet exported from another
Oracle GRC Controls Suite Fundamentals Ver. 8.5/7.3.1/5.5.1
 Oracle University Contact Us: 0800 891 6502 Oracle GRC Controls Suite Fundamentals Ver. 8.5/7.3.1/5.5.1 Duration: 4 Days What you will learn This course describes the four governors that comprise the GRC
Oracle University Contact Us: 0800 891 6502 Oracle GRC Controls Suite Fundamentals Ver. 8.5/7.3.1/5.5.1 Duration: 4 Days What you will learn This course describes the four governors that comprise the GRC
SAP PAPA Shop User Guide
 Norfolk Southern Corporation 1/15/2015 Background PAPA (Position Attribute Privilege Assignment) Shop is a web-based entitlement management system designed to facilitate the maintenance and monitoring
Norfolk Southern Corporation 1/15/2015 Background PAPA (Position Attribute Privilege Assignment) Shop is a web-based entitlement management system designed to facilitate the maintenance and monitoring
Maintain Organizational Structure
 Maintain Organizational Structure Contents Introduction... 2 1.1 Preliminary Setting... 2 1.1.1 Create User Settings for Organization Management... 2 1.1 Relations Organizational Units, Positions, Jobs...
Maintain Organizational Structure Contents Introduction... 2 1.1 Preliminary Setting... 2 1.1.1 Create User Settings for Organization Management... 2 1.1 Relations Organizational Units, Positions, Jobs...
Intercompany Purchasing
 Configuration Guide SAP Business One 9.0 integration for SAP NetWeaver Document Version: 1.0 2013-03-22 All Countries Typographic Conventions Type Style Example Example EXAMPLE Example Example
Configuration Guide SAP Business One 9.0 integration for SAP NetWeaver Document Version: 1.0 2013-03-22 All Countries Typographic Conventions Type Style Example Example EXAMPLE Example Example
Oracle Risk Management Cloud. Release 13 (updates 18A 18C) What s New
 Oracle Risk Management Cloud Release 13 (updates 18A 18C) What s New TABLE OF CONTENTS DOCUMENT HISTORY 4 UPDATE 18C 4 Revision History 4 Overview 4 Feature Summary 5 Risk Management 8 Common 8 Monitor
Oracle Risk Management Cloud Release 13 (updates 18A 18C) What s New TABLE OF CONTENTS DOCUMENT HISTORY 4 UPDATE 18C 4 Revision History 4 Overview 4 Feature Summary 5 Risk Management 8 Common 8 Monitor
SAP Certified Application Professional Management Accounting (CO) with SAP ERP 6.0 EHP5
 SAP EDUCATION SAMPLE QUESTIONS: P_FINMGT_65 Disclaimer: These sample questions are for self-evaluation purposes only and do not appear on the actual certification exams. Answering the sample questions
SAP EDUCATION SAMPLE QUESTIONS: P_FINMGT_65 Disclaimer: These sample questions are for self-evaluation purposes only and do not appear on the actual certification exams. Answering the sample questions
Establishing RFC Connection between Data Stage SAP BW
 Establishing RFC Connection between Data Stage SAP BW Applies to: SAP BW 3.5 and Higher. Summary This Article gives you a brief idea on how to create RFC Connection between Data stage and SAP BI. For more
Establishing RFC Connection between Data Stage SAP BW Applies to: SAP BW 3.5 and Higher. Summary This Article gives you a brief idea on how to create RFC Connection between Data stage and SAP BI. For more
Fastpath. Innovation in User Experience for Automated Controls SOLUTIONPERSPECTIVE EXPERIENCE. November 2017
 November 2017 Fastpath Innovation in User Experience for Automated Controls EXPERIENCE 2017 SOLUTIONPERSPECTIVE Governance, Risk Management & Compliance Insight 2017 GRC 20/20 Research, LLC. All Rights
November 2017 Fastpath Innovation in User Experience for Automated Controls EXPERIENCE 2017 SOLUTIONPERSPECTIVE Governance, Risk Management & Compliance Insight 2017 GRC 20/20 Research, LLC. All Rights
Chapter Contents. Manage Employers Option Screen
 16: Manage Employers Chapter Contents Create an Employer Account (Registration)... 16-2 Add Employer Locations... 16-6 Assign a Case Manager... 16-8 Add Contacts... 16-9 Assist an Employer... 16-13 Search
