Internal Audit s Role in Third Party Risk Management (TPRM)
|
|
|
- Elizabeth Perkins
- 5 years ago
- Views:
Transcription
1 Internal Audit s Role in Third (TPRM) Jon Pastore, Nick Fullmer
2 Third (TPRM) Framework What is Third? Third Party risk management is focused on understanding and managing risks associated with third parties with which the company does business and/or shares data. Risk Vendors Third Parties Affiliates The PwC TPRM Framework Risk Considerations Reputational Privacy TPRM s? Suppliers Joint Ventures Business Channels Business Associates Regulated Entities Marketing Partners Operational Financial Business Continuity Disaster Recovery Regulatory / Compliance Physical Security Subcontractor Technology Information Security Country Concentration 3
3 Vendor (VM) vs. TPRM What is Third? Vendor management accounts for the enterprise-wide relationships and the potentially numerous products/services that the third party may provide, including the service level and risk aspects. TPRM risk are conducted in parallel to the vendor management relationship and service level. Risk TPRM s? TPRM life cycle VM life cycle Business Case 1. Document Need 2. Cost Benefit Analysis 3. Determine business requirements 4. Determine ROI 5. Determine Third Party Base 6. Determine inherent risk 7. Document Source/No- Source Decision 8. Obtain Approval 9. Assign owners 10.For critical, involve appropriate levels within the organization Planning Due Diligence Contract Negotiation Ongoing Monitoring Termination Sourcing Analysis 1. Sourcing Approach - Competitive Bid RFP/RFI/ RFQ - Sole Source 2. Identify Third Parties - Existing - Potential 3. Third Party Rationalization 4. Single vs. Multiple Third Parties 5. Validation - Proof of Concepts - Pilot Third (TPRM) in BLUE BOLD Third Party Selection 1. Conduct RFI/ RFP/RFQ 2. Competitive Bid/Proposal Evaluation 3. Short List vs Single Finalist 4. Selection Criteria 5. Price vs Value 6. Due Diligence Assessments 7. Nature, Location and Ownership of Controls 8. Number of third parties to use Contracting 1. Contract Vehicle - MSA - SoW 2. Source paper 3. Standard clauses 4. Clauses to address open Issues 5. SLAs 6. Training 7. Fee Structure 8. Determine residual risk 9. Contract 10. A/P Setup 11. For critical, involve appropriate levels within the organization 12.Appropriate contractual controls if subcontractors will be used Ongoing monitoring 1. Transition Pre- Contract to Post- Contract 2. Track open issues to closure 3. Ongoing performance & risk monitoring 4. Ongoing due diligence &assessments 5. Ongoing site visits and reviews 6. Oversight and Supervision 7. Customer Complaint Handling 8. Third Party Contingency Plans 9. Re-certification 10. Spend 11. Monitoring and Reporting Cadence 12. Contract Administration Relationship exit 1. Finalize Exit Strategy 2. Provide Notifications 3. Risk Exposure assessment 4. Continuity Planning 5. Transition Planning and Execution 6. Transfer of assets and Information 7. Legal confirmation of transition 8. Payments, Penalties and final billings 4
4 Regulatory Considerations Risk? Why is Third TPRM s? Over the last 20+ years, multiple new regulations across industries have demanded increased focus on how organizations monitor their third parties. Regulatory changes in certain sectors may also have a down-stream impact on business partners. 5
5 Reputational Drivers for TPRM Risk? Why is Third TPRM s? Sample headlines involving Third Parties: $1.55 million settlement underscores the importance of executing HIPAA business associate agreements An investigation indicated that the hospital failed to have in place an appropriate business associate agreement, as required under the HIPAA Privacy and Security Rules, so that its business associate could perform certain payment and healthcare operations on its behalf. Breach by Vendor Awakens New Insider Threat Concerns Employees of a third party service provider violated privacy guidelines by accessing, without authorization, consumer accounts as part of a scheme to obtain customer names and partial SSNs, which were used to request unlock codes for stolen mobile phones. As a result of the breach, service provider agreed to settle an FCC investigation and pay a $25 million fine. Attackers Broke in via HVAC Company Attackers first broke into a leading retailer s network using network credentials stolen from a provider of refrigeration and HVAC systems. As a result, 70 million people were affected and the stolen customer information included names, mailing addresses, phone numbers as well as addresses. Hackers Used Third Party Log-on to Steal Data and s Hackers used stolen credentials from a third party to gain access to a retailer s network, where they exploited an unpatched vulnerability in the system to gain access to point-of-sale data. As a result, around 56 million payment cards accounts and 53 million addresses were stolen. CFPB Orders $59.5 Million Fine for Illegal Credit Card Practices The Consumer Financial Protection Bureau (CFPB) ordered a large credit card provider to refund an estimated $59.5 million to more than 335,000 consumers for illegal credit card practices after they discovered three subsidiaries, their vendors and telemarketers engaged in misleading and deceptive tactics to sell some of the company s credit card add-on products. 17,300 patients have their protected health information breached following a scam executed by a group posing as a vendor. Recent Ponemon Institute surveys reveal: Approximately half the respondents (49%) confirm their organization experienced a data breach cause by one of their vendors. 73% of the respondents see the number of cybersecurity incidents involving vendors increasing. 65% of the respondents also say it is difficult to manage cybersecurity incidents involving vendors. 6
6 Third (TPRM) Lifecycle Risk? Risk TPRM s? 7
7 Internal Audit Program Governance Structure Risk? Risk A TPRM strategy is supported by three lines of defense the first line lies within each individual Line of Business and is empowered by the second line who owns the provision of ongoing guidance, tool support, and facilitation of cross-business collaboration. The third line is responsible for evaluating the design and operating effectiveness of the Program. C Board Of Directors Risk Committee TPRM Steering Committee Risk Group B C. Third Line of Defense Independently test, verify and evaluate risk management controls against internal policies Report upon effectiveness of the TPRM s? Risk Group Risk Group Third Office (TPRMO) Risk Group Risk Group B. Second Line of Defense Design and assist in implementing company-wide risk framework and oversee enterprise risks Perform quality reviews and other targeted oversight practices to ensure that the line of business is compliant with internal policies/ external regulations Business Unit 1 Business Unit 2 Business Unit 3 A A. First Line of Defense BU managers and third party relationship owners are responsible for identifying, assessing and mitigating risk associated with their business Implement internal controls and practices that are consistent with company-wide policies & procedures 8
8 Third Process Risk? Planning Due Diligence Contracting Ongoing Monitoring Termination Risk TPRM s? Upon identification of a potential product / service to outsource to a Third Party, organizations should ensure there is a plan to manage the relationship. This plan should start by identifying the inherent risk profile of the product/ service to be outsourced. Prior to contract execution, organizations should conduct a review of potential third parties in order to select a Third Party with the appropriate qualifications, and to understand the Third Party s controls to mitigate the inherent risks posed by the relationship. The contract should clearly define expectations and responsibilities of the Third Party. The inclusion of appropriate contract clauses help to ensure the contract s enforceability, limits the organization s liability, and mitigates disputes about performance. Post contract execution and ongoing monitoring should include both risk and performance management. Issues should be identified, remediated, and escalated to appropriate decision authorities. Contingency plans should be maintained to ensure the can be transitioned in-house or to another Third Party. Termination may be required when a contract expires, the terms of the contract have been satisfied, in response to contract default, or in response to changes to the organization s or Third Party s business strategy. The organization should execute against written contingency plans to mitigate risk during termination. 9
9 Planning Third Party inventory and stratification Risk? Risk The inventory, risk rating and ongoing testing model enables a focus on efforts to establish the third party inventory, oversee services with higher levels of inherent risk. The model drives the ongoing due diligence process based on the inherent risk and the nature of the services provided. TPRM s? 10
10 Total Third Party Inventory from multiple data sources Establishing third party inventory Risk? Risk This framework will assist the Third Program in honing in on the inventory list by analyzing multiple sources in rapid manner and identifying the third parties that need to be included as part of the, and rated by inherent risk. Begin with A/P spend and LOB files to identify Vendors and Special Categories. Remove those that don t pose risk. Identify unique third parties and validate services against existing invoices & data sources. Remove those that don t pose risk. Perform cleansing and enhancement of third party data In-scope third party inventory for risk segmentation Inherent risk assessment Inherent Risk Rating TPRM s? Starting with commodity categories, we use a process to focus on those products/services that do and do not pose inherent risk and thus to be included as part of the. Common Third Inventory Data Attributes Third Party Name Third Party Parent Name/Associated Third Parties Product/Service Third Party Type (Business Process Outsourcing, Partnership, Technology etc.) Spend We then clean and enhance the existing third party data to be put into the inventory repository. Business Lines/Processes Supported by the Third Party Country/Region where Third Party is Based Contract Date (Engagement Date) Results of Third Classification Results of Third Assessments (e.g., Third Party Information Security Assessments) 11
11 Inherent risk assessment Risk? Risk TPRM s? The inherent risk assessment process allows for the sorting of third party services/products inherent risk scores and inherent risk ratings. Inherent risk determination Financial Information Security Legal & Regulatory Compliance Business Continuity Privacy Reputational Service Inherent Risk High Risk Moderate Risk Low Risk Very Low Risk Risk stratification structure 1 High Risk These third parties are handling high risk services, have a critical level of disruption, access to highly restricted types of data and are client facing. 2 Moderate Risk These third parties are handling high or medium risk services, have high level of disruption, access to restricted data and may be client facing. 3 Low Risk These third parties are handling medium risk services, have a moderate level of disruption, have access to restricted data and are not client facing. 4 Very Low Risk These third parties are handling low risk services, have a low level of disruption, do not have access to restricted data and are not client facing. 12
