Electronic Checklist of Risk Items on Construction Projects
|
|
|
- Patrick Page
- 6 years ago
- Views:
Transcription
1 Electronic Checklist of Risk Items on Construction Projects Moselhi, O. 1 and Hassanein, A. 2 1 Prof. and Chair, Dept. of Building, Civil and Environmental Engineering Concordia University, Montréal, Québec moselhi@cbs-engr.concordia.ca 2 Post-Doctorate Fellow, Dept. of Building, Civil and Environmental Engineering Concordia University, Montréal, Québec hass@alcor.concordia.ca. ABSTRACT: Risk management in construction encompasses four main phases; risk identification, quantification, mitigation and control. Risk identification has been recognized as the most crucial phase of a successful risk management program. This paper briefly describes a model, designed to automate the risk identification process. The model facilitates the development of an electronic checklist of items that are likely to give rise to risk on construction projects. A risk classification scheme is proposed, where risks are classified as either generic or domain-specific. Generic risks are those which might be encountered on any project, irrespective of its type (e.g. currency fluctuations). Domain-specific risks, on the other hand, are those which are associated with the nature of the project at hand (e.g. risks encountered on transportation projects might not be encountered in hydro projects). At the core of the model is its relational database, designed to store various risk items. The impact of project domain, size, location and delivery type (Engineering Procurement Construction vs. Build Operate Transfer) are considered in developing an automated list of project-specific risk items. The proposed model is implemented in a prototype software, which operates in Microsoft Windows environment. It employs Microsoft Access as the database management system and incorporates a user-friendly graphical user interface, utilizing dialog boxes, menus and toolbars. The developed system has several practical features, including the definition of one or more references to each stored risk item to enable tracking and reviewing of their sources. It provides three levels of access for security purposes. It is flexible, allowing updates and editing of defined project-specific risks. KEYWORDS: Risk identification, risk management, construction management. 1. INTRODUCTION The first and most important phase of a risk management program is risk identification (CII 1988; De Zoysa and Russell 2003), as a risk that is not identified cannot be quantified, controlled, transferred or otherwise managed. The process is particularly difficult as there are no structured methodologies that may be adopted to identify project risks. It remains a process that relies heavily on the experience and insight knowledge of project personnel. Risks have typically been identified through several methods including brainstorming, workshops, checklists, questionnaires and interviews, literature review, and knowledge-based systems (De Zoysa and Russell 2003). Upon identifying risk items to which a project might be exposed, most construction organizations store them in the form of a risk register. Such registers have been identified as extremely effective tools by Patterson and Neailey (2002). However, no formal structure has been developed to systematically identify risks to which a particular project might be exposed. Typically, risk management in construction tends to depend mainly on individual key players (Tah and Carr 2000). These individuals adopt different terminology and techniques for describing and managing risks, which could potentially cause inconsistencies and ambiguities. A common language for describing risk is necessary to facilitate a consistent approach to assessment and quantification of its impact. 557
2 This paper presents a model, designed to automate the risk identification process and provide a systematic approach to reduce ambiguities. The proposed model accounts for several practical factors when identifying risks to which a project might be exposed, including project location, domain and size. The impact of project delivery system on potential risk items is also considered. The sources from which risk items were obtained are stored to enable subsequent assessment of their reliability. A prototype software, based on the proposed model is developed. It operates in Microsoft Windows environment, providing a user friendly interface utilizing menus, dialog boxes and a toolbar. It provides various levels of access, ensuring security and integrity of its central database. It provides a vehicle for construction companies to continuously enhance and fine-tune their risk registers to store corporate knowledge, and efficiently draw upon it for potential business opportunities. 2. SCOPE The proposed model automates the generation of risk items to which a project might be exposed, while embracing flexibility and practicality. It was developed in collaboration with a major Canadian contractor to automate the risk identification process, and as a the first phase towards the development of a risk management program. It is designed to aid practitioners in identifying various risks and opportunities to which a project might be exposed. It automatically generates a list of all risk items and opportunities to which a project is exposed, enabling users to select some or all of them, as per the unique requirements of each project. In addition to risk items, the proposed model stores: 1) the username of individuals who define/edit these risk items on a regular basis; and 2) sources from which these risks were obtained (personal experience/literature review). It is designed to be employed in the pre-bidding stage, building on the knowledge base and user s experience. An issue that caused some debate between researchers is whether the term risk should be confined to define threats, or whether it should be broad to encompass both threats and opportunities. A recent study (Raftery et al. 2001) determined that contractors pay more attention to threats than opportunities, even if the attached monetary values were identical. Recently, the trend has been to regard risks as both opportunities and threats, (see the Project Management Body of Knowledge (PMBoK 2000)). In this paper, it was decided that the term risk be used to define uncertain events with both positive and negative impacts on the project. This is because: 1. Opportunities and threats are not qualitatively different in nature, since both involve uncertainty and have the potential to impact project progress; 2. Adopting this nomenclature would aid management in both minimizing the impact of threats and maximizing the impact of opportunities; and 3. This approach would aid management in the adoption of an unbiased approach to risk management (Raftery et al. 2001). When generating the list of potential risk items for a project, it was recognized that the adopted project delivery system has a significant impact on the risks to which a project might be exposed. Engineering/procurement/construction (EPC) and build-operate-transfer (BOT) delivery systems pose different risks that can impact the project being analyzed. Additionally, various types of contracts (e.g. lump-sum, cost-plus) allocate risks differently between contracting parties. The proposed model accounts for project delivery systems and adopted contract type. The following sections provide an overview of the proposed model. 3. RISK CLASSIFICATION A coherent risk classification scheme has been identified as a crucial step in risk identification (Al-Bahar and Crandall 1990; De Zoysa and Russell 2003). A comprehensive review of risk classification schemes was conducted to establish the current state-of-the-art in the field and identify and categorize the various risk items to which a class of projects may be subjected. Classification schemes reported in literature, along with that developed by the industry partner were reviewed. Most classification schemes reported in literature divide risks based on either: 1) their source (e.g. Odeyinka 2001; CII 1989); or 2) ability to control them (e.g. Tah and Carr 2001). Another classification scheme was proposed by Tah and Carr (2001) based on their nature throughout project life cycle. From this viewpoint, risks are divided into static and dynamic. Static risks maintain their nature throughout project life or until they seize to pose a threat (or opportunity). That is to say, the probability of occurrence of the risk and its impact on project progress remain unchanged. On the other hand, the likelihood of 558
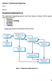
