A SURVEY ON AVAILABILITY CALCULATION AND DEFINITION FOR INFORMATION TECHNOLOGY SERVICES
|
|
|
- Mariah Jackson
- 6 years ago
- Views:
Transcription
1 Association for Information Systems AIS Electronic Library (AISeL) PACIS 2016 Proceedings Pacific Asia Conference on Information Systems (PACIS) Summer A SURVEY ON AVAILABILITY CALCULATION AND DEFINITION FOR INFORMATION TECHNOLOGY SERVICES Oscar Avila University of Los Ande, oj.avila@uniandes.edu.co Sebastian Sastoque H. University of Los Ande, s.sastoque10@uniandes.edu.co Follow this and additional works at: Recommended Citation Avila, Oscar and Sastoque H., Sebastian, "A SURVEY ON AVAILABILITY CALCULATION AND DEFINITION FOR INFORMATION TECHNOLOGY SERVICES" (2016). PACIS 2016 Proceedings This material is brought to you by the Pacific Asia Conference on Information Systems (PACIS) at AIS Electronic Library (AISeL). It has been accepted for inclusion in PACIS 2016 Proceedings by an authorized administrator of AIS Electronic Library (AISeL). For more information, please contact elibrary@aisnet.org.
2 A SURVEY ON AVAILABILITY CALCULATION AND DEFINITION FOR INFORMATION TECHNOLOGY SERVICES Oscar Avila, Department of System and Computing Engineering, School of Engineering, University of Los Andes, Bogotá, Colombia, Sebastian Sastoque H., Department of System and Computing Engineering, School of Engineering, University of Los Andes, Bogotá, Colombia, Abstract Nowadays companies outsource a lot of their IT resources and capabilities by contracting them with external IT providers. The agreements between providers and customers concerning different quality aspects of the contracted services such as availability, maintainability, security and continuity are formalized through Server Level Agreements (SLAs). One of the most important quality aspects and, at the same time, most difficult to agree is the availability level to be reached. Indeed, the process, methods and types of inputs used by providers and customers to calculate this level are still very informal and in many cases the resulting availability target is not suited to the customer requirements and the provider capabilities. In this boarder, this work presents a survey aimed at identifying and analysing the research literature to analyse what are the most used inputs and methods for availability calculation and prediction as wells as to analyse their applicability in the industry. Keywords: Service Level Agreement, SLA, Availability, Definition, Literature Review.
3 1 INTRODUCTION Over the past decade there has been an increasing tendency for outsourcing of IT services. Thus companies IT resources and capabilities are being contracted to external IT providers following a service orientation. By using this approach, Service Level Agreements (SLAs) are very important tools for defining responsibilities of providers and consumers. The Service Level Targets (SLTs), documented into the SLAs, constitute an agreement between providers and consumers in reference to different quality aspects of the service such as availability, maintainability, security and continuity. SLTs are defined through negotiation on Service Level Requirements (SLRs) between the two parts. Even though the availability is the most crucial quality aspect to IT service customers (Franke et al., 2014), it is at the same time one of the most difficult to be defined. Indeed, the measurement used to agree the SLT related to availability is commonly defined in terms of a percentage to be reached by the provider. One important characteristic of IT service availability is that it does not only depend on the service infrastructure (software, hardware, network, etc). Indeed, an IT service is a complex and abstract concept that involves IT, processes and people. In this way there are important organizational elements apart from infrastructure that providers and customer need to consider when defining availability SLTs. For instance, the availability of an IT service in case of fail depends on the reactivity mechanisms of the IT organization to resolve incidents. These mechanisms may include processes such as incident management and resources such as management tools and people. Despite the importance of availability and the complexity of its definition, process, methods and types of inputs used by providers and customers to calculate or defining the availability SLTs are still very informal. In fact, as inputs they use mainly the history of reached service levels (when it exists) as well as the SLTs documented in existing underpinning contracts (UCs) with third parties and Operating Level Agreements (OLAs) between internal IT areas from which the service availability depends. As calculation method the main one used is the expert judgment. The lack of a formal definition of inputs and methods is leading to erroneous definitions of availability SLTs what in turn leads to fail in meeting customer service requirements because they were defined below the optimal level or incur in expensive and unnecessary acquisitions of IT resources and capabilities because they were defined above the optimal level. In this boarder, our main objective is to carry out a systematic review of the literature in order to identify and analyse the main methods that could help practitioners to define optimal availability SLTs as well as to evaluate their applicability to the industry. In addition, we consider in the review the research works addressing reliability prediction as it measures how long an IT service or system can perform its agreed function without interruption and therefore availability directly depends on it. This paper is organized as follows: Section 2 presents the related work in terms of previous surveys, Section 3 describes the method used in the literature review process and its results and finally Section 4 presents the discussion and concludes the paper. 2 RELATED WORKS Although literature reviews on availability and reliability prediction already exist (Bosse et al., 2014; Immonen & Niemelä, 2008; Goševa-Popstojanova & Trivedi, 2003), they only present the description of different approaches and do not analyse the aspects previously mentioned. Bosse et al., (2014) performed a literature review in the area of IT service availability prediction, specifically in the design phase of a service. The authors evidenced that the area is growing their publications numbers and the works were published with the following distribution: Conference (22%), Book (23%) Journal (35%) and Symposium (19%). The authors concluded about the analysis that the field of IT Service Availability prediction is still heavily discussed and current research still lacks of approaches approved by scientists and practitioners.
4 Goševa-Popstojanova and Trivedi (2003) made a survey to identify the common approaches that address the quantification of the software reliability based on black-box models. The authors give an overview about quantitative methods to assess the reliability of software systems based on architecture-based approaches. They distinguish state-based, path-based and additive approaches and present examples from literature for each category. State-based approaches model all possible states of the system. Pathbased approaches focus on execution paths. Additive models consider the system reliability as a random variable and try to map it to stochastic processes. Immonen and Niemelä, (2008) provide a survey of reliability and availability prediction methods in Software Architecture. They develop a framework to compare different methods. The framework includes criteria from the context, the users, the contents and the validation of the models. The Context is related with the goal, the scope of applicability, the architecture specificity, the platform implementation technology independency, the component specificity and the application domain independency. The Users are related to the target group, the expected benefits, the needed skills and the required resources. The Contents are associated to the language, the analysis model, the system usage, the variability, the tool support, the analysis process, the limitations and the architectural viewpoints. Finally, the Validation relates the maturity of the method, the precision of the prediction and the traceability of R&A requirements. With these criteria six different works were compared. According to the authors the most common shortcomings were a lack of support for tools and variability, weak reliability analysis of software components, and weak validation of the methods and their results. The final conclusion of the paper is that none of the investigated methods satisfies all defined criteria. 3 SURVEY METHOD AND RESULTS The structured literature review process consists of four steps: Planning, Conducting and Material Collection, Summarizing and Reporting (Bosse et al., 2014; Seuring & Müller, 2008). The Planning consist in the definition of the criteria to conduct the search and validate the selected works. It aims to identify the relevant contributions in the research fields. The Conducting and Material Collection step is related to perform a comprehensive, exhaustive search for primary approaches by using the criteria previously defined as well as validation and assessment of found approaches with respect to the research questions. In this phase the formal aspects of the identified papers are analysed in order to characterize the result set. In order to evaluate the material content related categories are identified and selected in this step. The Summarizing is related with extract for each selected work the most relevant information to answer the research questions. Finally, the Reporting phase present a synthesis of the answers for the research questions and a review analysis and interpretation of the material. 3.1 Planning The review goal is to find out the main elements used in the research literature to define the availability of IT services. The availability of IT services does not only depend on the IT infrastructure. In fact, it also depends on other IT resources and capabilities such as IT processes and teams. Thus the review concentrates on approaches related to IT processes, IT capabilities, IT infrastructures and Computer Systems. To perform the review three evaluation elements are defined: (1) Context, related with the domain, goal and scope of the approach. (2) Method, related with the necessary inputs, the techniques used to calculate availability and reliability and the output of the solution. (3) Application, related to usability of the approach which can give us hints about its potential applicability in the industry. Each element contains criteria that answer a review question. The revaluation element and criteria are presented in Table 1. Category Criteria Question Context Domain What is the main area of the work? Goal What is the goal of the approach? Scope What applications have the approach?