12 Third party stratification and assessment model Risk? Risk TPRM s? The inherent risk determination should be dictate what initial and ongoing due diligence are required based on input from applicable Subject Matter Specialists groups. Inherent risk determination Pre-Sourcing Inherent Risk drives SMS input and due diligence requirements Example Stakeholders Legal Third Office Subject Matter Specialists Business Unit Sponsor Compliance Sourcing & Other Key Stakeholders Initial due diligence performed during pre-contract utilizing and SMS input Legal should advise on potential sourcing of critical and when negotiating any contract or service agreement. The TPRM Office will assist with the execution of pre-contract and ongoing due diligence assessments. Subject Matter Specialists (e.g., InfoSec, BC/DR, Compliance, etc.) will either have input or will perform the pre-contract due diligence assessment from the perspective of the specialized risk area Business unit sponsors will be required to complete the inherent risk assessment and exit plan if required. Compliance will assist in determining applicable laws and regulations. Sourcing will advise the business in areas of strategic sourcing initiatives, and maintain process alignment with sourcing strategy. 13
13 Third party risks in relation to assessments Risk? The following correlates significant third party risks to the assessments utilized by organizations to evaluate the effectiveness of third party controls in place to mitigate risks. Risk TPRM s? 14
14 Risk assessment types Risk? Risk TPRM s? The following are examples of Third Party due diligence assessments performed on potential and existing third parties to understand the existing control environment and capabilities. Information Security & Privacy Security policies Change controls Encryption Logical access Control Monitoring, communication and connectivity Incident management Application management System development Customer contact Country Political Geographic Regulatory Legal Economic Travel Safety Operational People Process Financial Reporting Subcontractors Concentration Reputational Technology Technology Architecture Assets utilized Technology Roadmap Technological capabilities Litigation or ethical flags Media coverage OFAC or other factors Criminal and/or civil complaints Physical Security Fire Suppression Server Security & Conditions Data Centers Backup Power Sources Asset management Key Card & Facility Access Financial Going concern Liquidity Leverage Profitability Transaction Processing Compliance Regulatory requirements HIPAA CFPB GLBA Customer complaints handling, PCI Subcontractor Third Party Relationship Sub-Service Third Party Relationships Logical access Control Monitoring, communication and connectivity Business Continuity & Resiliency* Recovery Data Backup Offsite storage Media and vital records Data integrity 15 *Business Continuity includes Business Contingency ( BC ) planning and Disaster Recovery ( DR )
15 Due diligence Leveraging SOC 2 + reporting Risk? Risk TPRM s? 16 A SOC 2 + can provide an efficient and effective solution to facilitate burdensome third party assessments. It can enable you to reduce costs associated with accommodating multiple TPRM questionnaires and on-site TPRM assessment procedures. Challenges with prior solutions Questionnaires used by most organizations are large and open to interpretation Assessments are performed at the point of time No clear linkage between questions and risks being addressed Benefits to the organization Reduces time and money spent on resources Offers more time to proactively address risks Improves management of costs Decreases the number of on-site audits One to MANY reporting and remediation relationships as compared to the current customer Third response process SOC 2 + framework SOC2 report framework based on the AICPA guiding principles with insight for third party industry best practices Criteria agreed upon by the audit team and the organization (third party) that address customer concerns, outside of the scope of standard SSAE16/SOC1 and SOC2 control testing environments Conducted by independent firm SOC2 + Framework Third Principles Security, Confidentiality, Privacy, Availability, Processing Integrity Benefits to clients Reduces time and money spent on resources and travel Helps restore confidence Provides positive and independent analysis across a period of time, not just a point-in-time Reduces time for the assessment lifecycle
16 Due diligence and contracting Risk? In addition to generating a risk rating/segment based on the inherent risk of the relationship to your organization, the results of your pre-contract due diligence should drive contractual protections. Risk TPRM s? 17
17 Depth and Frequency of Ongoing Monitoring Ongoing Monitoring Risk? Inherent risks should drive the nature, timing and extent of used to monitor, oversee, and re-assess Third Party relationships. Risk TPRM s? Ongoing Monitoring Risk Scorecards / Satisfaction Surveys SLA Tracking 0% Very Low 40-50% Low 20-30% Moderate 10-15% High 3-5% 18
18 Termination Risk? Each third party termination will be unique; however, there are common decisions, considerations, and results that should be addressed with key stakeholders and executed with a defined plan and checklist. Risk Business Unit TPRM Office SMS Legal & Compliance Sourcing Consistent & continuous communication Third Parties/ Subcontractors Risk TPRM s? Termination decision Service Failure/Significant Customer Complaints Data Breach/Security Incident Regulatory/Legislative End of Contract Business Decision Product/Service Discontinued Termination considerations Product/Service Brought In-House Product/Service Transitioned to Alternate Third Party Customer Impact Operational Impact Patient Safety Contingency Procedures Oral & Implied Contracts Internal Employee Impact Termination result Interim Processes o NDA o Transfer Process Knowledge o Migrate or Destroy Information o Return or destruction o Ongoing safeguards o Ownership and control Costs o Monetary o Non-monetary Migrate/Sell Assets o Software/Intellectual Property o Hardware o Facilities Notification to Customers and Employees 19
19 Full Room Discussion 1 Risk? Risk Activity: Discuss your organization s approach to internal audits related to TPRM or third parties, including: A. Scope or focus of audits B. Frequency of these types of audits TPRM s? 20
20 Internal Audit Role of Internal Audit Risk? The role of internal audit is to perform two distinct services: (i) independently evaluate the effectiveness of the and (ii) ensure the is doing the right things Risk TPRM s? C Risk Group Risk Group Board Of Directors Risk Committee TPRM Steering Committee Risk Group Third Office (TPRMO) Risk Group Risk Group B Internal Audit IA must be independent and should examine whether the deployed TPRM Program controls are designed properly and are operating as designed, as related to occurring at the third party locations. IA should consider recent regulatory guidance and industry recommended practices when reviewing the TPRM Program to ensure the organization is focusing on the right things. IA s focus is typically on the more significant relationships from an inherent and residual risk perspective based on the second line of defense s risk assessments. Business Unit 1 Business Unit 2 Business Unit 3 A IA being the third line of defense, should not be influenced by what TPRM or Subject Matter Specialists may have completed. 21
21 Questions to Consider Risk? Risk TPRM s? Governance Who is accountable for oversight and the overall management of your Third (TPRM) Program? Are roles and responsibilities across the enterprise clearly delineated and adhered to? Planning Do you have an inventory of existing Third Parties? o Are they categorized by product / service? o Are each risk ranked? Do you have current contracts related to the product/service being provided? Do Third Parties go beyond traditional vendors and suppliers (e.g., joint ventures, affiliates)? Are there standardized risk profiling methodologies with defined assessment frequencies and types in place? Due Diligence and Third Party Selection Are due diligence assessments performed prior to contracting? o What risk areas are considered (e.g., information security, compliance, business continuity, reputation, etc.)? Do you know which of your third parties have access to data? Do you know which subcontractors are used by your third parties, and what work they are performing for you? Contract Negotiation Do contract clauses include the right to audit the Third Parties processes over the service provided? Are contracts for similar services consistent and contain Service Level Agreements? Ongoing Monitoring Do monitoring processes include both risk AND performance concerns? Termination Do you have exit strategies in place for significant/ high risk Third Party relationships? 22
22 Full Room Discussion 2 Risk? Risk Activity: Discuss TPRM audits, including: A. Challenges experienced in performing these types of audits B. Success stories TPRM s? 23
23 Common Challenges Risk? Risk TPRM s? Common challenges with TPRM Audits Example pitfalls when performing independent reviews include: Auditing perceived high risk vendors without auditing the or process Focusing on Third Party spend instead of risk Not applying same level of scrutiny as regulators (e.g. OCC TPRM Examination Procedures). For example: o o o o o Board approved policy Identification of process exceptions (e.g., Due diligence not completed prior to Contracting) Risks beyond Information Security and Business Continuity Ongoing monitoring above and beyond periodic re-assessments Trust but verify Not thinking broadly enough, (i.e., is the scope of the TPRM complete?) Focusing on completion of by the 1 st and 2 nd line instead of the quality of the and the skills and capabilities of the individuals managing the risk 24
24 Activities Risk? Risk TPRM s? Successful Internal Audit TPRM Internal Audits of TPRM s throughout the various stages of maturity and operation can drive significant value to the organization. Examples of successful, enterprise driven results include: Identification of breakdown in enterprise wide TPRM throughout the TPRM lifecycle. The audit drove an enterprise initiative to collaboratively develop an enterprise wide with formalized ownership and consistent processes. Uncovered inconsistent execution of requirements across business units. Resulted in enterprise procedures and templates being developed to enable consistency across a federated model. Raised gaps in regulatory compliance prior to formal examinations. Identified issues created urgency and drove management focus to enhance design and operationalization of TPRM within an accelerated timeframe. Identified areas of success in specific risk dimensions, but absence of oversight in other key areas. This resulted in a revision and expansion of TPRM focus to include other dimensions that were not initially addressed. Determined gaps in third party inventory as well as opportunities for enhancement in the payment control processes. The efforts resulted in refinement to onboarding and payment processes as well as better connection between risk, payment and contracting systems. 25
