Motivating Employees to Comply with Information Security Policies
|
|
|
- Elijah Doyle
- 6 years ago
- Views:
Transcription
1 Association for Information Systems AIS Electronic Library (AISeL) MWAIS 2016 Proceedings Midwest (MWAIS) Spring Motivating Employees to Comply with Information Security Policies David Sikolia Illinois State University, David Biros Oklahoma State University, Follow this and additional works at: Recommended Citation Sikolia, David and Biros, David, "Motivating Employees to Comply with Information Security Policies" (2016). MWAIS 2016 Proceedings This material is brought to you by the Midwest (MWAIS) at AIS Electronic Library (AISeL). It has been accepted for inclusion in MWAIS 2016 Proceedings by an authorized administrator of AIS Electronic Library (AISeL). For more information, please contact
2 Motivating Employees to Comply with Information Security Policies David Sikolia Illinois State University David Biros Oklahoma State University ABSTRACT Employee noncompliance with Information Systems security policies is a serious computer security threat. Employees extensive knowledge of information systems, their access credentials, and the trust accorded them by their employers make them a potential threat to computer security. The importance of this phenomenon has led to a number of studies on the insider threat. However, research on employee compliance with IS security policies has focused mainly on the role of extrinsic motivation. Few studies have focused on the role of intrinsic motivation. This study fills this gap by building a theoretical model based on data using grounded theory methodology. Seed concepts from High Performance Work Systems (HPWS) were used to develop initial questions for structured interviews with employees from a variety of institutions. This theoretical model lays a framework for how organizations can intrinsically motivate their employees to comply with organizational information security policies. Keywords: Information security, Grounded Theory Methodology, Intrinsic Motivation INTRODUCTION Information security threats come from many fronts, both external and internal, and organizations have implemented both technical and non-technical measures to mitigate these risks (Ifinedo 2012; Siponen et al. 2007). In this study, we focus on internal security risks, specifically the behavior of the trusted employees of an organization. We seek to understand the organizational initiatives that lead to improved employee compliance with information security policies. Considering the consequences of data and computer systems breaches, we develop a framework for explaining how employees can be intrinsically motivated to comply with such security policies. Motivational perspectives have been widely used to understand human behavior in relation to the use of information systems. For example, in their research, Davis et al. (1992) found both intrinsic and extrinsic motivational factors to be key drivers for the adoption of technology in organizations, giving perceived usefulness as an example of extrinsic motivation and enjoyment as an example of intrinsic motivation. Intrinsic motivation leads to behavior that is driven by internal rewards, while extrinsic motivation leads to behavior driven by external rewards. Intrinsic motivation refers to an individuals engagement in a given behavior for no other reason other than the pleasure or satisfaction derived from it (Davies et al. 1992; Venkatesh 1999). Extrinsic motivation is behavior influenced by the value of outcomes that are distinct from the activity itself, for example promotions, pay raises, and improved job performance (Davies et al. 1992; Venkatesh 1999). Most studies on the insider threat have focused on employee compliance or non-compliance with information security policies on the basis of extrinsic motivators (Guo et al. 2011). The extrinsic motivators in these studies include perceived certainty, severity, and celerity of punishment; subjective norms; cost-benefit analysis; perceived vulnerability; and sanction effects. These studies have examined this phenomenon using theoretical lenses that include deterrence theory (D Arcy et al. 2009; Herath and Rao 2009; Hu et al. 2011; Siponen and Iivari 2006; Siponen and Vance 2010; Straub 1990), protection motivation theory (Herath and Rao 2009; Siponen and Iivari 2006), and rational choice theory (Bulgurcu et al. 2010; Li et al. 2010), among others. A review of the literature reveals that extrinsic motivational factors show mixed or even contradictory results (D'Arcy and Herath 2011). As a research community, in seeking to understand why employees fail to comply with information security policies, we have not explicitly examined the role of intrinsic motivation. This is the gap we hope to fill by exploring the two research questions below. RQ1: Why do employees fail to comply with an organization s information security policies? Proceedings of the Eleventh Midwest Association for Information Systems Conference, Milwaukee, Wisconsin, May 19-20,
3 RQ2: How can organizations help their employees to be intrinsically motivated to comply with the organization s information security policies? The rest of the study is organized as follows. The next section describes the research methodology, followed by our findings, a discussion of the findings. RESEARCH METHODOLOGY This study applies a grounded theory methodology (GTM) because the goal is to generate a theoretical model with explanatory power (Birks and Mills 2011). We began by identifying ideational or seed constructs, which were used to develop initial interview questions. Data analysis proceeded from open coding (identifying categories, properties, and dimensions) through selective coding (clustering around categories), to theoretical coding (Urquhart 2012). Figure 1. Research process One characteristic of grounded theory is that there is no prior formulation of hypotheses or expectations to be confirmed by the data. The goal of grounded theory is not to verify or falsify existing theory. However, a researcher cannot approach a study with an empty head; rather he or she must be open minded (Urquhart et al. 2010). A priori specification of constructs can help guide the initial design of the data collection in grounded research, but these constructs are tentative and none is guaranteed a place in the final theory (Eisenhardt 1989). The seed ideas for how organizations can help their employees be intrinsically motivated to comply with information security policies came from human resources literature. Specifically, we looked at the role of high performance work systems in motivating employees. High performance work systems (HPWS) are defined as a set of unique but interconnected human resource practices designed to enhance employees skills and effort (Messersmith et al. 2011; Patel et al. 2013). The human resource (HR) literature does not include a specific set of HPWS practices but they traditionally included recruitment and selection, pay and compensation plans, information sharing, performance appraisal processes, and training. These HR practices have been linked to factors such as productivity, voluntary turnover, profitability, growth, innovation, and customer service (Messersmith et al. 2011; Patel et al. 2013). HPWS are associated with higher levels of job satisfaction, commitment to the organization, and psychological empowerment by the employees. This positive attitude has been positively correlated with better organizational citizenship behavior (Messersmith et al. 2011; Patel et al. 2013). Such behavior may include compliance with organizational information security policies. The relationship between organizational HPWS and two individual-level employee attitudes, job satisfaction and affective commitment were found to be fully mediated by organizational-level concern for employees. HPWS have been found to facilitate a climate of concern for both employees and customers which resulted in employees engaging in positive behaviors towards customers and fellow employees (Chuang and Liao 2010). Proceedings of the Eleventh Midwest Association for Information Systems Conference, Milwaukee, Wisconsin, May 19-20,
4 HPWS have been shown to affect employee motivation. Liao et al. (2009) found that two motivational constructs, psychological empowerment and perceived organizational support, have an impact on individual employee performance. Psychological empowerment, which refers to self-motivating mechanisms and consists of meaning, competency, and selfdetermination, reflects an individual s innate intrinsic task motivation (Liao et al. 2009). We propose that these HPWS in an organization can lead to improved employee compliance with information systems security policies through psychological empowerment of the employees or the activation of their innate intrinsic motivation (Liao et al. 2009). Therefore, these HPWS practices provided the seed ideas or ideational concepts that informed our first set of interview questions. Interviews Data was collected through semi-structured interviews. The interview questions were adjusted during the interview based on the responses to initial questions as well as over the course of the data collection period. The initial interview questions were developed around concepts identified in the high performance work systems (Boxall and Macky 2009). The interviews were semi-structured and therefore new questions were asked whenever new ideas were presented by the interviewees. Additional questions were also asked to probe more deeply into the responses received or to clarify some issues. Thus, the interviews were tailored to the people and the context. We conducted more than 20 interviews, 17 face to face and recorded on an audio device and three by telephone with notes taken during the interview. The interviewees came from a large mid-western University, a small technology firm with 150 employees, a large oil company and an aircraft parts manufacturer. On average, each interview lasted a little more than 30 minutes. In total there were 670 minutes of interview audio. The interviews were then transcribed, resulting in more than 200 single spaced pages in a Word document. Data analysis The interviews were coded in the following order: open coding, selective coding, and theoretical coding (Urquhart 2012). A memo summarizing the core message from each interview was also written at this stage. Open coding was performed multiple times on each of these transcripts. The next step was selective coding. From the open codes identified in each interview, we selected core codes that explain compliance with information security policies. The memos summarizing each interview transcript were used to search for themes that appeared in more than one interview. These themes were aggregated into categories or super-categories. At this point, we used NVivo software to help us manage and organize the textual data. From our analysis of the data, the following framework emerged for improving employee compliance with information security policies in organizations (Figure 2). Proceedings of the Eleventh Midwest Association for Information Systems Conference, Milwaukee, Wisconsin, May 19-20,
5 Figure 2: Framework for improving employee compliance with information security policies The concepts, formed from selectively coding and categorizing the open coding labels, are clustered into four main categories: organization, information technology, employee, and outcomes. The framework represents a cycle with each of the categories impacting all the other categories. DISCUSSION The primary goal of this study was to understand how organizations can intrinsically motivate their employees to comply with information security policies. Although our data analysis shows that employees need both intrinsic and extrinsic motivation to improve their compliance, the discussion here is limited to intrinsic motivation. The first research question was: RQ1: Why do employees fail to comply with an organization s information security policies? Our study found two intrinsic motivations, employee engagement and employee perception that a task can be accomplished. Engagement has two components, emotional attachment and commitment. Employees who demonstrate engagement comply with the information security policies with a passion and understand how important their behavior is to the organization. They feel a strong emotional bond to the organization and demonstrate a willingness to encourage fellow employees to comply with the information security policies. Accomplishable refers to a policy that is realizable, achievable, doable, or manageable. The information security policies make sense to the employees and they have the ability to actually comply with them. The information security policies are well defined so that the employees can act on them. Therefor employees fail to comply for lack of engagement and if given tasks that are difficult to implement. The second research question was: RQ2: How can organizations help their employees to be intrinsically motivated to comply with the organization s information security policies? Proceedings of the Eleventh Midwest Association for Information Systems Conference, Milwaukee, Wisconsin, May 19-20,
6 These two sources of intrinsic motivation are influenced by two organizational practices, organizational culture and job design respectively. Organizational culture emerged as a determinant of employee compliance with information security policies. Two dimensions were identified in the organizational environment: employee involvement and organizational support. Employee involvement refers to employees feeling they are part of the team that makes decisions impacting them. The opposite of this is a feeling of living under the law, and a dislike for rules that are inhibiting and excessively restrictive. Organizational support refers to the perception by employees that the organization has in place structures to help them succeed in their job. This support ranges from compensation, the work environment, and in-house technical support to the relationship with management. Job design, the putting together of tasks or elements to form a job, includes what tasks are done, when and how the tasks are done, how many tasks are done, and in what order the tasks are done, factors which affect the work and the organization of the content and tasks. It is easier to comply with IT policies if they are built into the work process. For example, if employees are required to destroy social security numbers as part of their work, building this process into an IT policy would almost guarantee compliance. Job design clarifies what tasks are done and when and how they are done. For example, the interaction between a nurse, a patient, and the information technology (computer hardware and software applications) should be clearly stated step by step. Job design encompasses task characteristics and the usefulness of the procedures and limitations imposed by the information systems. In this context, procedure refers to who, what, where, when, and why a job is done in a given way; other words and phrases for this concept include protocol, accounting rules, and departmental login processes. Usefulness refers to convenient, enabling, and unobtrusive information security policies. For example, being required to change one s password too often is seen as inconvenient and policies that are too restrictive slow down the pace at which a job is done. Sometimes employees perceive information security policies as a barrier to accomplishing their day-today business. Effect of organizational culture on employee engagement Figure 3: Model for intrinsically motivating employees Therefore, organizations can help their employees comply with IS policies through creation of a positive work environment and designing policies that can be implemented comfortably. REFERENCES (Sykes and Matza 1957)Birks, M., and Mills, J Grounded Theory: A Practical Guide. Thousand Oaks, California: Sage. Boxall, P., and Macky, K "Research and Theory on High-Performance Work Systems: Progressing the High Involvement Stream," Human Resource Management Journal (19:1), pp Bulgurcu, B., Cavusoglu, H., and Benbasat, I "Information Security Policy Compliance: An Empirical Study of Rationality-Based Beliefs and Information Security Awareness," MIS Quarterly (34:3), pp. 523-A527. Proceedings of the Eleventh Midwest Association for Information Systems Conference, Milwaukee, Wisconsin, May 19-20,
7 Chuang, C.-H., and Liao, H "Strategic Human Resource Management in Service Context: Taking Care of Business by Taking Care of Employees and Customers," Personnel Psychology (63:1), pp D'Arcy, J., and Herath, T "A Review and Analysis of Deterrence Theory in the Is Security Literature: Making Sense of the Disparate Findings," European Journal of Information Systems (20:6), pp D Arcy, J., Hovav, A., and Galletta, D "User Awareness of Security Countermeasures and Its Impact on Information Systems Misuse: A Deterrence Approach," Information Systems Research (20:1), pp Davies, F. D., Bagozzi, R. B., and Warshaw, P. R "Extrinsic and Intrinsic Motivation to Use Computes in the Workplace," Journal of Applied Psychology (22:14), pp Eisenhardt, K. M "Building Theories from Case Study Research," Academy of Management Review (14:4), pp Goffee, R., and Jones, G "What Hold the Modern Company Together?," Harvard Business Review (76:6), pp Goodhue, D. L., and Thompson, R. L "Task-Technology Fit and Individual Performance," MIS Quarterly (19:2), pp Guo, K. H., Yuan, Y., Archer, N. P., and Connelly, C. E "Understanding Nonmalicious Security Violations in the Workplace: A Composite Behavior Model," Journal of Management Information Systems (28:2), pp Hackman, J. R., and Oldham, G. R "Motivation through the Design of Work," Organizational Behaviour and Human Performance (16), pp Harper, G. R., and Utley, D. R "Organizational Culture and Successful Information Technology Implementation," Engineering Management Journal (13:2), pp Herath, T., and Rao, H. R "Protection Motivation and Deterrence: A Framework for Security Policy Compliance in Organisations," European Journal of Information Systems (18:2), pp Hoffman, N., and Klepper, R "Assimilating New Technologies: The Role of Organizational Culture," Information Systems Management (17:3), pp Hu, Q., Xu, Z., Dinev, T., and Ling, H "Does Deterrence Work in Reducing Information Security Policy Abuse by Employees?," Communications of the ACM (54:6), pp Ifinedo, P "Understanding Information Security Systems Security Policy Compliance: An Integration of the Theory of Planned Behavior and Protection Motivation Theory," Computers & Security (31), pp Lawler, E. E., and Hall, D. T "Relationship of Job Characteristics to Job Invlovement, Satisfaction and Intrinsic Motivation," Journal of Applied Psychology (54:4), pp Leidner, D. E., and Kayworth, T "Review: A Review of Culture in Information Systems Research: Toward a Theory of Information Technology Culture Conflict," MIS Quarterly (30:2), pp Li, H., Zhang, J., and Sarathy, R "Understanding Compliance with Internet Use Policy from the Perspective of Rational Choice Theory," Decision Support Systems (48:4), pp Liao, H., Toya, K., Lepak, D. P., and Hong, Y "Do They See Eye to Eye? Management and Employee Perspectives of High-Perfomance Work Systems and Influence Processes on Service Quality," Journal of Applied Psychology (94:2), pp Messersmith, J. G., Patel, P. C., and Lepak, D. P "Unlocking the Black Box: Exploring the Link between High- Performance Work Systems and Performance," Journal of Applied Psychology (96:6), pp Minor, W. W "Techniques of Neutralization: A Reconceptualization and Empirical Examination," Journal of Research in Crime and Delinquency (18:2), pp Patel, P. C., Messersmith, J. G., and Lepak, D. P "Walking the Tightrope: An Assessment of the Relationship between High-Performance Work Systems and Organizational Ambidexterity," Academy of Management Journal (56:5), pp Proceedings of the Eleventh Midwest Association for Information Systems Conference, Milwaukee, Wisconsin, May 19-20,
8 Siponen, M., and Iivari, J "Six Design Theories for Is Security Policies and Guidelines," Journal of the Association for Information Systems (7:7), pp Siponen, M., Pahnila, S., and Mahmood, A. (eds.) Employee's Adherence to Information Security Policies: An Empirical Study. Boston: Springer. Siponen, M., and Vance, A "Neutralization: New Insights into the Problem of Employee Informaton Systems Security Policy Violations," MIS Quarterly (34:3), pp. 487-A412. Straub, D. W "Effective Is Security: An Empirical Study," Information Systems Research (1:3), pp Sykes, G. M., and Matza, D "Techniques of Neutralization: A Theory of Delinquency," American Sociological Review (22:6), pp Urquhart, C., Lehmann, H., and Myers, M. D "Putting the 'Theory' Back into Grounded Theory: Guidelines for Grounded Theory Studies in Information Systems," Information Systems Journal (20), pp Urquhart, K Grounded Theory for Qualitative Research: A Practical Guide. Venkatesh, V "Creation of Favorable User Perceptions: Exploring the Role of Intrinsic Motivation," MIS Quarterly (23:2), pp Proceedings of the Eleventh Midwest Association for Information Systems Conference, Milwaukee, Wisconsin, May 19-20,
The Role of Buying Center Members Individual Motivations for the Adoption of Innovative Hybrid Offerings
 The Role of Buying Center Members Individual Motivations for the Adoption of Innovative Hybrid Offerings - The Case of Battery Electric Vehicles in Corporate Fleets This paper investigates the adoption
The Role of Buying Center Members Individual Motivations for the Adoption of Innovative Hybrid Offerings - The Case of Battery Electric Vehicles in Corporate Fleets This paper investigates the adoption
Adoption of Information Security as Decisionmaking under Uncertainty: A Behavioural Economics Approach
 Association for Information Systems AIS Electronic Library (AISeL) ECIS 2015 Research-in-Progress Papers ECIS 2015 Proceedings Spring 5-29-2015 Adoption of Information Security as Decisionmaking under
Association for Information Systems AIS Electronic Library (AISeL) ECIS 2015 Research-in-Progress Papers ECIS 2015 Proceedings Spring 5-29-2015 Adoption of Information Security as Decisionmaking under
IT Knowledge and Skills Required in Business An Investigation of Different Business Professions
 Association for Information Systems AIS Electronic Library (AISeL) MWAIS 2010 Proceedings Midwest (MWAIS) 5-2010 An Investigation of Different Business Professions Jun He University of Michigan - Dearborn,
Association for Information Systems AIS Electronic Library (AISeL) MWAIS 2010 Proceedings Midwest (MWAIS) 5-2010 An Investigation of Different Business Professions Jun He University of Michigan - Dearborn,
From Employee Perceived HR Practices to Employee Engagement: The Influence of Psychological Empowerment and Intrinsic Motivation Jie HE 1,a
 International Conference on Management Science and Management Innovation (MSMI 2014) From Employee Perceived HR Practices to Employee Engagement: The Influence of Psychological Empowerment and Intrinsic
International Conference on Management Science and Management Innovation (MSMI 2014) From Employee Perceived HR Practices to Employee Engagement: The Influence of Psychological Empowerment and Intrinsic
Strategic Information Systems Planning: A Literature Review
 Association for Information Systems AIS Electronic Library (AISeL) MWAIS 2014 Proceedings Midwest (MWAIS) 5-15-2014 Strategic Information Systems Planning: A Literature Review George Mangalaraj Western
Association for Information Systems AIS Electronic Library (AISeL) MWAIS 2014 Proceedings Midwest (MWAIS) 5-15-2014 Strategic Information Systems Planning: A Literature Review George Mangalaraj Western
Social Media Malware: Determinants of Users Intention to Share Potentially Infected Posts
 Social Media Malware: Determinants of Users Intention to Share Potentially Infected Posts Emergent Research Forum Paper Sonia Camacho Universidad de los Andes so-camac@uniandes.edu.co Abstract Malware
Social Media Malware: Determinants of Users Intention to Share Potentially Infected Posts Emergent Research Forum Paper Sonia Camacho Universidad de los Andes so-camac@uniandes.edu.co Abstract Malware
An Integrative Model of Clients' Decision to Adopt an Application Service Provider
 Association for Information Systems AIS Electronic Library (AISeL) AMCIS 2003 Proceedings Americas Conference on Information Systems (AMCIS) December 2003 An Integrative Model of Clients' Decision to Adopt
Association for Information Systems AIS Electronic Library (AISeL) AMCIS 2003 Proceedings Americas Conference on Information Systems (AMCIS) December 2003 An Integrative Model of Clients' Decision to Adopt
Business Process Agility
 Association for Information Systems AIS Electronic Library (AISeL) AMCIS 2005 Proceedings Americas Conference on Information Systems (AMCIS) 2005 Robyn L. Raschke Arizona State University, robyn.raschke@asu.edu
Association for Information Systems AIS Electronic Library (AISeL) AMCIS 2005 Proceedings Americas Conference on Information Systems (AMCIS) 2005 Robyn L. Raschke Arizona State University, robyn.raschke@asu.edu
Value-Focused Assessment of Information System Security in Organizations
 Association for Information Systems AIS Electronic Library (AISeL) ICIS 2001 Proceedings International Conference on Information Systems (ICIS) 12-31-2001 Value-Focused Assessment of Information System
Association for Information Systems AIS Electronic Library (AISeL) ICIS 2001 Proceedings International Conference on Information Systems (ICIS) 12-31-2001 Value-Focused Assessment of Information System
High Performance Work Systems
 1 High Performance Work Systems 2 HIGH PERFORMANCE WORK SYSTEMS High Performance Work System (HPWS) is a name given to the form of organization that is frequently seen as most appropriate for contemporary
1 High Performance Work Systems 2 HIGH PERFORMANCE WORK SYSTEMS High Performance Work System (HPWS) is a name given to the form of organization that is frequently seen as most appropriate for contemporary
User Acceptance of E-Government Services
 Association for Information Systems AIS Electronic Library (AISeL) PACIS 2007 Proceedings Pacific Asia Conference on Information Systems (PACIS) 2007 User Acceptance of E-Government Services Ying-Hsun
Association for Information Systems AIS Electronic Library (AISeL) PACIS 2007 Proceedings Pacific Asia Conference on Information Systems (PACIS) 2007 User Acceptance of E-Government Services Ying-Hsun
Does Transformational Leadership Leads To Higher Employee Work Engagement. A Study of Pakistani Service Sector Firms
 Does Transformational Leadership Leads To Higher Employee Work Engagement. A Study of Pakistani Service Sector Firms M. Waqas Raja PhD Scholar COMSATS Institute of Information Technology Chak Shahzad Campus,
Does Transformational Leadership Leads To Higher Employee Work Engagement. A Study of Pakistani Service Sector Firms M. Waqas Raja PhD Scholar COMSATS Institute of Information Technology Chak Shahzad Campus,
Knowledge of Security Protocols and Acceptance of E-commerce
 Knowledge of Security Protocols and Acceptance of E-commerce Sumendra Singh, Faculty of Business and IT, Webster University, Thailand. E-mail: singh89sumendra@gmail.com Leslie Klieb, Faculty of Business
Knowledge of Security Protocols and Acceptance of E-commerce Sumendra Singh, Faculty of Business and IT, Webster University, Thailand. E-mail: singh89sumendra@gmail.com Leslie Klieb, Faculty of Business
Understanding the Current Situation of E-Government in Saudi Arabia: A Model for Implementation and Sustainability
 Understanding the Current Situation of E-Government in Saudi Arabia: A Model for Implementation and Sustainability Majed Alfayad and Edward Abbott-Halpin School of Computing, Creative Technology, and Engineering,
Understanding the Current Situation of E-Government in Saudi Arabia: A Model for Implementation and Sustainability Majed Alfayad and Edward Abbott-Halpin School of Computing, Creative Technology, and Engineering,
USER ACCEPTANCE OF DIGITAL LIBRARY: AN EMPIRICAL EXPLORATION OF INDIVIDUAL AND SYSTEM COMPONENTS
 USER ACCEPTANCE OF DIGITAL LIBRARY: AN EMPIRICAL EXPLORATION OF INDIVIDUAL AND SYSTEM COMPONENTS Ganesh Vaidyanathan, Indiana University South Bend, gvaidyan@iusb.edu Asghar Sabbaghi, Indiana University
USER ACCEPTANCE OF DIGITAL LIBRARY: AN EMPIRICAL EXPLORATION OF INDIVIDUAL AND SYSTEM COMPONENTS Ganesh Vaidyanathan, Indiana University South Bend, gvaidyan@iusb.edu Asghar Sabbaghi, Indiana University
TIONAL EFFECTIVENESS
 ROLE OF EMPLOYEE COMMITMENT IN ORGANIZA ANIZATIO TIONAL EFFECTIVENESS G.P.P.. Mishra* THE study leads us to believe that in the eyes of employees they do a lot for their organization and they also have
ROLE OF EMPLOYEE COMMITMENT IN ORGANIZA ANIZATIO TIONAL EFFECTIVENESS G.P.P.. Mishra* THE study leads us to believe that in the eyes of employees they do a lot for their organization and they also have
International Review of Business Research Papers Vol. 3 No.5 November 2007 Pp.36-43
 International Review of Business Research Papers Vol. 3 No.5 November 2007 Pp.36-43 Inhibitors and Enablers to Internet Banking in Oman - A Comparison with Banks in Australia Salim Al-Hajri* and Arthur
International Review of Business Research Papers Vol. 3 No.5 November 2007 Pp.36-43 Inhibitors and Enablers to Internet Banking in Oman - A Comparison with Banks in Australia Salim Al-Hajri* and Arthur
The Effect of Service Guarantees on Online Customers Purchase Intention
 Association for Information Systems AIS Electronic Library (AISeL) WHICEB 2014 Proceedings Wuhan International Conference on e-business Summer 6-1-2014 The Effect of Service Guarantees on Online Customers
Association for Information Systems AIS Electronic Library (AISeL) WHICEB 2014 Proceedings Wuhan International Conference on e-business Summer 6-1-2014 The Effect of Service Guarantees on Online Customers
A Study of the Employee Engagement Practices in the Indian Manufacturing Sector
 A Study of the Employee Engagement Practices in the Indian Manufacturing Sector 1 Dr Shilpa Varma, 2 Ms PriyaVij, 3 Dr R Gopal 1 Associate Professor DY Patil University School of Management 2 Assistant
A Study of the Employee Engagement Practices in the Indian Manufacturing Sector 1 Dr Shilpa Varma, 2 Ms PriyaVij, 3 Dr R Gopal 1 Associate Professor DY Patil University School of Management 2 Assistant
Organizational Commitment. Schultz, 1
 Organizational Commitment Schultz, 1 Schultz, 2 Organizational Commitment Organizational commitment has an important place in the study of organizational behavior. This is in part due to the vast number
Organizational Commitment Schultz, 1 Schultz, 2 Organizational Commitment Organizational commitment has an important place in the study of organizational behavior. This is in part due to the vast number
The Influence of Intrinsic and Extrinsic Motivation on Employee Engagement
 The Influence of Intrinsic and Extrinsic Motivation on Employee Engagement A qualitative study of the perceptions of managers in public and private sector organizations Authors: Supervisor: Emma Bergström
The Influence of Intrinsic and Extrinsic Motivation on Employee Engagement A qualitative study of the perceptions of managers in public and private sector organizations Authors: Supervisor: Emma Bergström
An Investigation on How Brand Attachment and Brand Experience Affect Customer equity and Customer Loyalty
 An Investigation on How Brand Attachment and Brand Experience Affect Customer equity and Customer Loyalty Research motivation: In the recent years, many constructs have been developed in the field of branding.
An Investigation on How Brand Attachment and Brand Experience Affect Customer equity and Customer Loyalty Research motivation: In the recent years, many constructs have been developed in the field of branding.
EMPLOYEE ENGAGEMENT. Administrative Office Circuit Court of Lake County, Illinois 2014 Court Employee Engagement Survey. Employee Growth & Development
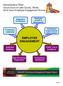 Administrative Office, Illinois 2014 Court Employee Engagement Survey Supportive Co-Workers Employee Growth & Development Trustworthy Leadership Continuous Organizational Improvement EMPLOYEE ENGAGEMENT
Administrative Office, Illinois 2014 Court Employee Engagement Survey Supportive Co-Workers Employee Growth & Development Trustworthy Leadership Continuous Organizational Improvement EMPLOYEE ENGAGEMENT
EVALUATING AND RANKING LOCAL E- GOVERNMENT SERVICES
 Association for Information Systems AIS Electronic Library (AISeL) MCIS 2010 Proceedings Mediterranean Conference on Information Systems (MCIS) 9-2010 EVALUATING AND RANKING LOCAL E- GOVERNMENT SERVICES
Association for Information Systems AIS Electronic Library (AISeL) MCIS 2010 Proceedings Mediterranean Conference on Information Systems (MCIS) 9-2010 EVALUATING AND RANKING LOCAL E- GOVERNMENT SERVICES
End-user IT Security Policy Compliance: A Confidence-Building Measures Approach
 End-user IT Security Policy Compliance: A Confidence-Building Measures Approach Abstract Research-in-Progress Emmanuel Ayaburi The University of Texas at San Antonio emmanuel.ayaburi@utsa.edu Corporate
End-user IT Security Policy Compliance: A Confidence-Building Measures Approach Abstract Research-in-Progress Emmanuel Ayaburi The University of Texas at San Antonio emmanuel.ayaburi@utsa.edu Corporate
HRM and Dairy. Research Questions. Purpose of the Study. Dependent Variable. Explanatory Variables
 HRM and Dairy Managing for Commitment: How Human Resource Management Practices Affect Dairy Employee Attitudes Richard Stup, Ph.D. AgChoice Farm Credit Popular press is filled with articles, information,
HRM and Dairy Managing for Commitment: How Human Resource Management Practices Affect Dairy Employee Attitudes Richard Stup, Ph.D. AgChoice Farm Credit Popular press is filled with articles, information,
HRM. Unit 1. Dr. Vinita Pimpale. Dr. Vinita Pimpale R.A.Podar College of Commerce & Economics
 HRM Unit 1 1 What Is Human Resource Management? Human Resource Management (HRM) is the function within an organization that focuses on recruitment of, management of, and providing direction for the people
HRM Unit 1 1 What Is Human Resource Management? Human Resource Management (HRM) is the function within an organization that focuses on recruitment of, management of, and providing direction for the people
Basic Motivation Concepts
 Basic Motivation Concepts 2005 Prentice Hall Inc. All rights reserved. ORGANIZATIONAL BEHAVIOR S T E P H E N P. R O B B I N S E L E V E N T H E D I T I O N W W W. P R E N H A L L. C O M / R O B B I N S
Basic Motivation Concepts 2005 Prentice Hall Inc. All rights reserved. ORGANIZATIONAL BEHAVIOR S T E P H E N P. R O B B I N S E L E V E N T H E D I T I O N W W W. P R E N H A L L. C O M / R O B B I N S
Toward An Understanding of the Behavioral Intention to Use Mobile Banking Services
 Association for Information Systems AIS Electronic Library (AISeL) PACIS 2004 Proceedings Pacific Asia Conference on Information Systems (PACIS) December 2004 Toward An Understanding of the Behavioral
Association for Information Systems AIS Electronic Library (AISeL) PACIS 2004 Proceedings Pacific Asia Conference on Information Systems (PACIS) December 2004 Toward An Understanding of the Behavioral
The Effect of Accounting Information Systems in Accounting
 The Effect of Accounting Information Systems in Accounting Awosejo, O.J 1, Kekwaletswe, R, M 2, Pretorius, P 3 and Zuva, T 4 Abstracts Generally, ICT have improved the quality of professional services
The Effect of Accounting Information Systems in Accounting Awosejo, O.J 1, Kekwaletswe, R, M 2, Pretorius, P 3 and Zuva, T 4 Abstracts Generally, ICT have improved the quality of professional services
SUPERVISORY COMMUNICATION AND ITS EFFECT ON EMPLOYEE SATISFACTION AT THE CUT, WELKOM CAMPUS
 SUPERVISORY COMMUNICATION AND ITS EFFECT ON EMPLOYEE SATISFACTION AT THE CUT, WELKOM CAMPUS Abstract M. MOLEFE AND M. VAN DEVENTER Many large organisations tend to focus on their external communication
SUPERVISORY COMMUNICATION AND ITS EFFECT ON EMPLOYEE SATISFACTION AT THE CUT, WELKOM CAMPUS Abstract M. MOLEFE AND M. VAN DEVENTER Many large organisations tend to focus on their external communication
QUALITY INSTITUTIONALIZATION IN THE PUBLIC SECTOR: THE WISCONSIN DEPARTMENT OF REVENUE STUDY
 QUALITY INSTITUTIONALIZATION IN THE PUBLIC SECTOR: THE WISCONSIN DEPARTMENT OF REVENUE STUDY Peter Hoonakker+, Mary McEniry~, Pascale Carayon*+ and Christian Korunka^ & Francois Sainfort*+ * Department
QUALITY INSTITUTIONALIZATION IN THE PUBLIC SECTOR: THE WISCONSIN DEPARTMENT OF REVENUE STUDY Peter Hoonakker+, Mary McEniry~, Pascale Carayon*+ and Christian Korunka^ & Francois Sainfort*+ * Department
GROUP DYNAMICS. Definition:
 Definition: GROUP DYNAMICS Group dynamics involve the study and analysis of how people interact and communicate with each other in face-to face small groups. The study of group dynamics provides a vehicle
Definition: GROUP DYNAMICS Group dynamics involve the study and analysis of how people interact and communicate with each other in face-to face small groups. The study of group dynamics provides a vehicle
CULTURAL DIFFERENCES IN THE WORK PLACE: A STUDY OF THE WORK ETHICS OF CHINESE AND AMERICANS
 CULTURAL DIFFERENCES IN THE WORK PLACE: A STUDY OF THE WORK ETHICS OF CHINESE AND AMERICANS John E. Merchant, Ph.D. California State University Sacramento (merchant@csus.edu) Abstract While much has been
CULTURAL DIFFERENCES IN THE WORK PLACE: A STUDY OF THE WORK ETHICS OF CHINESE AND AMERICANS John E. Merchant, Ph.D. California State University Sacramento (merchant@csus.edu) Abstract While much has been
A STUDY ON FACTOR THAT INFLUENCE ONLINE SHOPPING IN MALAYSIA. Universiti Tun Hussein Onn Malaysia Batu Pahat, Johor, Malaysia ABSTRACT
 A STUDY ON FACTOR THAT INFLUENCE ONLINE SHOPPING IN MALAYSIA. 1 Rohaizan Ramlan 2 Fatimah. Z. Omar 1 Department of Technology Management 2 Faculty of Technology Management, Business and Entrepreneurship
A STUDY ON FACTOR THAT INFLUENCE ONLINE SHOPPING IN MALAYSIA. 1 Rohaizan Ramlan 2 Fatimah. Z. Omar 1 Department of Technology Management 2 Faculty of Technology Management, Business and Entrepreneurship
Analysing Interview Data (1) Dr Maria de Hoyos & Dr Sally-Anne Barnes
 Analysing Interview Data (1) Dr Maria de Hoyos & Dr Sally-Anne Barnes Institute for Employment Research University of Warwick January 2014 Show of hands Aims of the week 3 and 4 sessions To reflect on
Analysing Interview Data (1) Dr Maria de Hoyos & Dr Sally-Anne Barnes Institute for Employment Research University of Warwick January 2014 Show of hands Aims of the week 3 and 4 sessions To reflect on
Nelson Mandela s Influence Using Organizational Behaviour Techniques
 Nelson Mandela s Influence Using Organizational Behaviour Techniques Leadership and Motivation Megan Latzkowski A leader is like a shepherd. He stays behind the flock, letting them go out ahead, not realizing
Nelson Mandela s Influence Using Organizational Behaviour Techniques Leadership and Motivation Megan Latzkowski A leader is like a shepherd. He stays behind the flock, letting them go out ahead, not realizing
International Journal of Interdisciplinary and Multidisciplinary Studies (IJIMS), 2014, Vol 1, No.6,
 International Journal of Interdisciplinary and Multidisciplinary Studies (IJIMS), 2014, Vol 1, No.6, 49-54. 49 Available online at http://www.ijims.com ISSN: 2348 0343 Study of Importance of Empowered
International Journal of Interdisciplinary and Multidisciplinary Studies (IJIMS), 2014, Vol 1, No.6, 49-54. 49 Available online at http://www.ijims.com ISSN: 2348 0343 Study of Importance of Empowered
Measures for success. Assessment of two E s engagement and enablement can give organizations powerful insights on inclusion beyond diversity.
 Measures for success Assessment of two E s engagement and enablement can give organizations powerful insights on inclusion beyond diversity. Companies for years measured the diversity of their workforce
Measures for success Assessment of two E s engagement and enablement can give organizations powerful insights on inclusion beyond diversity. Companies for years measured the diversity of their workforce
Relationship between HRM Practices and Organizational Commitment of Employees: An Empirical Study of Textile Sector in Pakistan
 Vol. 6, No.1, January 2016, pp. 23 28 E-ISSN: 2225-8329, P-ISSN: 2308-0337 2016 HRMARS www.hrmars.com Relationship between HRM Practices and Organizational Commitment of Employees: An Empirical Study of
Vol. 6, No.1, January 2016, pp. 23 28 E-ISSN: 2225-8329, P-ISSN: 2308-0337 2016 HRMARS www.hrmars.com Relationship between HRM Practices and Organizational Commitment of Employees: An Empirical Study of
Customer Satisfaction and Employee Satisfaction: A Conceptual Model and Research Propositions
 Customer Satisfaction and Employee Satisfaction: A Conceptual Model and Research Propositions Abstract The marketing literature reflects remarkably little effort to develop a framework for understanding
Customer Satisfaction and Employee Satisfaction: A Conceptual Model and Research Propositions Abstract The marketing literature reflects remarkably little effort to develop a framework for understanding
OPQ Profile OPQ. Universal Competency Report. Name Mr Sample Candidate. Date September 20,
 OPQ Profile OPQ Universal Competency Report Name Mr Sample Candidate Date September 20, 2013 www.ceb.shl.com INTRODUCTION This report is intended for use by managers and HR professionals. It summarizes
OPQ Profile OPQ Universal Competency Report Name Mr Sample Candidate Date September 20, 2013 www.ceb.shl.com INTRODUCTION This report is intended for use by managers and HR professionals. It summarizes
Transactional Leadership
 DePaul University From the SelectedWorks of Marco Tavanti 2008 Transactional Leadership Marco Tavanti, DePaul University Available at: https://works.bepress.com/marcotavanti/15/ Transactional Leadership
DePaul University From the SelectedWorks of Marco Tavanti 2008 Transactional Leadership Marco Tavanti, DePaul University Available at: https://works.bepress.com/marcotavanti/15/ Transactional Leadership
HARASSMENT AND BULLYING POLICY
 HARASSMENT AND BULLYING POLICY Latest Revision October 2015 Reviewer: HR Dept Next Revision May 2018 Compliance Associated Policies Current legislation and guidance Grievance, Whistleblowing, Disciplinary
HARASSMENT AND BULLYING POLICY Latest Revision October 2015 Reviewer: HR Dept Next Revision May 2018 Compliance Associated Policies Current legislation and guidance Grievance, Whistleblowing, Disciplinary
Custodial Services Strategic Plan
 Hamilton College Custodial Services Strategic Plan 2005-2008 February 1, 2005 Table of Contents Context for planning..3 Vision.6 Mission.. 6 Core Values...6 Internal/External Assessment 7 Department Description..
Hamilton College Custodial Services Strategic Plan 2005-2008 February 1, 2005 Table of Contents Context for planning..3 Vision.6 Mission.. 6 Core Values...6 Internal/External Assessment 7 Department Description..
Success Factors for Information Systems Outsourcing: A Meta-Analysis
 Association for Information Systems AIS Electronic Library (AISeL) AMCIS 2009 Proceedings Americas Conference on Information Systems (AMCIS) 2009 Success Factors for Information Systems Outsourcing: A
Association for Information Systems AIS Electronic Library (AISeL) AMCIS 2009 Proceedings Americas Conference on Information Systems (AMCIS) 2009 Success Factors for Information Systems Outsourcing: A
The Technology Acceptance Model for Competitive Software Products
 The Technology Acceptance Model for Competitive Software Products Hock Chuan CHAN Department of Information Systems National University of Singapore chanhc@comp.nus.edu.sg Jing YANG Department of Information
The Technology Acceptance Model for Competitive Software Products Hock Chuan CHAN Department of Information Systems National University of Singapore chanhc@comp.nus.edu.sg Jing YANG Department of Information
Job Satisfaction among Primary School Teachers With Respect To Age, Gender and Experience
 The International Journal of Indian Psychology ISSN 2348-5396 (e) ISSN: 2349-3429 (p) Volume 3, Issue 2, No.10, DIP: 18.01.183/20160302 ISBN: 978-1-329-99963-3 http://www.ijip.in January - March, 2016
The International Journal of Indian Psychology ISSN 2348-5396 (e) ISSN: 2349-3429 (p) Volume 3, Issue 2, No.10, DIP: 18.01.183/20160302 ISBN: 978-1-329-99963-3 http://www.ijip.in January - March, 2016
High Performance Organization
 Kai Laamanen HPO description 1 (6) 15.10.2007 High Performance Organization Leaders of today face ever-increasing complexity in private business and public sector. Innotiimi meets the growing need for
Kai Laamanen HPO description 1 (6) 15.10.2007 High Performance Organization Leaders of today face ever-increasing complexity in private business and public sector. Innotiimi meets the growing need for
Employee Performance Enhancement
 Employee Performance Enhancement In today s challenging economic environment, many employers have been reluctant to make significant changes or investments. However, technology has afforded employers the
Employee Performance Enhancement In today s challenging economic environment, many employers have been reluctant to make significant changes or investments. However, technology has afforded employers the
Influences of the Organizational Citizenship Behaviors and Organizational Commitments on the Effects of Organizational Learning in Taiwan
 2010 International Conference on E-business, Management and Economics IPEDR vol.3 (2011) (2011) IACSIT Press, Hong Kong Influences of the Organizational Citizenship Behaviors and Organizational Commitments
2010 International Conference on E-business, Management and Economics IPEDR vol.3 (2011) (2011) IACSIT Press, Hong Kong Influences of the Organizational Citizenship Behaviors and Organizational Commitments
Explaining Organizational Responsiveness to Work-Life Balance Issues: The Role of Business Strategy and High Performance Work System
 Explaining Organizational Responsiveness to Work-Life Balance Issues: The Role of Business Strategy and High Performance Work System Jing Wang1 Anil Verma 2 1 Sobey School of Business, Saint Mary's University,
Explaining Organizational Responsiveness to Work-Life Balance Issues: The Role of Business Strategy and High Performance Work System Jing Wang1 Anil Verma 2 1 Sobey School of Business, Saint Mary's University,
Recruitment and Retention Insights for the Hotel Industry
 Hospitality Review Volume 9 Issue 1 Hospitality Review Volume 9/Issue 1 Article 5 1-1-1991 Recruitment and Retention Insights for the Hotel Industry Peter W. Williams Simon Fraser University, null@sfu.ca
Hospitality Review Volume 9 Issue 1 Hospitality Review Volume 9/Issue 1 Article 5 1-1-1991 Recruitment and Retention Insights for the Hotel Industry Peter W. Williams Simon Fraser University, null@sfu.ca
An Investigation of the Relationship between Social Loafing and Organizational Citizenship Behavior
 Available online at www.sciencedirect.com ScienceDirect Procedia - Social and Behavioral Scien ce s 99 ( 2013 ) 206 215 9 th International Strategic Management Conference An Investigation of the Relationship
Available online at www.sciencedirect.com ScienceDirect Procedia - Social and Behavioral Scien ce s 99 ( 2013 ) 206 215 9 th International Strategic Management Conference An Investigation of the Relationship
Factors Influencing Knowledge Sharing in Organizations: A Literature Review
 International Journal of Science and Research (IJSR) Factors Influencing Knowledge Sharing in Organizations: A Literature Review Ammar Dheyaa Noor 1, Hayder Salah Hashim 2, Norashikin Ali 3 1,2,3 University
International Journal of Science and Research (IJSR) Factors Influencing Knowledge Sharing in Organizations: A Literature Review Ammar Dheyaa Noor 1, Hayder Salah Hashim 2, Norashikin Ali 3 1,2,3 University
Hafan Cymru Job Description
 Job title Grade / Salary Scale Location Contract hours Working Pattern Responsible to Responsible for (staff / finance / Service Users /Customers Job Purpose Competency and Level required Project Manager
Job title Grade / Salary Scale Location Contract hours Working Pattern Responsible to Responsible for (staff / finance / Service Users /Customers Job Purpose Competency and Level required Project Manager
Job Satisfaction of Room Service Personnel in Star Hotels
 International Journal of Business Administration and Management. ISSN 2278-3660 Volume 7, Number 1 (2017), pp. 1-8 Research India Publications http://www.ripublication.com Job Satisfaction of Room Service
International Journal of Business Administration and Management. ISSN 2278-3660 Volume 7, Number 1 (2017), pp. 1-8 Research India Publications http://www.ripublication.com Job Satisfaction of Room Service
Relationship Between Employee Motivation And Performance Of The Employees Working In Retail Sector In Jaipur Dr. Neha Sharma, Ms.
 Relationship Between Employee Motivation And Performance Of The Employees Working In Retail Sector In Jaipur Dr. Neha Sharma, Ms. Avni Sharma Dr. Neha Sharma, Assistant Professor, Department of Commerce,
Relationship Between Employee Motivation And Performance Of The Employees Working In Retail Sector In Jaipur Dr. Neha Sharma, Ms. Avni Sharma Dr. Neha Sharma, Assistant Professor, Department of Commerce,
FROM ACCEPTANCE TO OUTCOME: TOWARDS AN INTEGRATIVE FRAMEWORK FOR INFORMATION TECHNOLOGY ADOPTION
 Association for Information Systems AIS Electronic Library (AISeL) ECIS 2014 Proceedings FROM ACCEPTANCE TO OUTCOME: TOWARDS AN INTEGRATIVE FRAMEWORK FOR INFORMATION TECHNOLOGY ADOPTION Christian Sorgenfrei
Association for Information Systems AIS Electronic Library (AISeL) ECIS 2014 Proceedings FROM ACCEPTANCE TO OUTCOME: TOWARDS AN INTEGRATIVE FRAMEWORK FOR INFORMATION TECHNOLOGY ADOPTION Christian Sorgenfrei
SLA Defined Metrics as a Tool to Manage Outsourced Help Desk Support Services
 Association for Information Systems AIS Electronic Library (AISeL) AMCIS 2011 Proceedings - All Submissions 8-5-2011 SLA Defined Metrics as a Tool to Manage Outsourced Help Desk Support Services David
Association for Information Systems AIS Electronic Library (AISeL) AMCIS 2011 Proceedings - All Submissions 8-5-2011 SLA Defined Metrics as a Tool to Manage Outsourced Help Desk Support Services David
Purpose of Using Social Networks
 American International Journal of Contemporary Research Vol. 2 No. 3; March 2012 Purpose of Using Social Networks Abstract William Barnett, PhD Associate Professor of Computer Information Systems College
American International Journal of Contemporary Research Vol. 2 No. 3; March 2012 Purpose of Using Social Networks Abstract William Barnett, PhD Associate Professor of Computer Information Systems College
Linking supervisor and coworker support to employee innovative behavior at work: role of psychological Conditions
 Linking supervisor and coworker support to employee innovative behavior at work: role of psychological Conditions Vipra Arora Department of Management Studies, Indian Institute of Technology, Madras, India
Linking supervisor and coworker support to employee innovative behavior at work: role of psychological Conditions Vipra Arora Department of Management Studies, Indian Institute of Technology, Madras, India
The Influence of Shopping Website Design on Consumer s Intention to Buy Online: The Case of 3D vs. 2D Online Book Stores
 Association for Information Systems AIS Electronic Library (AISeL) AMCIS 2011 Proceedings - All Submissions 8-6-2011 The Influence of Shopping Website Design on Consumer s Intention to Buy Online: The
Association for Information Systems AIS Electronic Library (AISeL) AMCIS 2011 Proceedings - All Submissions 8-6-2011 The Influence of Shopping Website Design on Consumer s Intention to Buy Online: The
The Impact Of Reward System On The Productivity Of Construction Employees: A Study Of Selected Construction Projects In Port Harcourt
 Volume Issue 4, April 015 ISSN: 394-4404 The Impact Of Reward System On The Productivity Of Construction Employees: A Study Of Selected Construction Projects In Port Harcourt Mee-Edoiye Meeting Andawei
Volume Issue 4, April 015 ISSN: 394-4404 The Impact Of Reward System On The Productivity Of Construction Employees: A Study Of Selected Construction Projects In Port Harcourt Mee-Edoiye Meeting Andawei
Metropolitan College of New York School for Business
 Metropolitan College of New York School for Business Healthcare Management Purpose 6 Handbook Managing Human Resources In Healthcare Contents OVERVIEW OF THE PURPOSE Purpose deliverables, competencies
Metropolitan College of New York School for Business Healthcare Management Purpose 6 Handbook Managing Human Resources In Healthcare Contents OVERVIEW OF THE PURPOSE Purpose deliverables, competencies
University of Macedonia The MBA Program
 University of Macedonia The MBA Program Fall Semester 2017-2018 Human Resources Management: Selected Topics Dimitrios M. Mihail, Ph.D. Professor Department of Business Administration Office: 406 Tel. 2310
University of Macedonia The MBA Program Fall Semester 2017-2018 Human Resources Management: Selected Topics Dimitrios M. Mihail, Ph.D. Professor Department of Business Administration Office: 406 Tel. 2310
Abstract. 1. Introduction
 Abstract Influence of Job Satisfaction on Employees Performance A general Perspective Kamala Saranya* *Research Scholar, Vels University, Pallavaram, Chennai, Tamil Nadu, India. This study takes a dynamic
Abstract Influence of Job Satisfaction on Employees Performance A general Perspective Kamala Saranya* *Research Scholar, Vels University, Pallavaram, Chennai, Tamil Nadu, India. This study takes a dynamic
QUALIFICATION AND COURSE CATALOGUE CIPD
 QUALIFICATION AND COURSE CATALOGUE CIPD CIPD CATEGORIES Click on a category to view course titles CIPD Advanced Awards in HR CIPD Intermediate Awards in HR CIPD Intermediate Awards in L&D CIPD Foundation
QUALIFICATION AND COURSE CATALOGUE CIPD CIPD CATEGORIES Click on a category to view course titles CIPD Advanced Awards in HR CIPD Intermediate Awards in HR CIPD Intermediate Awards in L&D CIPD Foundation
Full file at https://fratstock.eu
 Performance and Productivity: Team Performance Criteria and Threats to Productivity OVERVIEW This chapter is best discussed following a team exercise or case so that students have an opportunity to reflect
Performance and Productivity: Team Performance Criteria and Threats to Productivity OVERVIEW This chapter is best discussed following a team exercise or case so that students have an opportunity to reflect
Durham Research Online
 Durham Research Online Deposited in DRO: 01 December 2017 Version of attached le: Peer-review status of attached le: Peer-reviewed Citation for published item: Bozionelos, N. and Nikolaou, I. (2010) 'Does
Durham Research Online Deposited in DRO: 01 December 2017 Version of attached le: Peer-review status of attached le: Peer-reviewed Citation for published item: Bozionelos, N. and Nikolaou, I. (2010) 'Does
Job Satisfaction And Gender Factor Of Administrative Staff In South West Nigeria Universities E. O. Olorunsola, University Of Ado-Ekiti, Nigeria
 Job Satisfaction And Gender Factor Of Administrative Staff In South West Nigeria Universities E. O. Olorunsola, University Of Ado-Ekiti, Nigeria ABSTRACT The study investigated the level of job satisfaction
Job Satisfaction And Gender Factor Of Administrative Staff In South West Nigeria Universities E. O. Olorunsola, University Of Ado-Ekiti, Nigeria ABSTRACT The study investigated the level of job satisfaction
[ ] 1 Tel: , Fax: ,
![[ ] 1 Tel: , Fax: , [ ] 1 Tel: , Fax: ,](/thumbs/74/70235007.jpg) [007-0540] Handling the Information Management Process in Industrial Service Organisations Aligning Goals and Measures to the Needs of Service Operations André MINKUS 1, ETH Zurich, Centre for Enterprise
[007-0540] Handling the Information Management Process in Industrial Service Organisations Aligning Goals and Measures to the Needs of Service Operations André MINKUS 1, ETH Zurich, Centre for Enterprise
Determinants of Information Technology Leadership Program
 Review of European Studies; Vol. 6, No. 2; 2014 ISSN 1918-7173 E-ISSN 1918-7181 Published by Canadian Center of Science and Education Determinants of Information Technology Leadership Program Roya Anvari
Review of European Studies; Vol. 6, No. 2; 2014 ISSN 1918-7173 E-ISSN 1918-7181 Published by Canadian Center of Science and Education Determinants of Information Technology Leadership Program Roya Anvari
Application of the Technology Acceptance Model to a Knowledge Management System
 Application of the Technology Acceptance Model to a Knowledge Management System Associate Professor William Money, Ph. D Arch Turner, Doctoral Candidate The George Washington University wmoney@gwu.edu/turnera@onr.navy.mil
Application of the Technology Acceptance Model to a Knowledge Management System Associate Professor William Money, Ph. D Arch Turner, Doctoral Candidate The George Washington University wmoney@gwu.edu/turnera@onr.navy.mil
Organizational Factors Affecting Employee Innovative Behavior
 Doi:10.5901/mjss.2015.v6n1s3p435 Abstract Organizational Factors Affecting Employee Innovative Behavior Kabasheva I.A. a Rudaleva I.A. b Bulnina I.S. c Askhatova L.I. d a b c d Kazan Federal University,
Doi:10.5901/mjss.2015.v6n1s3p435 Abstract Organizational Factors Affecting Employee Innovative Behavior Kabasheva I.A. a Rudaleva I.A. b Bulnina I.S. c Askhatova L.I. d a b c d Kazan Federal University,
Learning Objectives. After you have read this chapter, you should be able to:
 ROBERT L. MATHIS JOHN H. JACKSON Chapter 3 Organization/Individual Relations and Retention Presented by: Prof. Dr. Deden Mulyana, SE.,M,Si. SECTION 1 Nature of Human Resource Management http://www.deden08m.wordpress.com
ROBERT L. MATHIS JOHN H. JACKSON Chapter 3 Organization/Individual Relations and Retention Presented by: Prof. Dr. Deden Mulyana, SE.,M,Si. SECTION 1 Nature of Human Resource Management http://www.deden08m.wordpress.com
Toward a Rational Choice Process Theory of Internet Scamming: The Offender s Perspective
 Toward a Rational Choice Process Theory of Internet Scamming: The Offender s Perspective Research-in-Progress Tambe Ebot Alain Claude University of Jyväskylä Jyväskylä, Finland alcltamb@student.jyu.fi
Toward a Rational Choice Process Theory of Internet Scamming: The Offender s Perspective Research-in-Progress Tambe Ebot Alain Claude University of Jyväskylä Jyväskylä, Finland alcltamb@student.jyu.fi
Organization Culture Dimensions as Antecedents of Internet Technology Adoption
 Organization Culture Dimensions as Antecedents of Internet Technology Adoption Subhasish Dasgupta 1 and Babita Gupta 2 1 George Washington University, 2115 G Street, NW, Suite 515, Washington, DC 20052,
Organization Culture Dimensions as Antecedents of Internet Technology Adoption Subhasish Dasgupta 1 and Babita Gupta 2 1 George Washington University, 2115 G Street, NW, Suite 515, Washington, DC 20052,
Material and Non-material Motivation of Compliant Food Businesses: Disclosure of Food Hygiene Inspection Results in Germany
 Material and Non-material Motivation of Compliant Food Businesses: Disclosure of Food Hygiene Inspection Results in Germany Miroslava Bavorová 1, Anica Fietz 2 1, 2 Martin-Luther University Halle-Wittenberg
Material and Non-material Motivation of Compliant Food Businesses: Disclosure of Food Hygiene Inspection Results in Germany Miroslava Bavorová 1, Anica Fietz 2 1, 2 Martin-Luther University Halle-Wittenberg
Why Employees Do Non-Work-Related Computing: An Investigation of Factors Affecting NWRC in a Workplace
 Association for Information Systems AIS Electronic Library (AISeL) PACIS 2006 Proceedings Pacific Asia Conference on Information Systems (PACIS) 2006 Why Employees Do Non-Work-Related Computing: An Investigation
Association for Information Systems AIS Electronic Library (AISeL) PACIS 2006 Proceedings Pacific Asia Conference on Information Systems (PACIS) 2006 Why Employees Do Non-Work-Related Computing: An Investigation
Personality Matters, Inc. Cherry A. Collier, PhD, MCC, RCC. Chief Engagement Officer (CEO) & Head Coach
 Personality Matters, Inc. Cherry A. Collier, PhD, MCC, RCC. Chief Engagement Officer (CEO) & Head Coach www.mypersonalitymatters.com MPM@mypersonalitymatters.com 919 4.PEOPLE (473.6753) or 678.574.5070
Personality Matters, Inc. Cherry A. Collier, PhD, MCC, RCC. Chief Engagement Officer (CEO) & Head Coach www.mypersonalitymatters.com MPM@mypersonalitymatters.com 919 4.PEOPLE (473.6753) or 678.574.5070
Determinants of Performance
 MOTIVATION 1 Determinants of Performance Person: Ability Motivation Accurate Role Perceptions Situation: Environmental (Constraints and Facilitators) Performance 2 Fundamentals of Motivation Motivation
MOTIVATION 1 Determinants of Performance Person: Ability Motivation Accurate Role Perceptions Situation: Environmental (Constraints and Facilitators) Performance 2 Fundamentals of Motivation Motivation
Organization/Individual Relations and Retention
 ROBERT L. MATHIS JOHN H. JACKSON Chapter 3 Organization/Individual Relations and Retention Presented by: Prof. Dr. Deden Mulyana, SE.,M,Si. SECTION 1 Nature of Human Resource Management http://www.deden08m.com
ROBERT L. MATHIS JOHN H. JACKSON Chapter 3 Organization/Individual Relations and Retention Presented by: Prof. Dr. Deden Mulyana, SE.,M,Si. SECTION 1 Nature of Human Resource Management http://www.deden08m.com
AVAILABILITY, RESPONSIVENESS, CONTINUITY (ARC):
 AVAILABILITY, RESPONSIVENESS, CONTINUITY (ARC): IMPROVING CLIENTS LIVES: RESEARCH AND PRACTICE INNOVATION VIA THE ARC MODEL OF ORGANIZATIONAL EFFECTIVENESS Anthony L Hemmelgarn, Ph.D. Children s Mental
AVAILABILITY, RESPONSIVENESS, CONTINUITY (ARC): IMPROVING CLIENTS LIVES: RESEARCH AND PRACTICE INNOVATION VIA THE ARC MODEL OF ORGANIZATIONAL EFFECTIVENESS Anthony L Hemmelgarn, Ph.D. Children s Mental
Project Human Resource and Communication Management. Prof. Dr. Daning Hu Department of Informatics University of Zurich
 Project Human Resource and Communication Management Prof. Dr. Daning Hu Department of Informatics University of Zurich Now you tell me.. n What are the things a Project Manager needs to do regarding Human
Project Human Resource and Communication Management Prof. Dr. Daning Hu Department of Informatics University of Zurich Now you tell me.. n What are the things a Project Manager needs to do regarding Human
Examining user acceptance of SMS: An empirical study in China and Hong Kong
 Association for Information Systems AIS Electronic Library (AISeL) PACIS 2008 Proceedings Pacific Asia Conference on Information Systems (PACIS) July 2008 Examining user acceptance of SMS: An empirical
Association for Information Systems AIS Electronic Library (AISeL) PACIS 2008 Proceedings Pacific Asia Conference on Information Systems (PACIS) July 2008 Examining user acceptance of SMS: An empirical
Ethnocentric Strategies in Information Security Management
 Association for Information Systems AIS Electronic Library (AISeL) AMCIS 2006 Proceedings Americas Conference on Information Systems (AMCIS) December 2006 Ethnocentric Strategies in Information Security
Association for Information Systems AIS Electronic Library (AISeL) AMCIS 2006 Proceedings Americas Conference on Information Systems (AMCIS) December 2006 Ethnocentric Strategies in Information Security
A summary of a doctoral thesis written under the scientific guidance of prof. Grażyna Gruszczyńska-Malec
 A summary of a doctoral thesis written under the scientific guidance of prof. Grażyna Gruszczyńska-Malec Title: PERCEIVED ORGANIZATIONAL SUPPORT. HIGH PERFORMANCE WORK SYSTEM PERSPECTIVE Author: MA INTRODUCTION
A summary of a doctoral thesis written under the scientific guidance of prof. Grażyna Gruszczyńska-Malec Title: PERCEIVED ORGANIZATIONAL SUPPORT. HIGH PERFORMANCE WORK SYSTEM PERSPECTIVE Author: MA INTRODUCTION
The Influential Factors of Organization Adoption of Egovernment Cloud
 2017 International Conference on Financial Management, Education and Social Science (FMESS 2017) The Influential Factors of Organization Adoption of Egovernment Cloud Wei Wang1, 3, a, Yiming Liu1, 3, b,
2017 International Conference on Financial Management, Education and Social Science (FMESS 2017) The Influential Factors of Organization Adoption of Egovernment Cloud Wei Wang1, 3, a, Yiming Liu1, 3, b,
UNIVERSITY OF TEXAS AT AUSTIN EMPLOYEE ENGAGEMENT GUIDE
 UNIVERSITY OF TEXAS AT AUSTIN EMPLOYEE ENGAGEMENT GUIDE WHAT IS THE SURVEY OF EMPLOYEE ENGAGEMENT? The Survey of Employee Engagement facilitated by the UT Austin Institute for Organizational Excellence,
UNIVERSITY OF TEXAS AT AUSTIN EMPLOYEE ENGAGEMENT GUIDE WHAT IS THE SURVEY OF EMPLOYEE ENGAGEMENT? The Survey of Employee Engagement facilitated by the UT Austin Institute for Organizational Excellence,
Running head: Literature Review 1
 Running head: Literature Review 1 Literature Review: (Conflict in Corporate Workplaces: Includes Healthcare, Education, General Businesses) (Michael E. Markgraf) Liberty University 2 Abstract This paper
Running head: Literature Review 1 Literature Review: (Conflict in Corporate Workplaces: Includes Healthcare, Education, General Businesses) (Michael E. Markgraf) Liberty University 2 Abstract This paper
The effective recruitment and selection practices of organizations in the financial sector operating in the Slovak republic
 The effective recruitment and selection practices of organizations in the financial sector operating in the Slovak republic Ľuba Tomčíková University of Prešov in Prešov Department of management Ul. 17
The effective recruitment and selection practices of organizations in the financial sector operating in the Slovak republic Ľuba Tomčíková University of Prešov in Prešov Department of management Ul. 17
Motivating Employees in Academic Libraries in Tough Times
 Motivating Employees in Academic Libraries in Tough Times Abstract Academic library HR management is facing many interesting challenges. With an increasing number of M.L.S. graduates seeking positions
Motivating Employees in Academic Libraries in Tough Times Abstract Academic library HR management is facing many interesting challenges. With an increasing number of M.L.S. graduates seeking positions
The Role and Impact of Cultural Dimensions on Information Systems Security in Saudi Arabia National Health Service
 The Role and Impact of Cultural Dimensions on Information Systems Security in Saudi Arabia National Health Service Saleh Alumaran, Giampaolo Bella and Feng Chen Software Technology Research Laboratory
The Role and Impact of Cultural Dimensions on Information Systems Security in Saudi Arabia National Health Service Saleh Alumaran, Giampaolo Bella and Feng Chen Software Technology Research Laboratory
HR Transformation: Building Capacity, Work Performance and Community. Presenters. Today s Presentation. Jay Canetto.
 HR Transformation: Building Capacity, Work Performance and Community 2008 IPMA-HR International Training Conference and Exposition October 20, 2008 Presenters Jay Canetto Director of Personnel New York
HR Transformation: Building Capacity, Work Performance and Community 2008 IPMA-HR International Training Conference and Exposition October 20, 2008 Presenters Jay Canetto Director of Personnel New York
CREATIVITY AUDIT QUESTIONNAIRE
 CREATIVITY AUDIT QUESTIONNAIRE CREATIVITY AUDIT This audit aims to record your opinion about creativity at work in order to better address your organizational needs in terms of creativity and innovation.
CREATIVITY AUDIT QUESTIONNAIRE CREATIVITY AUDIT This audit aims to record your opinion about creativity at work in order to better address your organizational needs in terms of creativity and innovation.
Course Learning Outcomes for Unit VI
 UNIT VI STUDY GUIDE Motivation and Leadership Reading Assignment Chapter 13: Motivation and Performance Chapter 14: Leadership Suggested Reading See information below. Learning Activities (Non-Graded)
UNIT VI STUDY GUIDE Motivation and Leadership Reading Assignment Chapter 13: Motivation and Performance Chapter 14: Leadership Suggested Reading See information below. Learning Activities (Non-Graded)
A Study of Intention to Use Tablet PC E-books from a Perspective. Combining TAM and IDT
 A Study of Intention to Use Tablet PC E-books from a Perspective Combining TAM and IDT MEI-YING WU, HUNG-CHI PAN Department of Information Management Chung-Hua University No.707, Sec.2, WuFu Road, Hsinchu
A Study of Intention to Use Tablet PC E-books from a Perspective Combining TAM and IDT MEI-YING WU, HUNG-CHI PAN Department of Information Management Chung-Hua University No.707, Sec.2, WuFu Road, Hsinchu
Incentivizing Survey Participation: Best Practices and Recommendations DePaul University Division of Student Affairs Joanne Kang, Assessment Intern
 Incentivizing Survey Participation: Best Practices and Recommendations DePaul University Division of Student Affairs Joanne Kang, Assessment Intern July 2016 2 Introduction The use of incentives to increase
Incentivizing Survey Participation: Best Practices and Recommendations DePaul University Division of Student Affairs Joanne Kang, Assessment Intern July 2016 2 Introduction The use of incentives to increase
Differential Effects of Hindrance and Challenge Stressors on Innovative Performance
 Differential Effects of Hindrance and Challenge Stressors on Innovative Performance Usman Raja, PhD and Muhammad Abbas Abstract The paper investigated the differential effects of challenge related stressors
Differential Effects of Hindrance and Challenge Stressors on Innovative Performance Usman Raja, PhD and Muhammad Abbas Abstract The paper investigated the differential effects of challenge related stressors