5 Method Input What are the inputs needed to perform the prediction? Technique What are the methods and techniques used in the solution? Output What are the solution s output and metrics? Application Tools Are there any tools that support the method? Precision of prediction How close are the predicted values to the actual values when the method has been used? Limitations What are the assumptions and limitations when using the method? Table 1. Categories, criteria and questions to resolve with the survey. 3.2 Conducting and Material Collection In order to search for primary approaches, we use the Scopus Database by introducing the following criteria: Searching terms: (Availability or Reliability) and (Software or Information Technology or IT or System or IT processes or IT capabilities) and (Prediction or Estimation or Forecast). Search area: Computer Science. Document type: Conference paper or Journal paper. Search field type: abstract, title and keywords. Language: English. Given these criteria, the Scopus searching engine gave as a result of 2249 candidate articles. To limit the number of papers to be included in the review, firstly, we limited the articles by reading the title and keywords. This filter reduced the number of works to 140. Then we read the abstract of the works to filter those ones that do not have hint to answer the review questions. This filter limited the number of work to 16. Finally, a full reading of the paper was performed to select the final set of works. A group of 9 papers were identified and included in this review. In this set of papers, a relevant survey on Availability was included. 3.3 Summarizing In this phase, data was identified, extracted and summarized for selected approaches. A description and classification of them is given below. According to Benlarbi (2006) there are two modelling approaches to evaluate networking systems availability: discrete-event simulation and analytical modelling. A discrete-event simulation model dynamically mimics detailed system behaviour to evaluate specific measures such as rerouting delays or resources utilization. An analytical modelling uses a set of mathematical equations to describe the system behaviour. The measures, e.g. the system availability, reliability and Mean Time Between Failure (MTBF), are obtained from solving these equations. The author proposes to represent the two modelling approaches by using the Reliability Block Diagram (RBD) in conjunction with a Markov Chain. In this work, each node of the network represents a state of the Markov Chain, and the availability prediction is performed by the estimation of possible change state of the Node using the RBD Logic. According to Rahman et al. (2010), exploiting the unused resources in the enterprise Grid environments across the Internet can deliver massive computer power to investigate complex problems in different scientific fields (biology, physics, astronomy, business intelligence, etc.). Thus, the prediction of a machine availability in an enterprise Grid (that goes until it restarts) is useful to perform an effective resource allocation and application scheduling. To this end, the authors propose a Jaccard Index based prediction approach in conjunction with a lazy learning algorithm that dynamically searches for a best match of a sequence pattern in the historical or training data to predict the availability. To test the approach, the author used two datasets: (i) Microsoft Corporate Network ( Pc s) and (ii) PlanetLab (321 nodes). They used two week of the traces as training data and evaluate the prediction for the following three weeks. They compare the accuracy with two existing predictive algorithms (K- NN and Naive Bayes) obtaining an improvement of and respectively.
6 Toktam and Deldari (2010) propose two prediction systems for task execution availability of resources in desktop grid platform by using binary data of availability (available and unavailable).the first system is based on cellular automats that consist of a set of cells that interact between them. The state of each cell represent a resource availability and it is updated in discrete time depending on its current state and the neighbours states by using the Von Neumann neighbourhood. The second system is based on Bayesian networks that use a feature vector of four characteristics: (i) the hour of the day and (ii, iii and iv) the availability history of the resource in the last three time steps. The accuracy of proposed prediction systems were evaluated in four real desktop grids. The comparison between the two prediction systems indicates that cellular automata have a better behaviour than Bayesian network. Rodrigues et al. (2005) propose to calculate the prediction of software system reliability by adding two attributes to software systems functional scenarios (Uchitel et al., 2004). These attributes are: (i) the probability of component failure, and (ii) the probability of transition between scenarios from an operational profile of the system which consists in a quantitative representation of how the system will be used. The extended scenario specification is then combined with probabilistic behaviour models for each component to represent the reliability of a component. Specifically, the model uses the relative frequency of the failure probability resulted from system usage and the transition probability from one scenario to another. Finally, the authors use the Cheung model for software reliability to compute a reliability prediction from the system behaviour model. Gokhale and Trivedi (2006) propose a unified framework to synthesize state-based approaches that calculate independently the reliability of software components in order to predict the whole reliability of a software. This framework uses as inputs: (i) a method of solution (Hierarchical or Composite), (ii) the system architectural model and (iii) the system failure model. From the inputs the framework relies on a classification scheme of the state-based approaches in order to assist practitioners in the selection of one of them to calculate the reliability. As the approach selected is based on either Continuous Time Markov Chain or Discrete Time Markov Chain, the inputs to calculate the probability of reliability are: transition probabilities among the software components, historical execution time and failure behaviour. According to Koutras et al. (2008), software usually presents memory leaks, fragmentation and numerical round-off errors that can cause software aging and unavailability. In this context, software rejuvenation has been proposed in the literature to perform preventive maintenance consisting in periodically stopping a running software, cleaning its internal state and then restarting it. In the rejuvenation process some errors could arise that directly impact the machine availability and cause a failed rejuvenation. Consequently, one step before to the rejuvenation is to determine what policies must be used to ensure the success of the process. Thus, the authors propose a method that uses rejuvenation policies, maximum likelihood estimators and Markov chains to predict the availability level during the rejuvenation process. Specifically, the method predicts in which of the following states the machine will be during the process: (i) robust; (ii) resource degradation; (iii) failure probable; (iv) failure may occur. Bartsch et al. (2009) propose a Petri-net based approach for modelling and simulating service processes in terms of availability levels to foster a priori estimations in design time of a service, based on the need to perform a good estimation service level agreements (SLA) between stakeholders. Petri-nets are a formal graphical process description language that combines the advantages of the graphical representation of processes with a formal definition. The authors use service downtimes and the corresponding Time to Restore Service as input parameters to simulate the availability of the service. Then, petri-nets are used to represent each state of the availability by using the duration of the service. Finally, the simulation predicts period of times when the service could be unavailable and the possible causes. According to Bosse S. (2013), ensuring high availability in IT services is crucial for IT service provider. The author argues that operator errors account a high number of service downtimes, however in current prediction systems these errors are not being considered as an important factor to predict quantitatively the availability. In this way, the author proposes a new model for availability prediction of IT services, based on flexible petri-nets simulation that includes operator errors and mechanisms to face them. The
7 approach uses models of the service components that are extended to include operators, tasks, errors and mechanisms to face errors. Within this, petri-nets are used to simulate the behaviour of the service and predict its availability. This approach requires a detailed knowledge of the system and the parameterization with real data could be difficult due to the knowledge of unknown components. Franke et al., (2014) present an architecture framework for modelling IT services in order to assess availability. This approach combines and integrate the qualitative methods, such as maturity models, with quantitative methods, such as fault trees. The framework is composed of models, meta-models, relationships and attributes suitable to represent availability. It has also features to represent a computational model with the probabilistic version of the Object Constraint Language. The model of the framework is based on fourteen systemic factors that impact software availability and integrates the structural features of the service architecture. The framework was tested empirically with nine enterprise information systems case studies, based on the availability baseline and the annual evolution of the model s factors. The outcome of the tests were availability predictions that were compared with actual outcomes, the SLA reports and System Logs. 3.4 Reporting The contributions of the ten selected approaches related to the three evaluation elements are summarised as follows: Table 2 present the Context element, Table 3 shows the Method element and Table 4 summarises the Application element. These tables allow the understanding of how availability prediction is achieved from different perspectives. Author Context Domain Goal Scope Benlarbi (2006) Networks To predict the availability of a node in a network Network Communications Rahman et al. (2010) Grid Computing To predict the availability of a Enterprise Grids machine Toktam and Deldari Grid Computing To predict the availability of a Enterprise Grids (2010) machine Rodrigues et al. (2005) Software To predict software system Software systems Engineering reliability Gokhale and Trivedi, Software To predict software system Software systems (2006) Engineering reliability Koutras et al. (2008) Software To predict the availability of a Systems' Components Engineering machine Bartsch et al. (2009) IT Services To predict the service s availability Infrastructure Services Bosse S. (2013) IT Services To predict the service s availability Infrastructure Services Franke et al. (2014) IT Services To predict the service s availability Infrastructure Services Table 2. Evidence related to the Context category of the survey Summarizing from the Table 2, it can be concluded the following with respect to each research question of the Context: What is the main area of the work? The domain areas are mainly divided in three: Software architecture and engineering, IT (infrastructure) services and networks, grid and cloud computing. As a consequence, the research literature is mainly focused on the IT infrastructure aspects and we do not find works dealing with organizational aspects such as IT support process when defining availability. What is the goal of the approach? The goal of each approach is related to its context and consists in predicting a quantitatively measure, e.g., percentage or time, of availability or reliability for a machine, node, etc. The latter is directly involved with the former as reliability is a measure of how long an IT service or other IT configuration item can perform its agreed function without interruption.