25 Questions?
26 Wrap Up and Closing Remarks
27 This content is for general information purposes only, and should not be used as a substitute for consultation with professional advisors PwC. All rights reserved. PwC refers to the US member firm or one of its subsidiaries or affiliates, and may sometimes refer to the PwC network. Each member firm is a separate legal entity. Please see for further details. 28
Lessons Learned in Streamlining the Third-party Risk Assessment Process
 Lessons Learned in Streamlining the Third-party Risk Assessment Process Agenda Welcome & Introductions Overview of the Third Party Risk Management Lifecycle Three Unique Perspectives on: Third Party Inventories
Lessons Learned in Streamlining the Third-party Risk Assessment Process Agenda Welcome & Introductions Overview of the Third Party Risk Management Lifecycle Three Unique Perspectives on: Third Party Inventories
Ensuring Organizational & Enterprise Resiliency with Third Parties
 Ensuring Organizational & Enterprise Resiliency with Third Parties Geno Pandolfi Tuesday, May 17, 2016 Room 7&8 (1:30-2:15 PM) Session Review Objectives Approaches to Third Party Risk Management Core Concepts
Ensuring Organizational & Enterprise Resiliency with Third Parties Geno Pandolfi Tuesday, May 17, 2016 Room 7&8 (1:30-2:15 PM) Session Review Objectives Approaches to Third Party Risk Management Core Concepts
Effective Vendor Risk Management. April 21, Mario A. Mosse. This Training is Brought to you by ComplianceOnline. Presenter:
 This Training is Brought to you by ComplianceOnline. Effective Vendor Risk Management Presenter: Mario A. Mosse April 21, 2017 This training session is sponsored by 2014 ComplianceOnline www.complianceonlie.com
This Training is Brought to you by ComplianceOnline. Effective Vendor Risk Management Presenter: Mario A. Mosse April 21, 2017 This training session is sponsored by 2014 ComplianceOnline www.complianceonlie.com
Vendor Management Challenges and Expectations An Open Discussion April 13, 2017
 1 Practical solutions driving tangible results Vendor Management Challenges and Expectations An Open Discussion April 13, 2017 Agenda Common Themes Discussion Expectations Overcoming Obstacles Common Comments
1 Practical solutions driving tangible results Vendor Management Challenges and Expectations An Open Discussion April 13, 2017 Agenda Common Themes Discussion Expectations Overcoming Obstacles Common Comments
VENDOR RISK MANAGEMENT FCC SERVICES
 VENDOR RISK MANAGEMENT FCC SERVICES Introductions Chris Tait, CISA, CFSA, CCSK, CCSFP Principal, Financial Services Baker Tilly Russ Sommers, CPA, CISA Senior Manager, Financial Services Baker Tilly Agenda
VENDOR RISK MANAGEMENT FCC SERVICES Introductions Chris Tait, CISA, CFSA, CCSK, CCSFP Principal, Financial Services Baker Tilly Russ Sommers, CPA, CISA Senior Manager, Financial Services Baker Tilly Agenda
SECURITY ACCENTURE GROW DEMYSTIFYING THIRD PARTY RISK MANAGEMENT (TPRM) Sheldon Nailer, CISSP, CISA Accenture Latvia, Security Team Lead
 GROW ACCENTURE SECURITY DEMYSTIFYING THIRD PARTY RISK MANAGEMENT (TPRM) October 09, 2018 Sheldon Nailer, CISSP, CISA Accenture Latvia, Security Team Lead AGENDA Background and Context Regulatory Landscape
GROW ACCENTURE SECURITY DEMYSTIFYING THIRD PARTY RISK MANAGEMENT (TPRM) October 09, 2018 Sheldon Nailer, CISSP, CISA Accenture Latvia, Security Team Lead AGENDA Background and Context Regulatory Landscape
Third Party Risk Management ( TPRM ) Transformation
 Third Party Risk Management ( TPRM ) Transformation September 20, 2017 Internal use only An introduction to TPRM What is a Third Party relationship? A Third Party relationship is any business arrangement
Third Party Risk Management ( TPRM ) Transformation September 20, 2017 Internal use only An introduction to TPRM What is a Third Party relationship? A Third Party relationship is any business arrangement
Outsourcing and the Need for Supplier Audits
 Outsourcing and the Need for Supplier Audits John A. Gatto Retired April 3, 2017 Agenda Why Audit Suppliers Outsourcing Supplier Risks Minimum Security Standards Audit Focus 2 1 Definitions Third Party
Outsourcing and the Need for Supplier Audits John A. Gatto Retired April 3, 2017 Agenda Why Audit Suppliers Outsourcing Supplier Risks Minimum Security Standards Audit Focus 2 1 Definitions Third Party
Managing the Business Associate Relationship: From Onboarding to Breaches. March 27, 2016
 Managing the Business Associate Relationship: From Onboarding to Breaches March 27, 2016 HCCA s 21 st Annual Compliance Institute National Harbor, MD Today s Agenda Onboarding: Health care providers and
Managing the Business Associate Relationship: From Onboarding to Breaches March 27, 2016 HCCA s 21 st Annual Compliance Institute National Harbor, MD Today s Agenda Onboarding: Health care providers and
STRATEGIES FOR EFFECTIVELY WORKING WITH THIRD-PARTIES. September 2017
 STRATEGIES FOR EFFECTIVELY WORKING WITH THIRD-PARTIES September 2017 Your presenters Nancy Aubrey Partner Boston, MA Nancy.aubrey@rsmus.com Rick Shriner Principal McLean, VA Rick.shriner@rsmus.com 2 Agenda
STRATEGIES FOR EFFECTIVELY WORKING WITH THIRD-PARTIES September 2017 Your presenters Nancy Aubrey Partner Boston, MA Nancy.aubrey@rsmus.com Rick Shriner Principal McLean, VA Rick.shriner@rsmus.com 2 Agenda
REGULATORY HOT TOPIC Third Party IT Vendor Management
 REGULATORY HOT TOPIC Third Party IT Vendor Management 1 Todays Outsourced Technology Services Core Processing Internet Banking Mobile Banking Managed Security Services Managed Data Center Services And
REGULATORY HOT TOPIC Third Party IT Vendor Management 1 Todays Outsourced Technology Services Core Processing Internet Banking Mobile Banking Managed Security Services Managed Data Center Services And
Navigating the New Health Economy
 Navigating the New Health Economy How non-traditional healthcare players are using the HITRUST CSF to drive their security programs forward Speakers Dennis Quandt Risk Assurance Director, PwC Boston, MA
Navigating the New Health Economy How non-traditional healthcare players are using the HITRUST CSF to drive their security programs forward Speakers Dennis Quandt Risk Assurance Director, PwC Boston, MA
How to Stand Up a Privacy Program: Privacy in a Box
 How to Stand Up a Privacy Program: Privacy in a Box Part III of III: Maturing a Privacy Program Presented by the IT, Privacy, & ecommerce global committee of ACC Thanks to: Nick Holland, Fieldfisher (ITPEC
How to Stand Up a Privacy Program: Privacy in a Box Part III of III: Maturing a Privacy Program Presented by the IT, Privacy, & ecommerce global committee of ACC Thanks to: Nick Holland, Fieldfisher (ITPEC
Third Party Vendor Management and FDR Compliance
 Smart decisions. Lasting value. Third Party Vendor Management and FDR Compliance Healthcare Summit 2018: Simplifying Healthcare September 18, 2018 Jason Lackey, Cigna-HealthSpring Scott Gerard, Crowe Matt
Smart decisions. Lasting value. Third Party Vendor Management and FDR Compliance Healthcare Summit 2018: Simplifying Healthcare September 18, 2018 Jason Lackey, Cigna-HealthSpring Scott Gerard, Crowe Matt
STEPS FOR EFFECTIVE MANAGEMENT OF VENDOR AND SUPPLIER CYBERSECURITY RISKS. April 25, 2018 In-House Counsel Conference
 STEPS FOR EFFECTIVE MANAGEMENT OF VENDOR AND SUPPLIER CYBERSECURITY RISKS April 25, 2018 In-House Counsel Conference Presenters: Daniela Ivancikova, Assistant General Counsel, University of Delaware Evan
STEPS FOR EFFECTIVE MANAGEMENT OF VENDOR AND SUPPLIER CYBERSECURITY RISKS April 25, 2018 In-House Counsel Conference Presenters: Daniela Ivancikova, Assistant General Counsel, University of Delaware Evan
THIRD-PARTY RISK MANAGEMENT
 THIRD-PARTY RISK MANAGEMENT Beyond a Regulatory Requirement April 28, 2017 Ken Glascock, CPA, CAMS, CIA, CFSA, CRCM Director kglascock@bkd.com AGENDA Let s Break It Down What Is Third-Party Risk Management?