3 the occurrence of dynamic risks and their impact vary during the life cycle of the project. The events causing this class of risks should be constantly monitored, the likelihood of their occurring reassessed and their impact reevaluated. Figure 1 depicts the proposed risk classification scheme, where risks are divided into two broad categories: generic and domain-specific (or sectorspecific). Generic risks are those which are inherent in all projects, irrespective of their nature or the type of work involved. These are divided into five sub-categories based on their sources. These are: commercial, technical, location, client and own risks. Own risks include: 1) those which an organization poses to itself, such as availability of technical know-how and right staff within the organization to carry out a project successfully; and 2) competence of selected partners. Domainspecific risks, on the other hand, are dependant on the project type, and would only be relevant for a specific domain (e.g. transportation, power plants). In the current study, sixteen domains are defined, reflecting the sixteen domains which the industry partner is involved in. Risks Commercial Location Own Detail A Generic Technical Client Domainspecific EPC Both Detail A Figure 1. Proposed risk classification scheme BOT The proposed classification scheme accounts for the adopted project delivery method (EPC vs. BOT). This enables the identification of risks that are inherent under differing project delivery systems (EPC vs. BOT projects). In that regard, risks are classified into three main groups (Figure 1, detail A ): 1) BOT; 2) EPC; and 3) both risks. The definition of the third category acknowledges the presence of certain risk factors that are applicable irrespective of the project delivery method and accounts for the fact that a BOT project may include EPC-related risks. This accounts for the nature of BOT projects, which impose additional risks over and above those inherent under traditional project delivery systems. The prolonged planning horizon, increased number of project participants and markedly increased project variables increase a project s vulnerability to external risks (Kumaraswamy and Morris 2002). 4. COMPUTER IMPLEMENTATION The proposed model is implemented in a prototype software that operates in Microsoft Windows environment. It is coded in Visual C++ Version 6, utilizing Microsoft Foundation Classes (MFC). It provides three levels of access: 1) administrator; 2) management; and 3) project team. Access privileges for each group are listed in Table 1. As the table shows, only administrators have access to all projects, while managers only have access to projects with which they are involved. Microsoft Access is employed as the database management system (DBMS), using Open DataBase Connectivity (ODBC), which enables real-time updating of the database. The database enables management to query risk items based on the access level of the person who input them, enabling fast queries on various risk items and evaluating their value to the company. If approved by management, the risk item is no longer highlighted, otherwise it is deleted. This process is designed to encourage participation and help capture the company s experience and builds on its reservoir of knowledge and expertise, while ensuring the integrity of the database. The proposed model provides a simple, friendly graphical user interface, as shown in Figure 2. The left portion of the screen contains a tree view, similar to that of Windows Explorer, listing a variety of data including defined projects and risks to which they are exposed, stored risk items and sources from which they were defined. Upon double clicking on a risk item defined for a project, the user can edit its probability of occurrence and/or potential impact. The right portion of the screen provides a more detailed description of the project at hand, its domain, cost, project delivery method, location and risk items to which it is exposed, along with their probability of occurrence and potential impact. The user can edit these risk items to suit the unique conditions of each project through: 1) adding risk items; 2) 559
4 deleting risk items; or 3) revising a risk item s probability of occurrence and/or potential impact. This increases the model s flexibility, enabling it to continuously adjust to account for dynamic risks (Tah and Carr 2001). Figure 3. Dialog window to define new risk item Figure 2. Main software screen The dialog window shown in Figure 3 is designed to define new risk items. It captures all required data to categorize and store defined risk items in the database. For generic risk items, a subcategory (commercial/technological/client/own /location), while for domain-specific risks, a domain needs to be specified. The list of domains is also user-defined, enabling the software to be tailored to the domains of expertise of the user, and enabling its modification to accommodate emerging domains. The project delivery method that gives rise to the risk item also needs to be defined, along with the minimum project cost with which it is associated. The same dialog window is employed to input opportunities (risks with positive impact on project cost/schedule), as the user can select whether the risk item is a liability or a potential gain. It is worth noting that a description of the risk item is also required as input in order to resolve any ambiguities that might arise regarding its nature and what it covers. Periodic review of defined risk items and their definitions would avoid duplicity and aid in developing a company-wide terminology regarding risk. The software employs a two-stage approach to identify risks to which construction projects (within the sixteen pre-defined domains) might be exposed. The first stage is project definition, which is carried out employing the dialog window shown in Figure 4. All variables required to determine risk items to which a project might exposed are input using that dialog window. Upon defining the project, and based on its domain, estimated cost and delivery method, a broad group of risk items is retrieved from the database. The data included in the dialog window shown in Figure 4 is all the input that is required of the user to generate its checklist of risk items. Figure 4. Stage one: project definition The second stage employs the dialog window shown in Figure 5, and entails selecting risk items relevant to the project at hand from a list of risk items that might potentially impact a project. As the figure demonstrates, the dialog window 560
5 contains two lists of the generic and domain/sector specific risk factors. The project shown in Figure 4 is an environmental project constructed using the BOT delivery system. As the figure shows, the software retrieves relevant risk items from the database and lists them alphabetically for the user to select some or all of the listed items. In the case shown in the figure, risks applicable to both: 1) BOT-related risks; and 2) risks applicable to both EPC and BOT delivery systems are considered relevant. This query is carried out for both generic and domain-specific risks (in this case, environmental) to develop the electronic checklist shown in Figure 5. Once this list is developed, it could be subject to further review for further additions and/or deletion, as the project team deems fit. To reduce ambiguities, a description of a risk item can be reviewed by double-clicking on its name. user-friendly interface, minimizing the time and effort required to identify risks to which a project might be exposed. It aids in achieving conformity in risk terminology within the company, aiding construction companies to develop a well-defined business culture towards risk management. 6. REFERENCES Al-Bahar, J. And Crandall, K., 1990, Systematic Risk Management Approach for Construction Projects, Journal of Construction Engineering and Management (ASCE), Vol. 116, No. 3, pp CII, 1988, Contract Risk Allocation and Cost Effectiveness, Contract task Force, Publication 5-3. CII, 1989, Management of Project Risks and Uncertainties, Risk Management Task Force, Publication 6-8. De Zoysa, S. and Russell, A., 2003, Knowledgebased Risk Identification in Infrastructure Projects, Canadian Journal of Civil Engineering (CSCE), Vol. 30, No. 3, pp Figure 5. Stage two: selecting risk items Upon completion of this stage, a project-specific checklist of risk items is developed as shown in Figure 2. These items can later be revised to account for the dynamic nature of the construction industry. The effort required to generate a risk checklist for a construction project has been reduced to two simple point-and-click dialog windows. 5. CONCLUSIONS This paper presented a model, designed to automate risk identification for construction projects. The project was part of a collaborative research program with a major Canadian contractor. A robust risk classification scheme is proposed to aid in the risk management process. The proposed model employs a two-step approach to generate project-specific checklist of risk items that require management s attention. It is implemented in a computer software that operates in Microsoft Windows environment. It provides a Kumaraswamy, M. and Morris, D., 2002, Build- Operate-Transfer-Type Procurement in Asian Megaprojects, Journal of Construction Engineering and Management (ASCE), Vol. 128, No. 2, pp Odeyinka, H., 2000, An Evaluation of the Use of Insurance in Managing Construction Risks, Construction Management and Economics, Vol. 18, pp Patterson, F. and Neailey, K., 2002, A Risk Register Database System to Aid the Management of Project Risk, International Journal of Project Management, Vol. 20, pp Project Management Institute (PMI), 2000, A Guide to the Project Management Body of Knowledge, Project Management Institute, Upper Darby, PA. Raftery, J., Csete, J. and Hui, S., 2001, Are Risk Attitudes Robust? Qualitative Evidence Before and After a Business Cycle Inflection, Construction Management and Economics, pp