8 What applications have the approach? The approaches show that the applications are related commonly to full systems and services, in some cases, by aggregating the availability of single components. Most of the approaches are aimed to enterprise applications. Author Method Inputs Process Output Benlarbi (2006) Current Node State Markov Chains and RBD Prediction of node state Rahman et al. (2010) Historical Data of Availability Lazy algorithm that use the Jaccard Index The availability prediction of each machine Toktam and The three last states of a Cellular automats and The availability of the Deldari (2010) Rodrigues et al. (2005) Gokhale and Trivedi, (2006) machine Annotated message sequence charts, labelled transition systems Transition probabilities, execution time and failure behaviour Bayesian Networks Markov model Continuous and Discrete Time Markov Chains Koutras et al. (2008) Rejuvenation Policies Maximum likelihood estimators, Markov Chain Bartsch et al. Service downtimes and Simulation on High-level (2009) time to restore Petri Nets Bosse S. (2013) Model of each service Petri Nets and availability estimation model Franke et al., Availability baseline of 14 Probabilistic prediction (2014) factors through a framework Table 3. Evidence related to the Method category of the survey. machine System reliability estimation. Probability of component reliability Availability state of a machine Service availability Service availability Service availability Summarizing from the Table 3, it can be concluded the following with respect to each research question of the method: What are the inputs needed to perform the prediction? The inputs commonly used in the methods are historical data or states, system and service representations and probabilities of failures. What are the methods and techniques used in the solution? The techniques are variable between them, however the most used are the Markov chains and probabilistic methods. What are the solution s output and metrics? The methods mainly present as an output the forecast of availability or reliability in terms of percentages, nodes states or time. Author Benlarbi (2006) Rahman et al. (2010) Toktam and Deldari (2010) Rodrigues et al. (2005) Gokhale and Trivedi, (2006) Koutras et al. (2008) Bartsch et al. (2009) Bosse S. (2013) Application Tools Precision of prediction Limitations The calculation algorithm Not compared with A high knowledge about is automated actual values Markov Chains The calculation algorithm 98.31% of accuracy The historical Data is automated There exists commercial 95.22% of accuracy Variability on the learning tools phase Tool for synthesis of LTS Not compared with Component reliability models actual values must be available There no exists a tool that Not compared with A high knowledge about supports the approach actual values Markov Chains There no exists a tool that Not compared with A high knowledge about supports the approach actual values Markov Chains The calculation algorithm Not compared with Computational resource is automated actual values intensive The calculation algorithm The prediction differs in A high knowledge about is automated 1% of reference values the system
9 Franke et al., (2014) Table 4. EA2T tool for implementing the model The Root Mean Squared Error is 25% smaller Evidence related to the Application category of the survey. No to be used with detailed arch. models Summarizing from the Table 4, it can be concluded the following with respect to each research question of the Application: Are there any tools that support the method? Only Toktam and Deldari (2010) proposes a commercial tool that can support practitioners. However, most the calculation algorithms are automated so that it could be easy to build tools from them. How close are the predicted values to the actual values when the method has been used? The approaches that perform quantitative evaluation show a high precision in terms of accuracy. However, datasets used are smaller than real world applications and in most of the cases the authors propose as future work an exhaustive evaluation of the methods to be applicable in real context. What are the assumptions and limitations of the method? The limitations of the methods are related, in most of cases, to the availability of the inputs parameters. Also, most of the approaches were tested within controlled scenarios, cases studies and were rarely used by practitioners. 4 DISCUSSION AND CONCLUSION This paper presents a survey that identifies and analyses research works for availability and reliability prediction by using three evaluation categories: context, method and application. Each category contains criteria that answer a review question. The first category, context, is related with the domain, goal and scope of the reviewed approaches. The second category, method, analyses inputs, techniques used to calculate availability and reliability and outputs of the research works. The last, application, is intended to evaluate the usability of the reviewed approaches in the industrial context. Concerning the analysis of the context, as a result we obtained that most of the research works focus on IT infrastructure aspects which is confirmed by the fact that the main research domains concern Networks, Grid Computing, Software Engineering and IT Services. Therefore, there is a lack of research works addressing the organizational aspects involved in the definition of IT service availability such as, for example, IT support process and IT skills. Regarding the method analysis category, the inputs used in the reviewed approaches are rarely available in enterprises and real scenarios. In addition, these inputs are mainly related to the technical capabilities of the IT providers, e.g., historical availability or failure probability of technical components and communication infrastructures. However, in the SLT definition process, other inputs, that are not necessarily technical and depend on the customer, need to be included, such as the customer available budget and the criticity of the business process to be supported. Indeed, these inputs can determine the level of the technical capabilities to be delivered by the provider. Furthermore, on the provider side, inputs such as the SLT documented in existing UCs and OLAs on which the service availability can depend, need to be included as well. Respecting the calculation methods, they were not validated or used in the industry so that there is no proof of the maturity of such methods. This is because most of the works concentrate the discussion on the modelling aspect and how the method could be used. With respect to the analysis of the last evaluation category, i.e. application, the low use of the approaches by practitioners may be influenced by the low number of commercial tools and the need for expert knowledge to apply the methods. Last, the lack of a quantitative application of the approaches in real world scenarios or using datasets that relates availability of services over a long period of time results in that the accuracy of the predictions presented is not reliable. In summary, future work is needed to develop frameworks that help in the prediction of IT service availability facilitating the agreement between customers and providers. These frameworks should include other organisational factors on which IT service availability directly depend such as IT support process, skills, budget, business process criticity, among others.
10 References Bartsch, C., Mevius, M., and Oberweis, A. (2009). Simulation of IT Service Processes with Petri-Nets. Service-Oriented Computing ICSOC 2008 Workshops (pp ). Berlin: Springer Berlin Heidelberg. Benlarbi, S. (2006). Estimating SLAs availability/reliability in multi-services IP networks. Third International Service Availability Symposium (pp ). Helsinki: Lecture Notes in Computer Science. Bosse, S. (2013). Predicting an IT Service s Availability with Respect to Operator Errors. Proceedings of the Nineteenth Americas Conference on Information Systems (pp. 1-11). Chicago: AIS. Bosse, S., Splieth, M., and Turowski, K. (2014). Model-Based Prediction of IT Service Availability - A Literature Review. Proceedings of the 13th International Conference on Modeling and Applied Simulation. Bordeaux: Curran Associates. Franke, U., Pontus, J., and König, J. (2014). An architecture framework for enterprise IT service availability analysis. Software and Systems Modeling, 13(4), Gokhale, S. S., and Trivedi, K. S. (2006). Analytical Models for Architecture-Based Software Reliability Prediction: A Unification Framework. IEEE Transactions on Reliability, 55(4), Goševa-Popstojanova, K., and Trivedi, K. S. (2003). Architecture-based approaches to software reliability prediction. Computers and Mathematics with Applications, 46(7), Hunnebeck, L., Rudd, C., Lacy, S., and Hanna, A. (2011). ITIL service design. London: The Stationery Office. Immonen, A., and Niemelä, E. (2008). Survey of reliability and availability prediction methods from the viewpoint of software architecture. Software and Systems Modeling, 7(1), Koutras, V. P., Platis, A. N., and Limnios, N. (2008). Availability and reliability estimation for a system undergoing minimal, perfect and failed rejuvenation. International Conference on Software Reliability Engineering Workshops (pp. 1-6). Raleigh: IEEE. Rahman, M., Hassan, M. R., and Buyya, R. (2010). Jaccard index based availability prediction in enterprise grids. Procedia Computer Science, 1(1), Rodrigues, G., Rosenblum, D., and Uchitel, S. (2005). Using scenarios to predict the reliability of concurrent component-based software systems. Fundamental Approaches to Software Engineering (pp ). Edinburgh: Springer Berlin Heidelberg. Seuring, S., and Müller, M. (2008). From a literature review to a conceptual framework for sustainable supply chain management. Journa of cleaner production, 16(15), Toktam, G.-M., and Deldari, H. (2010). Task execution availability prediction in the enterprise desktop grid. Proceedings of the 9th Parallel and Distributed computing and networks Conferences (pp ). Innsbruck: IASTED. Uchitel, S., Kramer, J., and Magee, J. (2004). Incremental elaboration of scenario-based specifications and behavior models using implied scenarios. ACM Transactions on Software Engineering and Methodology (TOSEM), 13(1),
Evaluating Workflow Trust using Hidden Markov Modeling and Provenance Data
 Evaluating Workflow Trust using Hidden Markov Modeling and Provenance Data Mahsa Naseri and Simone A. Ludwig Abstract In service-oriented environments, services with different functionalities are combined
Evaluating Workflow Trust using Hidden Markov Modeling and Provenance Data Mahsa Naseri and Simone A. Ludwig Abstract In service-oriented environments, services with different functionalities are combined
Research on Architecture and Key Technology for Service-Oriented Workflow Performance Analysis
 Research on Architecture and Key Technology for Service-Oriented Workflow Performance Analysis Bo Liu and Yushun Fan Department of Automation, Tsinghua University, Beijing 100084, China liubo03@mails.tsinghua.edu.cn,
Research on Architecture and Key Technology for Service-Oriented Workflow Performance Analysis Bo Liu and Yushun Fan Department of Automation, Tsinghua University, Beijing 100084, China liubo03@mails.tsinghua.edu.cn,
A Study of the Production Process Simulation System Based on Workflow Management
 Association for Information Systems AIS Electronic Library (AISeL) WHICEB 2013 Proceedings Wuhan International Conference on e-business Summer 5-25-2013 A Study of the Production Process Simulation System
Association for Information Systems AIS Electronic Library (AISeL) WHICEB 2013 Proceedings Wuhan International Conference on e-business Summer 5-25-2013 A Study of the Production Process Simulation System
Project Time Management
 Project Time Management Project Time Management Project Time Management includes the processes required to manage timely completion of the project. Plan schedule management The process of establishing
Project Time Management Project Time Management Project Time Management includes the processes required to manage timely completion of the project. Plan schedule management The process of establishing
Towards Modelling-Based Self-adaptive Resource Allocation in Multi-tiers Cloud Systems
 Towards Modelling-Based Self-adaptive Resource Allocation in Multi-tiers Cloud Systems Mehdi Sliem 1(B), Nabila Salmi 1,2, and Malika Ioualalen 1 1 MOVEP Laboratory, USTHB, Algiers, Algeria {msliem,nsalmi,mioualalen}@usthb.dz
Towards Modelling-Based Self-adaptive Resource Allocation in Multi-tiers Cloud Systems Mehdi Sliem 1(B), Nabila Salmi 1,2, and Malika Ioualalen 1 1 MOVEP Laboratory, USTHB, Algiers, Algeria {msliem,nsalmi,mioualalen}@usthb.dz
A Framework for Economics-Driven Assessment of Data Quality Decisions
 Association for Information Systems AIS Electronic Library (AISeL) AMCIS 2009 Proceedings Americas Conference on Information Systems (AMCIS) 2009 A Framework for Economics-Driven Assessment of Data Quality
Association for Information Systems AIS Electronic Library (AISeL) AMCIS 2009 Proceedings Americas Conference on Information Systems (AMCIS) 2009 A Framework for Economics-Driven Assessment of Data Quality
SE curriculum in CC2001 made by IEEE and ACM: What is Software Engineering?