THIRD-PARTY RISK MANAGEMENT Beyond a Regulatory Requirement April 28, 2017 Ken Glascock, CPA, CAMS, CIA, CFSA, CRCM Director kglascock@bkd.com AGENDA Let s Break It Down What Is Third-Party Risk Management?
Defining and promoting excellence in the provision of mobile money services
 SAFEGUARDING OF FUNDS DATA PRIVACY AML/CFT/FRAUD PREVENTION STAFF AND PARTNER MANAGEMENT CUSTOMER SERVICE TRANSPARENCY QUALITY OF OPERATIONS SECURITY OF SYSTEMS Defining and promoting excellence in the
SAFEGUARDING OF FUNDS DATA PRIVACY AML/CFT/FRAUD PREVENTION STAFF AND PARTNER MANAGEMENT CUSTOMER SERVICE TRANSPARENCY QUALITY OF OPERATIONS SECURITY OF SYSTEMS Defining and promoting excellence in the
Enterprise Availability Management
 Statement of Work Enterprise Availability Management This Statement of Work ( SOW ) is between the Customer (also called you and your ) and the IBM legal entity referenced below ( IBM ). This SOW is subject
Statement of Work Enterprise Availability Management This Statement of Work ( SOW ) is between the Customer (also called you and your ) and the IBM legal entity referenced below ( IBM ). This SOW is subject
VENDOR MANAGEMENT 101
 VENDOR MANAGEMENT 101 Enterprise Risk Management Vendor Management Business Continuity IT GRC Internal Audit Regulatory Compliance Manager Introduction to Vendor Management About Your Presenter Andrea
VENDOR MANAGEMENT 101 Enterprise Risk Management Vendor Management Business Continuity IT GRC Internal Audit Regulatory Compliance Manager Introduction to Vendor Management About Your Presenter Andrea
Optiv's Third- Party Risk Management Solution
 Optiv's Third- Party Management Solution Third-Party Relationships Pose Overwhelming To Your Organization. Data Processing 641 Accounting Education 601 Payroll Processing Call Center 452 400 901 Healthcare
Optiv's Third- Party Management Solution Third-Party Relationships Pose Overwhelming To Your Organization. Data Processing 641 Accounting Education 601 Payroll Processing Call Center 452 400 901 Healthcare
Optimizing an Enterprise Wide Effective Vendor Risk Management Program. Pam Schott Head and VP Enterprise Supplier Governance
 Optimizing an Enterprise Wide Effective Vendor Risk Program Pam Schott Head and VP Enterprise Supplier Governance June 1, 2015 Emerging Industry Trends As Procurement organizations mature; their focus
Optimizing an Enterprise Wide Effective Vendor Risk Program Pam Schott Head and VP Enterprise Supplier Governance June 1, 2015 Emerging Industry Trends As Procurement organizations mature; their focus
15,500+ 5, , ,000. Bloomberg Corporate Profile. Real-time financial information. employees. 192 locations around the world
 Bloomberg Corporate Profile Bloomberg, the global business and financial information and news leader, gives influential decision makers a critical edge by connecting them to a dynamic network of information,
Bloomberg Corporate Profile Bloomberg, the global business and financial information and news leader, gives influential decision makers a critical edge by connecting them to a dynamic network of information,
Extended Enterprise Risk Management
 Extended Enterprise Risk Management Driving performance through the extended enterprise October 2015 A network within a network The Extended Enterprise is the concept that an organization does not operate
Extended Enterprise Risk Management Driving performance through the extended enterprise October 2015 A network within a network The Extended Enterprise is the concept that an organization does not operate
PCI Data Breach Preparedness How To Prevent Your Organization From Becoming the Next Data Breach Headline
 PCI Data Breach Preparedness How To Prevent Your Organization From Becoming the Next Data Breach Headline Presented by the Bryan Cave Payments Team and Special Guest Speaker Andi Baritchi Agenda Introduction
PCI Data Breach Preparedness How To Prevent Your Organization From Becoming the Next Data Breach Headline Presented by the Bryan Cave Payments Team and Special Guest Speaker Andi Baritchi Agenda Introduction
Buying IoT Technology: How to Contract Securely. By Nicholas R. Merker, Partner, Ice Miller LLP
 Buying IoT Technology: How to Contract Securely By Nicholas R. Merker, Partner, Ice Miller LLP More and more products are shipping with sensors and network connectivity to capitalize on the currency of
Buying IoT Technology: How to Contract Securely By Nicholas R. Merker, Partner, Ice Miller LLP More and more products are shipping with sensors and network connectivity to capitalize on the currency of
Data rich and regulation wary
 Data rich and regulation wary Improving risk compliance in today s data rich environment kpmg.com Key highlights Expect regulatory and Increase data and security 1 policy focus 2 controls 3 Personal consumer
Data rich and regulation wary Improving risk compliance in today s data rich environment kpmg.com Key highlights Expect regulatory and Increase data and security 1 policy focus 2 controls 3 Personal consumer
Case Study Webinar: Vendor Risk Management at Global Lending Services
 Case Study Webinar: Vendor Risk Management at Global Lending Services Al Palmer, SVP Compliance, Global Lending Services LLC (GLS) Melissa Brown, Compliance Manager, Global Lending Services LLC (GLS) John
Case Study Webinar: Vendor Risk Management at Global Lending Services Al Palmer, SVP Compliance, Global Lending Services LLC (GLS) Melissa Brown, Compliance Manager, Global Lending Services LLC (GLS) John
VENDORINSIGHTU P D A T E
 VENDORINSIGHTU P D A T E November 12, 2013 COMPLIANCE VendorInsight is the industry-leading solution for financial institutions offering the most features and capabilities for vendor risk monitoring. Ask
VENDORINSIGHTU P D A T E November 12, 2013 COMPLIANCE VendorInsight is the industry-leading solution for financial institutions offering the most features and capabilities for vendor risk monitoring. Ask
Managing Third Party Risk
 Managing Third Party Risk Presenters: L o r i D a n i e l s E n g a g e m e n t M a n a g e r R i s k A d v i s o r y S e r v i c e s T i m L i e t z R e g i o n a l P r a c t i c e L e a d e r R i s k
Managing Third Party Risk Presenters: L o r i D a n i e l s E n g a g e m e n t M a n a g e r R i s k A d v i s o r y S e r v i c e s T i m L i e t z R e g i o n a l P r a c t i c e L e a d e r R i s k
Effects of GDPR and NY DFS on your Third Party Risk Management Program
 Effects of GDPR and NY DFS on your Third Party Risk Management Program Please disable popup blocking software before viewing this webcast June 27, 2017 Grant Thornton LLP. All rights reserved. 1 CPE Reminders
Effects of GDPR and NY DFS on your Third Party Risk Management Program Please disable popup blocking software before viewing this webcast June 27, 2017 Grant Thornton LLP. All rights reserved. 1 CPE Reminders
Rick Ensenbach, CISSP-ISSMP, CISA, CISM, CCSFP Senior Manager, Wipfli Risk Advisory Services OBJECTIVES
 Rick Ensenbach, CISSP-ISSMP, CISA, CISM, CCSFP Senior Manager, Wipfli Risk Advisory Services 1 OBJECTIVES What should be done before you sign a contract with a vendor Your responsibilities throughout the
Rick Ensenbach, CISSP-ISSMP, CISA, CISM, CCSFP Senior Manager, Wipfli Risk Advisory Services 1 OBJECTIVES What should be done before you sign a contract with a vendor Your responsibilities throughout the
HCCA Compliance Institute : Intersection of Internal Audit & Compliance. April 17, Agenda. Where are we today?