16: Manage Employers Chapter Contents Create an Employer Account (Registration)... 16-2 Add Employer Locations... 16-6 Assign a Case Manager... 16-8 Add Contacts... 16-9 Assist an Employer... 16-13 Search
After working through that presentation, you will be prepared to use Xcelsius dashboards accessing BI query data via SAP NetWeaver BW connection in
 After working through that presentation, you will be prepared to use Xcelsius dashboards accessing BI query data via SAP NetWeaver BW connection in your company. 1 Topics Learn how to build Xcelsius dashboards
After working through that presentation, you will be prepared to use Xcelsius dashboards accessing BI query data via SAP NetWeaver BW connection in your company. 1 Topics Learn how to build Xcelsius dashboards
BUSINESS CASE FOR VTIGER CRM
 http://www.its4you.sk/en/ email: info@its4you.sk phone: +421-51-7732370 BUSINESS CASE FOR VTIGER CRM Introduction The Business Case module developed by IT-Solutions 4You is new module for vtiger CRM. The
http://www.its4you.sk/en/ email: info@its4you.sk phone: +421-51-7732370 BUSINESS CASE FOR VTIGER CRM Introduction The Business Case module developed by IT-Solutions 4You is new module for vtiger CRM. The
Software changes and error corrections - TimePlan
 Do you use the module Holiday rules management and are you affected by the error corrections TP-22668, TP-22633, TP-22513, TP-22484, TP-22473, TP-22369 and TP-19412 batch run on all holiday rules is necessary
Do you use the module Holiday rules management and are you affected by the error corrections TP-22668, TP-22633, TP-22513, TP-22484, TP-22473, TP-22369 and TP-19412 batch run on all holiday rules is necessary
Proactively Managing ERP Risks. January 7, 2010
 Proactively Managing ERP Risks January 7, 2010 0 Introductions and Objectives Establish a structured model to demonstrate the variety of risks associated with an ERP environment Discuss control areas that
Proactively Managing ERP Risks January 7, 2010 0 Introductions and Objectives Establish a structured model to demonstrate the variety of risks associated with an ERP environment Discuss control areas that
Preparing a Reevaluation Using the Documented Reevaluation Checklist (DRC)
 Guidance Preparing a Reevaluation Using the Documented This guidance outlines the TxDOT process for preparing a documented reevaluation as required by 43 TAC 2.85 and 23 CFR 771.129. TxDOT Environmental
Guidance Preparing a Reevaluation Using the Documented This guidance outlines the TxDOT process for preparing a documented reevaluation as required by 43 TAC 2.85 and 23 CFR 771.129. TxDOT Environmental
Oracle Talent Management Cloud. What s New in Release 9
 Oracle Talent Management Cloud What s New in Release 9 30 April 2015 TABLE OF CONTENTS REVISION HISTORY... 4 OVERVIEW... 5 Give Us Feedback... 5 RELEASE FEATURE SUMMARY... 6 HCM COMMON FEATURES... 8 HCM
Oracle Talent Management Cloud What s New in Release 9 30 April 2015 TABLE OF CONTENTS REVISION HISTORY... 4 OVERVIEW... 5 Give Us Feedback... 5 RELEASE FEATURE SUMMARY... 6 HCM COMMON FEATURES... 8 HCM
Payroll Basics for ADP Workforce Now
 Payroll Basics for ADP Workforce Now Activity Workbook Automatic Data Processing, Inc. ES Canada PAYROLL LEVEL 1 FOR WORKFORCE NOW ADP s Trademarks The ADP Logo and ADP Workforce Now are registered trademarks
Payroll Basics for ADP Workforce Now Activity Workbook Automatic Data Processing, Inc. ES Canada PAYROLL LEVEL 1 FOR WORKFORCE NOW ADP s Trademarks The ADP Logo and ADP Workforce Now are registered trademarks
Oracle Fusion Human Capital Management
 Oracle Fusion Human Capital Management STRATEGIC GLOBAL HUMAN CAPITAL MANAGEMENT KEY FEATURES Support for multiple work relationships that employees or contingent workers may have with multiple legal employers,
Oracle Fusion Human Capital Management STRATEGIC GLOBAL HUMAN CAPITAL MANAGEMENT KEY FEATURES Support for multiple work relationships that employees or contingent workers may have with multiple legal employers,
Administration. Welcome to the Eastwood Harris Pty Ltd MICROSOFT PROJECT AND PMBOK GUIDE FOURTH EDITION training course presented by.