 SE curriculum in CC2001 made by IEEE and ACM: Overview and Ideas for Our Work Katerina Zdravkova Institute of Informatics E-mail: Keti@ii.edu.mk What is Software Engineering? SE is the discipline concerned
SE curriculum in CC2001 made by IEEE and ACM: Overview and Ideas for Our Work Katerina Zdravkova Institute of Informatics E-mail: Keti@ii.edu.mk What is Software Engineering? SE is the discipline concerned
Computational Complexity and Agent-based Software Engineering
 Srinivasan Karthikeyan Course: 609-22 (AB-SENG) Page 1 Course Number: SENG 609.22 Session: Fall, 2003 Course Name: Agent-based Software Engineering Department: Electrical and Computer Engineering Document
Srinivasan Karthikeyan Course: 609-22 (AB-SENG) Page 1 Course Number: SENG 609.22 Session: Fall, 2003 Course Name: Agent-based Software Engineering Department: Electrical and Computer Engineering Document
MANAGEMENT INFORMATION SYSTEMS COURSES Student Learning Outcomes 1
 MANAGEMENT INFORMATION SYSTEMS COURSES Student Learning Outcomes 1 MIS 180: Principles of Information Systems 1. Explain the importance of determining information system requirements for all management
MANAGEMENT INFORMATION SYSTEMS COURSES Student Learning Outcomes 1 MIS 180: Principles of Information Systems 1. Explain the importance of determining information system requirements for all management
MANAGEMENT INFORMATION SYSTEMS COURSES Student Learning Outcomes 1
 MANAGEMENT INFORMATION SYSTEMS COURSES Student Learning Outcomes 1 MIS 180: Principles of Information Systems 1. Explain the importance of determining information system requirements for all management
MANAGEMENT INFORMATION SYSTEMS COURSES Student Learning Outcomes 1 MIS 180: Principles of Information Systems 1. Explain the importance of determining information system requirements for all management
Book Outline. Software Testing and Analysis: Process, Principles, and Techniques
 Book Outline Software Testing and Analysis: Process, Principles, and Techniques Mauro PezzèandMichalYoung Working Outline as of March 2000 Software test and analysis are essential techniques for producing
Book Outline Software Testing and Analysis: Process, Principles, and Techniques Mauro PezzèandMichalYoung Working Outline as of March 2000 Software test and analysis are essential techniques for producing
Design of a Performance Measurement Framework for Cloud Computing
 A Journal of Software Engineering and Applications, 2011, *, ** doi:10.4236/jsea.2011.***** Published Online ** 2011 (http://www.scirp.org/journal/jsea) Design of a Performance Measurement Framework for
A Journal of Software Engineering and Applications, 2011, *, ** doi:10.4236/jsea.2011.***** Published Online ** 2011 (http://www.scirp.org/journal/jsea) Design of a Performance Measurement Framework for
Passit4Sure.OG Questions. TOGAF 9 Combined Part 1 and Part 2
 Passit4Sure.OG0-093.221Questions Number: OG0-093 Passing Score: 800 Time Limit: 120 min File Version: 7.1 TOGAF 9 Combined Part 1 and Part 2 One of the great thing about pass4sure is that is saves our
Passit4Sure.OG0-093.221Questions Number: OG0-093 Passing Score: 800 Time Limit: 120 min File Version: 7.1 TOGAF 9 Combined Part 1 and Part 2 One of the great thing about pass4sure is that is saves our
9. Verification, Validation, Testing
 9. Verification, Validation, Testing (a) Basic Notions (b) Dynamic testing. (c) Static analysis. (d) Modelling. (e) Environmental Simulation. (f) Test Strategies. (g) Tool support. (h) Independent Verification
9. Verification, Validation, Testing (a) Basic Notions (b) Dynamic testing. (c) Static analysis. (d) Modelling. (e) Environmental Simulation. (f) Test Strategies. (g) Tool support. (h) Independent Verification
Agent-based Architecture for Flexible Lean Cell Design, Analysis and Evaluation
 Agent-based Architecture for Flexible Lean Cell Design, Analysis and Evaluation T.E. Potok, N.D. Ivezic, N.F. Samatova Collaborative Technologies Research Center, Computer Science and Mathematics Division,
Agent-based Architecture for Flexible Lean Cell Design, Analysis and Evaluation T.E. Potok, N.D. Ivezic, N.F. Samatova Collaborative Technologies Research Center, Computer Science and Mathematics Division,
Predicting Defect Types in Software Projects
 dr Łukasz Radliński Institute of Information Technology in Management Faculty of Economics and Management University of Szczecin Predicting Defect Types in Software Projects Abstract Predicting software
dr Łukasz Radliński Institute of Information Technology in Management Faculty of Economics and Management University of Szczecin Predicting Defect Types in Software Projects Abstract Predicting software
MADVERTISER: A SYSTEM FOR MOBILE ADVERTISING IN MOBILE PEER-TO-PEER ENVIRONMENTS
 Association for Information Systems AIS Electronic Library (AISeL) PACIS 2014 Proceedings Pacific Asia Conference on Information Systems (PACIS) 2014 MADVERTISER: A SYSTEM FOR MOBILE ADVERTISING IN MOBILE
Association for Information Systems AIS Electronic Library (AISeL) PACIS 2014 Proceedings Pacific Asia Conference on Information Systems (PACIS) 2014 MADVERTISER: A SYSTEM FOR MOBILE ADVERTISING IN MOBILE
A Novel Framework to Model a Secure Information System (IS)
 2012 International Conference on Information and Computer Applications (ICICA 2012) IPCSIT vol. 24 (2012) (2012) IACSIT Press, Singapore A Novel Framework to Model a Secure Information System (IS) Youseef
2012 International Conference on Information and Computer Applications (ICICA 2012) IPCSIT vol. 24 (2012) (2012) IACSIT Press, Singapore A Novel Framework to Model a Secure Information System (IS) Youseef
Designing Software Ecosystems. How Can Modeling Techniques Help? Mahsa H. Sadi, Eric Yu. 1 Introduction. 2 Modeling Requirements.
 Introduction Ecosystems Mahsa H. Sadi, Department of Computer Science University of Toronto E mail: mhsadi@cs.toronto.edu Exploring Modeling Methods for Systems Analysis and Design (EMMSAD) Working Conference
Introduction Ecosystems Mahsa H. Sadi, Department of Computer Science University of Toronto E mail: mhsadi@cs.toronto.edu Exploring Modeling Methods for Systems Analysis and Design (EMMSAD) Working Conference
7. Model based software architecture
 UNIT - III Model based software architectures: A Management perspective and technical perspective. Work Flows of the process: Software process workflows, Iteration workflows. Check Points of The process
UNIT - III Model based software architectures: A Management perspective and technical perspective. Work Flows of the process: Software process workflows, Iteration workflows. Check Points of The process
FOUNDATIONAL CONCEPTS FOR MODEL DRIVEN SYSTEM DESIGN
 FOUNDATIONAL CONCEPTS FOR MODEL DRIVEN SYSTEM DESIGN Loyd Baker, Paul Clemente, Bob Cohen, Larry Permenter, Byron Purves, and Pete Salmon INCOSE Model Driven System Interest Group Abstract. This paper
FOUNDATIONAL CONCEPTS FOR MODEL DRIVEN SYSTEM DESIGN Loyd Baker, Paul Clemente, Bob Cohen, Larry Permenter, Byron Purves, and Pete Salmon INCOSE Model Driven System Interest Group Abstract. This paper
DEPARTMENT OF COMPUTER SCIENCE AND ENGINEERING Software Engineering Third Year CSE( Sem:I) 2 marks Questions and Answers
 DEPARTMENT OF COMPUTER SCIENCE AND ENGINEERING Software Engineering Third Year CSE( Sem:I) 2 marks Questions and Answers UNIT 1 1. What are software myths Answer: Management myths: We already have a book
DEPARTMENT OF COMPUTER SCIENCE AND ENGINEERING Software Engineering Third Year CSE( Sem:I) 2 marks Questions and Answers UNIT 1 1. What are software myths Answer: Management myths: We already have a book
A Systematic Approach to Performance Evaluation
 A Systematic Approach to Performance evaluation is the process of determining how well an existing or future computer system meets a set of alternative performance objectives. Arbitrarily selecting performance
A Systematic Approach to Performance evaluation is the process of determining how well an existing or future computer system meets a set of alternative performance objectives. Arbitrarily selecting performance
Glossary 1. For a complete glossary of support center terminology, please visit HDI s Web site at HDI Course Glossary
 Glossary 1 Term Abandon Before Answer (ABA) Rate The percentage of customers that terminate a call (i.e., hang up) before the call is answered. ABA is a leading indicator that is used to manage staffing
Glossary 1 Term Abandon Before Answer (ABA) Rate The percentage of customers that terminate a call (i.e., hang up) before the call is answered. ABA is a leading indicator that is used to manage staffing
A Study on Software Metrics and Phase based Defect Removal Pattern Technique for Project Management
 International Journal of Soft Computing and Engineering (IJSCE) A Study on Software Metrics and Phase based Defect Removal Pattern Technique for Project Management Jayanthi.R, M Lilly Florence Abstract:
International Journal of Soft Computing and Engineering (IJSCE) A Study on Software Metrics and Phase based Defect Removal Pattern Technique for Project Management Jayanthi.R, M Lilly Florence Abstract:
Document Control Information
 Document Control Information Document Details Document Name Purpose of Document Document Version Number 5.3 Document Status Document Owner Prepared By The ITIL Intermediate Qualification Service Offerings
Document Control Information Document Details Document Name Purpose of Document Document Version Number 5.3 Document Status Document Owner Prepared By The ITIL Intermediate Qualification Service Offerings
INTERACTIVE E-SCIENCE CYBERINFRASTRUCTURE FOR WORKFLOW MANAGEMENT COUPLED WITH BIG DATA TECHNOLOGY
 Section Name INTERACTIVE E-SCIENCE CYBERINFRASTRUCTURE FOR WORKFLOW MANAGEMENT COUPLE WITH BIG ATA TECHNOLOGY enis Nasonov 1 Alexander Visheratin 1 Konstantin Knyazkov 1 Sergey Kovalchuk 1 1 ITMO University,
Section Name INTERACTIVE E-SCIENCE CYBERINFRASTRUCTURE FOR WORKFLOW MANAGEMENT COUPLE WITH BIG ATA TECHNOLOGY enis Nasonov 1 Alexander Visheratin 1 Konstantin Knyazkov 1 Sergey Kovalchuk 1 1 ITMO University,
Organization of Data Warehousing in Large Service Companies: A Matrix Approach Based on Data Ownership and Competence Centers
 Association for Information Systems AIS Electronic Library (AISeL) AMCIS 2001 Proceedings Americas Conference on Information Systems (AMCIS) December 2001 Organization of Data Warehousing in Large Service
Association for Information Systems AIS Electronic Library (AISeL) AMCIS 2001 Proceedings Americas Conference on Information Systems (AMCIS) December 2001 Organization of Data Warehousing in Large Service
Models in Engineering Glossary
 Models in Engineering Glossary Anchoring bias is the tendency to use an initial piece of information to make subsequent judgments. Once an anchor is set, there is a bias toward interpreting other information
Models in Engineering Glossary Anchoring bias is the tendency to use an initial piece of information to make subsequent judgments. Once an anchor is set, there is a bias toward interpreting other information
Machine Learning 2.0 for the Uninitiated A PRACTICAL GUIDE TO IMPLEMENTING ML 2.0 SYSTEMS FOR THE ENTERPRISE.