 HCCA Institute 2018 708: Intersection of & April 17, 2018 Agenda Objectives Where are we today? Corporate Integrity: The intersection of, and Privacy Questions 2 Where are we today? 3 1 Regulatory change
HCCA Institute 2018 708: Intersection of & April 17, 2018 Agenda Objectives Where are we today? Corporate Integrity: The intersection of, and Privacy Questions 2 Where are we today? 3 1 Regulatory change
Vendor Management Risk Mitigation:
 Vendor Management Risk Mitigation: The Importance of Having a Formalized Methodology Sun Life Financial Laura Williams AVP, Procurement Opus Sam Mele Vice President Sales sig.org/summit Case Study: Supplier
Vendor Management Risk Mitigation: The Importance of Having a Formalized Methodology Sun Life Financial Laura Williams AVP, Procurement Opus Sam Mele Vice President Sales sig.org/summit Case Study: Supplier
Do You Know What Your Business Associates Subcontractors & Vendors Are Doing With Your PHI & ephi?
 Do You Know What Your Business Associates Subcontractors & Vendors Are Doing With Your PHI & ephi? Web Hull Privacy, Data Protection, & Compliance Advisor Web.Hull@icloud.com HCCA 2017 Compliance Institute
Do You Know What Your Business Associates Subcontractors & Vendors Are Doing With Your PHI & ephi? Web Hull Privacy, Data Protection, & Compliance Advisor Web.Hull@icloud.com HCCA 2017 Compliance Institute
Do You Know What Your Business Associates Subcontractors & Vendors Are Doing With Your PHI & ephi?
 Do You Know What Your Business Associates Subcontractors & Vendors Are Doing With Your PHI & ephi? Web Hull Privacy, Data Protection, & Compliance Advisor Web.Hull@icloud.com HCCA 2017 Compliance Institute
Do You Know What Your Business Associates Subcontractors & Vendors Are Doing With Your PHI & ephi? Web Hull Privacy, Data Protection, & Compliance Advisor Web.Hull@icloud.com HCCA 2017 Compliance Institute
Trusted KYC Data Sharing Framework Implementation
 July 2017 Trusted KYC Data Sharing Framework Implementation Supporting Document Contents Preface... 3 1 Objective of this Document... 4 2 Evolving Benefits Provided by the Data Sharing Environment... 5
July 2017 Trusted KYC Data Sharing Framework Implementation Supporting Document Contents Preface... 3 1 Objective of this Document... 4 2 Evolving Benefits Provided by the Data Sharing Environment... 5
Assessments for Certified and Non-Certified Vendors
 Assessments for Certified and Non-Certified Vendors 3rd party Vendors Security Risk Profile 63% of all 2016 data breaches resulted from third party vendor s risk Small companies are high risk - security
Assessments for Certified and Non-Certified Vendors 3rd party Vendors Security Risk Profile 63% of all 2016 data breaches resulted from third party vendor s risk Small companies are high risk - security
Third-Party Risk: The Examiners are Coming!
 Third-Party Risk: The Examiners are Coming! Brad Keller, Sr. Director, 3rd Party Strategy Prevalent Inc. Hosted by Compliance Week s assistant director of events & programs, Tsvetelina Gabin. 1 Agenda
Third-Party Risk: The Examiners are Coming! Brad Keller, Sr. Director, 3rd Party Strategy Prevalent Inc. Hosted by Compliance Week s assistant director of events & programs, Tsvetelina Gabin. 1 Agenda
Strengthening Vendor Risk Management Program
 Strengthening Vendor Risk Management Program ACUIA Region 5 Fall Meeting Portsmouth, N.H. October 2017 PKF O Connor Davies Risk Advisory Services Governance & Regulations Cyber-Security Risk Management
Strengthening Vendor Risk Management Program ACUIA Region 5 Fall Meeting Portsmouth, N.H. October 2017 PKF O Connor Davies Risk Advisory Services Governance & Regulations Cyber-Security Risk Management
Call-Off Contract. Legal Consultancy Services Framework Call-Off Number DCCT0012 Legal consultancy on GDPR. Version: V1.0
 Call-Off Contract Legal Consultancy Services Framework Call-Off Number DCCT0012 Legal consultancy on GDPR Version: V1.0 Date: 16 August 2017 Author: Classification: Redacted DCC Public CONSULTANCY LEGAL
Call-Off Contract Legal Consultancy Services Framework Call-Off Number DCCT0012 Legal consultancy on GDPR Version: V1.0 Date: 16 August 2017 Author: Classification: Redacted DCC Public CONSULTANCY LEGAL
IBM Emptoris Strategic Supply Management on Cloud
 Service Description IBM Emptoris Strategic Supply Management on Cloud This Service Description describes the Cloud Service IBM provides to Client. Client means the company and its authorized users and
Service Description IBM Emptoris Strategic Supply Management on Cloud This Service Description describes the Cloud Service IBM provides to Client. Client means the company and its authorized users and
Business Partners: Pragmatic Steps to Managing Your Clients Compliance and Litigation Risk
 Business Partners: Pragmatic Steps to Managing Your Clients Compliance and Litigation Risk By: Ryan Murphy and Sara Putnam 1 A global company, facing a joint DOJ/SEC probe involving strategies and business
Business Partners: Pragmatic Steps to Managing Your Clients Compliance and Litigation Risk By: Ryan Murphy and Sara Putnam 1 A global company, facing a joint DOJ/SEC probe involving strategies and business
Supplier risk compliance obligation or source of competitive advantage? Improve supplier reliability to lift business performance
 Supplier risk compliance obligation or source of competitive advantage? Improve supplier reliability to lift business performance Steps to reduce supplier uncertainty and uncover cost savings An unreliable
Supplier risk compliance obligation or source of competitive advantage? Improve supplier reliability to lift business performance Steps to reduce supplier uncertainty and uncover cost savings An unreliable
IT Strategic Plan Portland Community College 2017 Office of the CIO
 IT Strategic Plan Portland Community College 2017 Office of the CIO 1 Our Vision Information Technology To be a nationally recognized standard for Higher Education Information Technology organizations
IT Strategic Plan Portland Community College 2017 Office of the CIO 1 Our Vision Information Technology To be a nationally recognized standard for Higher Education Information Technology organizations
IT Strategic Plan Portland Community College 2017 Office of the CIO
 IT Strategic Plan Portland Community College 2017 Office of the CIO 1 Our Vision Information Technology To be a nationally recognized standard for Higher Education Information Technology organizations
IT Strategic Plan Portland Community College 2017 Office of the CIO 1 Our Vision Information Technology To be a nationally recognized standard for Higher Education Information Technology organizations
SOLUTION BRIEF EU GENERAL DATA PROTECTION REGULATION COMPLIANCE WITH RSA ARCHER
 EU GENERAL DATA PROTECTION REGULATION COMPLIANCE WITH RSA ARCHER ARRIVAL OF GDPR IN 2018 The European Union (EU) General Data Protection Regulation (GDPR), which takes effect in 2018, will bring changes
EU GENERAL DATA PROTECTION REGULATION COMPLIANCE WITH RSA ARCHER ARRIVAL OF GDPR IN 2018 The European Union (EU) General Data Protection Regulation (GDPR), which takes effect in 2018, will bring changes
Topics for Discussion
 Reviewing & Managing Third Party Compliance Marjorie W. Doyle, JD, CCEP-F, Managing Director, Aegis Compliance & Ethics Center, LLP with input from Diana Lutz SCCE Midwest Regional Conference, April 27,
Reviewing & Managing Third Party Compliance Marjorie W. Doyle, JD, CCEP-F, Managing Director, Aegis Compliance & Ethics Center, LLP with input from Diana Lutz SCCE Midwest Regional Conference, April 27,
Policy Outsourcing and Cloud-Based File Sharing
 Policy Outsourcing and Cloud-Based File Sharing Version 3.3 Table of Contents Outsourcing and Cloud-Based File Sharing Policy... 2 Outsourcing Cloud-Based File Sharing Management Standard... 2 Overview...