6 Tah, J. and Carr, V., 2000, A Proposal for Construction Project risk Assessment Using Fuzzy Logic, Construction Management and Economics, Vol. 18, No. 4, pp Tah, J. and Carr, V., 2001, Knowledge-Based Approach to Construction Project Risk Management, Journal of Computing in Civil Engineering (ASCE), Vol. 15, No. 3, pp Table 1. Levels of access enabled in proposed model Privileges Administrator Management Project Team Access to projects All Restricted Restricted Define new risk items Yes Yes Yes* Define new project/deleting project Yes Yes No Associating risk item with project Yes Yes Yes* Deleting risk item from project Yes Yes No Defining new user Yes No No Viewing user privileges Yes No No * Pending management approval 562
Microsoft Office Project 2010 Basic Course 01: Getting Started
 Microsoft Office Project 2010 Basic Course 01: Getting Started Slide 1 Topic A Project Management Concepts Slide 2 Project Constraints Slide 3 Phases of Project Management The initial Phase Initiating
Microsoft Office Project 2010 Basic Course 01: Getting Started Slide 1 Topic A Project Management Concepts Slide 2 Project Constraints Slide 3 Phases of Project Management The initial Phase Initiating
Risk Management Using Spiral Model for Information Technology
 Risk Management Using Spiral Model for Information Technology Rajendra Ganpatrao Sabale, Dr. A.R Dani Student of Ph.D., Singhania University, Pacheri Bari, Dist. Jhunjhunu( Rajasthan), India International
Risk Management Using Spiral Model for Information Technology Rajendra Ganpatrao Sabale, Dr. A.R Dani Student of Ph.D., Singhania University, Pacheri Bari, Dist. Jhunjhunu( Rajasthan), India International
The 9 knowledge Areas and the 42 Processes Based on the PMBoK 4th
 The 9 knowledge Areas and the 42 Processes Based on the PMBoK 4th www.pmlead.net PMI, PMP, CAPM and PMBOK Guide are trademarks of the Project Management Institute, Inc. PMI has not endorsed and did not
The 9 knowledge Areas and the 42 Processes Based on the PMBoK 4th www.pmlead.net PMI, PMP, CAPM and PMBOK Guide are trademarks of the Project Management Institute, Inc. PMI has not endorsed and did not
Week 4 Pre-Project Planning (2)
 Week 4 Pre-Project Planning (2) 457.307 Construction Planning and Management Department of Civil and Environmental Engineering Seoul National University Prof. Seokho Chi shchi@snu.ac.kr 건설환경공학부 35 동 304
Week 4 Pre-Project Planning (2) 457.307 Construction Planning and Management Department of Civil and Environmental Engineering Seoul National University Prof. Seokho Chi shchi@snu.ac.kr 건설환경공학부 35 동 304
Darshan Institute of Engineering & Technology for Diploma Studies Rajkot Unit-1
 Failure Rate Darshan Institute of Engineering & Technology for Diploma Studies Rajkot Unit-1 SOFTWARE (What is Software? Explain characteristics of Software. OR How the software product is differing than
Failure Rate Darshan Institute of Engineering & Technology for Diploma Studies Rajkot Unit-1 SOFTWARE (What is Software? Explain characteristics of Software. OR How the software product is differing than
RISK MANAGEMENT : BEST PRACTICE AND FUTURE DEVELOPMENTS
 3 Lower Heyshott, Petersfield Hampshire GU31 4PZ, UK Tel : +44(0)7717.665222 Email : info@risk-doctor.com Web : www.risk-doctor.com RISK MANAGEMENT : BEST PRACTICE AND FUTURE DEVELOPMENTS Dr David Hillson
3 Lower Heyshott, Petersfield Hampshire GU31 4PZ, UK Tel : +44(0)7717.665222 Email : info@risk-doctor.com Web : www.risk-doctor.com RISK MANAGEMENT : BEST PRACTICE AND FUTURE DEVELOPMENTS Dr David Hillson
Key Components of a Project Quality Plan
 15 th Asia Pacific Conference for Non-Destructive Testing (APCNDT017), Singapore. Key Components of a Project Quality Plan Dr. B. Muthuramalingam, Novriandi, VIRGIN Santiago A Quality Assurance & Quality
15 th Asia Pacific Conference for Non-Destructive Testing (APCNDT017), Singapore. Key Components of a Project Quality Plan Dr. B. Muthuramalingam, Novriandi, VIRGIN Santiago A Quality Assurance & Quality
Available online at ScienceDirect. Procedia CIRP 28 (2015 ) rd CIRP Global Web Conference
 Available online at www.sciencedirect.com ScienceDirect Procedia CIRP 28 (2015 ) 179 184 3rd CIRP Global Web Conference Quantifying risk mitigation strategies for manufacturing and service delivery J.
Available online at www.sciencedirect.com ScienceDirect Procedia CIRP 28 (2015 ) 179 184 3rd CIRP Global Web Conference Quantifying risk mitigation strategies for manufacturing and service delivery J.
Risk Based Testing. -Why we need RBT? -Types of risks -Managing risks -Methods of evaluation & risk analysis -Costs and benefits
 Risk Based Testing -Why we need RBT? -Types of risks -Managing risks -Methods of evaluation & risk analysis -Costs and benefits Ladislau Szilagyi www.euroqst.ro Definitions (ISTQB glossary) Risk = a factor
Risk Based Testing -Why we need RBT? -Types of risks -Managing risks -Methods of evaluation & risk analysis -Costs and benefits Ladislau Szilagyi www.euroqst.ro Definitions (ISTQB glossary) Risk = a factor
Risk Management User Guide
 Risk Management User Guide Version 17 December 2017 Contents About This Guide... 5 Risk Overview... 5 Creating Projects for Risk Management... 5 Project Templates Overview... 5 Add a Project Template...
Risk Management User Guide Version 17 December 2017 Contents About This Guide... 5 Risk Overview... 5 Creating Projects for Risk Management... 5 Project Templates Overview... 5 Add a Project Template...
A PROTOTYPE RISK MANAGEMENT DECISION SUPPORT TOOL FOR CONSTRUCTION PROJECTS
 A PROTOTYPE RISK MANAGEMENT DECISION SUPPORT TOOL FOR CONSTRUCTION PROJECTS Arif Erdem Arikan Middle East Technical University, Civil Engineering Department, Ankara, Turkey aearikan@metu.edu.tr Irem Dikmen
A PROTOTYPE RISK MANAGEMENT DECISION SUPPORT TOOL FOR CONSTRUCTION PROJECTS Arif Erdem Arikan Middle East Technical University, Civil Engineering Department, Ankara, Turkey aearikan@metu.edu.tr Irem Dikmen
Because you re reading this book, we can safely assume that the products
 Chapter 1: Understanding Project Server In This Chapter Discovering Project Server Determining whether you need Project Server Planning the implementation of Project Server Because you re reading this
Chapter 1: Understanding Project Server In This Chapter Discovering Project Server Determining whether you need Project Server Planning the implementation of Project Server Because you re reading this
ECI: Two-Stage Contracts
 ECI: Two-Stage Contracts Client and Contractor Considerations Michael Creedon Special Counsel ECI in Infrastructure and Major Projects Summit 2010 Sydney, 17 June 2010 Sessions Outline Introduction /
ECI: Two-Stage Contracts Client and Contractor Considerations Michael Creedon Special Counsel ECI in Infrastructure and Major Projects Summit 2010 Sydney, 17 June 2010 Sessions Outline Introduction /
Mitigations on Joint Venture Risks in Real Estate Projects
 Mitigations on Joint Venture Risks in Real Estate Projects Laxmikant Bajarang Zirape 1, Prof. Abhijit A. Warudkar 2 1M.E (Construction & Management) Student, Civil Dept. ICOER, Wagholi, Pune, India 2Professor,
Mitigations on Joint Venture Risks in Real Estate Projects Laxmikant Bajarang Zirape 1, Prof. Abhijit A. Warudkar 2 1M.E (Construction & Management) Student, Civil Dept. ICOER, Wagholi, Pune, India 2Professor,
Project Management Framework with reference to PMBOK (PMI) July 01, 2009
 Project Management Framework with reference to PMBOK (PMI) July 01, 2009 Introduction Context Agenda Introduction to Methodologies What is a Methodology? Benefits of an Effective Methodology Methodology
Project Management Framework with reference to PMBOK (PMI) July 01, 2009 Introduction Context Agenda Introduction to Methodologies What is a Methodology? Benefits of an Effective Methodology Methodology
Morningstar Direct SM Search Criteria
 The Search Criteria in Morningstar Direct generates a set of investments that currently match the criteria defined. Each time the file is retrieved from the Search Criteria folder, the members are redefined
The Search Criteria in Morningstar Direct generates a set of investments that currently match the criteria defined. Each time the file is retrieved from the Search Criteria folder, the members are redefined
Knowledge-Based Audits of Construction Companies and Contractors must
 Knowledge-Based Audits of Construction Companies and Contractors is designed to help the auditor efficiently and effectively perform financial statement audits of construction companies and contractors
Knowledge-Based Audits of Construction Companies and Contractors is designed to help the auditor efficiently and effectively perform financial statement audits of construction companies and contractors
The Sector Skills Council for the Financial Services Industry. National Occupational Standards. Risk Management for the Financial Sector
 The Sector Skills Council for the Financial Services Industry National Occupational Standards Risk Management for the Financial Sector Final version approved April 2009 IMPORTANT NOTES These National Occupational
The Sector Skills Council for the Financial Services Industry National Occupational Standards Risk Management for the Financial Sector Final version approved April 2009 IMPORTANT NOTES These National Occupational
10/18/2018. London Governance, Risk, and Compliance
 10/18/2018 Governance, Risk, and Compliance Contents Contents... 4 Applications and integrations supporting GRC workflow... 6 GRC terminology... 7 Domain separation in... 9 Policy and Compliance Management...11
10/18/2018 Governance, Risk, and Compliance Contents Contents... 4 Applications and integrations supporting GRC workflow... 6 GRC terminology... 7 Domain separation in... 9 Policy and Compliance Management...11
SELECTING EARTHMOVING EQUIPMENT FLEETS USING GENETIC ALGORITHMS. Mohamed Marzouk Osama Moselhi
 Proceedings of the 2002 Winter Simulation Conference E. Yücesan, C.-H. Chen, J. L. Snowdon, and J. M. Charnes, eds. SELECTING EARTHMOVING EQUIPMENT FLEETS USING GENETIC ALGORITHMS Mohamed Marzouk Osama
Proceedings of the 2002 Winter Simulation Conference E. Yücesan, C.-H. Chen, J. L. Snowdon, and J. M. Charnes, eds. SELECTING EARTHMOVING EQUIPMENT FLEETS USING GENETIC ALGORITHMS Mohamed Marzouk Osama
Success Factors in Large Construction Projects
 Success Factors in Large Construction Projects Szentes, H. Department of Civil, Mining and Environmental Engineering Luleå University of Technology, Luleå, Sweden (email: henrik@szentes.se) Abstract The
Success Factors in Large Construction Projects Szentes, H. Department of Civil, Mining and Environmental Engineering Luleå University of Technology, Luleå, Sweden (email: henrik@szentes.se) Abstract The
Standard for Validation, Verification and Audit
 Standard for Validation, Verification and Audit Carbon Competitiveness Incentive Regulation Version 2.0 June 2018 Title: Standard for Validation, Verification and Audit Number: 2.0 Program Name: Carbon
Standard for Validation, Verification and Audit Carbon Competitiveness Incentive Regulation Version 2.0 June 2018 Title: Standard for Validation, Verification and Audit Number: 2.0 Program Name: Carbon
TRANSPORTATION ASSET MANAGEMENT GAP ANALYSIS TOOL
 Project No. 08-90 COPY NO. 1 TRANSPORTATION ASSET MANAGEMENT GAP ANALYSIS TOOL USER S GUIDE Prepared For: National Cooperative Highway Research Program Transportation Research Board of The National Academies
Project No. 08-90 COPY NO. 1 TRANSPORTATION ASSET MANAGEMENT GAP ANALYSIS TOOL USER S GUIDE Prepared For: National Cooperative Highway Research Program Transportation Research Board of The National Academies
INTEGRATED MANAGEMENT OF THE CONSTRUCTION PROJECT DURING THE BUILDING PHASE
 INTEGRATED MANAGEMENT OF THE CONSTRUCTION PROJECT DURING THE BUILDING PHASE Yun Na WU, Na YAO School of Business & Management, North China Electric Power University, Beijing 102206, China Abstract: Traditional
INTEGRATED MANAGEMENT OF THE CONSTRUCTION PROJECT DURING THE BUILDING PHASE Yun Na WU, Na YAO School of Business & Management, North China Electric Power University, Beijing 102206, China Abstract: Traditional
PROJECT EXECUTION PLANNING FOR COST AND SCHEDULE MANAGERS
 PROJECT EXECUTION PLANNING FOR COST AND SCHEDULE MANAGERS ALLEN C. HAMILTON PMP CCE Project Management Associates LLC 3 Totten Way, Suite 110 Morris Plains, New Jersey 07950 USA Telephone: +1 973 984-1853
PROJECT EXECUTION PLANNING FOR COST AND SCHEDULE MANAGERS ALLEN C. HAMILTON PMP CCE Project Management Associates LLC 3 Totten Way, Suite 110 Morris Plains, New Jersey 07950 USA Telephone: +1 973 984-1853
AN INTRODUCTION TO USING PROSIM FOR BUSINESS PROCESS SIMULATION AND ANALYSIS. Perakath C. Benjamin Dursun Delen Madhav Erraguntla
 Proceedings of the 1998 Winter Simulation Conference D.J. Medeiros, E.F. Watson, J.S. Carson and M.S. Manivannan, eds. AN INTRODUCTION TO USING PROSIM FOR BUSINESS PROCESS SIMULATION AND ANALYSIS Perakath
Proceedings of the 1998 Winter Simulation Conference D.J. Medeiros, E.F. Watson, J.S. Carson and M.S. Manivannan, eds. AN INTRODUCTION TO USING PROSIM FOR BUSINESS PROCESS SIMULATION AND ANALYSIS Perakath
COAA EPCM CONTRACT PHILOSOPHY. COAA EPCM Contract Committee
 COAA EPCM CONTRACT PHILOSOPHY COAA EPCM Contract Committee 1. Introduction The COAA EPCM Contract Committee, consisting of owner, contractor and affiliate members, has developed a standard form EPCM Contract
COAA EPCM CONTRACT PHILOSOPHY COAA EPCM Contract Committee 1. Introduction The COAA EPCM Contract Committee, consisting of owner, contractor and affiliate members, has developed a standard form EPCM Contract
OPTIMIZING EARTHMOVING OPERATIONS USING OBJECT-ORIENTED SIMULATION. Mohamed Marzouk Osama Moselhi
 Proceedings of the 2000 Winter Simulation Conference J A Joines, R R Barton, K Kang, and P A Fishwick, eds OPTIMIZING EARTHMOVING OPERATIONS USING OBJECT-ORIENTED SIMULATION Mohamed Marzouk Osama Moselhi
Proceedings of the 2000 Winter Simulation Conference J A Joines, R R Barton, K Kang, and P A Fishwick, eds OPTIMIZING EARTHMOVING OPERATIONS USING OBJECT-ORIENTED SIMULATION Mohamed Marzouk Osama Moselhi
ORACLE HYPERION PLANNING
 ORACLE HYPERION PLANNING KEY FEATURES AND BENEFITS KEY FEATURES: Multi-dimensional / multi user planning with a powerful business rules engine Flexible workflow and plan management capabilities Comprehensive
ORACLE HYPERION PLANNING KEY FEATURES AND BENEFITS KEY FEATURES: Multi-dimensional / multi user planning with a powerful business rules engine Flexible workflow and plan management capabilities Comprehensive
A Taxonomy-Based Model for Identifying Risks
 A Taxonomy-Based Model for Identifying Risks Sebastian Maniasi, Paola Britos and Ramón García-Martínez Global Software Group (GSG) Argentina Motorola Argentina Centro de Software Software & Knowledge Engineering
A Taxonomy-Based Model for Identifying Risks Sebastian Maniasi, Paola Britos and Ramón García-Martínez Global Software Group (GSG) Argentina Motorola Argentina Centro de Software Software & Knowledge Engineering
A Study on Critical Risk Factors involved Life Cycle of construction Projects
 A Study on Critical Risk Factors involved Life Cycle of construction Projects R.Sakthiganesh 1, Dr.S.Suchithra 2, S.Saravanakumar 3 1 PostGraduate student, Department of Civil Engineering, kongu Engineering
A Study on Critical Risk Factors involved Life Cycle of construction Projects R.Sakthiganesh 1, Dr.S.Suchithra 2, S.Saravanakumar 3 1 PostGraduate student, Department of Civil Engineering, kongu Engineering
Spectrum PowerCC Energy Control The Control System for Industrial Networks
 Spectrum PowerCC Energy Control The Control System for Industrial Networks Power Transmission and Distribution Competition in industry is leading to increased cost pressure, which is forcing many companies
Spectrum PowerCC Energy Control The Control System for Industrial Networks Power Transmission and Distribution Competition in industry is leading to increased cost pressure, which is forcing many companies
INTRODUCTION TO AUDITING GUIDE
 NEOXEN MODUS METHODOLOGY RELEASE 5.0.0.2 INTRODUCTION TO AUDITING GUIDE D O C U M E N T A T I O N L I C E N S E This documentation, as well as the software described in it, is furnished under license
NEOXEN MODUS METHODOLOGY RELEASE 5.0.0.2 INTRODUCTION TO AUDITING GUIDE D O C U M E N T A T I O N L I C E N S E This documentation, as well as the software described in it, is furnished under license
Summary of 47 project management processes (PMBOK Guide, 5 th edition, 2013)
 Summary of 47 project management processes (PMBOK Guide, 5 th edition, 2013) Integration Management: processes & activities needed to properly coordinate all aspects of the project to meet stakeholder
Summary of 47 project management processes (PMBOK Guide, 5 th edition, 2013) Integration Management: processes & activities needed to properly coordinate all aspects of the project to meet stakeholder
QuickBill for Dentrix
 QuickBill 3.3.7 for Dentrix USER S GUIDE www.dentrix.com/eservices 1-800-734-5561 2 PUBLICATION DATE November 2016 COPYRIGHT 1987-2016 Henry Schein, Inc. Dentrix, Henry Schein, and the S logo are registered
QuickBill 3.3.7 for Dentrix USER S GUIDE www.dentrix.com/eservices 1-800-734-5561 2 PUBLICATION DATE November 2016 COPYRIGHT 1987-2016 Henry Schein, Inc. Dentrix, Henry Schein, and the S logo are registered
Requirements Analysis and Design Definition. Chapter Study Group Learning Materials
 Requirements Analysis and Design Definition Chapter Study Group Learning Materials 2015, International Institute of Business Analysis (IIBA ). Permission is granted to IIBA Chapters to use and modify this
Requirements Analysis and Design Definition Chapter Study Group Learning Materials 2015, International Institute of Business Analysis (IIBA ). Permission is granted to IIBA Chapters to use and modify this
Risk Management of the Equipment Supply Process in the Power Plant Projects in Iran
 Risk Management of the Equipment Supply Process in the Power Plant Projects in Iran Hannaneh Etemadinia, PhD. Student, and Mahdi Tavakolan, PhD. Department of Construction Engineering and Management, School
Risk Management of the Equipment Supply Process in the Power Plant Projects in Iran Hannaneh Etemadinia, PhD. Student, and Mahdi Tavakolan, PhD. Department of Construction Engineering and Management, School
Architecture Exception Governance
 Architecture Exception Governance Ondruska Marek Abstract The article presents the whole model of IS/IT architecture governance. As first, the assumptions of presented model are set. As next, there is
Architecture Exception Governance Ondruska Marek Abstract The article presents the whole model of IS/IT architecture governance. As first, the assumptions of presented model are set. As next, there is
Question 2: Requirements Engineering. Part a. Answer: Requirements Engineering Process
 Question 2: Requirements Engineering Part a. Answer: Requirements Engineering Process The requirements engineering process varies from domain to domain. But the general activities involved are: Elicitation
Question 2: Requirements Engineering Part a. Answer: Requirements Engineering Process The requirements engineering process varies from domain to domain. But the general activities involved are: Elicitation
RISK.03. Project Management Oversight: An Effective Risk Management Tool for EPC/Design-Build Projects
 RISK.03 Project Management Oversight: An Effective Risk Management Tool for EPC/Design-Build Projects A s the popularity of the EPC (engineer, procure, construct) contracts increases along with the size
RISK.03 Project Management Oversight: An Effective Risk Management Tool for EPC/Design-Build Projects A s the popularity of the EPC (engineer, procure, construct) contracts increases along with the size
Knowledge Areas According to the PMBOK edition 5. Chapter 4 - Integration
 Knowledge Areas According to the PMBOK edition 5 Chapter 4 - Integration 4.1 - Develop Project Charter Process Project statement of work Expert Judgment Project charter Business case Facilitation techniques
Knowledge Areas According to the PMBOK edition 5 Chapter 4 - Integration 4.1 - Develop Project Charter Process Project statement of work Expert Judgment Project charter Business case Facilitation techniques
Step 2: Analyze Stakeholders/Drivers and Define the Target Business Strategy
 Step 2: Analyze Stakeholders/Drivers and Define the Target Business Strategy Version 1.5, December 2006 1. Step Description and Purpose The step Analyze Stakeholders/Drivers and Define the Target Business
Step 2: Analyze Stakeholders/Drivers and Define the Target Business Strategy Version 1.5, December 2006 1. Step Description and Purpose The step Analyze Stakeholders/Drivers and Define the Target Business
Concept Searching is unique. No other statistical search and classification vendor puts compound terms in their index. This technique delivers high
 1 2 Concept Searching is unique. No other statistical search and classification vendor puts compound terms in their index. This technique delivers high precision without the loss of recall. Why Classification?
1 2 Concept Searching is unique. No other statistical search and classification vendor puts compound terms in their index. This technique delivers high precision without the loss of recall. Why Classification?
Requirements Engineering. Andreas Zeller Saarland University
 Requirements Engineering Software Engineering Andreas Zeller Saarland University Communication project initiation requirements gathering Planning estimating scheduling tracking Waterfall Model (1968) Modeling
Requirements Engineering Software Engineering Andreas Zeller Saarland University Communication project initiation requirements gathering Planning estimating scheduling tracking Waterfall Model (1968) Modeling
RISK MANAGEMENT STEPS Lecture 2
 RISK MANAGEMENT STEPS Lecture 2 1 RISK MANAGEMENT STEPS Identification Updating Assessment Analysis Mitigation 2 RISK IDENTIFICATION Risk identification is a critical phase The result of this phase will
RISK MANAGEMENT STEPS Lecture 2 1 RISK MANAGEMENT STEPS Identification Updating Assessment Analysis Mitigation 2 RISK IDENTIFICATION Risk identification is a critical phase The result of this phase will
GOVERNANCE. Overview. The Governance Module can address all applicable standards and regulations.
 GOVERNANCE Overview The platform facilitates the design and development of Information Security Frameworks supported by embedded content and process models that vary depending on the industry sector as
GOVERNANCE Overview The platform facilitates the design and development of Information Security Frameworks supported by embedded content and process models that vary depending on the industry sector as
Fulfilling CDM Phase II with Identity Governance and Provisioning
 SOLUTION BRIEF Fulfilling CDM Phase II with Identity Governance and Provisioning SailPoint has been selected as a trusted vendor by the Continuous Diagnostics and Mitigation (CDM) and Continuous Monitoring
SOLUTION BRIEF Fulfilling CDM Phase II with Identity Governance and Provisioning SailPoint has been selected as a trusted vendor by the Continuous Diagnostics and Mitigation (CDM) and Continuous Monitoring
BASICS of CONSTRUCTION PROJECT MANAGEMENT
 BASICS of CONSTRUCTION PROJECT MANAGEMENT 1 Outline What is a project? What is a construction project? Program & Portfolio Characteristics of a Construction Life Cycle Areas to Manage in Construction Comparison
BASICS of CONSTRUCTION PROJECT MANAGEMENT 1 Outline What is a project? What is a construction project? Program & Portfolio Characteristics of a Construction Life Cycle Areas to Manage in Construction Comparison
Oracle Stores User Training Manual Version of 123. Oracle Stores User Manual Version 1.0
 Oracle Stores User Training Manual Version 1.0 1 of 123 Oracle Stores User Manual Version 1.0 STORES USER MANUAL DOCUMENT Implementation of Management Information System (MIS) Including Financial Management
Oracle Stores User Training Manual Version 1.0 1 of 123 Oracle Stores User Manual Version 1.0 STORES USER MANUAL DOCUMENT Implementation of Management Information System (MIS) Including Financial Management
Jane Systems Ltd. Tel : /6
 1 /6 Jane s innovative suite of applications covers all aspects of HR including Recruitment, Payroll, Skills, Talent & Performance Management, Learning & Development, Salary Review, Self-Service, Workflows
1 /6 Jane s innovative suite of applications covers all aspects of HR including Recruitment, Payroll, Skills, Talent & Performance Management, Learning & Development, Salary Review, Self-Service, Workflows
Aon Infrastructure Solutions
 Aon Risk Solutions Aon Infrastructure Solutions Aon Infrastructure Solutions Alternative Project Delivery Risk Advisors Aon plc is the leading global provider of risk management services, insurance and
Aon Risk Solutions Aon Infrastructure Solutions Aon Infrastructure Solutions Alternative Project Delivery Risk Advisors Aon plc is the leading global provider of risk management services, insurance and
PRINCESS NOURA UNIVESRSITY. Project Management BUS 302. Reem Al-Qahtani
 PRINCESS NOURA UNIVESRSITY Project BUS 302 Reem Al-Qahtani This is only for helping reading the PMBOK it has our notes for focusing on the book Project Framework What is PMBOK? o PMBOK= Project Body of
PRINCESS NOURA UNIVESRSITY Project BUS 302 Reem Al-Qahtani This is only for helping reading the PMBOK it has our notes for focusing on the book Project Framework What is PMBOK? o PMBOK= Project Body of
Series on increasing project management contributions to helping achieve broader ends 1 Article 3 of 4
 Series on increasing project management contributions to helping achieve broader ends 1 Article 3 of 4 Organizational strategic plans, projects, and strategic outcomes BACKGROUND By Alan Stretton In the
Series on increasing project management contributions to helping achieve broader ends 1 Article 3 of 4 Organizational strategic plans, projects, and strategic outcomes BACKGROUND By Alan Stretton In the
For the people who count.
 For the people who count. The Value of Function Point Analysis Software organisations in all industries suffer from the inability to effectively estimate software projects, value software assets and objectively
For the people who count. The Value of Function Point Analysis Software organisations in all industries suffer from the inability to effectively estimate software projects, value software assets and objectively
IBM Data Security Services for activity compliance monitoring and reporting log analysis management
 Improving your compliance posture and reducing risk through log analysis management IBM Data Security Services for activity compliance monitoring and reporting log analysis management Highlights Provide
Improving your compliance posture and reducing risk through log analysis management IBM Data Security Services for activity compliance monitoring and reporting log analysis management Highlights Provide
HOW INTEGRATION WORKS...3
 Contents INTRODUCTION...1 How to Use This Guide... 1 Software Editions Supported... 2 HOW INTEGRATION WORKS...3 INTEGRATION RULES... 4 INTEGRATION SETTINGS... 8 Send Settings... 8 Get Settings... 9 Account
Contents INTRODUCTION...1 How to Use This Guide... 1 Software Editions Supported... 2 HOW INTEGRATION WORKS...3 INTEGRATION RULES... 4 INTEGRATION SETTINGS... 8 Send Settings... 8 Get Settings... 9 Account
Advisory Circular. Date: DRAFT Initiated by: AIR-110
 U.S. Department of Transportation Federal Aviation Administration Advisory Circular Subject: DETERMINING THE CLASSIFICATION OF A CHANGE TO TYPE DESIGN. Date: DRAFT Initiated by: AIR-110 AC No: 21.93-1
U.S. Department of Transportation Federal Aviation Administration Advisory Circular Subject: DETERMINING THE CLASSIFICATION OF A CHANGE TO TYPE DESIGN. Date: DRAFT Initiated by: AIR-110 AC No: 21.93-1
Requirements Engineering
 Requirements Engineering Software Engineering Andreas Zeller Saarland University Requirements Engineering The Real World Requirements Engineering A description of what the system should do (but not how)
Requirements Engineering Software Engineering Andreas Zeller Saarland University Requirements Engineering The Real World Requirements Engineering A description of what the system should do (but not how)
Contents About This Guide... 5 Upgrade Overview... 5 Examining Your Upgrade Criteria... 7 Upgrade Best Practices... 8
 P6 EPPM Upgrade Best Practices Guide 16 R2 September 2016 Contents About This Guide... 5 Upgrade Overview... 5 Upgrade Process... 5 Assessing the Technical Environment... 6 Preparing for the Upgrade...
P6 EPPM Upgrade Best Practices Guide 16 R2 September 2016 Contents About This Guide... 5 Upgrade Overview... 5 Upgrade Process... 5 Assessing the Technical Environment... 6 Preparing for the Upgrade...
Oracle Service Cloud. New Feature Summary. Release 18C ORACLE
 Oracle Service Cloud Release 18C New Feature Summary ORACLE TABLE OF CONTENTS Revision History 3 Overview 3 Agent Browser Desktop Automation 3 Workflow Enable Save Option for Workflow Elements 3 Workflow
Oracle Service Cloud Release 18C New Feature Summary ORACLE TABLE OF CONTENTS Revision History 3 Overview 3 Agent Browser Desktop Automation 3 Workflow Enable Save Option for Workflow Elements 3 Workflow
10/16/2018. Kingston Governance, Risk, and Compliance
 10/16/2018 Kingston Governance, Risk, and Compliance Contents Contents... 4 Domain separation in... 8 Policy and Compliance Management...9 Understanding Policy and Compliance Management... 10 Risk Management...87
10/16/2018 Kingston Governance, Risk, and Compliance Contents Contents... 4 Domain separation in... 8 Policy and Compliance Management...9 Understanding Policy and Compliance Management... 10 Risk Management...87
Project Planning & Management. Lecture 11 Project Risk Management
 Lecture 11 Project Risk Management The Importance of Project Risk Management PMBOK definition of Project Risk An uncertain event or condition that, if it occurs, has a positive or negative effect on the
Lecture 11 Project Risk Management The Importance of Project Risk Management PMBOK definition of Project Risk An uncertain event or condition that, if it occurs, has a positive or negative effect on the
CHAPTER CHAPTER 3. PROJECT MANAGEMENT TOOLS (PART II)
 CHAPTER 3 CHAPTER 3. PROJECT MANAGEMENT TOOLS (PART II) Project management tools (Parte II) This document represents the intellectual property of the Inter-American Development Bank (IDB) and the Inter-American
CHAPTER 3 CHAPTER 3. PROJECT MANAGEMENT TOOLS (PART II) Project management tools (Parte II) This document represents the intellectual property of the Inter-American Development Bank (IDB) and the Inter-American
Jakarta ServiceNow Governance Risk Compliance. Last updated: February 13, 2019
 Jakarta Governance Risk Compliance Last updated: February 13, 2019 Jakarta Table of Contents Table of Contents Governance, Risk, and Compliance (GRC)... 4 Policy and Compliance Management... 7 Understanding
Jakarta Governance Risk Compliance Last updated: February 13, 2019 Jakarta Table of Contents Table of Contents Governance, Risk, and Compliance (GRC)... 4 Policy and Compliance Management... 7 Understanding
User Guide. User Guide to Recurring Billing and Storage. Setting up and using the Recurring Billing system
 User Guide User Guide to Recurring Billing and Storage Setting up and using the Recurring Billing system Version 3.7 (Fall 2008) User Guide to Recurring Billing and Storage Copyright Copyright 1997-2009
User Guide User Guide to Recurring Billing and Storage Setting up and using the Recurring Billing system Version 3.7 (Fall 2008) User Guide to Recurring Billing and Storage Copyright Copyright 1997-2009
The Quality Assurance Reviews at Statistics Canada
 The Quality Assurance Reviews at Statistics Canada Laurie Reedman, Claude Julien Statistics Canada 100 Tunney s Pasture Driveway, Ottawa (Ontario), K1A 0T6, Canada 1. Description of the Quality Assurance
The Quality Assurance Reviews at Statistics Canada Laurie Reedman, Claude Julien Statistics Canada 100 Tunney s Pasture Driveway, Ottawa (Ontario), K1A 0T6, Canada 1. Description of the Quality Assurance
Project risk management
 Project risk management 6th African Rift Geothermal Conference ARGeo-C6 Short Course 1 Project Management for Geothermal Development Carine Chatenay, Verkís Learning outcome How to develop risk management
Project risk management 6th African Rift Geothermal Conference ARGeo-C6 Short Course 1 Project Management for Geothermal Development Carine Chatenay, Verkís Learning outcome How to develop risk management
Systematic Project Management
 Systematic Project Management Karlos A. Artto at HUT S-72.124 Product Development of Telecommunication Systems Lecture on March 16, 2001 Systematic Project Management CONTENTS 1 What are the capabilities
Systematic Project Management Karlos A. Artto at HUT S-72.124 Product Development of Telecommunication Systems Lecture on March 16, 2001 Systematic Project Management CONTENTS 1 What are the capabilities
PMP MOCK EXAMS BASED ON PMBOK 5TH EDITION
 PMP MOCK EXAMS http://www.tutorialspoint.com/pmp-exams/pmp_mock_exams_set4.htm Copyright tutorialspoint.com BASED ON PMBOK 5TH EDITION Here are 200 objective type sample questions and their answers are
PMP MOCK EXAMS http://www.tutorialspoint.com/pmp-exams/pmp_mock_exams_set4.htm Copyright tutorialspoint.com BASED ON PMBOK 5TH EDITION Here are 200 objective type sample questions and their answers are
ISO whitepaper, January Inspiring Business Confidence.
 Inspiring Business Confidence. ISO 31000 whitepaper, January 2015 Author: Graeme Parker enquiries@parkersolutionsgroup.co.uk www.parkersolutionsgroup.co.uk ISO 31000 is an International Standard for Risk
Inspiring Business Confidence. ISO 31000 whitepaper, January 2015 Author: Graeme Parker enquiries@parkersolutionsgroup.co.uk www.parkersolutionsgroup.co.uk ISO 31000 is an International Standard for Risk
CHAPTER-8 DEVELOPMENT OF SPARCS
 CHAPTER-8 DEVELOPMENT OF SPARCS--SUPPLY-CHAIN PARAMETERS CLASSIFICATION SYSTEM FOR SMALL SCALE INDUSTRY The performance of the material-procurement decisions is heavily dependent on the combination of
CHAPTER-8 DEVELOPMENT OF SPARCS--SUPPLY-CHAIN PARAMETERS CLASSIFICATION SYSTEM FOR SMALL SCALE INDUSTRY The performance of the material-procurement decisions is heavily dependent on the combination of
Estimating post- and pre-mitigation contingency in construction
 Risk Analysis IX 243 Estimating post- and pre-mitigation contingency in construction A. Salah & O. Moselhi Department of Building, Civil and Environmental Engineering, Concordia University, Canada Abstract
Risk Analysis IX 243 Estimating post- and pre-mitigation contingency in construction A. Salah & O. Moselhi Department of Building, Civil and Environmental Engineering, Concordia University, Canada Abstract
Vendor Cloud Platinum Package: Included Capabilities
 Solution Overview Third-Party Risk Management Vendor Cloud Platinum Package: Included Capabilities The Vendor Cloud Platinum package provides the highest level of risk management capabilities, offering
Solution Overview Third-Party Risk Management Vendor Cloud Platinum Package: Included Capabilities The Vendor Cloud Platinum package provides the highest level of risk management capabilities, offering
2005 National Information Services - QuickBill for Easy Dental version 3.0. QuickBill. for Easy Dental. Version 3.0
 QuickBill for Easy Dental Version 3.0 727 E. Utah Valley Dr., Ste. 750 American Fork, UT 84003 Tel: (800) 734-5561 Fax: (801) 847-3800 1 SEPTEMBER 2005 COPYRIGHT 2005 Easy Dental Systems, Inc. and National
QuickBill for Easy Dental Version 3.0 727 E. Utah Valley Dr., Ste. 750 American Fork, UT 84003 Tel: (800) 734-5561 Fax: (801) 847-3800 1 SEPTEMBER 2005 COPYRIGHT 2005 Easy Dental Systems, Inc. and National
Project Management Courses
 "A well planned project will give results exactly as planned." Project Management Courses Professional Development Training has a specialised division of Project Management experts that will tailor the
"A well planned project will give results exactly as planned." Project Management Courses Professional Development Training has a specialised division of Project Management experts that will tailor the
SmartPlant Spoolgen for Fabrication and Construction
 WHITE PAPER SmartPlant Spoolgen for Fabrication and Construction Fast and Accurate Spool and Erection Isometrics Contents 1. Introduction... 1 1.1. For the Owner Operator... 2 1.2. For the EPC... 2 1.3.
WHITE PAPER SmartPlant Spoolgen for Fabrication and Construction Fast and Accurate Spool and Erection Isometrics Contents 1. Introduction... 1 1.1. For the Owner Operator... 2 1.2. For the EPC... 2 1.3.
IAASB CAG Public Session (March 2018) CONFORMING AND CONSEQUENTIAL AMENDMENTS ARISING FROM DRAFT PROPOSED ISA 540 (REVISED) 1
 Agenda Item B.4 CONFORMING AND CONSEQUENTIAL AMENDMENTS ARISING FROM DRAFT PROPOSED ISA 540 (REVISED) 1 ISA 200, Overall Objectives of the Independent Auditor and the Conduct of an Audit in Accordance
Agenda Item B.4 CONFORMING AND CONSEQUENTIAL AMENDMENTS ARISING FROM DRAFT PROPOSED ISA 540 (REVISED) 1 ISA 200, Overall Objectives of the Independent Auditor and the Conduct of an Audit in Accordance
Business Analysis for Practitioners - Introduction
 Business Analysis for Practitioners - Introduction COURSE STRUCTURE Introduction to Business Analysis Module 1 Needs Assessment Module 2 Business Analysis Planning Module 3 Requirements Elicitation and
Business Analysis for Practitioners - Introduction COURSE STRUCTURE Introduction to Business Analysis Module 1 Needs Assessment Module 2 Business Analysis Planning Module 3 Requirements Elicitation and
CORROSION MANAGEMENT MATURITY MODEL
 CORROSION MANAGEMENT MATURITY MODEL CMMM Model Definition AUTHOR Jeff Varney Executive Director APQC Page 1 of 35 TABLE OF CONTENTS OVERVIEW... 5 I. INTRODUCTION... 6 1.1 The Need... 6 1.2 The Corrosion
CORROSION MANAGEMENT MATURITY MODEL CMMM Model Definition AUTHOR Jeff Varney Executive Director APQC Page 1 of 35 TABLE OF CONTENTS OVERVIEW... 5 I. INTRODUCTION... 6 1.1 The Need... 6 1.2 The Corrosion
Design of an Integrated Model for Development of Business and Enterprise Systems
 International Journal of Research Studies in Computer Science and Engineering (IJRSCSE) Volume 2, Issue 5, May 2015, PP 50-57 ISSN 2349-4840 (Print) & ISSN 2349-4859 (Online) www.arcjournals.org Design
International Journal of Research Studies in Computer Science and Engineering (IJRSCSE) Volume 2, Issue 5, May 2015, PP 50-57 ISSN 2349-4840 (Print) & ISSN 2349-4859 (Online) www.arcjournals.org Design
CONTEMPORARY APPROACHES TO PROJECT RISK MANAGEMENT: ASSESSMENT & RECOMMENDATIONS
 CONTEMPORARY APPROACHES TO PROJECT RISK MANAGEMENT: ASSESSMENT & RECOMMENDATIONS Prepared by: Mohamed Noordin Yusuff IT Security Officer Dip.ECC, SDip.IS, M.IntSecMgmt(Distinction) 1 INTRODUCTION In order
CONTEMPORARY APPROACHES TO PROJECT RISK MANAGEMENT: ASSESSMENT & RECOMMENDATIONS Prepared by: Mohamed Noordin Yusuff IT Security Officer Dip.ECC, SDip.IS, M.IntSecMgmt(Distinction) 1 INTRODUCTION In order
A purposefully designed core banking system engineered and developed for African microfinance institutions
 A purposefully designed core banking system engineered and developed for African microfinance institutions Introducing XCORE FlexBank Despite the recent advances in technology, many MFIs, especially in
A purposefully designed core banking system engineered and developed for African microfinance institutions Introducing XCORE FlexBank Despite the recent advances in technology, many MFIs, especially in
RiskyProject. Project Risk Management Software
 Project Risk Management Software Intaver Institute Inc. 303, 6707, Elbow Drive S.W, Calgary, AB, Canada Tel: +1 (403) 692-2252 Fax: +1 (403) 459-4533 www.intaver.com RiskyProject 1 Project Scheduling Risk
Project Risk Management Software Intaver Institute Inc. 303, 6707, Elbow Drive S.W, Calgary, AB, Canada Tel: +1 (403) 692-2252 Fax: +1 (403) 459-4533 www.intaver.com RiskyProject 1 Project Scheduling Risk
Information Technology Independent Verification and Validation
 Florida Department of Management Services Information Technology Independent Verification and Validation RFP No. Work Plan and Methodology ; 2:30 PM EST 2150 River Plaza Drive Suite 380 Sacramento California
Florida Department of Management Services Information Technology Independent Verification and Validation RFP No. Work Plan and Methodology ; 2:30 PM EST 2150 River Plaza Drive Suite 380 Sacramento California
The software process
 Software Processes The software process A structured set of activities required to develop a software system Specification; Design; Validation; Evolution. A software process model is an abstract representation
Software Processes The software process A structured set of activities required to develop a software system Specification; Design; Validation; Evolution. A software process model is an abstract representation
Smart Security CyCop Technology Integration
 Technology Integration The Next Generation of Security Workforce Management CYCOP INTEGRATION STEPS is an essential tool in s performance management toolbox. With CyCop, customers can leverage technology
Technology Integration The Next Generation of Security Workforce Management CYCOP INTEGRATION STEPS is an essential tool in s performance management toolbox. With CyCop, customers can leverage technology
Project Management Training Brochure
 Project Management Training Brochure We develop project management training sessions by integrating our 40 years of combined practitioner experience with the most current project management knowledgebase
Project Management Training Brochure We develop project management training sessions by integrating our 40 years of combined practitioner experience with the most current project management knowledgebase
AGENCY FOR STATE TECHNOLOGY
 AGENCY FOR STATE TECHNOLOGY PROJECT RISK & COMPLEXITY ASSESSMENT TOOL Risk & Complexity Assessment Model for State Information Technology Projects Purpose: In order to determine the level of risk associated
AGENCY FOR STATE TECHNOLOGY PROJECT RISK & COMPLEXITY ASSESSMENT TOOL Risk & Complexity Assessment Model for State Information Technology Projects Purpose: In order to determine the level of risk associated
NAVIGATING PMO IMPROVEMENT WITH OPM3
 NAVIGATING PMO IMPROVEMENT WITH OPM3 MAY 8, 2014 PITTSBURGH PMI CHAPTER CHRIS ULDRIKS PRESIDENT & PRINCIPAL CONSULTANT OPM3, PMBOK, and PMI are registered trademarks of the Project Management Institute
NAVIGATING PMO IMPROVEMENT WITH OPM3 MAY 8, 2014 PITTSBURGH PMI CHAPTER CHRIS ULDRIKS PRESIDENT & PRINCIPAL CONSULTANT OPM3, PMBOK, and PMI are registered trademarks of the Project Management Institute
How to Successfully Collect, Analyze and Implement User Requirements Gerry Clancy Glenn Berger
 Esri International User Conference San Diego, California Technical Workshops July 24, 2012 How to Successfully Collect, Analyze and Implement User Requirements Gerry Clancy Glenn Berger Requirements Gathering
Esri International User Conference San Diego, California Technical Workshops July 24, 2012 How to Successfully Collect, Analyze and Implement User Requirements Gerry Clancy Glenn Berger Requirements Gathering
Smart Security CyCop Workforce Management Technology
 Workforce Management Technology The Next Generation Information Management and Workforce Management Technology Security operations at commercial properties are uniquely challenging. Often fulfilling a
Workforce Management Technology The Next Generation Information Management and Workforce Management Technology Security operations at commercial properties are uniquely challenging. Often fulfilling a
Requirements elicitation: Finding the Voice of the Customer
 Requirements elicitation: Finding the Voice of the Customer Establishing customer requirements for a software system Identify sources of user requirements on your project Identify different classes of
Requirements elicitation: Finding the Voice of the Customer Establishing customer requirements for a software system Identify sources of user requirements on your project Identify different classes of
PROCEDURES FOR CHANGE MANAGEMENT IN THE REALIZATION PHASE OF CONSTRUCTION PROJECTS
 PROCEDURES FOR CHANGE MANAGEMENT IN THE REALIZATION PHASE OF CONSTRUCTION PROJECTS Maja-Marija Nahod 1 and Mladen Radujković Construction Management Department, Faculty of Civil Engineering, University
PROCEDURES FOR CHANGE MANAGEMENT IN THE REALIZATION PHASE OF CONSTRUCTION PROJECTS Maja-Marija Nahod 1 and Mladen Radujković Construction Management Department, Faculty of Civil Engineering, University
Project Management Body of Knowledge (PMBOK)
 Project Management Body of Knowledge (PMBOK) Enterprise & Project Management Please note that these slides are not intended as a substitute to reading the recommended text for this course. Objectives Explain
Project Management Body of Knowledge (PMBOK) Enterprise & Project Management Please note that these slides are not intended as a substitute to reading the recommended text for this course. Objectives Explain
METHODS OF PRACTICAL PROJECT CATEGORIZATION
 THE PURPOSES AND METHODS OF PRACTICAL PROJECT CATEGORIZATION Russell D. Archibald, MSc Fellow PMI and APM/IPMA, PMP 1 Objectives of This Presentation To discuss the purposes p of and need for a project
THE PURPOSES AND METHODS OF PRACTICAL PROJECT CATEGORIZATION Russell D. Archibald, MSc Fellow PMI and APM/IPMA, PMP 1 Objectives of This Presentation To discuss the purposes p of and need for a project
ipm it s project management Integrated. Intuitive. Intelligent IPM PROJECT MANAGEMENT WITH INTEGRATION TO MICROSOFT DYNAMICS NAV
 ipm it s project management Integrated. Intuitive. Intelligent IPM PROJECT MANAGEMENT WITH INTEGRATION TO MICROSOFT DYNAMICS NAV IPM, by IPM Global, is a next generation project management suite that provides
ipm it s project management Integrated. Intuitive. Intelligent IPM PROJECT MANAGEMENT WITH INTEGRATION TO MICROSOFT DYNAMICS NAV IPM, by IPM Global, is a next generation project management suite that provides
Please find below a sampling of the various implementation documents and spreadsheets that are part of the Timberline Production Management Solution.
 Please find below a sampling of the various implementation documents and spreadsheets that are part of the Timberline Production Management Solution. Production Management Implementation Documentation
Please find below a sampling of the various implementation documents and spreadsheets that are part of the Timberline Production Management Solution. Production Management Implementation Documentation
RiskyProject Lite 7. Getting Started Guide. Intaver Institute Inc. Project Risk Management Software.
 RiskyProject Lite 7 Project Risk Management Software Getting Started Guide Intaver Institute Inc. www.intaver.com email: info@intaver.com Chapter 1: Introduction to RiskyProject 3 What is RiskyProject?
RiskyProject Lite 7 Project Risk Management Software Getting Started Guide Intaver Institute Inc. www.intaver.com email: info@intaver.com Chapter 1: Introduction to RiskyProject 3 What is RiskyProject?
Managing Risk with PM 2
 Managing Risk with PM 2 lex.vander.helm@capgemini.com Lex van der Helm Lead trainer - Capgemini Academy Introduction Risk Risk Management Risk Management in PM 2 Process Steps & Artefacts 2 Speaker's name
Managing Risk with PM 2 lex.vander.helm@capgemini.com Lex van der Helm Lead trainer - Capgemini Academy Introduction Risk Risk Management Risk Management in PM 2 Process Steps & Artefacts 2 Speaker's name
GAHIMSS Chapter. CPHIMS Review Session. Systems Analysis. Stephanie Troncalli, Healthcare IT Strategist Himformatics July 22, 2016
 GAHIMSS Chapter CPHIMS Review Session Systems Analysis Stephanie Troncalli, Healthcare IT Strategist Himformatics July 22, 2016 CPHIMS Competency Areas CPHIMS Examination Content Outline (effective February,
GAHIMSS Chapter CPHIMS Review Session Systems Analysis Stephanie Troncalli, Healthcare IT Strategist Himformatics July 22, 2016 CPHIMS Competency Areas CPHIMS Examination Content Outline (effective February,