 Machine Learning 2.0 for the Uninitiated A PRACTICAL GUIDE TO IMPLEMENTING ML 2.0 SYSTEMS FOR THE ENTERPRISE. What is ML 2.0? ML 2.0 is a new paradigm for approaching machine learning projects. The key
Machine Learning 2.0 for the Uninitiated A PRACTICAL GUIDE TO IMPLEMENTING ML 2.0 SYSTEMS FOR THE ENTERPRISE. What is ML 2.0? ML 2.0 is a new paradigm for approaching machine learning projects. The key
Document Control Information
 Document Control Information Document Details Document Name Purpose of Document Document Version Number 5.1 Document Status Document Owner Prepared By The ITIL Intermediate Qualification: Service Offerings
Document Control Information Document Details Document Name Purpose of Document Document Version Number 5.1 Document Status Document Owner Prepared By The ITIL Intermediate Qualification: Service Offerings
C. Wohlin, P. Runeson and A. Wesslén, "Software Reliability Estimations through Usage Analysis of Software Specifications and Designs", International
 C. Wohlin, P. Runeson and A. Wesslén, "Software Reliability Estimations through Usage Analysis of Software Specifications and Designs", International Journal of Reliability, Quality and Safety Engineering,
C. Wohlin, P. Runeson and A. Wesslén, "Software Reliability Estimations through Usage Analysis of Software Specifications and Designs", International Journal of Reliability, Quality and Safety Engineering,
LOGISTICAL ASPECTS OF THE SOFTWARE TESTING PROCESS
 LOGISTICAL ASPECTS OF THE SOFTWARE TESTING PROCESS Kazimierz Worwa* * Faculty of Cybernetics, Military University of Technology, Warsaw, 00-908, Poland, Email: kazimierz.worwa@wat.edu.pl Abstract The purpose
LOGISTICAL ASPECTS OF THE SOFTWARE TESTING PROCESS Kazimierz Worwa* * Faculty of Cybernetics, Military University of Technology, Warsaw, 00-908, Poland, Email: kazimierz.worwa@wat.edu.pl Abstract The purpose
The 9 knowledge Areas and the 42 Processes Based on the PMBoK 4th
 The 9 knowledge Areas and the 42 Processes Based on the PMBoK 4th www.pmlead.net PMI, PMP, CAPM and PMBOK Guide are trademarks of the Project Management Institute, Inc. PMI has not endorsed and did not
The 9 knowledge Areas and the 42 Processes Based on the PMBoK 4th www.pmlead.net PMI, PMP, CAPM and PMBOK Guide are trademarks of the Project Management Institute, Inc. PMI has not endorsed and did not
ANALYZING SYSTEM MAINTAINABILITY USING ENTERPRISE ARCHITECTURE MODELS
 ANALYZING SYSTEM MAINTAINABILITY USING ENTERPRISE ARCHITECTURE MODELS Lagerström, Robert, Royal Institute of Technology, Osquldas väg 12, 100 44 Stockholm, Sweden, robertl@ics.kth.se Abstract A fast and
ANALYZING SYSTEM MAINTAINABILITY USING ENTERPRISE ARCHITECTURE MODELS Lagerström, Robert, Royal Institute of Technology, Osquldas väg 12, 100 44 Stockholm, Sweden, robertl@ics.kth.se Abstract A fast and
AMERICAN SOCIETY FOR QUALITY CERTIFIED RELIABILITY ENGINEER (CRE) BODY OF KNOWLEDGE
 AMERICAN SOCIETY FOR QUALITY CERTIFIED RELIABILITY ENGINEER (CRE) BODY OF KNOWLEDGE The topics in this Body of Knowledge include additional detail in the form of subtext explanations and the cognitive
AMERICAN SOCIETY FOR QUALITY CERTIFIED RELIABILITY ENGINEER (CRE) BODY OF KNOWLEDGE The topics in this Body of Knowledge include additional detail in the form of subtext explanations and the cognitive
TDWI Analytics Principles and Practices
 TDWI. All rights reserved. Reproductions in whole or in part are prohibited except by written permission. DO NOT COPY Previews of TDWI course books offer an opportunity to see the quality of our material
TDWI. All rights reserved. Reproductions in whole or in part are prohibited except by written permission. DO NOT COPY Previews of TDWI course books offer an opportunity to see the quality of our material
Introduction to RAM. What is RAM? Why choose RAM Analysis?
 Introduction to RAM What is RAM? RAM refers to Reliability, Availability and Maintainability. Reliability is the probability of survival after the unit/system operates for a certain period of time (e.g.
Introduction to RAM What is RAM? RAM refers to Reliability, Availability and Maintainability. Reliability is the probability of survival after the unit/system operates for a certain period of time (e.g.