Policy Outsourcing and Cloud-Based File Sharing Version 3.3 Table of Contents Outsourcing and Cloud-Based File Sharing Policy... 2 Outsourcing Cloud-Based File Sharing Management Standard... 2 Overview...
IT Service Delivery And Support Week Seven: SLA. IT Auditing and Cyber Security Fall 2016 Instructor: Liang Yao
 IT Service Delivery And Support Week Seven: SLA IT Auditing and Cyber Security Fall 2016 Instructor: Liang Yao 1 Outsourcing Drivers Outsourced IT Works Outsourced IT Activity Samples Top Three Outsourcing
IT Service Delivery And Support Week Seven: SLA IT Auditing and Cyber Security Fall 2016 Instructor: Liang Yao 1 Outsourcing Drivers Outsourced IT Works Outsourced IT Activity Samples Top Three Outsourcing
Proactively Managing ERP Risks. January 7, 2010
 Proactively Managing ERP Risks January 7, 2010 0 Introductions and Objectives Establish a structured model to demonstrate the variety of risks associated with an ERP environment Discuss control areas that
Proactively Managing ERP Risks January 7, 2010 0 Introductions and Objectives Establish a structured model to demonstrate the variety of risks associated with an ERP environment Discuss control areas that
Contents. Primer Series: HIPAA Privacy, Security, and the Omnibus Final Rule
 BEST PRACTICES Iron Mountain Document Conversion Services HEALTHCARE HIPAA Omnibus and the Implications for Document Conversion Primer Series: HIPAA Privacy, Security, and the Omnibus Final Rule Contents
BEST PRACTICES Iron Mountain Document Conversion Services HEALTHCARE HIPAA Omnibus and the Implications for Document Conversion Primer Series: HIPAA Privacy, Security, and the Omnibus Final Rule Contents
Hot Topics in the Board Room
 www.pwc.com Hot Topics in the Board Room Agenda State of the Internal Audit Profession Vendor Risk Management Privacy & Security April 2014 2 At a glance s 10 th Annual State of the Internal Audit Profession
www.pwc.com Hot Topics in the Board Room Agenda State of the Internal Audit Profession Vendor Risk Management Privacy & Security April 2014 2 At a glance s 10 th Annual State of the Internal Audit Profession
Emerging & disruptive technology risks
 Emerging & disruptive technology risks Shawn W. Lafferty, KPMG Partner IT Internal Audit/Risk Assurance April 2018 Why IT internal audit? find ways to overcome resource and budgetary constraints. This
Emerging & disruptive technology risks Shawn W. Lafferty, KPMG Partner IT Internal Audit/Risk Assurance April 2018 Why IT internal audit? find ways to overcome resource and budgetary constraints. This
Unified SaaS Solution for Cybersecurity and Risk. Curran Data Technologies
 Unified SaaS Solution for Cybersecurity and Risk Curran Data Technologies 317-974-1009 www.currandata.com Solution Discover the effective simplicity of a unified RSC solution Discover Solution Diagnose
Unified SaaS Solution for Cybersecurity and Risk Curran Data Technologies 317-974-1009 www.currandata.com Solution Discover the effective simplicity of a unified RSC solution Discover Solution Diagnose
Management Excluded Job Description
 Management Excluded Job Description 1. Position Identification Position Number 993234 Position Title Department Reports to (title) Associate Director, Supply Management Purchasing Services Director, Purchasing
Management Excluded Job Description 1. Position Identification Position Number 993234 Position Title Department Reports to (title) Associate Director, Supply Management Purchasing Services Director, Purchasing
Agenda. Agenda. Why Audit Suppliers. Outsourcing / Offshoring. Supplier Risks. Minimum Security Standards. Audit Focus
 Agenda Outsourcing and the Need for Supplier Audits 1 Agenda Why Audit Suppliers Outsourcing / Offshoring Supplier Risks Minimum Security Standards Audit Focus 2 Outsourcing and the Need for Supplier Audits
Agenda Outsourcing and the Need for Supplier Audits 1 Agenda Why Audit Suppliers Outsourcing / Offshoring Supplier Risks Minimum Security Standards Audit Focus 2 Outsourcing and the Need for Supplier Audits
The Role of the VMO in Regulatory Compliance Planning, Due Diligence and Contract Negotiation
 : The Role of the VMO in Regulatory Compliance Planning, Due Diligence and Contract Negotiation David England, Director, ISG ISG WHITE PAPER 2017 Information Services Group, Inc. All Rights Reserved EXECUTIVE
: The Role of the VMO in Regulatory Compliance Planning, Due Diligence and Contract Negotiation David England, Director, ISG ISG WHITE PAPER 2017 Information Services Group, Inc. All Rights Reserved EXECUTIVE
CONSULTING & CYBERSECURITY SOLUTIONS
 CONSULTING & CYBERSECURITY SOLUTIONS Who We Are Since 1996, Crossroads has been established as a respected Technology and Business Availability Enterprise with strategic competencies in Consulting, Compliance,
CONSULTING & CYBERSECURITY SOLUTIONS Who We Are Since 1996, Crossroads has been established as a respected Technology and Business Availability Enterprise with strategic competencies in Consulting, Compliance,
Firm Profile TURNING RISKS INTO OPPORTUNITIES
 Firm Profile TURNING RISKS INTO OPPORTUNITIES You can measure opportunity with the same yardstick that measures the risk involved. They go together. Earl Nightingale TRUSTED ADVISORS RiSK Opportunities
Firm Profile TURNING RISKS INTO OPPORTUNITIES You can measure opportunity with the same yardstick that measures the risk involved. They go together. Earl Nightingale TRUSTED ADVISORS RiSK Opportunities
15. Driving Organizational Value through Procurement Transformation
 15. Driving Organizational Value through Procurement Transformation 13 Global Procurement The Transformational Journey Chris Misiorski Nagendra Bhanu Version: February 27, 2014 Iron Mountain at a Glance
15. Driving Organizational Value through Procurement Transformation 13 Global Procurement The Transformational Journey Chris Misiorski Nagendra Bhanu Version: February 27, 2014 Iron Mountain at a Glance
The past, present and future of service organization control reporting
 The past, present and future of service organization control reporting Key takeaways from EY s Annual SOCR Client Conference March 2016 Study the past if you would define the future. Confucius b 1 Conference
The past, present and future of service organization control reporting Key takeaways from EY s Annual SOCR Client Conference March 2016 Study the past if you would define the future. Confucius b 1 Conference
WELCOME. 1
 WELCOME 1 The AML Risk Conundrum What Does AML Risk Really Mean? BSA Coalition Training Event November 17, 2016 2 Opening Remarks: Amanda Tucker, BSA Coalition Board Member Executive Vice President I Chief
WELCOME 1 The AML Risk Conundrum What Does AML Risk Really Mean? BSA Coalition Training Event November 17, 2016 2 Opening Remarks: Amanda Tucker, BSA Coalition Board Member Executive Vice President I Chief
IBM Emptoris Services Procurement on Cloud
 Service Description IBM Emptoris Services Procurement on Cloud This Service Description describes the Cloud Service IBM provides to Client. Client means the company and its authorized users and recipients
Service Description IBM Emptoris Services Procurement on Cloud This Service Description describes the Cloud Service IBM provides to Client. Client means the company and its authorized users and recipients
Why Is Third Party Risk Management Important?
 Third Party Risk Management Managing Risks in Your Extended Enterprise Why Is Third Party Risk Management Important? It is not a new concept for organisations to engage with third parties for the provision
Third Party Risk Management Managing Risks in Your Extended Enterprise Why Is Third Party Risk Management Important? It is not a new concept for organisations to engage with third parties for the provision
Risk Assessment. Consumer Risk Assessment. Using the Risk Assessment Template
 Consumer CFPB s process is designed to evaluate on a consistent basis the extent of risk to consumers arising from the activities of a particular supervised entity and to identify the sources of that risk.