 Welcome to the Eastwood Harris Pty Ltd MICROSOFT PROJECT AND PMBOK GUIDE FOURTH EDITION training course presented by Paul E Harris Administration Evacuation Timings, meals and facilities Mobile phones
Welcome to the Eastwood Harris Pty Ltd MICROSOFT PROJECT AND PMBOK GUIDE FOURTH EDITION training course presented by Paul E Harris Administration Evacuation Timings, meals and facilities Mobile phones
GRC300. SAP Access Control Implementation and Configuration COURSE OUTLINE. Course Version: 16 Course Duration: 5 Day(s)
 GRC300 SAP Access Control Implementation and Configuration. COURSE OUTLINE Course Version: 16 Course Duration: 5 Day(s) SAP Copyrights and Trademarks 2016 SAP SE or an SAP affiliate company. All rights
GRC300 SAP Access Control Implementation and Configuration. COURSE OUTLINE Course Version: 16 Course Duration: 5 Day(s) SAP Copyrights and Trademarks 2016 SAP SE or an SAP affiliate company. All rights
Identifying Proactive Process Solutions for Key Payroll and Time Management Controls. Bhavesh Bhagat, EnCrisp
 Identifying Proactive Process Solutions for Key Payroll and Time Management Controls Bhavesh Bhagat, EnCrisp What We ll Cover Need to monitor Payroll & Time proactively Control Basic Concepts SAP Payroll
Identifying Proactive Process Solutions for Key Payroll and Time Management Controls Bhavesh Bhagat, EnCrisp What We ll Cover Need to monitor Payroll & Time proactively Control Basic Concepts SAP Payroll
Focused Insights for SAP Solution Manager 7.2
 Security Guide Focused Insights for SAP Solution Manager Document Version: 1.5 2018-02-15 ST-OST 200 SP 1 Typographic Conventions Type Style Example Description Words or characters quoted from the screen.
Security Guide Focused Insights for SAP Solution Manager Document Version: 1.5 2018-02-15 ST-OST 200 SP 1 Typographic Conventions Type Style Example Description Words or characters quoted from the screen.
SAP Road Map for Governance, Risk, and Compliance Solutions
 SAP Road Map for Governance, Risk, and Compliance Solutions Q4 2016 Customer Disclaimer The information in this presentation is confidential and proprietary to SAP and may not be disclosed without the
SAP Road Map for Governance, Risk, and Compliance Solutions Q4 2016 Customer Disclaimer The information in this presentation is confidential and proprietary to SAP and may not be disclosed without the
Management of Global Employees
 Applies to: 4.7 and Ecc 6. For more information, visit the Enterprise Resource Planning homepage. Summary SAP R/3 Enterprise introduces a comprehensive solution for the management of global employees.
Applies to: 4.7 and Ecc 6. For more information, visit the Enterprise Resource Planning homepage. Summary SAP R/3 Enterprise introduces a comprehensive solution for the management of global employees.
TABLE OF CONTENTS DOCUMENT HISTORY
 TABLE OF CONTENTS DOCUMENT HISTORY 4 UPDATE 17D 4 Revision History 4 Overview 4 Optional Uptake of New Features (Opt In) 5 Update Tasks 5 Feature Summary 6 Manufacturing 7 Display Issued Quantities by
TABLE OF CONTENTS DOCUMENT HISTORY 4 UPDATE 17D 4 Revision History 4 Overview 4 Optional Uptake of New Features (Opt In) 5 Update Tasks 5 Feature Summary 6 Manufacturing 7 Display Issued Quantities by
Enter PSD Codes Manually
 CYMA Version 16 added the capability to formally support Act32 Local Income Tax reporting in CYMA. This includes both the ability to properly report Local Income Taxes in Box 18 of the W2 and to record
CYMA Version 16 added the capability to formally support Act32 Local Income Tax reporting in CYMA. This includes both the ability to properly report Local Income Taxes in Box 18 of the W2 and to record
10/16/2018. Kingston Governance, Risk, and Compliance
 10/16/2018 Kingston Governance, Risk, and Compliance Contents Contents... 4 Domain separation in... 8 Policy and Compliance Management...9 Understanding Policy and Compliance Management... 10 Risk Management...87
10/16/2018 Kingston Governance, Risk, and Compliance Contents Contents... 4 Domain separation in... 8 Policy and Compliance Management...9 Understanding Policy and Compliance Management... 10 Risk Management...87
TV3146 Umoja Create Shipment Request. Umoja Create Shipment Request Version 3 1
 TV3146 Umoja Create Shipment Request Umoja Create Shipment Request Version 3 Copyright Last Modified: United 28-April-15 Nations 1 Agenda Course Introduction Module 1: Umoja Shipment Overview Module 2:
TV3146 Umoja Create Shipment Request Umoja Create Shipment Request Version 3 Copyright Last Modified: United 28-April-15 Nations 1 Agenda Course Introduction Module 1: Umoja Shipment Overview Module 2:
Audit Trends & Framework for Improved Financial Reporting. Data Quality, Integrity, and Reliability
 Audit Trends & Framework for Improved Financial Reporting Data Quality, Integrity, and Reliability Agenda Audit Readiness vs. Audit The Complexity of the DoD Environment The Role of Analytics Factors Contributing
Audit Trends & Framework for Improved Financial Reporting Data Quality, Integrity, and Reliability Agenda Audit Readiness vs. Audit The Complexity of the DoD Environment The Role of Analytics Factors Contributing
Utilizing the Employee Training Module and ESS Munis: Human Resources
 [MU-HR-7-A] [MU-HR-14-A] Utilizing the Employee Training Module and ESS Munis: Human Resources CLASS DESCRIPTION This session will be an exploration of how Employee Self Service can be used in conjunction
[MU-HR-7-A] [MU-HR-14-A] Utilizing the Employee Training Module and ESS Munis: Human Resources CLASS DESCRIPTION This session will be an exploration of how Employee Self Service can be used in conjunction
Question 2: Requirements Engineering. Part a. Answer: Requirements Engineering Process
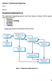 Question 2: Requirements Engineering Part a. Answer: Requirements Engineering Process The requirements engineering process varies from domain to domain. But the general activities involved are: Elicitation
Question 2: Requirements Engineering Part a. Answer: Requirements Engineering Process The requirements engineering process varies from domain to domain. But the general activities involved are: Elicitation
User guide. SAP umantis EM Interface. Campus Solution 728. SAP umantis EM Interface (V2.7.0)
 Campus Solution 728 SAP umantis EM Interface (V2.7.0) User guide SAP umantis EM Interface Solution SAP umantis EM Interface Date Monday, March 20, 2017 1:47:22 PM Version 2.7.0 SAP Release from ECC 6.0
Campus Solution 728 SAP umantis EM Interface (V2.7.0) User guide SAP umantis EM Interface Solution SAP umantis EM Interface Date Monday, March 20, 2017 1:47:22 PM Version 2.7.0 SAP Release from ECC 6.0
Product Documentation SAP Business ByDesign August Compliance Management
 Product Documentation PUBLIC Compliance Management Table Of Contents 1 Compliance.... 4 2 Tax Determination for MOSS.... 6 3 Audit Quick Guide.... 8 4 IT Compliance Quick Guide.... 11 5 Central Bank Reporting...
Product Documentation PUBLIC Compliance Management Table Of Contents 1 Compliance.... 4 2 Tax Determination for MOSS.... 6 3 Audit Quick Guide.... 8 4 IT Compliance Quick Guide.... 11 5 Central Bank Reporting...
The Research Foundation for The State University of New York Campus Security Administrator Handbook
 The Research Foundation for The State University of New York Campus Security Administrator Handbook Table of Contents Introduction... 3 Campus Security Administrator... 3 Responsibilities... 3 How to Appoint...
The Research Foundation for The State University of New York Campus Security Administrator Handbook Table of Contents Introduction... 3 Campus Security Administrator... 3 Responsibilities... 3 How to Appoint...
PNMsoft SCE July 2016 Product Version 7.5 and above
 PNMsoft Knowledge Base Sequence User Guides PNMsoft SCE July 2016 Product Version 7.5 and above 2016 PNMsoft All Rights Reserved This document, including any supporting materials, is owned by PNMsoft Ltd
PNMsoft Knowledge Base Sequence User Guides PNMsoft SCE July 2016 Product Version 7.5 and above 2016 PNMsoft All Rights Reserved This document, including any supporting materials, is owned by PNMsoft Ltd
HUD-US DEPT OF HOUSING & URBAN DEVELOPMENT: Understanding Internal Controls. Ladies and gentlemen, thank you for standing by and welcome to the
 Final Transcript HUD-US DEPT OF HOUSING & URBAN DEVELOPMENT: Understanding Internal Controls SPEAKERS Petergay Bryan PRESENTATION Moderator Ladies and gentlemen, thank you for standing by and welcome to
Final Transcript HUD-US DEPT OF HOUSING & URBAN DEVELOPMENT: Understanding Internal Controls SPEAKERS Petergay Bryan PRESENTATION Moderator Ladies and gentlemen, thank you for standing by and welcome to
Certified Identity Governance Expert (CIGE) Overview & Curriculum
 Overview Identity and Access Governance (IAG) provides the link between Identity and Access Management (IAM) rules and the policies within a company to protect systems and data from unauthorized access,
Overview Identity and Access Governance (IAG) provides the link between Identity and Access Management (IAM) rules and the policies within a company to protect systems and data from unauthorized access,
Welcome to the course on the working process across branch companies.
 Welcome to the course on the working process across branch companies. In this course we will review the major work processes across branch companies. We will start with the intercompany trade process.
Welcome to the course on the working process across branch companies. In this course we will review the major work processes across branch companies. We will start with the intercompany trade process.
For Publishers implementing and using the National Product Catalogue in Australia & New Zealand. Load & Maintain your National Product Catalogue
 User Guide Cookbook For Publishers implementing and using the National Product Catalogue in Australia & New Zealand December 2016 Load & Maintain your National Product Catalogue Licenses and Trademarks
User Guide Cookbook For Publishers implementing and using the National Product Catalogue in Australia & New Zealand December 2016 Load & Maintain your National Product Catalogue Licenses and Trademarks
Administrator Guide ANU Recruit HRMS Onboarding. Version: 7 Version Date: 03/01/2017 Author: Varghese Cherian
 Administrator Guide ANU Recruit HRMS Onboarding Version: 7 Version Date: 03/01/2017 Author: Varghese Cherian Table of Contents 1 Background... 3 1.1 Key features of the ANU Recruit Onboarding process include:...
Administrator Guide ANU Recruit HRMS Onboarding Version: 7 Version Date: 03/01/2017 Author: Varghese Cherian Table of Contents 1 Background... 3 1.1 Key features of the ANU Recruit Onboarding process include:...
OAUG / DOAG SIG DAY Vienna Sept 27 th 2010 Oracle Governance Risk and Compliance OAUG. August 2010
 OAUG / DOAG SIG DAY Vienna Sept 27 th 2010 Oracle Governance Risk and Compliance OAUG Automated Controls and Compliance in Oracle E-Business Suite August 2010 Focus Show some hands-on examples of how technical
OAUG / DOAG SIG DAY Vienna Sept 27 th 2010 Oracle Governance Risk and Compliance OAUG Automated Controls and Compliance in Oracle E-Business Suite August 2010 Focus Show some hands-on examples of how technical
Access to the system is browser-based. CCCWorks supports the Microsoft Internet Explorer, Mozilla Firefox, and Apple Safari web browsers.
 Introduction Welcome to the CCCWorks Time and Attendance Manager Reference Guide CCCWorks Time and Attendance application delivers the functionality and flexibility to enforce HR, payroll, and union policies
Introduction Welcome to the CCCWorks Time and Attendance Manager Reference Guide CCCWorks Time and Attendance application delivers the functionality and flexibility to enforce HR, payroll, and union policies
FI Enhancement Technique How-To-Guide on the Usage of Business Transaction Events (BTE)
 SDN Contribution FI Enhancement Technique How-To-Guide on the Usage of Business Transaction Events (BTE) Applies to: SAP 4.6C and Above Summary: This article provides a step-by-step guide on the usage
SDN Contribution FI Enhancement Technique How-To-Guide on the Usage of Business Transaction Events (BTE) Applies to: SAP 4.6C and Above Summary: This article provides a step-by-step guide on the usage
CHAPTER 5 INFORMATION TECHNOLOGY SERVICES CONTROLS
 5-1 CHAPTER 5 INFORMATION TECHNOLOGY SERVICES CONTROLS INTRODUCTION In accordance with Statements on Auditing Standards Numbers 78 and 94, issued by the American Institute of Certified Public Accountants
5-1 CHAPTER 5 INFORMATION TECHNOLOGY SERVICES CONTROLS INTRODUCTION In accordance with Statements on Auditing Standards Numbers 78 and 94, issued by the American Institute of Certified Public Accountants
TABLE OF CONTENTS DOCUMENT HISTORY
 TABLE OF CONTENTS DOCUMENT HISTORY 4 UPDATE 17D 4 Revision History 4 Overview 4 Optional Uptake of New Features (Opt In) 5 Update Tasks 5 Feature Summary 6 Installed Base 7 Track Quantity Changes of Nonserialized
TABLE OF CONTENTS DOCUMENT HISTORY 4 UPDATE 17D 4 Revision History 4 Overview 4 Optional Uptake of New Features (Opt In) 5 Update Tasks 5 Feature Summary 6 Installed Base 7 Track Quantity Changes of Nonserialized
Sage 300 ERP Sage 300 ERP Intelligence Release Notes
 Sage 300 ERP Intelligence Release Notes The software described in this document is protected by copyright, and may not be copied on any medium except as specifically authorized in the license or non disclosure
Sage 300 ERP Intelligence Release Notes The software described in this document is protected by copyright, and may not be copied on any medium except as specifically authorized in the license or non disclosure
Table of Contents. Genoa User Guide. Administration Bridge User Guide Administration
 Table of Contents 0 Genoa User Guide Administration 4.2.4 4.2.4 Bridge User Guide Administration Table of Contents 0 Table of Contents TABLE OF CONTENTS... ADMINISTRATION... 1 Licensee Company & Employees...
Table of Contents 0 Genoa User Guide Administration 4.2.4 4.2.4 Bridge User Guide Administration Table of Contents 0 Table of Contents TABLE OF CONTENTS... ADMINISTRATION... 1 Licensee Company & Employees...
SAP Business One Financial Consolidation
 Configuration Guide SAP Business One 9.0 integration for SAP NetWeaver Document Version: 1.1 2017-03-29 All Countries Typographic Conventions Type Style Example Example EXAMPLE Example Example
Configuration Guide SAP Business One 9.0 integration for SAP NetWeaver Document Version: 1.1 2017-03-29 All Countries Typographic Conventions Type Style Example Example EXAMPLE Example Example
SOLUTION BRIEF RSA IDENTITY GOVERNANCE & LIFECYCLE SOLUTION OVERVIEW ACT WITH INSIGHT TO DRIVE INFORMED DECISIONS TO MITIGATE IDENTITY RISK
 RSA IDENTITY GOVERNANCE & LIFECYCLE SOLUTION OVERVIEW ACT WITH INSIGHT TO DRIVE INFORMED DECISIONS TO MITIGATE IDENTITY RISK BENEFITS ACT WITH INSIGHTS Identity has emerged as today s most consequential
RSA IDENTITY GOVERNANCE & LIFECYCLE SOLUTION OVERVIEW ACT WITH INSIGHT TO DRIVE INFORMED DECISIONS TO MITIGATE IDENTITY RISK BENEFITS ACT WITH INSIGHTS Identity has emerged as today s most consequential
Microsoft Dynamics GP. Purchase Order Processing
 Microsoft Dynamics GP Purchase Order Processing Copyright Copyright 2007 Microsoft Corporation. All rights reserved. Complying with all applicable copyright laws is the responsibility of the user. Without
Microsoft Dynamics GP Purchase Order Processing Copyright Copyright 2007 Microsoft Corporation. All rights reserved. Complying with all applicable copyright laws is the responsibility of the user. Without
AiM User Guide Work Management Module
 AiM User Guide 2010 AssetWorks Inc. 1777 NE Loop 410, Suite 1250 San Antonio, Texas 78217 (800) 268-0325 Table of Contents AiM User Guide INTRODUCTION... 6 CHAPTER 1: WORK ORDER SCREEN... 7 CHAPTER 1 PART
AiM User Guide 2010 AssetWorks Inc. 1777 NE Loop 410, Suite 1250 San Antonio, Texas 78217 (800) 268-0325 Table of Contents AiM User Guide INTRODUCTION... 6 CHAPTER 1: WORK ORDER SCREEN... 7 CHAPTER 1 PART
5 key steps to defining your application-access control
 5 key steps to defining your application-access control An Evidian white paper Evidian Professional Services Summary Version 1.0 How to control access to your applications? From RBAC to Extended RBAC Top-Down
5 key steps to defining your application-access control An Evidian white paper Evidian Professional Services Summary Version 1.0 How to control access to your applications? From RBAC to Extended RBAC Top-Down
TABLE OF CONTENTS DOCUMENT HISTORY
 TABLE OF CONTENTS DOCUMENT HISTORY 5 UPDATE 17D 5 Revision History 5 Overview 5 Optional Uptake of New Features (Opt In) 6 Update Tasks 6 Feature Summary 7 Demand Management 9 Forecast Unique Demand Segments
TABLE OF CONTENTS DOCUMENT HISTORY 5 UPDATE 17D 5 Revision History 5 Overview 5 Optional Uptake of New Features (Opt In) 6 Update Tasks 6 Feature Summary 7 Demand Management 9 Forecast Unique Demand Segments
International Standards for the Professional Practice of Internal Auditing (Standards)
 INTERNATIONAL STANDARDS FOR THE PROFESSIONAL PRACTICE OF INTERNAL AUDITING (STANDARDS) Attribute Standards 1000 Purpose, Authority, and Responsibility The purpose, authority, and responsibility of the
INTERNATIONAL STANDARDS FOR THE PROFESSIONAL PRACTICE OF INTERNAL AUDITING (STANDARDS) Attribute Standards 1000 Purpose, Authority, and Responsibility The purpose, authority, and responsibility of the
Mastering new and expanding financial services regulations and audits
 IBM Software White Paper December 2010 Mastering new and expanding financial services regulations and audits 2 Mastering new and expanding financial services regulations and audits Contents 2 Executive
IBM Software White Paper December 2010 Mastering new and expanding financial services regulations and audits 2 Mastering new and expanding financial services regulations and audits Contents 2 Executive
CSI Authorization Auditor 2016
 CSI Authorization Auditor 2016 1. Functionality 2 2. Features and benefits 3 2.1 Audit features 3 2.2 Business support features 5 2.3 Monitoring features 6 2.4 License Management support features 6 3.
CSI Authorization Auditor 2016 1. Functionality 2 2. Features and benefits 3 2.1 Audit features 3 2.2 Business support features 5 2.3 Monitoring features 6 2.4 License Management support features 6 3.