Software Next Release Planning Approach through Exact Optimization
 Software Next Release Planning Approach through Optimization Fabrício G. Freitas, Daniel P. Coutinho, Jerffeson T. Souza Optimization in Software Engineering Group (GOES) Natural and Intelligent Computation
Software Next Release Planning Approach through Optimization Fabrício G. Freitas, Daniel P. Coutinho, Jerffeson T. Souza Optimization in Software Engineering Group (GOES) Natural and Intelligent Computation
Model-Driven Design-Space Exploration for Software-Intensive Embedded Systems
 Model-Driven Design-Space Exploration for Software-Intensive Embedded Systems (extended abstract) Twan Basten 1,2, Martijn Hendriks 1, Lou Somers 2,3, and Nikola Trčka 4 1 Embedded Systems Institute, Eindhoven,
Model-Driven Design-Space Exploration for Software-Intensive Embedded Systems (extended abstract) Twan Basten 1,2, Martijn Hendriks 1, Lou Somers 2,3, and Nikola Trčka 4 1 Embedded Systems Institute, Eindhoven,
Genetic Algorithms in Matrix Representation and Its Application in Synthetic Data
 Genetic Algorithms in Matrix Representation and Its Application in Synthetic Data Yingrui Chen *, Mark Elliot ** and Joe Sakshaug *** * ** University of Manchester, yingrui.chen@manchester.ac.uk University
Genetic Algorithms in Matrix Representation and Its Application in Synthetic Data Yingrui Chen *, Mark Elliot ** and Joe Sakshaug *** * ** University of Manchester, yingrui.chen@manchester.ac.uk University
PROFESSIONAL QUALIFICATION SCHEME INTERMEDIATE QUALIFICATION SERVICE CAPABILITY SERVICE OFFERINGS AND AGREEMENTS CERTIFICATE QUALIFICATION SYLLABUS
 PROFESSIONAL QUALIFICATION SCHEME INTERMEDIATE QUALIFICATION SERVICE CAPABILITY SERVICE OFFERINGS AND AGREEMENTS CERTIFICATE QUALIFICATION SYLLABUS The Swirl logo is a Trade Mark of the Office of Government
PROFESSIONAL QUALIFICATION SCHEME INTERMEDIATE QUALIFICATION SERVICE CAPABILITY SERVICE OFFERINGS AND AGREEMENTS CERTIFICATE QUALIFICATION SYLLABUS The Swirl logo is a Trade Mark of the Office of Government
DEVELOP QUALITY CHARACTERISTICS BASED QUALITY EVALUATION PROCESS FOR READY TO USE SOFTWARE PRODUCTS
 DEVELOP QUALITY CHARACTERISTICS BASED QUALITY EVALUATION PROCESS FOR READY TO USE SOFTWARE PRODUCTS Daiju Kato 1 and Hiroshi Ishikawa 2 1 WingArc1st Inc., Tokyo, Japan kato.d@wingarc.com 2 Graduate School
DEVELOP QUALITY CHARACTERISTICS BASED QUALITY EVALUATION PROCESS FOR READY TO USE SOFTWARE PRODUCTS Daiju Kato 1 and Hiroshi Ishikawa 2 1 WingArc1st Inc., Tokyo, Japan kato.d@wingarc.com 2 Graduate School
Master of Business Administration (General)
 MBA 510 Financial Accounting Cr Hr: 3 Prerequisite: MBA 511 Grad Scheme: Letter At the end of this course, students will be able to read, analyse and interpret financial data, appreciate the financial
MBA 510 Financial Accounting Cr Hr: 3 Prerequisite: MBA 511 Grad Scheme: Letter At the end of this course, students will be able to read, analyse and interpret financial data, appreciate the financial
7. Project Management
 Subject/Topic/Focus: 7. Project Management Management of Systems Engineering Processes Summary: Project management Systems engineering Maturity model and process improvement Literature: Ian Sommerville:
Subject/Topic/Focus: 7. Project Management Management of Systems Engineering Processes Summary: Project management Systems engineering Maturity model and process improvement Literature: Ian Sommerville:
Design of an Integrated Model for Development of Business and Enterprise Systems
 International Journal of Research Studies in Computer Science and Engineering (IJRSCSE) Volume 2, Issue 5, May 2015, PP 50-57 ISSN 2349-4840 (Print) & ISSN 2349-4859 (Online) www.arcjournals.org Design
International Journal of Research Studies in Computer Science and Engineering (IJRSCSE) Volume 2, Issue 5, May 2015, PP 50-57 ISSN 2349-4840 (Print) & ISSN 2349-4859 (Online) www.arcjournals.org Design
Software Engineering (CSC 4350/6350) Rao Casturi
 Software Engineering (CSC 4350/6350) Rao Casturi Recap What is software engineering? Modeling Problem solving Knowledge acquisition Rational Managing Software development Communication Rational Management
Software Engineering (CSC 4350/6350) Rao Casturi Recap What is software engineering? Modeling Problem solving Knowledge acquisition Rational Managing Software development Communication Rational Management
HP Operations Analytics
 HP Operations Analytics March 10, 2015 Joe Hasenohr, Ryan Huneidi HP Software HP Business Service Management Ensure optimal IT performance and availability in a dynamic world Business Service Management
HP Operations Analytics March 10, 2015 Joe Hasenohr, Ryan Huneidi HP Software HP Business Service Management Ensure optimal IT performance and availability in a dynamic world Business Service Management
IT Investment Decision Making: A Decision Analysis Cycle Model
 Association for Information Systems AIS Electronic Library (AISeL) AMCIS 2010 Proceedings Americas Conference on Information Systems (AMCIS) 8-2010 IT Investment Decision Making: A Decision Analysis Cycle
Association for Information Systems AIS Electronic Library (AISeL) AMCIS 2010 Proceedings Americas Conference on Information Systems (AMCIS) 8-2010 IT Investment Decision Making: A Decision Analysis Cycle
 CLASS/YEAR: II MCA SUB.CODE&NAME: MC7303, SOFTWARE ENGINEERING. 1. Define Software Engineering. Software Engineering: 2. What is a process Framework? Process Framework: UNIT-I 2MARKS QUESTIONS AND ANSWERS
CLASS/YEAR: II MCA SUB.CODE&NAME: MC7303, SOFTWARE ENGINEERING. 1. Define Software Engineering. Software Engineering: 2. What is a process Framework? Process Framework: UNIT-I 2MARKS QUESTIONS AND ANSWERS
Methodology for Selecting the Preferred Networked Computer System Solution for Dynamic Continuous Defense Missions
 Methodology for Selecting the Preferred Networked Computer Solution for Dynamic Continuous Defense Missions San Diego Dr. Glenn S. Tolentino Command & Control and Enterprise Engineering Department SPAWAR
Methodology for Selecting the Preferred Networked Computer Solution for Dynamic Continuous Defense Missions San Diego Dr. Glenn S. Tolentino Command & Control and Enterprise Engineering Department SPAWAR
Towards a Model-driven and Tool-integration Framework for Co- Simulation Environments. Jinzhi Lu, Martin Törngren
 Towards a Model-driven and Tool-integration Framework for Co- Simulation Environments Jinzhi Lu, Martin Törngren I. INTRODUCTION Cyber-Physical Systems (CPS) have evolved continuously over the past decades
Towards a Model-driven and Tool-integration Framework for Co- Simulation Environments Jinzhi Lu, Martin Törngren I. INTRODUCTION Cyber-Physical Systems (CPS) have evolved continuously over the past decades
TDWI Analytics Fundamentals. Course Outline. Module One: Concepts of Analytics
 TDWI Analytics Fundamentals Module One: Concepts of Analytics Analytics Defined Data Analytics and Business Analytics o Variations of Purpose o Variations of Skills Why Analytics o Cause and Effect o Strategy
TDWI Analytics Fundamentals Module One: Concepts of Analytics Analytics Defined Data Analytics and Business Analytics o Variations of Purpose o Variations of Skills Why Analytics o Cause and Effect o Strategy
A Comparative Study on the existing methods of Software Size Estimation
 A Comparative Study on the existing methods of Software Size Estimation Manisha Vatsa 1, Rahul Rishi 2 Department of Computer Science & Engineering, University Institute of Engineering & Technology, Maharshi
A Comparative Study on the existing methods of Software Size Estimation Manisha Vatsa 1, Rahul Rishi 2 Department of Computer Science & Engineering, University Institute of Engineering & Technology, Maharshi
Research Article Scheduling Methods for Food Resource Management under the Environment of Cloud
 Advance Journal of Food Science and Technology 11(4): 281-285, 2016 DOI:10.19026/ajfst.11.2411 ISSN: 2042-4868; e-issn: 2042-4876 2016 Maxwell Scientific Publication Corp. Submitted: May 5, 2015 Accepted:
Advance Journal of Food Science and Technology 11(4): 281-285, 2016 DOI:10.19026/ajfst.11.2411 ISSN: 2042-4868; e-issn: 2042-4876 2016 Maxwell Scientific Publication Corp. Submitted: May 5, 2015 Accepted:
Workflow Model Representation Concepts
 Workflow Model Representation Concepts József Tick Institute for Software Engineering, John von Neumann Faculty, Budapest Tech tick@bmf.hu Abstract: Workflow management and the possibilities of workflow
Workflow Model Representation Concepts József Tick Institute for Software Engineering, John von Neumann Faculty, Budapest Tech tick@bmf.hu Abstract: Workflow management and the possibilities of workflow
nddprint MPS White Paper - Print Management Service
 White Paper - Print Management Service nddprint MPS nddprint MPS is the most complete cloud-based architecture solution, developed to meet the needs of print outsourcing operations. The service goal is
White Paper - Print Management Service nddprint MPS nddprint MPS is the most complete cloud-based architecture solution, developed to meet the needs of print outsourcing operations. The service goal is
MANAGEMENT INFORMATION SYSTEMS COURSES Student Learning Outcomes 1
 MANAGEMENT INFORMATION SYSTEMS COURSES Student Learning Outcomes 1 MIS 180: Principles of Information Systems 1. Explain the importance of determining information system requirements for all management
MANAGEMENT INFORMATION SYSTEMS COURSES Student Learning Outcomes 1 MIS 180: Principles of Information Systems 1. Explain the importance of determining information system requirements for all management
BIOINFORMATICS AND SYSTEM BIOLOGY (INTERNATIONAL PROGRAM)
 BIOINFORMATICS AND SYSTEM BIOLOGY (INTERNATIONAL PROGRAM) PROGRAM TITLE DEGREE TITLE Master of Science Program in Bioinformatics and System Biology (International Program) Master of Science (Bioinformatics
BIOINFORMATICS AND SYSTEM BIOLOGY (INTERNATIONAL PROGRAM) PROGRAM TITLE DEGREE TITLE Master of Science Program in Bioinformatics and System Biology (International Program) Master of Science (Bioinformatics
Challenge H: For an even safer and more secure railway
 The application of risk based safety analysis has been introduced to the Railway system with the publication of the dedicated standard EN 50 126 in 1999. In the railway sector the application of these
The application of risk based safety analysis has been introduced to the Railway system with the publication of the dedicated standard EN 50 126 in 1999. In the railway sector the application of these
Probabilistic Macro-Architectural Decision Framework
 Probabilistic Macro-Architectural Decision Framework Plamen Petrov, University of Robert L. Nord, Carnegie Mellon University Ugo Buy, University of Presented at the 2 nd International Workshop on Software
Probabilistic Macro-Architectural Decision Framework Plamen Petrov, University of Robert L. Nord, Carnegie Mellon University Ugo Buy, University of Presented at the 2 nd International Workshop on Software
PMBOK Guide Fifth Edition Pre Release Version October 10, 2012
 5.3.1 Define Scope: Inputs PMBOK Guide Fifth Edition 5.3.1.1 Scope Management Plan Described in Section 5.1.3.1.The scope management plan is a component of the project management plan that establishes
5.3.1 Define Scope: Inputs PMBOK Guide Fifth Edition 5.3.1.1 Scope Management Plan Described in Section 5.1.3.1.The scope management plan is a component of the project management plan that establishes
ITIL Intermediate Lifecycle Stream:
 ITIL Intermediate Lifecycle Stream: CONTINUAL SERVICE IMPROVEMENT (CSI) CERTIFICATE Sample Paper 2, version 6.1 Gradient Style, Complex Multiple Choice QUESTION BOOKLET Gradient Style Multiple Choice 90
ITIL Intermediate Lifecycle Stream: CONTINUAL SERVICE IMPROVEMENT (CSI) CERTIFICATE Sample Paper 2, version 6.1 Gradient Style, Complex Multiple Choice QUESTION BOOKLET Gradient Style Multiple Choice 90
Availability Modeling of Grid Computing Environments Using SANs
 Availability Modeling of Grid Computing Environments Using SANs Reza Entezari-Maleki Department of Computer Engineering, Sharif University of Technology, Tehran, Iran E-mail: entezari@ce.sharif.edu Ali
Availability Modeling of Grid Computing Environments Using SANs Reza Entezari-Maleki Department of Computer Engineering, Sharif University of Technology, Tehran, Iran E-mail: entezari@ce.sharif.edu Ali
Modelling the Risk In Defence Engineering
 Modelling the Risk In Defence Engineering Model-Based Systems Engineering Symposium 27 October 2014 Canberra, Australia Presented by Chris Stecki, PHM Technology Executive Summary Defence is transitioning
Modelling the Risk In Defence Engineering Model-Based Systems Engineering Symposium 27 October 2014 Canberra, Australia Presented by Chris Stecki, PHM Technology Executive Summary Defence is transitioning
Business Flexibility and Operational Efficiency - Making Trade-Offs in Service Oriented Architecture
 Association for Information Systems AIS Electronic Library (AISeL) AMCIS 2005 Proceedings Americas Conference on Information Systems (AMCIS) 2005 Business Flexibility and Operational Efficiency - Making
Association for Information Systems AIS Electronic Library (AISeL) AMCIS 2005 Proceedings Americas Conference on Information Systems (AMCIS) 2005 Business Flexibility and Operational Efficiency - Making
Industrial Case: Blockchain on Aircraft s Parts Supply Chain Management
 Association for Information Systems AIS Electronic Library (AISeL) AMCIS 2017 Workshops Special Interest Group on Big Data Proceedings 2017 Industrial Case: Blockchain on Aircraft s Parts Supply Chain
Association for Information Systems AIS Electronic Library (AISeL) AMCIS 2017 Workshops Special Interest Group on Big Data Proceedings 2017 Industrial Case: Blockchain on Aircraft s Parts Supply Chain
Vendor: ISEB. Exam Code: BH Exam Name: ITIL V3 Foundation Certificate in IT Service Management. Version: Demo
 Vendor: ISEB Exam Code: BH0-006 Exam Name: ITIL V3 Foundation Certificate in IT Service Management Version: Demo QUESTION 1 Which of the following is NOT an example of Self-Help capabilities? A. Requirement
Vendor: ISEB Exam Code: BH0-006 Exam Name: ITIL V3 Foundation Certificate in IT Service Management Version: Demo QUESTION 1 Which of the following is NOT an example of Self-Help capabilities? A. Requirement
Business Intelligence, 4e (Sharda/Delen/Turban) Chapter 2 Descriptive Analytics I: Nature of Data, Statistical Modeling, and Visualization
 Business Intelligence, 4e (Sharda/Delen/Turban) Chapter 2 Descriptive Analytics I: Nature of Data, Statistical Modeling, and Visualization 1) One of SiriusXM's challenges was tracking potential customers
Business Intelligence, 4e (Sharda/Delen/Turban) Chapter 2 Descriptive Analytics I: Nature of Data, Statistical Modeling, and Visualization 1) One of SiriusXM's challenges was tracking potential customers
ITIL V3 Foundation (Classified Questions) Page 1 of Which of the following questions does Service Strategy help answer with its guidance?
 ITIL V3 Foundation (Classified Questions) Page 1 of 21 Service Strategy 1. Which of the following questions does Service Strategy help answer with its guidance? 1. How do we prioritize investments across
ITIL V3 Foundation (Classified Questions) Page 1 of 21 Service Strategy 1. Which of the following questions does Service Strategy help answer with its guidance? 1. How do we prioritize investments across
Enhancing Utility Outage Management System (OMS) Performance
 Enhancing Utility Outage Management System (OMS) Performance by John Dirkman, P.E. Executive summary Traditional grid outage management systems suffer from two fundamental flaws: they lack an accurate,
Enhancing Utility Outage Management System (OMS) Performance by John Dirkman, P.E. Executive summary Traditional grid outage management systems suffer from two fundamental flaws: they lack an accurate,
Generative Models for Networks and Applications to E-Commerce
 Generative Models for Networks and Applications to E-Commerce Patrick J. Wolfe (with David C. Parkes and R. Kang-Xing Jin) Division of Engineering and Applied Sciences Department of Statistics Harvard
Generative Models for Networks and Applications to E-Commerce Patrick J. Wolfe (with David C. Parkes and R. Kang-Xing Jin) Division of Engineering and Applied Sciences Department of Statistics Harvard
[2010] IEEE. Reprinted, with permission, from Didar Zowghi, A Framework for the Elicitation and Analysis of Information Technology Service
![[2010] IEEE. Reprinted, with permission, from Didar Zowghi, A Framework for the Elicitation and Analysis of Information Technology Service [2010] IEEE. Reprinted, with permission, from Didar Zowghi, A Framework for the Elicitation and Analysis of Information Technology Service](/thumbs/86/94317481.jpg) [2010] IEEE. Reprinted, with permission, from Didar Zowghi, A Framework for the Elicitation and Analysis of Information Technology Service Requirements and Their Alignment with Enterprise Business Goals,
[2010] IEEE. Reprinted, with permission, from Didar Zowghi, A Framework for the Elicitation and Analysis of Information Technology Service Requirements and Their Alignment with Enterprise Business Goals,
Enterprise resource planning Product life-cycle management Manufacturing operations management Information systems in industry ELEC-E8113
 Enterprise resource planning Product life-cycle management Manufacturing operations management Information systems in industry ELEC-E8113 Contents Enterprise resource planning (ERP) Product lifecycle management
Enterprise resource planning Product life-cycle management Manufacturing operations management Information systems in industry ELEC-E8113 Contents Enterprise resource planning (ERP) Product lifecycle management
ericsson White paper GFMC-17: Uen October 2017 TELECOM IT FOR THE DIGITAL ECONOMY
 ericsson White paper GFMC-17:000619 Uen October 2017 TELECOM IT FOR THE DIGITAL ECONOMY Introduction The rapidly expanding digital economy has exposed a clear gap in both the architecture and operational
ericsson White paper GFMC-17:000619 Uen October 2017 TELECOM IT FOR THE DIGITAL ECONOMY Introduction The rapidly expanding digital economy has exposed a clear gap in both the architecture and operational
e7 Capacity Expansion Long-term resource planning for resource planners and portfolio managers
 e7 Capacity Expansion Long-term resource planning for resource planners and portfolio managers e7 Capacity Expansion Overview The e7 Capacity Expansion solution gives resource planners and portfolio managers
e7 Capacity Expansion Long-term resource planning for resource planners and portfolio managers e7 Capacity Expansion Overview The e7 Capacity Expansion solution gives resource planners and portfolio managers
Knowledge Areas According to the PMBOK edition 5. Chapter 4 - Integration
 Knowledge Areas According to the PMBOK edition 5 Chapter 4 - Integration 4.1 - Develop Project Charter Process Project statement of work Expert Judgment Project charter Business case Facilitation techniques
Knowledge Areas According to the PMBOK edition 5 Chapter 4 - Integration 4.1 - Develop Project Charter Process Project statement of work Expert Judgment Project charter Business case Facilitation techniques
Evaluation of Modeling Techniques for Agent- Based Systems
 A tutorial report for SENG 609.22 Agent Based Software Engineering Course Instructor: Dr. Behrouz H. Far Evaluation of Modeling Techniques for Agent- Based Systems Prepared by: Wei Shen ABSTRACT To develop
A tutorial report for SENG 609.22 Agent Based Software Engineering Course Instructor: Dr. Behrouz H. Far Evaluation of Modeling Techniques for Agent- Based Systems Prepared by: Wei Shen ABSTRACT To develop
Deliverable: 1.4 Software Version Control and System Configuration Management Plan
 Deliverable: 1.4 Software Version Control and System Configuration VoteCal Statewide Voter Registration System Project State of California, Secretary of State (SOS) Authors This document was prepared
Deliverable: 1.4 Software Version Control and System Configuration VoteCal Statewide Voter Registration System Project State of California, Secretary of State (SOS) Authors This document was prepared
PSS E. High-Performance Transmission Planning Application for the Power Industry. Answers for energy.
 PSS E High-Performance Transmission Planning Application for the Power Industry Answers for energy. PSS E architecture power flow, short circuit and dynamic simulation Siemens Power Technologies International
PSS E High-Performance Transmission Planning Application for the Power Industry Answers for energy. PSS E architecture power flow, short circuit and dynamic simulation Siemens Power Technologies International
Functional Analysis Module
 CC532 Collaborate System Design Fundamentals of Systems Engineering W6, Spring, 2012 KAIST Functional Analysis Module Space Systems Engineering, version 1.0 Space Systems Engineering: Functional Analysis
CC532 Collaborate System Design Fundamentals of Systems Engineering W6, Spring, 2012 KAIST Functional Analysis Module Space Systems Engineering, version 1.0 Space Systems Engineering: Functional Analysis
This chapter illustrates the evolutionary differences between
 CHAPTER 6 Contents An integrated approach Two representations CMMI process area contents Process area upgrades and additions Project management concepts process areas Project Monitoring and Control Engineering
CHAPTER 6 Contents An integrated approach Two representations CMMI process area contents Process area upgrades and additions Project management concepts process areas Project Monitoring and Control Engineering
TOGAF 9.1 Phases E-H & Requirements Management
 TOGAF 9.1 Phases E-H & Requirements Management By: Samuel Mandebvu Sources: 1. Primary Slide Deck => Slide share @ https://www.slideshare.net/sammydhi01/learn-togaf-91-in-100-slides 1. D Truex s slide
TOGAF 9.1 Phases E-H & Requirements Management By: Samuel Mandebvu Sources: 1. Primary Slide Deck => Slide share @ https://www.slideshare.net/sammydhi01/learn-togaf-91-in-100-slides 1. D Truex s slide
AIS Electronic Library (AISeL) Association for Information Systems. jiaxin Li School of Economics and Management, Dalian Jiao Tong University, China
 Association for Information Systems AIS Electronic Library (AISeL) WHICEB 2014 Proceedings Wuhan International Conference on e-business Summer 6-1-2014 Research on Operating Mechanism of Collaborative
Association for Information Systems AIS Electronic Library (AISeL) WHICEB 2014 Proceedings Wuhan International Conference on e-business Summer 6-1-2014 Research on Operating Mechanism of Collaborative
APM Reliability Classic from GE Digital Part of our On-Premise Asset Performance Management Classic Solution Suite
 Provides operational visibility and analysis to help reduce asset failure, control costs and increase availability With escalating pressure on businesses to improve the bottom-line while being faced with
Provides operational visibility and analysis to help reduce asset failure, control costs and increase availability With escalating pressure on businesses to improve the bottom-line while being faced with
Model Driven Architecture as Approach to Manage Variability in Software Product Families
 Model Driven Architecture as Approach to Manage Variability in Software Product Families Sybren Deelstra, Marco Sinnema, Jilles van Gurp, Jan Bosch Department of Mathematics and Computer Science, University
Model Driven Architecture as Approach to Manage Variability in Software Product Families Sybren Deelstra, Marco Sinnema, Jilles van Gurp, Jan Bosch Department of Mathematics and Computer Science, University
TOGAF - The - The Continuing Story Story
 TOGAF - The - The Continuing Story Story The Open Group Framework (TOGAF) Presented by Chris Greenslade Chris@Architecting-the-Enterprise.com 1 of 53 TA P14 1 The questions to answer Who are we? What principles
TOGAF - The - The Continuing Story Story The Open Group Framework (TOGAF) Presented by Chris Greenslade Chris@Architecting-the-Enterprise.com 1 of 53 TA P14 1 The questions to answer Who are we? What principles
AN INTRODUCTION TO USING PROSIM FOR BUSINESS PROCESS SIMULATION AND ANALYSIS. Perakath C. Benjamin Dursun Delen Madhav Erraguntla
 Proceedings of the 1998 Winter Simulation Conference D.J. Medeiros, E.F. Watson, J.S. Carson and M.S. Manivannan, eds. AN INTRODUCTION TO USING PROSIM FOR BUSINESS PROCESS SIMULATION AND ANALYSIS Perakath
Proceedings of the 1998 Winter Simulation Conference D.J. Medeiros, E.F. Watson, J.S. Carson and M.S. Manivannan, eds. AN INTRODUCTION TO USING PROSIM FOR BUSINESS PROCESS SIMULATION AND ANALYSIS Perakath
Work Product Dependency Diagram
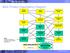 Work Product Dependency Diagram Project Definition System Context Subject Area Model Architectural Decisions Requirements Matrix Use Case Model Service Model Non Functional Requirements Component Model
Work Product Dependency Diagram Project Definition System Context Subject Area Model Architectural Decisions Requirements Matrix Use Case Model Service Model Non Functional Requirements Component Model
Testing of Web Services A Systematic Mapping
 Testing of Web Services A Systematic Mapping Abhishek Sharma, Theodore D. Hellmann, Frank Maurer Department of Computer Science University of Calgary Calgary, Canada {absharma, tdhellma, frank.maurer}@ucalgary.ca
Testing of Web Services A Systematic Mapping Abhishek Sharma, Theodore D. Hellmann, Frank Maurer Department of Computer Science University of Calgary Calgary, Canada {absharma, tdhellma, frank.maurer}@ucalgary.ca
Summary of 47 project management processes (PMBOK Guide, 5 th edition, 2013)
 Summary of 47 project management processes (PMBOK Guide, 5 th edition, 2013) Integration Management: processes & activities needed to properly coordinate all aspects of the project to meet stakeholder
Summary of 47 project management processes (PMBOK Guide, 5 th edition, 2013) Integration Management: processes & activities needed to properly coordinate all aspects of the project to meet stakeholder
Olin Business School Master of Science in Customer Analytics (MSCA) Curriculum Academic Year. List of Courses by Semester
 Olin Business School Master of Science in Customer Analytics (MSCA) Curriculum 2017-2018 Academic Year List of Courses by Semester Foundations Courses These courses are over and above the 39 required credits.
Olin Business School Master of Science in Customer Analytics (MSCA) Curriculum 2017-2018 Academic Year List of Courses by Semester Foundations Courses These courses are over and above the 39 required credits.
A Platform for Risk Analysis of Security Critical Systems
 of Security Critical Systems Model-based Risk Analysis Targeting Security Bjørn Axel Gran Institutt for energiteknikk / OECD Halden Reactor Project bjorn.axel.gran@hrp.no Overview Introduction The CORAS
of Security Critical Systems Model-based Risk Analysis Targeting Security Bjørn Axel Gran Institutt for energiteknikk / OECD Halden Reactor Project bjorn.axel.gran@hrp.no Overview Introduction The CORAS
Chapter 3 DECISION SUPPORT SYSTEMS CONCEPTS, METHODOLOGIES, AND TECHNOLOGIES: AN OVERVIEW
 Chapter 3 DECISION SUPPORT SYSTEMS CONCEPTS, METHODOLOGIES, AND TECHNOLOGIES: AN OVERVIEW Learning Objectives Understand possible decision support system (DSS) configurations Understand the key differences
Chapter 3 DECISION SUPPORT SYSTEMS CONCEPTS, METHODOLOGIES, AND TECHNOLOGIES: AN OVERVIEW Learning Objectives Understand possible decision support system (DSS) configurations Understand the key differences
The Three Dimensions of Requirements Engineering: 20 Years Later
 The Three Dimensions of Requirements Engineering: 20 Years Later Klaus Pohl and Nelufar Ulfat-Bunyadi Abstract Requirements engineering is the process of eliciting stakeholder needs and desires and developing
The Three Dimensions of Requirements Engineering: 20 Years Later Klaus Pohl and Nelufar Ulfat-Bunyadi Abstract Requirements engineering is the process of eliciting stakeholder needs and desires and developing
Daniel Research Group
 Daniel Research Group Understanding the Future Understanding the Future A Practical Guide to Designing and Developing Context Specific Segmented Forecasts and Models for Technology Markets Technology Forecast
Daniel Research Group Understanding the Future Understanding the Future A Practical Guide to Designing and Developing Context Specific Segmented Forecasts and Models for Technology Markets Technology Forecast
IBM WebSphere Extended Deployment, Version 5.1
 Offering a dynamic, goals-directed, high-performance environment to support WebSphere applications IBM, Version 5.1 Highlights Dynamically accommodates variable and unpredictable business demands Helps
Offering a dynamic, goals-directed, high-performance environment to support WebSphere applications IBM, Version 5.1 Highlights Dynamically accommodates variable and unpredictable business demands Helps
Simulation Analytics
 Simulation Analytics Powerful Techniques for Generating Additional Insights Mark Peco, CBIP mark.peco@gmail.com Objectives Basic capabilities of computer simulation Categories of simulation techniques
Simulation Analytics Powerful Techniques for Generating Additional Insights Mark Peco, CBIP mark.peco@gmail.com Objectives Basic capabilities of computer simulation Categories of simulation techniques
Appendix C: MS Project Software Development Plan and Excel Budget.
 1. Introduction. Appendix C: MS Project Software Development Plan and Excel Budget. Project: PickUp Game App The Project plan for this Application consist of 76 days; In this plan is defined how long each
1. Introduction. Appendix C: MS Project Software Development Plan and Excel Budget. Project: PickUp Game App The Project plan for this Application consist of 76 days; In this plan is defined how long each
Big Data. Methodological issues in using Big Data for Official Statistics
 Giulio Barcaroli Istat (barcarol@istat.it) Big Data Effective Processing and Analysis of Very Large and Unstructured data for Official Statistics. Methodological issues in using Big Data for Official Statistics
Giulio Barcaroli Istat (barcarol@istat.it) Big Data Effective Processing and Analysis of Very Large and Unstructured data for Official Statistics. Methodological issues in using Big Data for Official Statistics