Consumer CFPB s process is designed to evaluate on a consistent basis the extent of risk to consumers arising from the activities of a particular supervised entity and to identify the sources of that risk.
W207: How should you leverage internal audit? October 26, 2016
 W207: How should you leverage internal audit? October 26, 2016 Agenda Internal Audit Framework 3 Lines of Defense Value Enhancement Work Internal Audit vs. Compliance Areas of Focus Key takeaways 2 What
W207: How should you leverage internal audit? October 26, 2016 Agenda Internal Audit Framework 3 Lines of Defense Value Enhancement Work Internal Audit vs. Compliance Areas of Focus Key takeaways 2 What
SCCE Compliance & Ethics Institute. Agenda. Trust & Verify: Investigation and Compliance Forensic Tools. September 16, 2014
 SCCE & Ethics Institute Trust & Verify: Investigation and Forensic Tools September 16, 2014 Martin Wolin Chief Risk & Officer Mercer North & Latin America Boston, MA Alan K. Halfenger Chief Officer Bain
SCCE & Ethics Institute Trust & Verify: Investigation and Forensic Tools September 16, 2014 Martin Wolin Chief Risk & Officer Mercer North & Latin America Boston, MA Alan K. Halfenger Chief Officer Bain
Effective implementation of COSO s new anti-fraud guidance
 Effective implementation of COSO s new anti-fraud guidance In September 2016, the Committee of Sponsoring Organizations of the Treadway Commission (COSO) published a new Fraud Risk Management Guide (Anti-fraud
Effective implementation of COSO s new anti-fraud guidance In September 2016, the Committee of Sponsoring Organizations of the Treadway Commission (COSO) published a new Fraud Risk Management Guide (Anti-fraud
THOMSON REUTERS CLIENT ON-BOARDING
 THOMSON REUTERS CLIENT ON-BOARDING THOMSON REUTERS CLIENT ON-BOARDING Thomson Reuters Client On-Boarding automates the on-boarding of new clients and ongoing refresh cycles. Integrating a purpose built
THOMSON REUTERS CLIENT ON-BOARDING THOMSON REUTERS CLIENT ON-BOARDING Thomson Reuters Client On-Boarding automates the on-boarding of new clients and ongoing refresh cycles. Integrating a purpose built
Q1 Please select the primary industry in which your company operates.
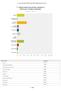 Q Please select the primary industry in which your company operates. Answered: 9 Skipped: Banking Construction & Real Estate Financial Services &... Food & Commodities Government Healthcare Higher Education
Q Please select the primary industry in which your company operates. Answered: 9 Skipped: Banking Construction & Real Estate Financial Services &... Food & Commodities Government Healthcare Higher Education
Drive Your Business. Four Ways to Improve Your Vendor Risk Program
 Drive Your Business Four Ways to Improve Your Vendor Risk Program Introduction Risk-management professionals often find the creation of a vendor risk management (VRM) program to be a challenging task,
Drive Your Business Four Ways to Improve Your Vendor Risk Program Introduction Risk-management professionals often find the creation of a vendor risk management (VRM) program to be a challenging task,
Collaboration with Business Associates on Compliance
 Collaboration with Business Associates on Compliance HCCA Compliance Institute April 19, 2016 Balancing risk management, compliance responsibility and business growth Responsibility of entities as they
Collaboration with Business Associates on Compliance HCCA Compliance Institute April 19, 2016 Balancing risk management, compliance responsibility and business growth Responsibility of entities as they
Intelligent automation and internal audit
 Intelligent automation and internal audit Adding value through governance, risk management, and controls Second article in the series kpmg.ch Contents Governing intelligent automation across the enterprise
Intelligent automation and internal audit Adding value through governance, risk management, and controls Second article in the series kpmg.ch Contents Governing intelligent automation across the enterprise
Outsourcing banking processes: The question is no longer if, but how to effectively manage extended enterprises
 Outsourcing banking processes: The question is no longer if, but how to effectively manage extended enterprises In today s business environment, banks are continuously facing challenges to reduce their
Outsourcing banking processes: The question is no longer if, but how to effectively manage extended enterprises In today s business environment, banks are continuously facing challenges to reduce their
Certified Outsourcing Professional (COP) Exam Study Guide
 Certified Outsourcing Professional (COP) Exam Study Guide DEVELOPED BY THE INTERNATIONAL ASSOCIATION OF OUTSOURCING PROFESSIONALS (IAOP) PART OF THE COP PROGRAM 2011 The Certified Outsourcing Professional
Certified Outsourcing Professional (COP) Exam Study Guide DEVELOPED BY THE INTERNATIONAL ASSOCIATION OF OUTSOURCING PROFESSIONALS (IAOP) PART OF THE COP PROGRAM 2011 The Certified Outsourcing Professional
IBM Emptoris Contract Management on Cloud
 Service Description IBM Emptoris Contract Management on Cloud This Service Description describes the Cloud Service IBM provides to Client. Client means the company and its authorized users and recipients
Service Description IBM Emptoris Contract Management on Cloud This Service Description describes the Cloud Service IBM provides to Client. Client means the company and its authorized users and recipients
PROTECTING YOUR BUSINESS AND CLIENTS FROM HIGH RISK BROKERS
 PROTECTING YOUR BUSINESS AND CLIENTS FROM HIGH RISK BROKERS Webinar 28 March 2018 Today s speakers Paul DiBlasi Director of Product Marketing, Financial Markets Compliance Paul.DiBlasi@actimize.com Brian
PROTECTING YOUR BUSINESS AND CLIENTS FROM HIGH RISK BROKERS Webinar 28 March 2018 Today s speakers Paul DiBlasi Director of Product Marketing, Financial Markets Compliance Paul.DiBlasi@actimize.com Brian
Business Resilience: Proactive measures for forward-looking enterprises
 IBM Global Services Business Resilience: Proactive measures for forward-looking enterprises protect deflect predict adapt Working with IBM, you can develop and implement a flexible business resilience
IBM Global Services Business Resilience: Proactive measures for forward-looking enterprises protect deflect predict adapt Working with IBM, you can develop and implement a flexible business resilience
INTEGRITY COMPLIANCE GUIDELINES
 AFRICAN DEVELOPMENT BANK GROUP African Development Bank Group Integrity and Anti-Corruption Department INTEGRITY COMPLIANCE GUIDELINES 1 1. Prohibition of Misconduct A clearly articulated and visible prohibition
AFRICAN DEVELOPMENT BANK GROUP African Development Bank Group Integrity and Anti-Corruption Department INTEGRITY COMPLIANCE GUIDELINES 1 1. Prohibition of Misconduct A clearly articulated and visible prohibition
CORE. Integration. EXAM SPECIFICATIONS Certified Professional in Supply Management (CPSM ) Supply Management. Supply Management. CPSM Learning System
 CPSM EXAMS SPECIFICATIONS Leadership and Transformation in Supply Supply Integration EXAM SPECIFICATIONS Certified Professional in Supply (CPSM ) Supply CORE CPSM Learning System Institute for Supply 2018,
CPSM EXAMS SPECIFICATIONS Leadership and Transformation in Supply Supply Integration EXAM SPECIFICATIONS Certified Professional in Supply (CPSM ) Supply CORE CPSM Learning System Institute for Supply 2018,
CERT Resilience Management Model, Version 1.2
 CERT Resilience Management Model, Organizational Process Focus (OPF) Richard A. Caralli Julia H. Allen David W. White Lisa R. Young Nader Mehravari Pamela D. Curtis February 2016 CERT Program Unlimited
CERT Resilience Management Model, Organizational Process Focus (OPF) Richard A. Caralli Julia H. Allen David W. White Lisa R. Young Nader Mehravari Pamela D. Curtis February 2016 CERT Program Unlimited
Integrating COSO s Fraud Risk Management Guide on an Enterprise Scale
 Integrating COSO s Fraud Risk Management Guide on an Enterprise Scale September 15, 2017 Vincent Walden Partner EY Atlanta Delores White Director, Internal Audit Southern Company Scott Hulsey Chief Compliance
Integrating COSO s Fraud Risk Management Guide on an Enterprise Scale September 15, 2017 Vincent Walden Partner EY Atlanta Delores White Director, Internal Audit Southern Company Scott Hulsey Chief Compliance
SOLUTION BRIEF EU GENERAL DATA PROTECTION REGULATION COMPLIANCE WITH RSA ARCHER
