Fraudulent Behavior Forecast in Telecom Industry Based on Data Mining Technology
|
|
|
- Cody Austin
- 6 years ago
- Views:
Transcription
1 Fraudulent Behavior Forecast in Telecom Industry Based on Data Mining Technology Sen Wu Naidong Kang Liu Yang School of Economics and Management University of Science and Technology Beijing ABSTRACT Outlier analysis in data mining is to find the deviation and abnormal data in the databases. By finding and explaining the outliers, we can apply them to detecting the business frauds effectively. This paper analyzes the common characteristics of fraudulent behavior of customers in telecom industry systematically. Based on the outlier-finding by clustering in data mining, we propose an effective solution to forecast the customers who are maliciously in arrears. Coupled with the actual application of forecasting the customers who are maliciously in arrears in telecom industry, we propose the specific method to forecast this kind of customers by using Kohonen neural network clustering algorithm. INTRODUCTION The behavior of malicious arrearage in telecom industry in China is common and has lasted for a long time. The malicious arrearage increases the bad account ratio in telecom companies and makes the profit untrue and the state-owed assets lost. Telecom industry is data-intensive. After many years of development, telecom companies have the detail records of both the customers and the real-time calls. Therefore, by analyzing the data on hand, companies can know the purchase habits and the nature attributes of customers. Based on the analysis of customers behavior, credit and risk, operators can build a system to avoid frauds. Through this system, operators can manage customers on-line at any time. Once a customer has abnormal phone call, operator gives alarm to service staff to take necessary actions, in case the customer leaves in arrears maliciously. Based on the clustering technique in data mining, this paper focuses on the problem of finding abnormal outliers in large data set by using Kohonen neural network clustering algorithm, and gives the specific method to forecast the behavior of malicious arrearage. Clustering Technique in Data Mining (1) Knowledge discovery by clustering From business aspect, data mining is a new method to process business information. Its main characteristic is that it selects, transforms and analyzes transaction data in business databases, extracts crucial information to help making business decisions. A common problem all companies face is that valuable information is limited though the data is rich. Therefore it is just like to collect gold from mine for company to gain information from the large data set, so data mining gets its name(han and Kamber, 2001). Company can enhance its competency by deep analysis of the information. Outlier detection in data mining is to find the deviation in databases, this kind of exploration of deviation or abnormal pattern has important meaning in related fields such as forecasting the customers who are maliciously in arrears in telecom industry. Supported by Program for New Century Excellent Talents in University (NCET ) Communications of the IIMA Volume 7 Issue 4
2 We could use clustering to accomplish the outlier detection. Knowledge discovery by clustering is one of the important functions of data mining. From the aspect of data mining, clustering research extracts valuable knowledge from large data sets intelligently and automatically. Knowledge discovery by clustering was proposed along with the development of databases and the emergence of data mining and Knowledge discovery technology. Knowledge discovery by clustering is applied in many areas, such as: forecast of bankruptcy, pattern recognition, marketing, market segmentation and so on. The abnormal data implies outliers in clustering. Through the finding and explaining of the outliers, we can extract the features of abnormal data, so apply them to detect business frauds effectively. (2) Kohonen neural network clustering algorithm We compared three kinds of clustering algorithms by experiment, Kohonen neural network algorithm, two-step clustering algorithm, and K-means algorithm. We figure out that Kohonen neural network algorithm is the most effective algorithm to find outliers. Kohonen neural network was proposed in It is also called self-organizing feature maps neural network clustering method. It gets the clusters of data set by using iterative algorithm to optimize the objective function (Li, Deng and Li, 2004; Yuan, 2000; Chen, 1996). Kohonen neural network is one of the most popular neural network methods for cluster analysis. Its goal is to represent all points in a high-dimensional source space by points in a low-dimensional (usually 2-D or 3-D) target space, such that the distance and proximity relationships are preserved as much as possible. The method is particularly useful when a nonlinear mapping is inherent in the problem itself (Han and Kamber, 2001). Kohonen neural network is a two layers feed-forward neural network, it has input layer and output layer. The number of neurons of input layer is M, which amounts to the dimension of input sample vector. The neurons of output layer are competitive output neurons, whose values are in {0, 1}. After self-organizing learning, Kohonen neural network makes the density of the connection weight vectors consistent with the probability distribution of input model, which means the density of the connection weight vectors could reflect the statistical features of input model. The layout of neurons in output layer has many forms, the typical one is two-dimension plane matrix (Yan and Zhang, 2000; Malone, etc., 2005). (1) Outlier finding BASIC IDEAS TO FORECAST THE MALICIOUS ARREARAGE To forecast the behavior of malicious arrearage in telecom industry based on outlier detection in data mining, is to find the abnormal customers from the large customer data set who have high-level call fees in short period of time and leave in arrears at last. In order to find the outliers, we first capture the features of the customers who leave network in arrears, then build model and apply it to analyze the current customers by comparing the features of current calling behavior of customers with those of malicious arrearage finally, detect the customers who will be possibly in arrears, warn them and suspend service to them (Wang, 2004). Classification is widely used for prediction in data mining, but when the ratio of target customer is small, it will miss many important rules by using classification, so the forecast result is poor. Outliers are the seldom abnormal case in data set. Outlier finding is a special and crucial application in data mining. We view the customers who are maliciously in arrears as outliers in the entire customer set. Based on Kohonen neural network clustering, we can find the outliers before classification in order to improve the quality of classification and forecast. The process of clustering can extract the outliers from the entire data set, but cannot state the features of this group, so we still have to use the decision tree of classification to extract the classification rules of this special group, and apply them to the process of business forecast. (2) Main steps to forecast the malicious arrearage We use a data mining tool Clementine (a data mining tool of SPSS) and Kohonen neural network clustering algorithm to analyze the data of training set, in order to find customer groups which are maliciously in arrears and Communications of the IIMA Volume 7 Issue 4
3 the basic features of these groups, then we will use these features to forecast the customers who may be maliciously in arrears and the probability of malicious arrearage happens so that we can ask for calling fees before this kind of customers leave the network. In order to evaluate the effectiveness of the model, we will test the model by test set different from training set. We follow the standard process of data mining CRISP-DM (Wu, Gao and Bastian, 2003), the specific steps are as follows: Step1: Business understanding: Data source is prepared in order to build the model for analysis; according to the business rules and requirements of telecom companies, clear definition is given of customers who are maliciously in arrears, and the entire customers are divided into target customers and unrelated customers. Step 2: Data understanding: Relevant data is selected based on the business understanding. By processing the bills and detail records of customers in a regular time period, we connect the fees of calling, time of calling, duration of calling, type of calling with information table and arrears table of customer and build feature records set of target customers. Step 3: Data preprocessing: it is the most time-consuming process in data mining. Its goal is to transform the original data into reliable data for mining (Corinne, etc., 2001). In the subject of forecasting and analysis of the malicious cheating, data preprocessing includes sampling, setting the label of cheat, the feature field calculation and so on. Step 4: Modeling: The sample customers are cluttered by Kohonen neural network algorithm in order to find the target customers which have features of malicious arrearage. We can extract the classification rules of target customers and build the model to forecast malicious arrearage. Step 5: Evaluation: adjusting and optimizing the model, evaluating the effectiveness of forecast model by test data set. Step 6: Implement: we forecast the behavior of malicious arrearage in the coming period by the forecast model, give the probability of malicious arrearage, and show it to telecom supervisor. (1) Target customer definition DATA PREPARATION BEFORE MODELING In order to forecast cheat, we should define the target customers beforehand. The target customers are the ones who are in debt and leave the network with high-level calling fees not paid. According to their information of consuming, account, state-changing, we forecast the probability of them to become the target customers in the later months. Customers may be halted out of services for arrearage for some reasons by the telecom companies, but they will pay for the bill in time. These customers are not target customers. We discover that 96.6% of the customers, who are halted out of services for more than four months, will not pay for the bill in the fifth month. And we should focus on the customers whose amounts of debts are high. If we could make them pay for the bill, we can recover major losses of the operators. We assume that the forecast period is one month. The customers who are maliciously in arrears, or the target customers, are described as follows: In forecast period, their states are normal and the bills for each customer are no less than 200 yuan, but they always halt with bills not paid or leave network in debt in the next four months. (2) Setting the time window The goal of forecast is to find the target customers before they leave the network. If the alarming point is too early, the accuracy is lower; on the contrary, if the alarming point is too late, we have no time to take action. Therefore our goal is to find the inclination of customers to leave network 2 or 3 months ahead. Based on the definition of target customers given above, we use the data in July, 2006 and the states of these customers in November, 2006, to build the model. That means if we want to forecast the customers who leave network in arrears in November, we can know it in August, the forecast depends on the data before August. Communications of the IIMA Volume 7 Issue 4
4 Indexes of the time window are as follows: (1) data window: July, 2006; (2) forecast window: November, 2006; (3) delay period: three months. (3) Data understanding Given the specific business goal, data understanding collects all the internal and external data relevant to the object of business. Then we check the quality of data and find subsets of data which are interesting and contain information. In the subject of forecasting the customers who are maliciously in arrears, we extract customers basic information table, bill of month, detailed records of calling, table of arrears and table of state-changing as our original data tables. From these tables, we can get the original data to forecast the customers who are maliciously in arrears. The original data includes: customer s ID, gender, age, time in network, state, fees of long-distant phone call, fees of roaming, lasting time of phone call, times of phone call, fees in arrears, service change type and so on. (4) Setting the label of cheat According to the standard of time window, we correlate the customer information tables from July to November. We choose the customer who joined the network before July and his/her state was normal and he/she spent more the 200 yuan in calling in July. We choose their states from August to November using customer s ID as foreign key. We add a field of flag as attribute of cheat in the tables. If the customer whose state is out of service and leave network in arrears, the value of flag is 1, which identifies the target customers; otherwise the flag is 0, which denotes that the customer is not our target. (5) Feature field selection We analyzed the amount of customer s spending in consecutive months and found that the range of cost fluctuates, but the range is small. Before the behavior of malicious arrearage conducted, the amount of customer s spending would rise dramatically compared with before. Therefore we create a derived variable, using the ratio of rising range of spending to the standard deviation of the amount of spending to measure the raised spending is normal or not. We call it index of spending. The formula is as below: Index of spending of the month n+1 M n+ 1 M S = n+ 1 n i= 1 ( M i M ) 2 (1) M i is the amount of spending in the month i, M is average amount of spending by month, M = n i=1 M n i (2) IMPLEMENT OF THE MODEL TO FORECAST MALICIOUS ARREARAGE (1) Clustering analysis The customers who are maliciously in arrears are outliers. Therefore when we set the parameters of the model, we should set enough classes to reflect the features of outliers so that the outliers will not submerged in the classes. We set 70 classes (the two-dimension matrix, length is 10, width is 7). The result of clustering analysis is show as figure 1. The black spots represent cheating customers, the gray spots represent the normal customers. A couple of Communications of the IIMA Volume 7 Issue 4
5 horizontal and vertical coordinates represent one class. In the picture, the black spots are mainly in the cluster (0, 6) and cluster (9, 6). Figure 1: Distribution map of the result of clustering analysis. (2) Extracting the rule of feature We get the cluster information of customers who are maliciously in arrears by using clustering analysis. If we want to acquire the main features of customers in that cluster, we should use decision tree of classification algorithm to attain the features of the target customer group. For example, a customer is target customer, if he/she has long-distant phone call with a particular number for a lot of times, the total time of calling is more than seconds or about 3.27 hours, he/she was in the network less than 6 months, and the index of spending is more than (3) Evaluating the effectiveness of the model We need to evaluate the forecasting effectiveness of the model by using test set. We can calculate the confusion matrix based on the test set. Table 1: Forecasting Effectiveness Forecast not in arrears 0 Forecast in arrears 1 Actually not in arrears 0 A B Actually in arrears 1 C D Accuracy rate of forecasting malicious arrearage = D/ (B+D) Accuracy rate of forecasting not in arrears maliciously = A/ (A+C) Hitting rate of forecasting malicious arrearage = D/(C+D) Hitting rate of forecasting not in arrears maliciously = A/ (A+B) (4) Application of the model Communications of the IIMA Volume 7 Issue 4
6 The model is a classifier. We can forecast the target customers by it. If the probability of a customer to be our target customer is higher than a given value, we can suspect that the customer inclines to cheat and take necessary action in order to reduce the probability of malicious arrearage and to effectively protect the profits of telecom companies. Because the parameters of the model are retained by historical data the model will be old after a few months. We can calculate the accuracy rate and hitting rate by comparing the target customers we forecasted 2 or 3 months ahead with the customers who actually leave the network. When the two rates decline, we should retrain and adjust the model. CONCLUSION In this paper, we apply Kohonen neural network clustering algorithm to the analysis of forecasting the customers who are maliciously in arrears in telecom industry. The main contents and results of the research are: (1) Data mining technology is used to forecast the cheat in telecom industry based on Kohonen neural network clustering algorithm. And the main steps are given to accomplish the task of forecasting the customers who are maliciously in arrears. (2) Following the CRISP-DM data mining model, we give the definition of target customers who are maliciously in arrears and the model of data extracting. And the specific methods are proposed to build, evaluate, and apply the model. (3) We find the outliers by using Kohonen neural network clustering algorithm, and furthermore extract the consumption features of target customers. A forecasting system is developed to find the customers who are maliciously in arrears for a telecom company. REFERENCES Chen, M. (1996). Neural Network Model. Dalian University of Technology Press. Dalian. Corinne, B., etc.. (2001). Mining Your Own Business in Telecoms Using DB2 Intelligent Miner for Data. IBM RedBooks, Malone, J., etc.. (2005). Data mining Using Rule Extraction from Kohonen Self-organising Maps. Neural Comput & Applic 15: Han, J., Kamber, M. (2001). Data Mining Concepts and Techniques. Academic Press, New York. Li, Z., Deng, Q. and Li, H. (2004). Kohonen SOFM Neural Network Evolution and Research. Computer Engineering and Design Wang, Y. (2004). The Study on Data Warehouse and Data Mining in Telecom industry Management Analysis and Application. College of Computer Science, Chongqing University. Chongqing. Wu, S., Gao, X. and Bastian, M. (2003). Data Warehousing and Data Mining. Metallurgical Industry Press. Beijing. Yan, P., Zhang, Ch. (2000). Artificial Neuron Network and Simulated Evolution Computing. Tsinghua University Press. Beijing. Yuan, C. (2000). Artificial Neuron Network and Application. Tsinghua University Press. Beijing. Communications of the IIMA Volume 7 Issue 4
PREDICTING EMPLOYEE ATTRITION THROUGH DATA MINING
 PREDICTING EMPLOYEE ATTRITION THROUGH DATA MINING Abbas Heiat, College of Business, Montana State University, Billings, MT 59102, aheiat@msubillings.edu ABSTRACT The purpose of this study is to investigate
PREDICTING EMPLOYEE ATTRITION THROUGH DATA MINING Abbas Heiat, College of Business, Montana State University, Billings, MT 59102, aheiat@msubillings.edu ABSTRACT The purpose of this study is to investigate
Session 15 Business Intelligence: Data Mining and Data Warehousing
 15.561 Information Technology Essentials Session 15 Business Intelligence: Data Mining and Data Warehousing Copyright 2005 Chris Dellarocas and Thomas Malone Adapted from Chris Dellarocas, U. Md. Outline
15.561 Information Technology Essentials Session 15 Business Intelligence: Data Mining and Data Warehousing Copyright 2005 Chris Dellarocas and Thomas Malone Adapted from Chris Dellarocas, U. Md. Outline
DATA MINING: A BRIEF INTRODUCTION
 DATA MINING: A BRIEF INTRODUCTION Matthew N. O. Sadiku, Adebowale E. Shadare Sarhan M. Musa Roy G. Perry College of Engineering, Prairie View A&M University Prairie View, USA Abstract Data mining may be
DATA MINING: A BRIEF INTRODUCTION Matthew N. O. Sadiku, Adebowale E. Shadare Sarhan M. Musa Roy G. Perry College of Engineering, Prairie View A&M University Prairie View, USA Abstract Data mining may be
Chapter 8 Analytical Procedures
 Slide 8.1 Principles of Auditing: An Introduction to International Standards on Auditing Chapter 8 Analytical Procedures Rick Hayes, Hans Gortemaker and Philip Wallage Slide 8.2 Analytical procedures Analytical
Slide 8.1 Principles of Auditing: An Introduction to International Standards on Auditing Chapter 8 Analytical Procedures Rick Hayes, Hans Gortemaker and Philip Wallage Slide 8.2 Analytical procedures Analytical
The Application of Data Mining Technology in Building Energy Consumption Data Analysis
 The Application of Data Mining Technology in Building Energy Consumption Data Analysis Liang Zhao, Jili Zhang, Chongquan Zhong Abstract Energy consumption, in particular those involving public buildings,
The Application of Data Mining Technology in Building Energy Consumption Data Analysis Liang Zhao, Jili Zhang, Chongquan Zhong Abstract Energy consumption, in particular those involving public buildings,
IBM SPSS Modeler Personal
 IBM SPSS Modeler Personal Make better decisions with predictive intelligence from the desktop Highlights Helps you identify hidden patterns and trends in your data to predict and improve outcomes Enables
IBM SPSS Modeler Personal Make better decisions with predictive intelligence from the desktop Highlights Helps you identify hidden patterns and trends in your data to predict and improve outcomes Enables
Data Mining in CRM THE CRM STRATEGY
 CHAPTER ONE Data Mining in CRM THE CRM STRATEGY Customers are the most important asset of an organization. There cannot be any business prospects without satisfied customers who remain loyal and develop
CHAPTER ONE Data Mining in CRM THE CRM STRATEGY Customers are the most important asset of an organization. There cannot be any business prospects without satisfied customers who remain loyal and develop
Achieve Better Insight and Prediction with Data Mining
 Clementine 12.0 Specifications Achieve Better Insight and Prediction with Data Mining Data mining provides organizations with a clearer view of current conditions and deeper insight into future events.
Clementine 12.0 Specifications Achieve Better Insight and Prediction with Data Mining Data mining provides organizations with a clearer view of current conditions and deeper insight into future events.
RFM analysis for decision support in e-banking area
 RFM analysis for decision support in e-banking area VASILIS AGGELIS WINBANK PIRAEUS BANK Athens GREECE AggelisV@winbank.gr DIMITRIS CHRISTODOULAKIS Computer Engineering and Informatics Department University
RFM analysis for decision support in e-banking area VASILIS AGGELIS WINBANK PIRAEUS BANK Athens GREECE AggelisV@winbank.gr DIMITRIS CHRISTODOULAKIS Computer Engineering and Informatics Department University
Application of neural network to classify profitable customers for recommending services in u-commerce
 Application of neural network to classify profitable customers for recommending services in u-commerce Young Sung Cho 1, Song Chul Moon 2, and Keun Ho Ryu 1 1. Database and Bioinformatics Laboratory, Computer
Application of neural network to classify profitable customers for recommending services in u-commerce Young Sung Cho 1, Song Chul Moon 2, and Keun Ho Ryu 1 1. Database and Bioinformatics Laboratory, Computer
Chapter 5 Evaluating Classification & Predictive Performance
 Chapter 5 Evaluating Classification & Predictive Performance Data Mining for Business Intelligence Shmueli, Patel & Bruce Galit Shmueli and Peter Bruce 2010 Why Evaluate? Multiple methods are available
Chapter 5 Evaluating Classification & Predictive Performance Data Mining for Business Intelligence Shmueli, Patel & Bruce Galit Shmueli and Peter Bruce 2010 Why Evaluate? Multiple methods are available
Approaching an Analytical Project. Tuba Islam, Analytics CoE, SAS UK
 Approaching an Analytical Project Tuba Islam, Analytics CoE, SAS UK Approaching an Analytical Project Starting with questions.. What is the problem you would like to solve? Why do you need analytics? Which
Approaching an Analytical Project Tuba Islam, Analytics CoE, SAS UK Approaching an Analytical Project Starting with questions.. What is the problem you would like to solve? Why do you need analytics? Which
A HYBRID MODERN AND CLASSICAL ALGORITHM FOR INDONESIAN ELECTRICITY DEMAND FORECASTING
 A HYBRID MODERN AND CLASSICAL ALGORITHM FOR INDONESIAN ELECTRICITY DEMAND FORECASTING Wahab Musa Department of Electrical Engineering, Universitas Negeri Gorontalo, Kota Gorontalo, Indonesia E-Mail: wmusa@ung.ac.id
A HYBRID MODERN AND CLASSICAL ALGORITHM FOR INDONESIAN ELECTRICITY DEMAND FORECASTING Wahab Musa Department of Electrical Engineering, Universitas Negeri Gorontalo, Kota Gorontalo, Indonesia E-Mail: wmusa@ung.ac.id
Data Analytics with MATLAB Adam Filion Application Engineer MathWorks
 Data Analytics with Adam Filion Application Engineer MathWorks 2015 The MathWorks, Inc. 1 Case Study: Day-Ahead Load Forecasting Goal: Implement a tool for easy and accurate computation of dayahead system
Data Analytics with Adam Filion Application Engineer MathWorks 2015 The MathWorks, Inc. 1 Case Study: Day-Ahead Load Forecasting Goal: Implement a tool for easy and accurate computation of dayahead system
Business Intelligence, Analytics, and Predictive Modeling Kim Gaddy
 Business Intelligence, Analytics, and Predictive Modeling Kim Gaddy Business intelligence and analytics C O M P E T I T I V E A D V A N T A G E Optimization Predictive Modeling Forecasting/ extrapolation
Business Intelligence, Analytics, and Predictive Modeling Kim Gaddy Business intelligence and analytics C O M P E T I T I V E A D V A N T A G E Optimization Predictive Modeling Forecasting/ extrapolation
Using Predictive Analytics to Detect Contract Fraud, Waste, and Abuse Case Study from U.S. Postal Service OIG
 Using Predictive Analytics to Detect Contract Fraud, Waste, and Abuse Case Study from U.S. Postal Service OIG MACPA Government & Non Profit Conference April 26, 2013 Isaiah Goodall, Director of Business
Using Predictive Analytics to Detect Contract Fraud, Waste, and Abuse Case Study from U.S. Postal Service OIG MACPA Government & Non Profit Conference April 26, 2013 Isaiah Goodall, Director of Business
A Trust Evaluation Model for Social Commerce Based on BP Neural Network
 Journal of Data Analysis and Information Processing, 2016, 4, 147-158 http://www.scirp.org/journal/jdaip ISSN Online: 2327-7203 ISSN Print: 2327-7211 A Trust Evaluation Model for Social Commerce Based
Journal of Data Analysis and Information Processing, 2016, 4, 147-158 http://www.scirp.org/journal/jdaip ISSN Online: 2327-7203 ISSN Print: 2327-7211 A Trust Evaluation Model for Social Commerce Based
SAS Machine Learning and other Analytics: Trends and Roadmap. Sascha Schubert Sberbank 8 Sep 2017
 SAS Machine Learning and other Analytics: Trends and Roadmap Sascha Schubert Sberbank 8 Sep 2017 How Big Analytics will Change Organizations Optimization and Innovation Optimizing existing processes Customer
SAS Machine Learning and other Analytics: Trends and Roadmap Sascha Schubert Sberbank 8 Sep 2017 How Big Analytics will Change Organizations Optimization and Innovation Optimizing existing processes Customer
The application of data mining technology in e-commerce
 5th International Conference on Education, Management, Information and Medicine (EMIM 2015) The application of data mining technology in e-commerce Li Yan Weifang Vocational College,ShanDong WeiFang,261041,China
5th International Conference on Education, Management, Information and Medicine (EMIM 2015) The application of data mining technology in e-commerce Li Yan Weifang Vocational College,ShanDong WeiFang,261041,China
Marketing & Big Data
 Marketing & Big Data Surat Teerakapibal, Ph.D. Lecturer in Marketing Director, Doctor of Philosophy Program in Business Administration Thammasat Business School What is Marketing? Anti-Marketing Marketing
Marketing & Big Data Surat Teerakapibal, Ph.D. Lecturer in Marketing Director, Doctor of Philosophy Program in Business Administration Thammasat Business School What is Marketing? Anti-Marketing Marketing
What is Business Intelligence and Performance Management
 What is Business Intelligence and Performance Management And Why Should I Care? Solve your business puzzles with Intelligent Solutions Claudia Imhoff, Ph.D. Intelligent Solutions, Inc. www.intelsols.com
What is Business Intelligence and Performance Management And Why Should I Care? Solve your business puzzles with Intelligent Solutions Claudia Imhoff, Ph.D. Intelligent Solutions, Inc. www.intelsols.com
Who Are My Best Customers?
 Technical report Who Are My Best Customers? Using SPSS to get greater value from your customer database Table of contents Introduction..............................................................2 Exploring
Technical report Who Are My Best Customers? Using SPSS to get greater value from your customer database Table of contents Introduction..............................................................2 Exploring
Research on Regional Logistics Industry Development Strategy Based on System Dynamics: Take Changzhou as a Case
 3rd International Conference on Management Science and Management Innovation (MSMI 2016) Research on Regional Logistics Industry Development Strategy Based on System Dynamics: Take Changzhou as a Case
3rd International Conference on Management Science and Management Innovation (MSMI 2016) Research on Regional Logistics Industry Development Strategy Based on System Dynamics: Take Changzhou as a Case
Genetic Algorithms-Based Model for Multi-Project Human Resource Allocation
 Genetic Algorithms-Based Model for Multi-Project Human Resource Allocation Abstract Jing Ai Shijiazhuang University of Applied Technology, Shijiazhuang 050081, China With the constant development of computer
Genetic Algorithms-Based Model for Multi-Project Human Resource Allocation Abstract Jing Ai Shijiazhuang University of Applied Technology, Shijiazhuang 050081, China With the constant development of computer
Data Mining: Next Generation Challenges and Future Directions
 Data Mining: Next Generation Challenges and Future Directions Dipti Verma and Rakesh Nashine Abstract Data mining is the process of discovering actionable information from large sets of data. Data mining,
Data Mining: Next Generation Challenges and Future Directions Dipti Verma and Rakesh Nashine Abstract Data mining is the process of discovering actionable information from large sets of data. Data mining,
Data Mining Research on Time Series of E-commerce Transaction. Lanzhou, China.
 , pp.9-18 http://dx.doi.org/10.1457/ijunesst.014.7.1.0 Data Mining Research on Time Series of E-commerce Transaction Xiao Qiang 1,, He Rui-Chun 1 and Liao Hui 1 School of Traffic and Transportation, Lanzhou
, pp.9-18 http://dx.doi.org/10.1457/ijunesst.014.7.1.0 Data Mining Research on Time Series of E-commerce Transaction Xiao Qiang 1,, He Rui-Chun 1 and Liao Hui 1 School of Traffic and Transportation, Lanzhou
Product Purchase Sequence Analyses By Using Horizontal Data Sorting Technique
 Purchase Sequence Analyses By Using Horizontal Data Sorting Technique TransUnion Canada Purchase Sequence Analyses By Using Horizontal Data Sorting Technique ABSTRACT Horizontal data sorting is a very
Purchase Sequence Analyses By Using Horizontal Data Sorting Technique TransUnion Canada Purchase Sequence Analyses By Using Horizontal Data Sorting Technique ABSTRACT Horizontal data sorting is a very
Advanced Analytics through the credit cycle
 Advanced Analytics through the credit cycle Alejandro Correa B. Andrés Gonzalez M. Introduction PRE ORIGINATION Credit Cycle POST ORIGINATION ORIGINATION Pre-Origination Propensity Models What is it?
Advanced Analytics through the credit cycle Alejandro Correa B. Andrés Gonzalez M. Introduction PRE ORIGINATION Credit Cycle POST ORIGINATION ORIGINATION Pre-Origination Propensity Models What is it?
Data Warehousing. and Data Mining. Gauravkumarsingh Gaharwar
 Data Warehousing 1 and Data Mining 2 Data warehousing: Introduction A collection of data designed to support decisionmaking. Term data warehousing generally refers to the combination of different databases
Data Warehousing 1 and Data Mining 2 Data warehousing: Introduction A collection of data designed to support decisionmaking. Term data warehousing generally refers to the combination of different databases
Week 1 Unit 4: Defining Project Success Criteria
 Week 1 Unit 4: Defining Project Success Criteria Business and data science project success criteria: reminder Business success criteria Describe the criteria for a successful or useful outcome to the project
Week 1 Unit 4: Defining Project Success Criteria Business and data science project success criteria: reminder Business success criteria Describe the criteria for a successful or useful outcome to the project
Use of Data Mining and Machine. Use of Data Mining and Machine. Learning for Fraud Detection. Learning for Fraud Detection. Welcome!
 Use of Data Mining and Machine Use of Data Mining and Machine Learning for Fraud Detection CPE PIN Code: UKLK Learning for Fraud Detection Welcome! Ramazan Isik, CFE, CIA, CRISC, CRMA Chief Audit Executive
Use of Data Mining and Machine Use of Data Mining and Machine Learning for Fraud Detection CPE PIN Code: UKLK Learning for Fraud Detection Welcome! Ramazan Isik, CFE, CIA, CRISC, CRMA Chief Audit Executive
The Combined Model of Gray Theory and Neural Network which is based Matlab Software for Forecasting of Oil Product Demand
 The Combined Model of Gray Theory and Neural Network which is based Matlab Software for Forecasting of Oil Product Demand Song Zhaozheng 1,Jiang Yanjun 2, Jiang Qingzhe 1 1State Key Laboratory of Heavy
The Combined Model of Gray Theory and Neural Network which is based Matlab Software for Forecasting of Oil Product Demand Song Zhaozheng 1,Jiang Yanjun 2, Jiang Qingzhe 1 1State Key Laboratory of Heavy
Data Mining Applications in Human Resources Management System
 Data Mining Applications in Human Resources Management System Hubei university of automotive technology, China, thinkpad.ibm@gmail.com Abstract This article applies data mining technology such as intelligent
Data Mining Applications in Human Resources Management System Hubei university of automotive technology, China, thinkpad.ibm@gmail.com Abstract This article applies data mining technology such as intelligent
RAID Collections. Datasheet. RAID Collections Datasheet 1
 RAID Collections Datasheet RAID Collections Datasheet 1 Improve your credit control and collections operations. The Solution RAID Collections manages and automates your credit control and collection operations
RAID Collections Datasheet RAID Collections Datasheet 1 Improve your credit control and collections operations. The Solution RAID Collections manages and automates your credit control and collection operations
SPM 8.2. Salford Predictive Modeler
 SPM 8.2 Salford Predictive Modeler SPM 8.2 The SPM Salford Predictive Modeler software suite is a highly accurate and ultra-fast platform for developing predictive, descriptive, and analytical models from
SPM 8.2 Salford Predictive Modeler SPM 8.2 The SPM Salford Predictive Modeler software suite is a highly accurate and ultra-fast platform for developing predictive, descriptive, and analytical models from
Progress Apama & Event Processing. Mark Palmer, Vice President of Event Processing
 Progress Apama & Event Processing Mark Palmer, Vice President of Event Processing Agenda (based on Symposium Guidelines) Major Characteristics of the Progress Approach Usage Scenarios Major Trends & Roadmap
Progress Apama & Event Processing Mark Palmer, Vice President of Event Processing Agenda (based on Symposium Guidelines) Major Characteristics of the Progress Approach Usage Scenarios Major Trends & Roadmap
The Training Strategy of Professional Core Competencies of Talents in Competitive Intelligence
 Research Journal of Applied Sciences, Engineering and Technology 5(16): 4088-4093, 2013 ISSN: 2040-7459; e-issn: 2040-7467 Maxwell Scientific Organization, 2013 Submitted: May 01, 2012 Accepted: December
Research Journal of Applied Sciences, Engineering and Technology 5(16): 4088-4093, 2013 ISSN: 2040-7459; e-issn: 2040-7467 Maxwell Scientific Organization, 2013 Submitted: May 01, 2012 Accepted: December
Data Warehouses & OLAP
 Riadh Ben Messaoud 1. The Big Picture 2. Data Warehouse Philosophy 3. Data Warehouse Concepts 4. Warehousing Applications 5. Warehouse Schema Design 6. Business Intelligence Reporting 7. On-Line Analytical
Riadh Ben Messaoud 1. The Big Picture 2. Data Warehouse Philosophy 3. Data Warehouse Concepts 4. Warehousing Applications 5. Warehouse Schema Design 6. Business Intelligence Reporting 7. On-Line Analytical
Value Proposition for Telecom Companies
 WWW.CUSTOMERS-DNA.COM VALUE PROPOSITION TELECOM COMPANIES Value Proposition for Telecom Companies Customer Intelligence in Telecoms CRM & CUSTOMER INTELLIGENCE SERVICES INFO@CUSTOMERS-DNA.COM 2 of 15 Value
WWW.CUSTOMERS-DNA.COM VALUE PROPOSITION TELECOM COMPANIES Value Proposition for Telecom Companies Customer Intelligence in Telecoms CRM & CUSTOMER INTELLIGENCE SERVICES INFO@CUSTOMERS-DNA.COM 2 of 15 Value
International Journal of Recent Trends in Electrical & Electronics Engg., Dec IJRTE ISSN:
 Market Basket Analysis of Sports Store using Association Rules Harpreet Kaur 1 and Kawaljeet Singh 2 1 Department of Computer Science, Punjabi University, Patiala, India. 2 University Computer Centre,
Market Basket Analysis of Sports Store using Association Rules Harpreet Kaur 1 and Kawaljeet Singh 2 1 Department of Computer Science, Punjabi University, Patiala, India. 2 University Computer Centre,
CLASSIFICATION OF WELDING DEFECTS IN RADIOGRAPHS USING TRAVERSAL PROFILES TO THE WELD SEAM
 CLASSIFICATION OF WELDING DEFECTS IN RADIOGRAPHS USING TRAVERSAL PROFILES TO THE WELD SEAM G. X. Padua 1, R. R. Silva 2, M. H. S. Siqueira 2, J. M. A. Rebello 2, L. P. Caloba 2 1 Petrobras, Rio de Janeiro,
CLASSIFICATION OF WELDING DEFECTS IN RADIOGRAPHS USING TRAVERSAL PROFILES TO THE WELD SEAM G. X. Padua 1, R. R. Silva 2, M. H. S. Siqueira 2, J. M. A. Rebello 2, L. P. Caloba 2 1 Petrobras, Rio de Janeiro,
The Research of Middleware Architecture of Intelligent Logistics System Based on SOA
 American Journal of Software Engineering and Applications 2015; 4(6): 115-120 Published online October 23, 2015 (http://www.sciencepublishinggroup.com/j/ajsea) doi: 10.11648/j.ajsea.20150406.13 ISSN: 2327-2473
American Journal of Software Engineering and Applications 2015; 4(6): 115-120 Published online October 23, 2015 (http://www.sciencepublishinggroup.com/j/ajsea) doi: 10.11648/j.ajsea.20150406.13 ISSN: 2327-2473
Is Machine Learning the future of the Business Intelligence?
 Is Machine Learning the future of the Business Intelligence Fernando IAFRATE : Sr Manager of the BI domain Fernando.iafrate@disney.com Tel : 33 (0)1 64 74 59 81 Mobile : 33 (0)6 81 97 14 26 What is Business
Is Machine Learning the future of the Business Intelligence Fernando IAFRATE : Sr Manager of the BI domain Fernando.iafrate@disney.com Tel : 33 (0)1 64 74 59 81 Mobile : 33 (0)6 81 97 14 26 What is Business
User Guide. User Guide to Recurring Billing and Storage. Setting up and using the Recurring Billing system
 User Guide User Guide to Recurring Billing and Storage Setting up and using the Recurring Billing system Version 3.7 (Fall 2008) User Guide to Recurring Billing and Storage Copyright Copyright 1997-2009
User Guide User Guide to Recurring Billing and Storage Setting up and using the Recurring Billing system Version 3.7 (Fall 2008) User Guide to Recurring Billing and Storage Copyright Copyright 1997-2009
Churn Prediction Model Using Linear Discriminant Analysis (LDA)
 IOSR Journal of Computer Engineering (IOSR-JCE) e-issn: 2278-0661,p-ISSN: 2278-8727, Volume 18, Issue 5, Ver. IV (Sep. - Oct. 2016), PP 86-93 www.iosrjournals.org Churn Prediction Model Using Linear Discriminant
IOSR Journal of Computer Engineering (IOSR-JCE) e-issn: 2278-0661,p-ISSN: 2278-8727, Volume 18, Issue 5, Ver. IV (Sep. - Oct. 2016), PP 86-93 www.iosrjournals.org Churn Prediction Model Using Linear Discriminant
The Analytical Revolution
 The Analytical Revolution Colin Shearer Global Executive, Advanced Analytic Solutions IBM Our world is becoming smarter Instrumented Interconnected Intelligent enabling organizations to make faster, better-informed
The Analytical Revolution Colin Shearer Global Executive, Advanced Analytic Solutions IBM Our world is becoming smarter Instrumented Interconnected Intelligent enabling organizations to make faster, better-informed
Multi-agent Modeling and Simulation for the Evolution of Enterprise IT Capability
 Journal of Computational Information Systems 7: 6 (2011) 1855-1862 Available at http://www.jofcis.com Multi-agent Modeling and Simulation for the Evolution of Enterprise IT Capability Bing BAI, Xiuquan
Journal of Computational Information Systems 7: 6 (2011) 1855-1862 Available at http://www.jofcis.com Multi-agent Modeling and Simulation for the Evolution of Enterprise IT Capability Bing BAI, Xiuquan
2 Maria Carolina Monard and Gustavo E. A. P. A. Batista
 Graphical Methods for Classifier Performance Evaluation Maria Carolina Monard and Gustavo E. A. P. A. Batista University of São Paulo USP Institute of Mathematics and Computer Science ICMC Department of
Graphical Methods for Classifier Performance Evaluation Maria Carolina Monard and Gustavo E. A. P. A. Batista University of São Paulo USP Institute of Mathematics and Computer Science ICMC Department of
BACKPROPAGATION NEURAL NETWORK AND CORRELATION-BASED FEATURE SELECTION FOR EARNING RESPONSE COEFFICIENT PREDICTION
 BACKPROPAGATION NEURAL NETWORK AND CORRELATION-BASED FEATURE SELECTION FOR EARNING RESPONSE COEFFICIENT PREDICTION 1 ABDUL SYUKUR, 2 CATUR SUPRIYANTO 1 Faculty of Economics and Business, University of
BACKPROPAGATION NEURAL NETWORK AND CORRELATION-BASED FEATURE SELECTION FOR EARNING RESPONSE COEFFICIENT PREDICTION 1 ABDUL SYUKUR, 2 CATUR SUPRIYANTO 1 Faculty of Economics and Business, University of
HOW ADVANCED INDUSTRIAL COMPANIES SHOULD APPROACH ARTIFICIAL-INTELLIGENCE STRATEGY
 Wouter Baan, Joshua Chang, and Christopher Thomas HOW ADVANCED INDUSTRIAL COMPANIES SHOULD APPROACH ARTIFICIAL-INTELLIGENCE STRATEGY November 2017 Leaders need to determine what AI can do for their company
Wouter Baan, Joshua Chang, and Christopher Thomas HOW ADVANCED INDUSTRIAL COMPANIES SHOULD APPROACH ARTIFICIAL-INTELLIGENCE STRATEGY November 2017 Leaders need to determine what AI can do for their company
An Integrated Data Mining and Behavioral Scoring Model for Analyzing Bank Customers Nan-Chen Hsieh
 An Integrated Data Mining and Behavioral Scoring Model for Analyzing Bank Customers Nan-Chen Hsieh Xin Ji (Jane) Institute of Financial Services Analytics University of Delaware Agenda Introduction Behavioural
An Integrated Data Mining and Behavioral Scoring Model for Analyzing Bank Customers Nan-Chen Hsieh Xin Ji (Jane) Institute of Financial Services Analytics University of Delaware Agenda Introduction Behavioural
BelVis PRO Enhancement Package (EHP)
 BelVis PRO EHP ENERGY MARKET SYSTEMS BelVis PRO Enhancement Package (EHP) Sophisticated methods for superior forecasts Methods for the highest quality of forecasts Tools to hedge the model stability Advanced
BelVis PRO EHP ENERGY MARKET SYSTEMS BelVis PRO Enhancement Package (EHP) Sophisticated methods for superior forecasts Methods for the highest quality of forecasts Tools to hedge the model stability Advanced
Lecture 1: What is Data Mining?
 Lecture 1: What is Data Mining? Alan Lee Department of Statistics STATS 784 Lecture 1 July 26, 2017 Page 1/34 Outline Housekeeping Introduction Data mining projects Statistical learning References Page
Lecture 1: What is Data Mining? Alan Lee Department of Statistics STATS 784 Lecture 1 July 26, 2017 Page 1/34 Outline Housekeeping Introduction Data mining projects Statistical learning References Page
Financial Crime Mitigation
 Financial Crime Mitigation A uniquely flexible range of intelligent, versatile solutions for financial institutions, large and small, to combat financial crime. Introduction Our Financial Crime Mitigation
Financial Crime Mitigation A uniquely flexible range of intelligent, versatile solutions for financial institutions, large and small, to combat financial crime. Introduction Our Financial Crime Mitigation
A Novel Intelligence Recommendation Model for Insurance Products with Consumer Segmentation
 Journal of Systems Science and Information Feb., 2014, Vol. 2, No. 1, pp. 16 28 A Novel Intelligence Recommendation Model for Insurance Products with Consumer Segmentation Wei XU School of Information,
Journal of Systems Science and Information Feb., 2014, Vol. 2, No. 1, pp. 16 28 A Novel Intelligence Recommendation Model for Insurance Products with Consumer Segmentation Wei XU School of Information,
MANAGING FRAUD ON TRAVEL BOOKINGS
 MANAGING FRAUD ON TRAVEL BOOKINGS EXECUTIVE SUMMARY The highly competitive travel industry faces a unique set of challenges around payments acceptance and fraud prevention. The sector is particularly susceptible
MANAGING FRAUD ON TRAVEL BOOKINGS EXECUTIVE SUMMARY The highly competitive travel industry faces a unique set of challenges around payments acceptance and fraud prevention. The sector is particularly susceptible
Data Processing of Thermal Power Plants Based on Dynamic Data Reconciliation
 1327 A publication of CHEMICAL ENGINEERING TRANSACTIONS VOL. 61, 2017 Guest Editors: Petar S Varbanov, Rongxin Su, Hon Loong Lam, Xia Liu, Jiří J Klemeš Copyright 2017, AIDIC Servizi S.r.l. ISBN 978-88-95608-51-8;
1327 A publication of CHEMICAL ENGINEERING TRANSACTIONS VOL. 61, 2017 Guest Editors: Petar S Varbanov, Rongxin Su, Hon Loong Lam, Xia Liu, Jiří J Klemeš Copyright 2017, AIDIC Servizi S.r.l. ISBN 978-88-95608-51-8;
MEASURING PUBLIC SATISFACTION FOR GOVERNMENT PROCESS REENGINEERING
 MEASURING PUBLIC SATISFACTION FOR GOVERNMENT PROCESS REENGINEERING Ning Zhang, School of Information, Central University of Finance and Economics, Beijing, P.R.C., zhangning@cufe.edu.cn Lina Pan, School
MEASURING PUBLIC SATISFACTION FOR GOVERNMENT PROCESS REENGINEERING Ning Zhang, School of Information, Central University of Finance and Economics, Beijing, P.R.C., zhangning@cufe.edu.cn Lina Pan, School
Using Data Mining to Increase Customer Life Time Value
 Using Data Mining to Increase Customer Life Time Value Chu Chai Henry Chan Hsin-Chieh Wu E-Business Research Lab Department of Industrial Engineering and Management, Chaoyang University of Technology Wufeng,
Using Data Mining to Increase Customer Life Time Value Chu Chai Henry Chan Hsin-Chieh Wu E-Business Research Lab Department of Industrial Engineering and Management, Chaoyang University of Technology Wufeng,
IM S5028. IMS Customer Relationship Management. What Is CRM? Ilona Jagielska 1
 IMS5028 - Customer Relationship Management CRM Concepts and Definitions What Is CRM? CRM is a strategy for acquiring and retaining profitable customers CRM is a strategy for optimising the lifetime value
IMS5028 - Customer Relationship Management CRM Concepts and Definitions What Is CRM? CRM is a strategy for acquiring and retaining profitable customers CRM is a strategy for optimising the lifetime value
Research on the E-Commerce Credit Scoring Model Using the Gaussian Density Function
 J Inf Process Syst, Vol.11, No., pp.173~183, June 015 http://dx.doi.org/10.3745/jips.04.001 ISSN 1976-913X (Print) ISSN 09-805X (Electronic) Research on the E-Commerce Credit Scoring Model Using the Gaussian
J Inf Process Syst, Vol.11, No., pp.173~183, June 015 http://dx.doi.org/10.3745/jips.04.001 ISSN 1976-913X (Print) ISSN 09-805X (Electronic) Research on the E-Commerce Credit Scoring Model Using the Gaussian
Applying Regression Techniques For Predictive Analytics Paviya George Chemparathy
 Applying Regression Techniques For Predictive Analytics Paviya George Chemparathy AGENDA 1. Introduction 2. Use Cases 3. Popular Algorithms 4. Typical Approach 5. Case Study 2016 SAPIENT GLOBAL MARKETS
Applying Regression Techniques For Predictive Analytics Paviya George Chemparathy AGENDA 1. Introduction 2. Use Cases 3. Popular Algorithms 4. Typical Approach 5. Case Study 2016 SAPIENT GLOBAL MARKETS
Predicting Corporate Influence Cascades In Health Care Communities
 Predicting Corporate Influence Cascades In Health Care Communities Shouzhong Shi, Chaudary Zeeshan Arif, Sarah Tran December 11, 2015 Part A Introduction The standard model of drug prescription choice
Predicting Corporate Influence Cascades In Health Care Communities Shouzhong Shi, Chaudary Zeeshan Arif, Sarah Tran December 11, 2015 Part A Introduction The standard model of drug prescription choice
Business Process Modeling for Supply Chain Transformation
 Business Process Modeling for Supply Chain Transformation Neha Jain, CPIM Janice Gullo, CFPIM, CSCP Neha Jain Neha Jain is a Business Process Consultant in DuPont. Her responsibilities include process
Business Process Modeling for Supply Chain Transformation Neha Jain, CPIM Janice Gullo, CFPIM, CSCP Neha Jain Neha Jain is a Business Process Consultant in DuPont. Her responsibilities include process
ECLT 5810 E-Commerce Data Mining Techniques - Introduction. Prof. Wai Lam
 ECLT 5810 E-Commerce Data Mining Techniques - Introduction Prof. Wai Lam Data Opportunities Business infrastructure have improved the ability to collect data Virtually every aspect of business is now open
ECLT 5810 E-Commerce Data Mining Techniques - Introduction Prof. Wai Lam Data Opportunities Business infrastructure have improved the ability to collect data Virtually every aspect of business is now open
ACCA Certified Accounting Technician Examination, Paper T5
 Answers ACCA Certified Accounting Technician Examination, Paper T5 Managing People and Systems December 2009 Answers and Marking Scheme Section A Questions 1 12 are all worth 2 marks each. 1 D 2 A 3 C
Answers ACCA Certified Accounting Technician Examination, Paper T5 Managing People and Systems December 2009 Answers and Marking Scheme Section A Questions 1 12 are all worth 2 marks each. 1 D 2 A 3 C
Predictive Analysis Risk Analysis
 Predictive Analysis Risk Analysis MARYLAND ASSOCIATION OF CPAS GOVERNMENT AND NOT-FOR-PROFIT CONFERENCE April 25, 2014 Overview Forensic Audit and Automated Oversight Data Analytics for Grant Oversight
Predictive Analysis Risk Analysis MARYLAND ASSOCIATION OF CPAS GOVERNMENT AND NOT-FOR-PROFIT CONFERENCE April 25, 2014 Overview Forensic Audit and Automated Oversight Data Analytics for Grant Oversight
Investigating the Demand for Short-shelf Life Food Products for SME Wholesalers
 Investigating the Demand for Short-shelf Life Food Products for SME Wholesalers Yamini Raju, Parminder S. Kang, Adam Moroz, Ross Clement, Ashley Hopwell, Alistair Duffy Abstract Accurate forecasting of
Investigating the Demand for Short-shelf Life Food Products for SME Wholesalers Yamini Raju, Parminder S. Kang, Adam Moroz, Ross Clement, Ashley Hopwell, Alistair Duffy Abstract Accurate forecasting of
Ranking Potential Customers based on GroupEnsemble method
 Ranking Potential Customers based on GroupEnsemble method The ExceedTech Team South China University Of Technology 1. Background understanding Both of the products have been on the market for many years,
Ranking Potential Customers based on GroupEnsemble method The ExceedTech Team South China University Of Technology 1. Background understanding Both of the products have been on the market for many years,
Intelligent Systems. For more information on partnering with the Kansas City Plant, contact:
 Intelligent Systems For more information on partnering with the Kansas City Plant, contact: Office of Business Development 1.800.225.8829 customer_inquiry@kcp.com Machine Intelligence Machine intelligence
Intelligent Systems For more information on partnering with the Kansas City Plant, contact: Office of Business Development 1.800.225.8829 customer_inquiry@kcp.com Machine Intelligence Machine intelligence
The Age of Intelligent Data Systems: An Introduction with Application Examples. Paulo Cortez (ALGORITMI R&D Centre, University of Minho)
 The Age of Intelligent Data Systems: An Introduction with Application Examples Paulo Cortez (ALGORITMI R&D Centre, University of Minho) Intelligent Data Systems: Introduction The Rise of Artificial Intelligence
The Age of Intelligent Data Systems: An Introduction with Application Examples Paulo Cortez (ALGORITMI R&D Centre, University of Minho) Intelligent Data Systems: Introduction The Rise of Artificial Intelligence
Big Data for Measuring the Information Society. Mohammad Ahli Executive Director Statistic Sector
 Big Data for Measuring the Information Society Mohammad Ahli Executive Director Statistic Sector هيئة اتحادية Authority Federal Big Data for Measuring the Information Society Project scope Utilizing big
Big Data for Measuring the Information Society Mohammad Ahli Executive Director Statistic Sector هيئة اتحادية Authority Federal Big Data for Measuring the Information Society Project scope Utilizing big
WHITEPAPER. Unlocking Your ATM Big Data : Understanding the power of real-time transaction monitoring and analytics.
 Unlocking Your ATM Big Data : Understanding the power of real-time transaction monitoring and analytics www.inetco.com Summary Financial organizations are heavily investing in self-service and omnichannel
Unlocking Your ATM Big Data : Understanding the power of real-time transaction monitoring and analytics www.inetco.com Summary Financial organizations are heavily investing in self-service and omnichannel
Using Decision Tree to predict repeat customers
 Using Decision Tree to predict repeat customers Jia En Nicholette Li Jing Rong Lim Abstract We focus on using feature engineering and decision trees to perform classification and feature selection on the
Using Decision Tree to predict repeat customers Jia En Nicholette Li Jing Rong Lim Abstract We focus on using feature engineering and decision trees to perform classification and feature selection on the
IBM SPSS Decision Trees
 IBM SPSS Decision Trees 20 IBM SPSS Decision Trees Easily identify groups and predict outcomes Highlights With SPSS Decision Trees you can: Identify groups, segments, and patterns in a highly visual manner
IBM SPSS Decision Trees 20 IBM SPSS Decision Trees Easily identify groups and predict outcomes Highlights With SPSS Decision Trees you can: Identify groups, segments, and patterns in a highly visual manner
Development Center, Warren, MI , USA 3 State Key Laboratory of Automotive Safety and Energy, Tsinghua University, Beijing , China
 EPD Congress 2013 TMS (The Minerals, Metals & Materials Society), 2013 STUDY ON EFFECTS OF INTERFACIAL ANISOTROPY AND ELASTIC INTERACTION ON MORPHOLOGY EVOLUTION AND GROWTH KINETICS OF A SINGLE PRECIPITATE
EPD Congress 2013 TMS (The Minerals, Metals & Materials Society), 2013 STUDY ON EFFECTS OF INTERFACIAL ANISOTROPY AND ELASTIC INTERACTION ON MORPHOLOGY EVOLUTION AND GROWTH KINETICS OF A SINGLE PRECIPITATE
Time Series Motif Discovery
 Time Series Motif Discovery Bachelor s Thesis Exposé eingereicht von: Jonas Spenger Gutachter: Dr. rer. nat. Patrick Schäfer Gutachter: Prof. Dr. Ulf Leser eingereicht am: 10.09.2017 Contents 1 Introduction
Time Series Motif Discovery Bachelor s Thesis Exposé eingereicht von: Jonas Spenger Gutachter: Dr. rer. nat. Patrick Schäfer Gutachter: Prof. Dr. Ulf Leser eingereicht am: 10.09.2017 Contents 1 Introduction
Billing Strategies for. Innovative Business Models
 Billing Strategies for Innovative Business Models How Boring Old Billing Could Be the Competitive Advantage You Never Knew You Had Billing Strategies for Innovative Business Models Page: 1 Introduction
Billing Strategies for Innovative Business Models How Boring Old Billing Could Be the Competitive Advantage You Never Knew You Had Billing Strategies for Innovative Business Models Page: 1 Introduction
Leveraging Robots for the Customer Journey
 Leveraging Robots for the Customer Journey How many customer service representatives (CSRs) does your organization have? 33.33% 28.21% 7.69% 14.10% 16.67% How many applications do you currently have running
Leveraging Robots for the Customer Journey How many customer service representatives (CSRs) does your organization have? 33.33% 28.21% 7.69% 14.10% 16.67% How many applications do you currently have running
Zoning Supporting Design of Deep Foundation Pit Based on Controlling Deformation of Surrounding Buildings
 International Journal of Architecture, Arts and Applications 2017; 3(5): 73-78 http://www.sciencepublishinggroup.com/j/ijaaa doi: 10.11648/j.ijaaa.20170305.12 ISSN: 2472-1107 (Print); ISSN: 2472-1131 (Online)
International Journal of Architecture, Arts and Applications 2017; 3(5): 73-78 http://www.sciencepublishinggroup.com/j/ijaaa doi: 10.11648/j.ijaaa.20170305.12 ISSN: 2472-1107 (Print); ISSN: 2472-1131 (Online)
Machine Learning 101
 Machine Learning 101 Mike Alperin September, 2016 Copyright 2000-2016 TIBCO Software Inc. Agenda What is Machine Learning? Decision Tree Models Customer Analytics Examples Manufacturing Examples Fraud
Machine Learning 101 Mike Alperin September, 2016 Copyright 2000-2016 TIBCO Software Inc. Agenda What is Machine Learning? Decision Tree Models Customer Analytics Examples Manufacturing Examples Fraud
International Journal of Computer Science Trends and Technology (IJCST) Volume 2 Issue 1, Jan-Feb 2014
 Heart Disease Prediction Using the Data mining Techniques Aswathy Wilson 1, Gloria Wilson 2, Likhiya Joy K 3 Professor 1, Department of Computer Science and Engineering Jyothi Engineering College, Cheruthuruthy,
Heart Disease Prediction Using the Data mining Techniques Aswathy Wilson 1, Gloria Wilson 2, Likhiya Joy K 3 Professor 1, Department of Computer Science and Engineering Jyothi Engineering College, Cheruthuruthy,
Digital Finance in Shared Services & GBS. Deloitte: Piyush Mistry & Oscar Hamilton LBG: Steve McKenna
 Digital Finance in Shared Services & GBS Deloitte: Piyush Mistry & Oscar Hamilton LBG: Steve McKenna Agenda Agenda Content Digital Finance of the Future Uncover the picture of what the future of Finance
Digital Finance in Shared Services & GBS Deloitte: Piyush Mistry & Oscar Hamilton LBG: Steve McKenna Agenda Agenda Content Digital Finance of the Future Uncover the picture of what the future of Finance
Knowledge Discovery Services and Applications
 Knowledge Discovery Services and Applications kdlabs AG www.kdlabs.com Dr. Jörg-Uwe Kietz Content Knowledge Discovery @ kdlabs Key features of Mining Mart for KD services and applications Clever processing
Knowledge Discovery Services and Applications kdlabs AG www.kdlabs.com Dr. Jörg-Uwe Kietz Content Knowledge Discovery @ kdlabs Key features of Mining Mart for KD services and applications Clever processing
Create a New Expense Report
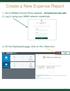 Create a New Expense Report 1. Go to [W&M] Chrome River website: chromeriver.wm.edu 2. Log in using your W&M network credentials 3. On the Dashboard page, click on the +New Icon Your name here 1 Completing
Create a New Expense Report 1. Go to [W&M] Chrome River website: chromeriver.wm.edu 2. Log in using your W&M network credentials 3. On the Dashboard page, click on the +New Icon Your name here 1 Completing
How to build and deploy machine learning projects
 How to build and deploy machine learning projects Litan Ilany, Advanced Analytics litan.ilany@intel.com Agenda Introduction Machine Learning: Exploration vs Solution CRISP-DM Flow considerations Other
How to build and deploy machine learning projects Litan Ilany, Advanced Analytics litan.ilany@intel.com Agenda Introduction Machine Learning: Exploration vs Solution CRISP-DM Flow considerations Other
Integrated production planning and control: A multi-objective optimization model
 Journal of Industrial Engineering and Management JIEM, 2013 6(4): 815-830 Online ISSN: 2013-0953 Print ISSN: 2013-8423 http://dx.doi.org/10.3926/jiem.771 Integrated production planning and control: A multi-objective
Journal of Industrial Engineering and Management JIEM, 2013 6(4): 815-830 Online ISSN: 2013-0953 Print ISSN: 2013-8423 http://dx.doi.org/10.3926/jiem.771 Integrated production planning and control: A multi-objective
Assessment of modification level of hypoeutectic Al -Si alloys by pattern recognition of cooling curves
 Assessment of modification level of hypoeutectic Al -Si alloys by pattern recognition of cooling curves *CHEN Xiang, GENG Hui-yuan, LI Yan-xiang (Department of Mechanical Engineering, Key Laboratory for
Assessment of modification level of hypoeutectic Al -Si alloys by pattern recognition of cooling curves *CHEN Xiang, GENG Hui-yuan, LI Yan-xiang (Department of Mechanical Engineering, Key Laboratory for
Managing Business Rules and Analytics as an Enterprise Asset
 Managing Business Rules and Analytics as an Enterprise Asset Discover Financial Services Business unit of Morgan Stanley Operates the Discover Card brands Largest proprietary credit card network in the
Managing Business Rules and Analytics as an Enterprise Asset Discover Financial Services Business unit of Morgan Stanley Operates the Discover Card brands Largest proprietary credit card network in the
Predictive Modeling Using SAS Visual Statistics: Beyond the Prediction
 Paper SAS1774-2015 Predictive Modeling Using SAS Visual Statistics: Beyond the Prediction ABSTRACT Xiangxiang Meng, Wayne Thompson, and Jennifer Ames, SAS Institute Inc. Predictions, including regressions
Paper SAS1774-2015 Predictive Modeling Using SAS Visual Statistics: Beyond the Prediction ABSTRACT Xiangxiang Meng, Wayne Thompson, and Jennifer Ames, SAS Institute Inc. Predictions, including regressions
A Highly Customizable Blockchain Infrastructure
 1 / 15 2 / 15 Abstract NULS is a blockchain that architecturally enables extendibility using smart contracts, modules and sub-chains. It is an open-source project that separates its features into customizable
1 / 15 2 / 15 Abstract NULS is a blockchain that architecturally enables extendibility using smart contracts, modules and sub-chains. It is an open-source project that separates its features into customizable
Investigating the myths and realities of contactless payment
 Investigating the myths and realities of contactless payment Questions & Answers There has been much recent coverage in the media (press, web, blogs.) about the perceived security vulnerabilities of contactless
Investigating the myths and realities of contactless payment Questions & Answers There has been much recent coverage in the media (press, web, blogs.) about the perceived security vulnerabilities of contactless
Data processing. In this project, researchers Henry Liu of the Department of Civil Engineering and
 Data mining of transit vehicle location, passenger count, and fare collection databases for intelligent transportation applications Supporting efficient transit service by maximizing the use of available
Data mining of transit vehicle location, passenger count, and fare collection databases for intelligent transportation applications Supporting efficient transit service by maximizing the use of available
Classification Model for Intent Mining in Personal Website Based on Support Vector Machine
 , pp.145-152 http://dx.doi.org/10.14257/ijdta.2016.9.2.16 Classification Model for Intent Mining in Personal Website Based on Support Vector Machine Shuang Zhang, Nianbin Wang School of Computer Science
, pp.145-152 http://dx.doi.org/10.14257/ijdta.2016.9.2.16 Classification Model for Intent Mining in Personal Website Based on Support Vector Machine Shuang Zhang, Nianbin Wang School of Computer Science
FFQA 1. Complied by: Mohammad Faizan Farooq Qadri Attari ACCA (Finalist) Contact:
 FFQA 1 Objective of IAS 2 The objective of IAS 2 is to prescribe the accounting treatment for inventories. It provides guidance for determining the cost of inventories and for subsequently recognising
FFQA 1 Objective of IAS 2 The objective of IAS 2 is to prescribe the accounting treatment for inventories. It provides guidance for determining the cost of inventories and for subsequently recognising
DESIGN OF COPD BIGDATA HEALTHCARE SYSTEM THROUGH MEDICAL IMAGE ANALYSIS USING IMAGE PROCESSING TECHNIQUES
 DESIGN OF COPD BIGDATA HEALTHCARE SYSTEM THROUGH MEDICAL IMAGE ANALYSIS USING IMAGE PROCESSING TECHNIQUES B.Srinivas Raja 1, Ch.Chandrasekhar Reddy 2 1 Research Scholar, Department of ECE, Acharya Nagarjuna
DESIGN OF COPD BIGDATA HEALTHCARE SYSTEM THROUGH MEDICAL IMAGE ANALYSIS USING IMAGE PROCESSING TECHNIQUES B.Srinivas Raja 1, Ch.Chandrasekhar Reddy 2 1 Research Scholar, Department of ECE, Acharya Nagarjuna
Adaptive Water Demand Forecasting for Near Real-time Management of Smart Water Distribution Systems
 Adaptive Water Demand Forecasting for Near Real-time Management of Smart Water Distribution Systems Presented by On behalf of Gary Wong & Kleanthis Mazarakis Kevin Woodward & Michele Romano @osisoft Copyright
Adaptive Water Demand Forecasting for Near Real-time Management of Smart Water Distribution Systems Presented by On behalf of Gary Wong & Kleanthis Mazarakis Kevin Woodward & Michele Romano @osisoft Copyright
TDA and Machine Learning: Better Together WHITE PAPER
 TDA and Machine Learning: Better Together Table of Contents Overview... 4 Introducing Topology, Topological Data Analysis, and the Ayasdi Machine Intelligence Platform... 4 The Promise of Machine Learning...
TDA and Machine Learning: Better Together Table of Contents Overview... 4 Introducing Topology, Topological Data Analysis, and the Ayasdi Machine Intelligence Platform... 4 The Promise of Machine Learning...
Sequential Association Rules Based on Apriori Algorithm Applied in Personal Recommendation
 , pp.257-264 http://dx.doi.org/10.14257/ijdta.2016.9.6.26 Sequential Association Rules Based on Apriori Algorithm Applied in Personal Recommendation Wang Yonggang School of information science and technology,
, pp.257-264 http://dx.doi.org/10.14257/ijdta.2016.9.6.26 Sequential Association Rules Based on Apriori Algorithm Applied in Personal Recommendation Wang Yonggang School of information science and technology,
Predictive analytics [Page 105]
![Predictive analytics [Page 105] Predictive analytics [Page 105]](/thumbs/74/70801456.jpg) Week 8, Lecture 17 and Lecture 18 Predictive analytics [Page 105] Predictive analytics is a highly computational data-mining technology that uses information and business intelligence to build a predictive
Week 8, Lecture 17 and Lecture 18 Predictive analytics [Page 105] Predictive analytics is a highly computational data-mining technology that uses information and business intelligence to build a predictive