 EU GENERAL DATA PROTECTION REGULATION COMPLIANCE WITH RSA ARCHER ARRIVAL OF GDPR IN 2018 The European Union (EU) General Data Protection Regulation (GDPR) that takes effect in 2018 will bring changes for
EU GENERAL DATA PROTECTION REGULATION COMPLIANCE WITH RSA ARCHER ARRIVAL OF GDPR IN 2018 The European Union (EU) General Data Protection Regulation (GDPR) that takes effect in 2018 will bring changes for
ISACA San Francisco Chapter
 ISACA San Francisco Chapter The 2007 Privacy Panel Rena Mears, CISSP, CIPP, CPA, CISA Partner, Deloitte & Touche LLP March 23, 2007 San Francisco 0 What is Privacy and Why Now? Definition of PII The definition
ISACA San Francisco Chapter The 2007 Privacy Panel Rena Mears, CISSP, CIPP, CPA, CISA Partner, Deloitte & Touche LLP March 23, 2007 San Francisco 0 What is Privacy and Why Now? Definition of PII The definition
RFQ ATTACHMENT V: RESPONSE TEMPLATE
 Instructions are provided in blue and may be deleted. Please complete your response in the template provided, and indicate clearly where separate documents are provided. Executive Summary 1. Applicant
Instructions are provided in blue and may be deleted. Please complete your response in the template provided, and indicate clearly where separate documents are provided. Executive Summary 1. Applicant
IBM Emptoris Managed Cloud Delivery
 IBM Terms of Use SaaS Specific Offering Terms IBM Emptoris Managed Cloud Delivery The Terms of Use ( ToU ) is composed of this IBM Terms of Use - SaaS Specific Offering Terms ( SaaS Specific Offering Terms
IBM Terms of Use SaaS Specific Offering Terms IBM Emptoris Managed Cloud Delivery The Terms of Use ( ToU ) is composed of this IBM Terms of Use - SaaS Specific Offering Terms ( SaaS Specific Offering Terms
Outsourcing Transparency Evolution: Creating Value Across the Third-Party Extended Enterprise
 Outsourcing Transparency Evolution: Creating Value Across the Third-Party Extended Enterprise @ComplianceWeek #CW2017 Release for answers to polling questions I understand that any data or information
Outsourcing Transparency Evolution: Creating Value Across the Third-Party Extended Enterprise @ComplianceWeek #CW2017 Release for answers to polling questions I understand that any data or information
3/21/2017. How and when should you leverage internal audit? March 28, Agenda. What are your initial thoughts on internal audit?
 How and when should you leverage internal audit? March 28, 2017 Agenda Internal Audit foundation 3 lines of defense Trends in consultative & value enhancement work Why you should care Key takeaways 2 What
How and when should you leverage internal audit? March 28, 2017 Agenda Internal Audit foundation 3 lines of defense Trends in consultative & value enhancement work Why you should care Key takeaways 2 What
CEI Vendor Exit Strategy
 CEI Vendor Exit Strategy I. Reasons for Change II. Risk Management III. Criticality/Ease of Replacement IV. Contract Issues V. Knowledge Base VI. Total Cost of Ownership VII. Project Planning & Management
CEI Vendor Exit Strategy I. Reasons for Change II. Risk Management III. Criticality/Ease of Replacement IV. Contract Issues V. Knowledge Base VI. Total Cost of Ownership VII. Project Planning & Management
Blue Telecom is compliant with the Telecommunications Consumer Protection Code (C628:2012), which applies if you meet one of the criteria below.
 Blue Telecom Regulatory Compliance Statement Blue Telecom is compliant with the Telecommunications Consumer Protection Code (C628:2012), which applies if you meet one of the criteria below. You are an
Blue Telecom Regulatory Compliance Statement Blue Telecom is compliant with the Telecommunications Consumer Protection Code (C628:2012), which applies if you meet one of the criteria below. You are an
CPSM. Exam Specifications. Building a Global Network of Supply Management Experts. Certified Professional in Supply Management (CPSM )
 Building a Global Network of Supply Management Experts CPSM Certified Professional in Supply Management (CPSM ) Exam Specifications InstituteforSupplyManagement.org 2018, Institute for Supply Management.
Building a Global Network of Supply Management Experts CPSM Certified Professional in Supply Management (CPSM ) Exam Specifications InstituteforSupplyManagement.org 2018, Institute for Supply Management.
Human Resources Security Management towards ISO/IEC 27001:2005 accreditation of an Information Security Management System
 Human Resources Security Management towards ISO/IEC 27001:2005 accreditation of an Information Security Management System Professor PhD. Constantin MILITARU Polytechnic University of Bucharest, Romania
Human Resources Security Management towards ISO/IEC 27001:2005 accreditation of an Information Security Management System Professor PhD. Constantin MILITARU Polytechnic University of Bucharest, Romania
APPENDIX O CONTRACTOR ROLES, RESPONSIBILITIES AND MINIMUM QUALIFICATIONS
 APPENDIX O CONTRACTOR ROLES, RESPONSIBILITIES AND MINIMUM QUALIFICATIONS Shared denotes whether a Contractor Resource may be responsible for that in addition to another identified. Contractor Required
APPENDIX O CONTRACTOR ROLES, RESPONSIBILITIES AND MINIMUM QUALIFICATIONS Shared denotes whether a Contractor Resource may be responsible for that in addition to another identified. Contractor Required
CERT Resilience Management Model, Version 1.2
 CERT Resilience Management Model, Asset Definition and Management (ADM) Richard A. Caralli Julia H. Allen David W. White Lisa R. Young Nader Mehravari Pamela D. Curtis February 2016 CERT Program Unlimited
CERT Resilience Management Model, Asset Definition and Management (ADM) Richard A. Caralli Julia H. Allen David W. White Lisa R. Young Nader Mehravari Pamela D. Curtis February 2016 CERT Program Unlimited
Sarbanes-Oxley Compliance Kit
 Kit February 2018 This product is NOT FOR RESALE or REDISTRIBUTION in any physical or electronic format. The purchaser of this template has acquired the rights to use it for a SINGLE Disaster Recovery
Kit February 2018 This product is NOT FOR RESALE or REDISTRIBUTION in any physical or electronic format. The purchaser of this template has acquired the rights to use it for a SINGLE Disaster Recovery
Navigating the Intersection of Vendor Management and Business Continuity
 Navigating the Intersection of Vendor Management and Business Continuity MICHAEL BERMAN, J.D. Table of Contents Why are we here? Business Continuity and Vendor Management Primary Intersection BCP Each
Navigating the Intersection of Vendor Management and Business Continuity MICHAEL BERMAN, J.D. Table of Contents Why are we here? Business Continuity and Vendor Management Primary Intersection BCP Each
Advanced Audit Techniques
 Certificate in Internal Audit 4 Advanced Audit Techniques Who should attend? Senior Auditors Audit Managers and those about to be appointed to that role Auditors that need to audit projects, contracts
Certificate in Internal Audit 4 Advanced Audit Techniques Who should attend? Senior Auditors Audit Managers and those about to be appointed to that role Auditors that need to audit projects, contracts
USAA's Supplier Governance Transformation that Optimizes Value and Addresses Risk
 USAA's Supplier Governance Transformation that Optimizes Value and Addresses Risk USAA Glenn Ellis Director, USAA Supplier Management Enlighta Nipun Sehgal CEO www.sig.org/eval USAA s Supplier Governance
USAA's Supplier Governance Transformation that Optimizes Value and Addresses Risk USAA Glenn Ellis Director, USAA Supplier Management Enlighta Nipun Sehgal CEO www.sig.org/eval USAA s Supplier Governance
Streamline your business processes for far-reaching results. EY s Business Process Management Services practice
 Streamline your business processes for far-reaching results EY s Business Process Management Services practice Introduction Today s financial services organizations are facing a number of pressures: Stressed
Streamline your business processes for far-reaching results EY s Business Process Management Services practice Introduction Today s financial services organizations are facing a number of pressures: Stressed
Security Monitoring Service Description
 Security Monitoring Service Description Contents Section 1: UnderdefenseSOC Security Monitoring Service Overview 3 Section 2: Key Components of the Service 4 Section 3: Onboarding Process 5 Section 4:
Security Monitoring Service Description Contents Section 1: UnderdefenseSOC Security Monitoring Service Overview 3 Section 2: Key Components of the Service 4 Section 3: Onboarding Process 5 Section 4:
