Information Security Policy Compliance: A User Acceptance Perspective
|
|
|
- Emil Barrett
- 6 years ago
- Views:
Transcription
1 Association for Information Systems AIS Electronic Library (AISeL) MWAIS 2011 Proceedings Midwest (MWAIS) Information Security Policy Compliance: A User Acceptance Perspective Ahmad Al-Omari, Aaal-omari8026@pluto.dsu.edu Omar El-Gayar, omar.el-gayar@dsu.edu Amit Deokar, Amit.Deokar@dsu.edu Follow this and additional works at: Recommended Citation Al-Omari, Ahmad; El-Gayar, Omar; and Deokar, Amit, "" (2011). MWAIS 2011 Proceedings This material is brought to you by the Midwest (MWAIS) at AIS Electronic Library (AISeL). It has been accepted for inclusion in MWAIS 2011 Proceedings by an authorized administrator of AIS Electronic Library (AISeL). For more information, please contact elibrary@aisnet.org.
2 ABSTRACT Information Security Policy Compliance: A User Acceptance Perspective Ahmad Al-Omari Aaal-omari8026@pluto.dsu.edu Amit Deokar Amit.Doekar@dsu.edu Omar El-Gayar Omar.El-Gayar@dsu.edu Compliance with information security policies (ISPs) is a key factor in reducing an organization s information security risks. As such, understanding employees compliance behavior with ISPs is an important first step to leverage knowledge worker assets in efforts targeted toward reducing information security risks. This study adapts the Technology Acceptance Model (TAM) to examine users behavioral intention to comply with ISPs. The impact of information security awareness on behavioral intentions to comply is also considered in the research model. This is a research in progress, and an instrument is being developed to conduct a survey study to gather data from employees in the banking sector in Jordan. Keywords: Information security awareness, compliance, information security policy, technology acceptance model, behavioral issues of information security. INTRODUCTION Information security has become one of the most important concerns and challenges facing organizations and users today. Studies concentrate on the need to design effective security policies (Whitman, Townsend, & Aalberts, 2001), as well as to motivate human and organizational factors to enhance users security awareness to comply with ISPs (Boss, Kirsch, Angermeier, Shingler, & Boss, 2009). Information security policies (ISPs) must be designed to provide employees with guidelines on how to secure information resources while they use information systems (IS) in performing their jobs (Straub, 1990; Whitman, et al., 2001). Although the creation of comprehensive ISPs and guidelines is given high priority, compliance with these policies is still lacking. Therefore, identifying the factors that motivate employees awareness to comply with an organization s ISPs is an important step. Drawing on the Technology Acceptance Model (TAM) (Davis, Bagozzi, & Warshaw, 1989), we propose a Security Acceptance Model (SAM). In this model, employees intention to comply with the organization s ISPs is influenced by Perceived Ease of Use (PEOU) of ISPs and Perceived Usefulness of Protection (PUOP) afforded through the use of ISPs. The role of self-efficacy (SE) and controllability (C), which are rooted in the Theory of Planned Behavior (TPB) (Ajzen, 2002), have also been considered. The proposed model captures some of the questions left unanswered by the previous studies. Besides, it is the first to completely examine the role of information security awareness in enhancing employees compliance with ISPs. Specifically, the study will try to answer the following questions: 1. What is the role of information security awareness in forming employees behavior toward compliance with ISPs? 2. What are the employees perceptions about their roles and responsibilities, as set in the ISPs, in safeguarding organization s information resources toward compliance with ISPs? 3. What are the employees perceptions about the degree of difficulty in complying with ISPs? The next section presents a brief review of the relevant literature and highlights this study s contributions. The third section presents the research model. The fourth section describes the research methodology, survey instrument, sample, and data collection method. LITERATURE REVIEW Employees compliance with ISPs is an important concern for organizations to prevent and reduce information system resources misuse and abuse by insiders (Straub, 1990). Studies that investigate end-user behavior argue that employees willingly choose to misuse or abuse the system (Bulgurcu, Cavusoglu, & Benbasat, 2010). Most empirical studies applied deterrence theory as a way to reduce system s abuse and misuse. Straub, (1990) found that different preventive and deterrent Proceedings of the Sixth Midwest Association for Information Systems Conference, Omaha, NE May 20-21,
3 User Awareness of Al-Omari, et al., 2011 techniques were found to be effective to reduce system abuse. (Kankanhalli, Teo, Tan, & Wei, 2003) found that greater deterrent effort appears to contribute to better IS security effectiveness. Similarly, (Pahnila, Siponen, & Mahmood, 2007) found that sanctions do not have an effect on employees intentions to comply with ISPs. Other studies employed different theories. Drawing on TPB and Rational Choice Theory, Bulgurcu, et al. (2010), found that attitude, normative belief, and self-efficacy have a significant effect on employees intention to comply with ISPs. Drawing on Protection Motivation Theory along with the Theory of Reasoned Action and TPB, Anderson & Agarwal (2010) found that home computer users intentions to perform security-related behavior are influenced by a combination of cognitive, social, and psychological factors. Siponen & Vance (2010) found that neutralization is an excellent predictor of employees intention to violate ISPs. Johnston & Warkentin (2010) found that fear appeal is a positive predictor of a user s behavioral intention to comply with recommended individual security acts. Based on the Theory of Planned Behavior (TPB) and TAM, (Dinev & Hu 2007) found that higher awareness leads to higher confidence in preventing negative technologies; and PU and PEOU have no significant effect on users intention to use protective technologies. Jones (2009) found that PU and Subjective Norms are significant predictors of employees behavioral intention to use security controls. D'Arcy, Hovav, & Galletta (2009) found that users awareness of security controls has an impact on sanctions perceptions which in turn reduced IS misuse intentions. Bulgurcu, et al. (2010) found that information security awareness has a strong effect on an employee s attitude to comply with the ISPs. Various behavioral theories have been employed to study employees compliance intentions with ISPs or to prevent systems misuse. While these studies have highlighted either the deterrent effect of sanctions or the role of incentives in encouraging employees desirable behavior, none of the studies have addressed this problem as a system that employees must accept first, as (Davis, 1986) did with the ordeal of accepting the technology. To address this gap, this research aims to develop a Security Acceptance Model (SAM), analogous to the TAM, to understand how information security awareness will enhance employees compliance with ISPs by enhancing the degree to which they believe that putting ISPs into practice and engaging in the corresponding roles and responsibilities are relatively effortless (PEOU), and that using these roles and responsibilities to safeguard the organization s information technology resources will help their job duties and performance (PUOP). RESEARCH MODEL Based on TAM developed by (Davis, et al., 1989), a Security Awareness Model (SAM) (Figure 1) is proposed, which will help explain employees intention to comply with ISPs. This study will examine the effect of external variables, namely perceived security protection mechanisms (security policies, Security education, Training and Awareness (SETA) programs, and computer monitoring) proposed and tested by D'Arcy & Hovav (2009), D'Arcy, et al. (2009), and Straub, (1990), controllability (Dinev & Hu, 2007; Rhee, Kim, & Ryu, 2009), information security awareness (Bulgurcu, et al., 2010) and self-efficacy (Dinev & Hu, 2007; Workman, Bommer, & Straub, 2008), on PUOP and PEOU of ISPs. Information security awareness is posited to directly influence employees perceived usefulness toward compliance with ISPs (Bulgurcu, et al., 2010). The original relations in the TAM model are posited to hold in the context of ISPs too; PEOU and PUOP of ISPs are postulated to impact behavioral intention to comply. Based on the model (SAM) a number of hypotheses are developed. Table 1 provides definitions of the SAM constructs in the model and their sources. Self-efficacy (SE) H3 Controllability (C) General Information Security (GIS) Security Policies (ISP) H5 H7 H4 H6 H8 H9 H10 Perceived usefulness of protection (PUOP) H1 Intention to Comply (IC) SETA program H11 H12 H13 Perceived ease of use (PEOU) H2 Computer Monitoring (CM) H14 Figure 1: Research Model - Security Acceptance Model (SAM) Proceedings of the Sixth Midwest Association for Information Systems Conference, Omaha, NE May 20-21,
4 Table 1: Definitions and Sources of Constructs Taken from the Theory of Planned Behavior, and TAM Construct Definition Source Intention to Comply An employee s intention to protect the information and technology resources of the organization from potential security breaches (Ajzen, 1991; Bulgurcu, et al., 2010) Information security State of the roles and responsibilities of the employees to safeguard the information and (Davis, 1989) Policy (ISP) technology resources of their organizations. PUOP The degree to which an employee believes that using ISPs roles and responsibilities to (Davis, 1989) safeguard the organization s information technology resources will enhance his/her job performance. PEOU The degree to which an employee believes that using ISPs in practice and undertaking (Bulgurcu, et al., 2010) related roles and responsibilities is relatively easy. Self-efficacy An employee s confidence in their ability, skills, and knowledge about satisfying the requirements of ISPs. (Ajzen, 1991; Pavlou & Fygenson, 2006) Controllability An individual judgment about the availability of resources and opportunities to perform the behavior. (Bulgurcu, et al., 2010; Goodhue & Straub, 1991) Information Security Awareness An employee s overall knowledge and understanding of potential issues related to information security and their ramifications. (D'Arcy, et al., 2009; Straub, 1990) SETA programs Passive security programs that are designed to deter misuse attempts by providing information regarding the proper use of information resources. (D'Arcy, et al., 2009; Urbaczewski & Jessup, 2002) Computer monitoring Is an active security control that increases organization s ability to detect different IS resources misuse. (D'Arcy, et al., 2009; Urbaczewski & Jessup, 2002) In accordance with TAM, it is assumed that an employee s intention to comply with the requirements of the organization s ISPs is associated with the degree to which the employee believes that using ISPs roles and responsibilities to safeguard the organization s information technology resources will enhance his/her job performance (PUOP). Also, it is associated with the degree to which an employee believes that using ISPs in practice and undertaking related roles and responsibilities is relatively easy (PEOU). The use of self-efficacy is consistent with the work of (Ajzen, 2002; Bulgurcu, et al., 2010; Fishbein & Cappella, 2006; Fishbein & Yzer, 2003). Controllability reflect the perceived ease of achieving an intended behavior (Ajzen, 1991), it is only, indirectly effect behavioral intention (Brown, Venkatesh, & Bala, 2006; Taylor & Todd, 1995). Employees are expected to be aware and knowledgeable of information security and cognizant of security technology and be able to formulate a general perception of what it entails. An individual s awareness and knowledge of information security is built from life experiences or from external resources such as the Internet, newspapers, security journals (Bulgurcu, et al., 2010; Goodhue & Straub, 1991). As employees become more aware of information security, the more they perceived that using ISPs in practice and undertaking related roles and responsibilities is relatively easy, and the more they believe that using ISPs roles and responsibilities to safeguard the organization s information technology resources will enhance his/her job performance. Monitoring according to (Urbaczewski & Jessup, 2002) has two basic uses: providing feedback and implementing control. Monitoring for feedback is to monitor employees for providing them with necessary feedback and suggestions for improvement, while monitoring for control is to monitor employees in order to gain compliance with rules and regulations (Urbaczewski & Jessup, 2002). This eventually will help employees perceive that using ISPs in practice and undertaking related roles and responsibilities is relatively easy. CONCLUSIONS AND FUTURE WORK We plan to conduct a survey study to investigate banks employees perceived controllability, self-efficacy, and awareness of general information security, security policies, SETA program, and computer monitoring toward complying with the bank s ISPs to test the proposed security acceptance research model. A random sample of banks employees in Jordan at different job levels and different departments will be taken. A sample of 10% of banks employees will be taken in order to have 500 participants as a final sample that will have at least five times as many observations as the number of variables to be analyzed. The information will be collected directly by distributing the questionnaire to the banks employees with help from a researchers colleague who will supervise data collection. Instruments for conducting the survey study are currently being designed. To ensure that the instrument is reliable and valid, the following procedures will be followed. To ensure content validity, in addition to drawing from published literature, the questionnaire will be given to a group of experts in the field, both in USA and Jordan, to verify that the content of the items are valid and measure what they are intended to measure. A pre-test will be conducted by distributing the questionnaire for a small group of employees, around 100; following up with a confirmatory factor analysis. Demographic information will be assessed in order to collect a sample that is very well matched demographically. Reliability test will also be conducted to measure the internal consistency for each construct. In this article, we have proposed a new research model that can help understand the compliance behavior of employees with respect to ISPs. The research model is unique in taking a user acceptance perspective at this research issue. The conceptual research model and hypotheses are presented, and future work has been outlined. Proceedings of the Sixth Midwest Association for Information Systems Conference, Omaha, NE May 20-21,
5 References Ajzen, I. (1991). The theory of planned behavior. Organizational behavior and human decision processes, 50(2), Ajzen, I. (2002). Perceived Behavioral Control, Self-Efficacy, Locus of Control, and the Theory of Planned Behavior1. Journal of Applied Social Psychology, 32(4), doi: /j tb00236.x Anderson, C. L., & Agarwal, R. (2010). Practicing Safe Computing Special Issue Practicing Safe Computing: A Multimethod Empirical Examination of Home Computer User Security Behavioral Intentions. MIS Quarterly, 34(3), Boss, S. R., Kirsch, L. J., Angermeier, I., Shingler, R. A., & Boss, R. W. (2009). If someone is watching, Ill do what Im asked: mandatoriness, control, and information security. European Journal of Information Systems, 18(2), Brown, S. A., Venkatesh, V., & Bala, H. (2006). Household technology use: integrating household life cycle and the model of adoption of technology in households. The Information Society, 22(4), Bulgurcu, B., Cavusoglu, H., & Benbasat, I. (2010). Information security policy compliance: an empirical study of rationality-based beliefs and information security awareness. MIS Quarterly, 34(3), D'Arcy, J., & Hovav, A. (2009). Does one size fit all? Examining the differential effects of IS security countermeasures. Journal of Business Ethics, 89(S1), D'Arcy, J., Hovav, A., & Galletta, D. (2009). User awareness of security countermeasures and its impact on information systems misuse: a deterrence approach. Information Systems Research, 20(1), Davis, F. D. (1986). A technology acceptance model for empirically testing new end-user information systems: theory and results. Massachusetts Institute of Technology, Cambridge, MA. (Ph.D. Dissertation) Davis, F. D. (1989). Perceived usefulness, perceived ease of use, and user acceptance of information technology. Mis Quarterly, 13(3), Davis, F. D., Bagozzi, R. P., & Warshaw, P. R. (1989). User acceptance of computer technology: a comparison of two theoretical models. Management science, 35(8), Dinev, T., & Hu, Q. (2007). The centrality of awareness in the formation of user behavioral intention toward protective information technologies. Journal of the Association for Information Systems, 8(7), 23. Fishbein, M., & Cappella, J. N. (2006). The Role of Theory in Developing Effective Health Communications. Journal of Communication, 56(S1), S1-S17. Fishbein, M., & Yzer, M. C. (2003). Using Theory to Design Effective Health Behavior Interventions. Communication Theory, 13(2), Goodhue, D. L., & Straub, D. W. (1991). Security concerns of system users : A study of perceptions of the adequacy of security. Information & Management, 20(1), Johnston, A. C., & Warkentin, M. (2010). Fear Appeals and Information Security Behaviors: An Empirical Study. Management Information Systems Quarterly, 34(3), Jones, C. (2009). Utilizing the technology acceptance model to assess employee adoption of information systems security measures. D.B.A. dissertation, Nova Southeastern University, United States -- Florida. Retrieved from Dissertations & Theses: Full Text.(Publication No. AAT ) Kankanhalli, A., Teo, H. H., Tan, B. C. Y., & Wei, K. K. (2003). An integrative study of information systems security effectiveness. International Journal of Information Management, 23(2), Pahnila, S., Siponen, M., & Mahmood, A. (2007, Jan. 2007). Employees' Behavior towards IS Security Policy Compliance. Paper presented at the 40th Annual Hawaii International Conference on System Sciences, HICSS Pavlou, P. A., & Fygenson, M. (2006). Understanding and predicting electronic commerce adoption: An extension of the theory of planned behavior. Management Information Systems Quarterly, 30(1), 8. Rhee, H.-S., Kim, C., & Ryu, Y. U. (2009). Self-efficacy in information security: Its influence on end users' information security practice behavior. Computers & Security, 28(8), Siponen, M., & Vance, A. O. (2010). Neutralization: New Insights into the Problem of Employee Systems Security Policy Violations. MIS Quarterly, 34(3), Straub, D. W. (1990). Effective IS security. Information Systems Research, 1(3), Taylor, S., & Todd, P. (1995). Decomposition and crossover effects in the theory of planned behavior: A study of consumer adoption intentions. International Journal of Research in Marketing, 12(2), Urbaczewski, A., & Jessup, L. M. (2002). Does electronic monitoring of employee internet usage work? Communications of the ACM, 45(1), Whitman, M. E., Townsend, A. M., & Aalberts, R. J. (2001). Information systems security and the need for policy. In G. Dhillon (Ed.), Information Security Management: Global Challenges in the New Millennium. Hershey, PA, USA: Idea Group Publishing. Workman, M., Bommer, W. H., & Straub, D. (2008). Security lapses and the omission of information security measures: A threat control model and empirical test. Computers in Human Behavior, 24(6), Proceedings of the Sixth Midwest Association for Information Systems Conference, Omaha, NE May 20-21,
Impact of Protection Motivation and Deterrence on IS Security Policy Compliance: A Multi- Cultural View
 Association for Information Systems AIS Electronic Library (AISeL) WISP 2012 Proceedings Pre-ICIS Workshop on Information Security and Privacy (SIGSEC) Winter 12-15-2012 Impact of Protection Motivation
Association for Information Systems AIS Electronic Library (AISeL) WISP 2012 Proceedings Pre-ICIS Workshop on Information Security and Privacy (SIGSEC) Winter 12-15-2012 Impact of Protection Motivation
Toward Developing a Theory of End User Information Security Competence
 Toward Developing a Theory of End User Information Security Competence Canchu Lin University of Toledo Canchu.lin@rockets.toledo.edu Anand S. Kunnathur University of Toledo anand.kunnathur@utoledo.edu
Toward Developing a Theory of End User Information Security Competence Canchu Lin University of Toledo Canchu.lin@rockets.toledo.edu Anand S. Kunnathur University of Toledo anand.kunnathur@utoledo.edu
Information Security Policies Compliance: The Role of
 Information Security Policies Compliance: The Role of Organizational Punishment Mohammad I. Merhi Department of Computer Information Systems & Quantitative Methods College of Business Administration University
Information Security Policies Compliance: The Role of Organizational Punishment Mohammad I. Merhi Department of Computer Information Systems & Quantitative Methods College of Business Administration University
A Theory of Employee Compliance with Information Security
 Association for Information Systems AIS Electronic Library (AISeL) MWAIS 2014 Proceedings Midwest (MWAIS) 5-15-2014 A Theory of Employee Compliance with Information Security David Sikolia dsikoli@ilstu.edu,
Association for Information Systems AIS Electronic Library (AISeL) MWAIS 2014 Proceedings Midwest (MWAIS) 5-15-2014 A Theory of Employee Compliance with Information Security David Sikolia dsikoli@ilstu.edu,
Motivating Employees to Comply with Information Security Policies
 Association for Information Systems AIS Electronic Library (AISeL) MWAIS 2016 Proceedings Midwest (MWAIS) Spring 5-19-2016 Motivating Employees to Comply with Information Security Policies David Sikolia
Association for Information Systems AIS Electronic Library (AISeL) MWAIS 2016 Proceedings Midwest (MWAIS) Spring 5-19-2016 Motivating Employees to Comply with Information Security Policies David Sikolia
Investigating Online Consumer Behavior in Iran Based on the Theory of Planned Behavior
 Modern Applied Science; Vol. 10, No. 4; 2016 ISSN 1913-1844 E-ISSN 1913-1852 Published by Canadian Center of Science and Education Investigating Online Consumer Behavior in Iran Based on the Theory of
Modern Applied Science; Vol. 10, No. 4; 2016 ISSN 1913-1844 E-ISSN 1913-1852 Published by Canadian Center of Science and Education Investigating Online Consumer Behavior in Iran Based on the Theory of
Knowledge Management System Adoption and Practice in Taiwan Life Insurance Industry: Analysis via Partial Least Squares
 Association for Information Systems AIS Electronic Library (AISeL) PACIS 2007 Proceedings Pacific Asia Conference on Information Systems (PACIS) 2007 Knowledge Management System Adoption and Practice in
Association for Information Systems AIS Electronic Library (AISeL) PACIS 2007 Proceedings Pacific Asia Conference on Information Systems (PACIS) 2007 Knowledge Management System Adoption and Practice in
The Influence of Individual-level Cultural Orientation on ERP System Adoption
 Association for Information Systems AIS Electronic Library (AISeL) AMCIS 2004 Proceedings Americas Conference on Information Systems (AMCIS) December 2004 The Influence of Individual-level Cultural Orientation
Association for Information Systems AIS Electronic Library (AISeL) AMCIS 2004 Proceedings Americas Conference on Information Systems (AMCIS) December 2004 The Influence of Individual-level Cultural Orientation
Internalization of Information Security Policy and Information Security Practice: A Comparison with Compliance
 Proceedings of the 51 st Hawaii International Conference on System Sciences 2018 Internalization of Information Security Policy and Information Security Practice: A Comparison with Compliance Minjung Park
Proceedings of the 51 st Hawaii International Conference on System Sciences 2018 Internalization of Information Security Policy and Information Security Practice: A Comparison with Compliance Minjung Park
User Acceptance of E-Government Services
 Association for Information Systems AIS Electronic Library (AISeL) PACIS 2007 Proceedings Pacific Asia Conference on Information Systems (PACIS) 2007 User Acceptance of E-Government Services Ying-Hsun
Association for Information Systems AIS Electronic Library (AISeL) PACIS 2007 Proceedings Pacific Asia Conference on Information Systems (PACIS) 2007 User Acceptance of E-Government Services Ying-Hsun
USER ACCEPTANCE OF E-COMMERCE TECHNOLOGY: A META-ANALYTIC COMPARISON OF COMPETING MODELS
 USER ACCEPTANCE OF E-COMMERCE TECHNOLOGY: A META-ANALYTIC COMPARISON OF COMPETING MODELS Yayla, Ali, Florida Atlantic University, 777 Glades Road, Boca Raton, FL 33431, USA, ayayla@fau.edu Hu, Qing, Florida
USER ACCEPTANCE OF E-COMMERCE TECHNOLOGY: A META-ANALYTIC COMPARISON OF COMPETING MODELS Yayla, Ali, Florida Atlantic University, 777 Glades Road, Boca Raton, FL 33431, USA, ayayla@fau.edu Hu, Qing, Florida
User acceptance of e-commerce technology: a meta-analytic comparison of competing models
 Iowa State University From the SelectedWorks of Qing Hu June, 2007 User acceptance of e-commerce technology: a meta-analytic comparison of competing models Ali Yayla, Florida Atlantic University Qing Hu,
Iowa State University From the SelectedWorks of Qing Hu June, 2007 User acceptance of e-commerce technology: a meta-analytic comparison of competing models Ali Yayla, Florida Atlantic University Qing Hu,
Online Purchase Intention in B2C E-Commerce: An Empirical Study
 Association for Information Systems AIS Electronic Library (AISeL) WHICEB 2013 Proceedings Wuhan International Conference on e-business Summer 5-25-2013 Online Purchase Intention in B2C E-Commerce: An
Association for Information Systems AIS Electronic Library (AISeL) WHICEB 2013 Proceedings Wuhan International Conference on e-business Summer 5-25-2013 Online Purchase Intention in B2C E-Commerce: An
Value-Focused Assessment of Information System Security in Organizations
 Association for Information Systems AIS Electronic Library (AISeL) ICIS 2001 Proceedings International Conference on Information Systems (ICIS) 12-31-2001 Value-Focused Assessment of Information System
Association for Information Systems AIS Electronic Library (AISeL) ICIS 2001 Proceedings International Conference on Information Systems (ICIS) 12-31-2001 Value-Focused Assessment of Information System
Evaluating Supply Chain Context-Specific Antecedents of Post-Adoption Technology Performance
 Association for Information Systems AIS Electronic Library (AISeL) SIGHCI 2005 Proceedings Special Interest Group on Human-Computer Interaction 2005 Evaluating Supply Chain Context-Specific Antecedents
Association for Information Systems AIS Electronic Library (AISeL) SIGHCI 2005 Proceedings Special Interest Group on Human-Computer Interaction 2005 Evaluating Supply Chain Context-Specific Antecedents
Assessing Student Perceptions and Current Adoption of E-Textbooks
 Association for Information Systems AIS Electronic Library (AISeL) MWAIS 2015 Proceedings Midwest (MWAIS) Spring 5-14-2015 Assessing Student Perceptions and Current Adoption of E-Textbooks Halbana Tarmizi
Association for Information Systems AIS Electronic Library (AISeL) MWAIS 2015 Proceedings Midwest (MWAIS) Spring 5-14-2015 Assessing Student Perceptions and Current Adoption of E-Textbooks Halbana Tarmizi
The Empirical Investigation of a Wiki based group system in organizations.
 Association for Information Systems AIS Electronic Library (AISeL) AMCIS 2010 Proceedings Americas Conference on Information Systems (AMCIS) 8-2010 The Empirical Investigation of a Wiki based group system
Association for Information Systems AIS Electronic Library (AISeL) AMCIS 2010 Proceedings Americas Conference on Information Systems (AMCIS) 8-2010 The Empirical Investigation of a Wiki based group system
Investigating Continuous Security Compliance Behavior: Insights from Information Systems Continuance Model
 Investigating Continuous Security Compliance Behavior: Insights from Information Systems Continuance Model Full Paper Javad Abed Gurpreet Dhillon Virginia Commonwealth University Virginia Commonwealth
Investigating Continuous Security Compliance Behavior: Insights from Information Systems Continuance Model Full Paper Javad Abed Gurpreet Dhillon Virginia Commonwealth University Virginia Commonwealth
 PROJECT Introduction Over the recent years, government use of the Internet as a platform to provide services to citizens has grown significantly. One of the major priorities already identified by
PROJECT Introduction Over the recent years, government use of the Internet as a platform to provide services to citizens has grown significantly. One of the major priorities already identified by
Management Science Letters
 Management Science Letters 3 (2013) 1307 1314 Contents lists available at GrowingScience Management Science Letters homepage: www.growingscience.com/msl An empirical study on different factors influencing
Management Science Letters 3 (2013) 1307 1314 Contents lists available at GrowingScience Management Science Letters homepage: www.growingscience.com/msl An empirical study on different factors influencing
Top Management Can Lower Resistance toward Information Security Compliance
 Top Management Can Lower Resistance toward Information Security Compliance Research-in-Progress Mohammad I. Merhi Judd Leighton School of Business & Economics Indiana University South Bend 1700 Mishawaka
Top Management Can Lower Resistance toward Information Security Compliance Research-in-Progress Mohammad I. Merhi Judd Leighton School of Business & Economics Indiana University South Bend 1700 Mishawaka
Quality of Usage as a Neglected Aspect of Information Technology Acceptance
 Quality of Usage as a Neglected Aspect of Information Technology Acceptance Birte Autzen Department of General Management and Information Systems Prof. Dr. Armin Heinzl University of Mannheim 68131 Mannheim
Quality of Usage as a Neglected Aspect of Information Technology Acceptance Birte Autzen Department of General Management and Information Systems Prof. Dr. Armin Heinzl University of Mannheim 68131 Mannheim
International Academic Institute for Science and Technology. Management. Vol. 3, No. 12, 2016, pp ISSN
 International Academic Institute for Science and Technology International Academic Journal of Accounting and Financial Management Vol. 3, No. 12, 2016, pp. 30-37. ISSN 2454-2350 International Academic
International Academic Institute for Science and Technology International Academic Journal of Accounting and Financial Management Vol. 3, No. 12, 2016, pp. 30-37. ISSN 2454-2350 International Academic
Toward Modeling the Effects of Cultural Dimension on ICT Acceptance in Indonesia
 Available online at www.sciencedirect.com Procedia - Social and Behavioral Sciences 65 ( 2012 ) 833 838 International Congress on Interdisciplinary Business and Social Science 2012 (ICIBSoS 2012) Toward
Available online at www.sciencedirect.com Procedia - Social and Behavioral Sciences 65 ( 2012 ) 833 838 International Congress on Interdisciplinary Business and Social Science 2012 (ICIBSoS 2012) Toward
Knowledge of Security Protocols and Acceptance of E-commerce
 Knowledge of Security Protocols and Acceptance of E-commerce Sumendra Singh, Faculty of Business and IT, Webster University, Thailand. E-mail: singh89sumendra@gmail.com Leslie Klieb, Faculty of Business
Knowledge of Security Protocols and Acceptance of E-commerce Sumendra Singh, Faculty of Business and IT, Webster University, Thailand. E-mail: singh89sumendra@gmail.com Leslie Klieb, Faculty of Business
AIS Contribution in Navigation Operation- Using AIS User Satisfaction Model
 International Journal on Marine Navigation and Safety of Sea Transportation Volume 1 Number 3 September 2007 AIS Contribution in Navigation Operation- Using AIS User Satisfaction Model A. Harati-Mokhtari
International Journal on Marine Navigation and Safety of Sea Transportation Volume 1 Number 3 September 2007 AIS Contribution in Navigation Operation- Using AIS User Satisfaction Model A. Harati-Mokhtari
Integrating Trust in Electronic Commerce with the Technology Acceptance Model: Model Development and Validation
 Association for Information Systems AIS Electronic Library (AISeL) AMCIS 2001 Proceedings Americas Conference on Information Systems (AMCIS) December 2001 Integrating Trust in Electronic Commerce with
Association for Information Systems AIS Electronic Library (AISeL) AMCIS 2001 Proceedings Americas Conference on Information Systems (AMCIS) December 2001 Integrating Trust in Electronic Commerce with
Discussion of Technostress Impact on Employees Information Security Behaviour
 Discussion of Technostress Impact on Employees Information Security Behaviour Masterarbeit zur Erlangung des akademischen Grades Master of Science (M.Sc.) im Masterstudiengang Wirtschaftswissenschaft der
Discussion of Technostress Impact on Employees Information Security Behaviour Masterarbeit zur Erlangung des akademischen Grades Master of Science (M.Sc.) im Masterstudiengang Wirtschaftswissenschaft der
Is the Technology Acceptance Model a Valid Model of User Satisfaction of Information Technology in Environments where Usage is Mandatory?
 Association for Information Systems AIS Electronic Library (AISeL) ACIS 2002 Proceedings Australasian (ACIS) December 2002 Is the Technology Acceptance Model a Valid Model of User Satisfaction of Information
Association for Information Systems AIS Electronic Library (AISeL) ACIS 2002 Proceedings Australasian (ACIS) December 2002 Is the Technology Acceptance Model a Valid Model of User Satisfaction of Information
TPB (Ajzen, 1991), TAM (Davis et al., 1989) Topic: E-filing
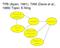 TPB (Ajzen, 1991), TAM (Davis et al., 1989) Topic: E-filing Perceived usefulness Attitude Intention Ease of use Perceived behavioral control Subjective norm Introduction Over the recent years, government
TPB (Ajzen, 1991), TAM (Davis et al., 1989) Topic: E-filing Perceived usefulness Attitude Intention Ease of use Perceived behavioral control Subjective norm Introduction Over the recent years, government
Toward An Understanding of the Behavioral Intention to Use Mobile Banking Services
 Association for Information Systems AIS Electronic Library (AISeL) PACIS 2004 Proceedings Pacific Asia Conference on Information Systems (PACIS) December 2004 Toward An Understanding of the Behavioral
Association for Information Systems AIS Electronic Library (AISeL) PACIS 2004 Proceedings Pacific Asia Conference on Information Systems (PACIS) December 2004 Toward An Understanding of the Behavioral
Technology Acceptance Analysis of Local Government Tourism Website
 African Journal of Business Management Vol. 6(49), pp. 11891-11895, 12 December, 2012 Available online at http://www.academicjournals.org/ajbm DOI: 10.5897/AJBM10.1590 ISSN 1993-8233 2012 Academic Journals
African Journal of Business Management Vol. 6(49), pp. 11891-11895, 12 December, 2012 Available online at http://www.academicjournals.org/ajbm DOI: 10.5897/AJBM10.1590 ISSN 1993-8233 2012 Academic Journals
Investigating Social Influence on Acceptance of Executive Information Systems: A UTAUT Framework Approach
 Association for Information Systems AIS Electronic Library (AISeL) SAIS 2007 Proceedings Southern (SAIS) 3-1-2007 Investigating Social Influence on Acceptance of Executive Information Systems: A UTAUT
Association for Information Systems AIS Electronic Library (AISeL) SAIS 2007 Proceedings Southern (SAIS) 3-1-2007 Investigating Social Influence on Acceptance of Executive Information Systems: A UTAUT
The Effect of Accounting Information Systems in Accounting
 The Effect of Accounting Information Systems in Accounting Awosejo, O.J 1, Kekwaletswe, R, M 2, Pretorius, P 3 and Zuva, T 4 Abstracts Generally, ICT have improved the quality of professional services
The Effect of Accounting Information Systems in Accounting Awosejo, O.J 1, Kekwaletswe, R, M 2, Pretorius, P 3 and Zuva, T 4 Abstracts Generally, ICT have improved the quality of professional services
Motivating Employees to Comply with Information Security policies
 Journal of the Midwest Association for Information Systems ( JMWAIS) Volume 2016 Issue 2 Article 2 2016 Motivating Employees to Comply with Information Security policies David Sikolia dsikoli@ilstu.edu,
Journal of the Midwest Association for Information Systems ( JMWAIS) Volume 2016 Issue 2 Article 2 2016 Motivating Employees to Comply with Information Security policies David Sikolia dsikoli@ilstu.edu,
By Samala Nagaraj & Dr. Sapna Singh
 Global Journal of Management and Business Research: E Marketing Volume 17 Issue 2 Version 1.0 Year 2017 Type: Double Blind Peer Reviewed International Research Journal Publisher: Global Journals Inc. (USA)
Global Journal of Management and Business Research: E Marketing Volume 17 Issue 2 Version 1.0 Year 2017 Type: Double Blind Peer Reviewed International Research Journal Publisher: Global Journals Inc. (USA)
Empirical evaluation of the revised end user computing acceptance model
 Computers in Human Behavior Computers in Human Behavior 23 (2007) 162 174 www.elsevier.com/locate/comphumbeh Empirical evaluation of the revised end user computing acceptance model Jen-Her Wu a,b, *, Yung-Cheng
Computers in Human Behavior Computers in Human Behavior 23 (2007) 162 174 www.elsevier.com/locate/comphumbeh Empirical evaluation of the revised end user computing acceptance model Jen-Her Wu a,b, *, Yung-Cheng
An Integrative Model of Clients' Decision to Adopt an Application Service Provider
 Association for Information Systems AIS Electronic Library (AISeL) AMCIS 2003 Proceedings Americas Conference on Information Systems (AMCIS) December 2003 An Integrative Model of Clients' Decision to Adopt
Association for Information Systems AIS Electronic Library (AISeL) AMCIS 2003 Proceedings Americas Conference on Information Systems (AMCIS) December 2003 An Integrative Model of Clients' Decision to Adopt
The Technology Acceptance Model for Competitive Software Products
 The Technology Acceptance Model for Competitive Software Products Hock Chuan CHAN Department of Information Systems National University of Singapore chanhc@comp.nus.edu.sg Jing YANG Department of Information
The Technology Acceptance Model for Competitive Software Products Hock Chuan CHAN Department of Information Systems National University of Singapore chanhc@comp.nus.edu.sg Jing YANG Department of Information
CONTROLLING INSIDER THREATS WITH INFORMATION SECURITY POLICIES
 Association for Information Systems AIS Electronic Library (AISeL) ECIS 2011 Proceedings European Conference on Information Systems (ECIS) Summer 10-6-2011 CONTROLLING INSIDER THREATS WITH INFORMATION
Association for Information Systems AIS Electronic Library (AISeL) ECIS 2011 Proceedings European Conference on Information Systems (ECIS) Summer 10-6-2011 CONTROLLING INSIDER THREATS WITH INFORMATION
Journal of Internet Banking and Commerce
 Journal of Internet Banking and Commerce An open access Internet journal (http://www.arraydev.com/commerce/jibc/) Journal of Internet Banking and Commerce, August 2010, vol. 15, no.2 (http://www.arraydev.com/commerce/jibc/)
Journal of Internet Banking and Commerce An open access Internet journal (http://www.arraydev.com/commerce/jibc/) Journal of Internet Banking and Commerce, August 2010, vol. 15, no.2 (http://www.arraydev.com/commerce/jibc/)
Adoption of Information Security as Decisionmaking under Uncertainty: A Behavioural Economics Approach
 Association for Information Systems AIS Electronic Library (AISeL) ECIS 2015 Research-in-Progress Papers ECIS 2015 Proceedings Spring 5-29-2015 Adoption of Information Security as Decisionmaking under
Association for Information Systems AIS Electronic Library (AISeL) ECIS 2015 Research-in-Progress Papers ECIS 2015 Proceedings Spring 5-29-2015 Adoption of Information Security as Decisionmaking under
Consumer Behavior towards Continued Use of Online Shopping: An Extend Expectation Disconfirmation Model
 Consumer Behavior towards Continued Use of Online Shopping: An Extend Expectation Disconfirmation Model Min Qin School of Communication, Jiangxi Normal University, P.R. China, 330022 helenqin126@163.com
Consumer Behavior towards Continued Use of Online Shopping: An Extend Expectation Disconfirmation Model Min Qin School of Communication, Jiangxi Normal University, P.R. China, 330022 helenqin126@163.com
A Methodological Analysis of User Technology Acceptance
 A Methodological Analysis of User nology Acceptance Heshan Sun School of Information Studies Syracuse University hesun@syr.edu Abstract The majority of research on user technology acceptance, e.g. technology
A Methodological Analysis of User nology Acceptance Heshan Sun School of Information Studies Syracuse University hesun@syr.edu Abstract The majority of research on user technology acceptance, e.g. technology
Exploring Technological Factors Affecting the Adoption of M-Commerce in Jordan
 Australian Journal of Basic and Applied Sciences, 7(6): 395-400, 2013 ISSN 1991-8178 Exploring Technological Factors Affecting the Adoption of M-Commerce in Jordan 1 Feras Fares Al Mashagba, 2 Eman Fares
Australian Journal of Basic and Applied Sciences, 7(6): 395-400, 2013 ISSN 1991-8178 Exploring Technological Factors Affecting the Adoption of M-Commerce in Jordan 1 Feras Fares Al Mashagba, 2 Eman Fares
Research on the Willingness to Accept Mobile Internet Advertising Based on Customer Perception---A Case of College Students
 Association for Information Systems AIS Electronic Library (AISeL) WHICEB 2017 Proceedings Wuhan International Conference on e-business Summer 5-26-2017 Research on the Willingness to Accept Mobile Internet
Association for Information Systems AIS Electronic Library (AISeL) WHICEB 2017 Proceedings Wuhan International Conference on e-business Summer 5-26-2017 Research on the Willingness to Accept Mobile Internet
AN EXPLORATION OF GROUP INFORMATION SECURITY COMPLIANCE: A SOCIAL NETWORK ANALYSIS PERSPECTIVE
 AN EXPLORATION OF GROUP INFORMATION SECURITY COMPLIANCE: A SOCIAL NETWORK ANALYSIS PERSPECTIVE Research-in-Progress Chul Woo Yoo University at Buffalo Buffalo, NY, USA chulwooy@buffalo.edu G. Lawrence
AN EXPLORATION OF GROUP INFORMATION SECURITY COMPLIANCE: A SOCIAL NETWORK ANALYSIS PERSPECTIVE Research-in-Progress Chul Woo Yoo University at Buffalo Buffalo, NY, USA chulwooy@buffalo.edu G. Lawrence
Which are the Most Effective Measures for Improving Employees Security Compliance?
 Which are the Most Effective Measures for Improving Employees Security Compliance? Completed Research Paper Martin Kretzer University of Mannheim Mannheim, Germany kretzer@es.uni-mannheim.de Alexander
Which are the Most Effective Measures for Improving Employees Security Compliance? Completed Research Paper Martin Kretzer University of Mannheim Mannheim, Germany kretzer@es.uni-mannheim.de Alexander
A Study of Behavioral Intention for 3G Mobile Internet Technology: Preliminary Research on Mobile Learning
 A Study of Behavioral Intention for 3G Mobile Internet Technology: Dulyalak Phuangthong and Settapong Malisawan, Ph.D. College of Management Mahidol University, Thailand dulyalak@hotmail.com settapong.m@cmmu.net
A Study of Behavioral Intention for 3G Mobile Internet Technology: Dulyalak Phuangthong and Settapong Malisawan, Ph.D. College of Management Mahidol University, Thailand dulyalak@hotmail.com settapong.m@cmmu.net
Factors Affecting the Intention to Use e-marketing: A case Study among Students in Jordan
 Vol. 7, No.1, January 2017, pp. 322 328 E-ISSN: 2225-8329, P-ISSN: 2308-0337 2017 HRMARS www.hrmars.com Factors Affecting the Intention to Use e-marketing: A case Study among Students in Jordan Farah Hanna
Vol. 7, No.1, January 2017, pp. 322 328 E-ISSN: 2225-8329, P-ISSN: 2308-0337 2017 HRMARS www.hrmars.com Factors Affecting the Intention to Use e-marketing: A case Study among Students in Jordan Farah Hanna
(Full Paper Submission) Yan Chen Auburn University at Montgomery
 DECISION SCIENCES INSTITUTE Influence of Security Concerns, Privacy Concerns, and Exchange Benefits on Mobile Commerce Adoption: A Social Exchange Perspective (Full Paper Submission) Yan Chen Auburn University
DECISION SCIENCES INSTITUTE Influence of Security Concerns, Privacy Concerns, and Exchange Benefits on Mobile Commerce Adoption: A Social Exchange Perspective (Full Paper Submission) Yan Chen Auburn University
Incorporating Perceived Risk Into The Diffusion Of Innovation Theory For The Internet And Related Innovations
 Incorporating Perceived Risk Into The Diffusion Of Innovation Theory For The Internet And Related Innovations Zakaria I. Saleh. Yarmouk University, Jordan DrZaatreh@netscape.net ABSTRACTS Despite the high
Incorporating Perceived Risk Into The Diffusion Of Innovation Theory For The Internet And Related Innovations Zakaria I. Saleh. Yarmouk University, Jordan DrZaatreh@netscape.net ABSTRACTS Despite the high
Applying Technology Acceptance Model, Theory of Planned Behavior and Social Cognitive Theory to Mobile Data Communications Service Acceptance
 Association for Information Systems AIS Electronic Library (AISeL) PACIS 2004 Proceedings Pacific Asia Conference on Information Systems (PACIS) 12-31-2004 Applying Technology Acceptance Model, Theory
Association for Information Systems AIS Electronic Library (AISeL) PACIS 2004 Proceedings Pacific Asia Conference on Information Systems (PACIS) 12-31-2004 Applying Technology Acceptance Model, Theory
Factors Influencing Electronic Government Adoption: Perspectives Of Less Frequent Internet Users Of Pakistan
 Factors Influencing Electronic Government Adoption: Perspectives Of Less Frequent Internet Users Of Pakistan Farooq Alam Khan, Basheer Ahmad Abstract: Much literature on electronic government services
Factors Influencing Electronic Government Adoption: Perspectives Of Less Frequent Internet Users Of Pakistan Farooq Alam Khan, Basheer Ahmad Abstract: Much literature on electronic government services
Cultural Dimensions as Moderators of the UTAUT Model: a Research Proposal in a Healthcare Context
 Association for Information Systems AIS Electronic Library (AISeL) AMCIS 2010 Proceedings Americas Conference on Information Systems (AMCIS) 8-2010 Cultural Dimensions as Moderators of the UTAUT Model:
Association for Information Systems AIS Electronic Library (AISeL) AMCIS 2010 Proceedings Americas Conference on Information Systems (AMCIS) 8-2010 Cultural Dimensions as Moderators of the UTAUT Model:
ANTECEDENTS OF EMPLOYEES' INFORMATION SECURITY AWARENESS - REVIEW, SYNTHESIS, AND DIRECTIONS FOR FUTURE RESEARCH
 Association for Information Systems AIS Electronic Library (AISeL) Research Papers ECIS 2017 Proceedings Spring 6-10-2017 ANTECEDENTS OF EMPLOYEES' INFORMATION SECURITY AWARENESS - REVIEW, SYNTHESIS, AND
Association for Information Systems AIS Electronic Library (AISeL) Research Papers ECIS 2017 Proceedings Spring 6-10-2017 ANTECEDENTS OF EMPLOYEES' INFORMATION SECURITY AWARENESS - REVIEW, SYNTHESIS, AND
Information System Security Commitment: A Study of External Influences on Senior Management
 Nova Southeastern University NSUWorks CEC Theses and Dissertations College of Engineering and Computing 2014 Information System Security Commitment: A Study of External Influences on Senior Management
Nova Southeastern University NSUWorks CEC Theses and Dissertations College of Engineering and Computing 2014 Information System Security Commitment: A Study of External Influences on Senior Management
EURASIAN JOURNAL OF SOCIAL SCIENCES
 Eurasian Journal of Social Sciences, 1(2), 2013, 46-51 EURASIAN JOURNAL OF SOCIAL SCIENCES http://www.econjournals.net PERSONALITY TRAITS AS FACTORS AFFECTING E-BOOK ADOPTION AMONG COLLEGE STUDENTS: DOES
Eurasian Journal of Social Sciences, 1(2), 2013, 46-51 EURASIAN JOURNAL OF SOCIAL SCIENCES http://www.econjournals.net PERSONALITY TRAITS AS FACTORS AFFECTING E-BOOK ADOPTION AMONG COLLEGE STUDENTS: DOES
M-COMMERCE ADOPTION AND PERFORMANCE IMPROVEMENT: PROPOSING A CONCEPTUAL FRAMEWORK
 International Journal of Economics, Commerce and Management United Kingdom Vol. III, Issue 4, April 2015 http://ijecm.co.uk/ ISSN 2348 0386 M-COMMERCE ADOPTION AND PERFORMANCE IMPROVEMENT: PROPOSING A
International Journal of Economics, Commerce and Management United Kingdom Vol. III, Issue 4, April 2015 http://ijecm.co.uk/ ISSN 2348 0386 M-COMMERCE ADOPTION AND PERFORMANCE IMPROVEMENT: PROPOSING A
Ruth C. King Michele L. Gribbins
 Adoption of Organizational Internet Technology: Can Current Technology Adoption Models Explain Web Adoption Strategies in Small & Mid-Sized Organizations? Ruth C. King ruthking@uiuc.edu 217-390-3617 Michele
Adoption of Organizational Internet Technology: Can Current Technology Adoption Models Explain Web Adoption Strategies in Small & Mid-Sized Organizations? Ruth C. King ruthking@uiuc.edu 217-390-3617 Michele
The Role of Individual Characteristics on Insider Abuse Intentions
 Association for Information Systems AIS Electronic Library (AISeL) AMCIS 2012 Proceedings Proceedings The Role of Individual Characteristics on Insider Abuse Intentions Merrill Warkentin Mgmt & Information
Association for Information Systems AIS Electronic Library (AISeL) AMCIS 2012 Proceedings Proceedings The Role of Individual Characteristics on Insider Abuse Intentions Merrill Warkentin Mgmt & Information
A MULTI-THEORETICAL STUDY ON SOCIAL NETWORKING TOURISM
 Association for Information Systems AIS Electronic Library (AISeL) PACIS 2014 Proceedings Pacific Asia Conference on Information Systems (PACIS) 2014 A MULTI-THEORETICAL STUDY ON SOCIAL NETWORKING TOURISM
Association for Information Systems AIS Electronic Library (AISeL) PACIS 2014 Proceedings Pacific Asia Conference on Information Systems (PACIS) 2014 A MULTI-THEORETICAL STUDY ON SOCIAL NETWORKING TOURISM
The Effect of the Consumers Innovativeness and Self-efficacy on Diffusion of Innovative Technology
 , pp.234-238 http://dx.doi.org/10.14257/astl.2016.129.46 The Effect of the Consumers Innovativeness and Self-efficacy on Diffusion of Innovative Technology Hye-young Oh 1 1 Dept. of Computer Information
, pp.234-238 http://dx.doi.org/10.14257/astl.2016.129.46 The Effect of the Consumers Innovativeness and Self-efficacy on Diffusion of Innovative Technology Hye-young Oh 1 1 Dept. of Computer Information
TAM Derived Construct of Perceived Customer Value and Online Purchase Behavior: An Empirical Exploration
 TAM Derived Construct of Perceived Customer Value and Online Purchase Kok-Wai Chew, P.M Shingi, Mohd. Ismail Ahmad Faculty of Management, Multimedia University, Jalan Multimedia, 63100 Cyberjaya, Selangor,
TAM Derived Construct of Perceived Customer Value and Online Purchase Kok-Wai Chew, P.M Shingi, Mohd. Ismail Ahmad Faculty of Management, Multimedia University, Jalan Multimedia, 63100 Cyberjaya, Selangor,
Social Media Malware: Determinants of Users Intention to Share Potentially Infected Posts
 Social Media Malware: Determinants of Users Intention to Share Potentially Infected Posts Emergent Research Forum Paper Sonia Camacho Universidad de los Andes so-camac@uniandes.edu.co Abstract Malware
Social Media Malware: Determinants of Users Intention to Share Potentially Infected Posts Emergent Research Forum Paper Sonia Camacho Universidad de los Andes so-camac@uniandes.edu.co Abstract Malware
UNDERSTANDING AND PREDICTING ELECTRONIC COMMERCE ADOPTION: AN EXTENSION OF
 RESEARCH ARTICLE UNDERSTANDING AND PREDICTING ELECTRONIC COMMERCE ADOPTION: AN EXTENSION OF THE THEORY OF PLANNED BEHAVIOR 1 By: Paul A. Pavlou Anderson Graduate School of Management University of California,
RESEARCH ARTICLE UNDERSTANDING AND PREDICTING ELECTRONIC COMMERCE ADOPTION: AN EXTENSION OF THE THEORY OF PLANNED BEHAVIOR 1 By: Paul A. Pavlou Anderson Graduate School of Management University of California,
Information Search Patterns on Product Comparison Services in ecommerce Websites
 Association for Information Systems AIS Electronic Library (AISeL) AMCIS 2005 Proceedings Americas Conference on Information Systems (AMCIS) 2005 Information Search Patterns on Product Comparison Services
Association for Information Systems AIS Electronic Library (AISeL) AMCIS 2005 Proceedings Americas Conference on Information Systems (AMCIS) 2005 Information Search Patterns on Product Comparison Services
Factors Influencing Employees Deep Usage of Information Systems
 Factors Influencing Employees Deep Usage of Information Systems Wei Wang Department of Management and Marketing The Hong Kong Polytechnic University, Hong Kong, China wang.wei@polyu.edu.hk Abstract The
Factors Influencing Employees Deep Usage of Information Systems Wei Wang Department of Management and Marketing The Hong Kong Polytechnic University, Hong Kong, China wang.wei@polyu.edu.hk Abstract The
The Effects of Experience, Complexity, and Computer Self Efficacy Factors towards The Use of Human Resources Information System Application
 Quest Journals Journal of Research in Business and Management Volume 2 ~ Issue 11 (2014) pp: 26-33 ISSN(Online) : 2347-3002 www.questjournals.org Research Paper The Effects of Experience, Complexity, and
Quest Journals Journal of Research in Business and Management Volume 2 ~ Issue 11 (2014) pp: 26-33 ISSN(Online) : 2347-3002 www.questjournals.org Research Paper The Effects of Experience, Complexity, and
Increasing Knowledge Seeking Initiation based on Theories of Human Behaviour
 Increasing Knowledge Seeking Initiation based on Theories of Human Behaviour CARRO SAAVEDRA Cristina * ; OCON GALILEA Alicia and LINDEMANN Udo Chair of Product Development, Technical University of Munich
Increasing Knowledge Seeking Initiation based on Theories of Human Behaviour CARRO SAAVEDRA Cristina * ; OCON GALILEA Alicia and LINDEMANN Udo Chair of Product Development, Technical University of Munich
FROM ACCEPTANCE TO OUTCOME: TOWARDS AN INTEGRATIVE FRAMEWORK FOR INFORMATION TECHNOLOGY ADOPTION
 Association for Information Systems AIS Electronic Library (AISeL) ECIS 2014 Proceedings FROM ACCEPTANCE TO OUTCOME: TOWARDS AN INTEGRATIVE FRAMEWORK FOR INFORMATION TECHNOLOGY ADOPTION Christian Sorgenfrei
Association for Information Systems AIS Electronic Library (AISeL) ECIS 2014 Proceedings FROM ACCEPTANCE TO OUTCOME: TOWARDS AN INTEGRATIVE FRAMEWORK FOR INFORMATION TECHNOLOGY ADOPTION Christian Sorgenfrei
INFLUENCE FACTORS ON INTENTION TO USE MOBILE BANKING
 INFLUENCE FACTORS ON INTENTION TO USE MOBILE BANKING 1 KYUNGTAG LEE, 2 JEONGWOO KIM, 3 MIJIN NOH 1,2 Yeungnam University, 3 Kyungpook National University E-mail: 1 mykr21@gmail.com, 3 yomydragon@naver.com,
INFLUENCE FACTORS ON INTENTION TO USE MOBILE BANKING 1 KYUNGTAG LEE, 2 JEONGWOO KIM, 3 MIJIN NOH 1,2 Yeungnam University, 3 Kyungpook National University E-mail: 1 mykr21@gmail.com, 3 yomydragon@naver.com,
IT Knowledge and Skills Required in Business An Investigation of Different Business Professions
 Association for Information Systems AIS Electronic Library (AISeL) MWAIS 2010 Proceedings Midwest (MWAIS) 5-2010 An Investigation of Different Business Professions Jun He University of Michigan - Dearborn,
Association for Information Systems AIS Electronic Library (AISeL) MWAIS 2010 Proceedings Midwest (MWAIS) 5-2010 An Investigation of Different Business Professions Jun He University of Michigan - Dearborn,
Why People Buy Virtual Items in Virtual Worlds with Real Money
 Why People Buy Virtual Items in Virtual Worlds with Real Money Yue Guo University of East Anglia Stuart Barnes University of East Anglia Abstract Virtual worlds, such as Second Life and Everquest, have
Why People Buy Virtual Items in Virtual Worlds with Real Money Yue Guo University of East Anglia Stuart Barnes University of East Anglia Abstract Virtual worlds, such as Second Life and Everquest, have
EXPLORING THE NEGATIVE SIDE OF SOCIAL NETWORKING SITES: THE ROLE OF PRIVACY RISK AND TRUSTWORTHINESS
 EXPLORING THE NEGATIVE SIDE OF SOCIAL NETWORKING SITES: THE ROLE OF PRIVACY RISK AND TRUSTWORTHINESS 1 DAUW-SONG ZHU, 2 ZUI CHIH LEE, 3 CHEN-WEN CHUNG 1,3 Department of Business Administration, National
EXPLORING THE NEGATIVE SIDE OF SOCIAL NETWORKING SITES: THE ROLE OF PRIVACY RISK AND TRUSTWORTHINESS 1 DAUW-SONG ZHU, 2 ZUI CHIH LEE, 3 CHEN-WEN CHUNG 1,3 Department of Business Administration, National
Internet Banking: Enablers and Inhibitors for Developing Economies A Study of Potential Users in Jamaica Completed Research Paper
 Internet Banking: Enablers and Inhibitors for Developing Economies A Study of Potential Users in Jamaica Completed Research Paper Annette M. Mills University of Canterbury Department of Accounting and
Internet Banking: Enablers and Inhibitors for Developing Economies A Study of Potential Users in Jamaica Completed Research Paper Annette M. Mills University of Canterbury Department of Accounting and
A Study of Intention to Use Tablet PC E-books from a Perspective. Combining TAM and IDT
 A Study of Intention to Use Tablet PC E-books from a Perspective Combining TAM and IDT MEI-YING WU, HUNG-CHI PAN Department of Information Management Chung-Hua University No.707, Sec.2, WuFu Road, Hsinchu
A Study of Intention to Use Tablet PC E-books from a Perspective Combining TAM and IDT MEI-YING WU, HUNG-CHI PAN Department of Information Management Chung-Hua University No.707, Sec.2, WuFu Road, Hsinchu
A Strategy of Business Collaboration for Adopting Information Technologies in Small and Medium Sized Companies in Latin America
 Association for Information Systems AIS Electronic Library (AISeL) AMCIS 2004 Proceedings Americas Conference on Information Systems (AMCIS) December 2004 A Strategy of Business Collaboration for Adopting
Association for Information Systems AIS Electronic Library (AISeL) AMCIS 2004 Proceedings Americas Conference on Information Systems (AMCIS) December 2004 A Strategy of Business Collaboration for Adopting
THEORIZING A TWO-SIDED ADOPTION MODEL FOR MOBILE MARKETING PLATFORMS
 Association for Information Systems AIS Electronic Library (AISeL) ICIS 2010 Proceedings International Conference on Information Systems (ICIS) 2010 THEORIZING A TWO-SIDED ADOPTION MODEL FOR MOBILE MARKETING
Association for Information Systems AIS Electronic Library (AISeL) ICIS 2010 Proceedings International Conference on Information Systems (ICIS) 2010 THEORIZING A TWO-SIDED ADOPTION MODEL FOR MOBILE MARKETING
Prediction of User Acceptance and Adoption of Smart Phone for Learning with Technology Acceptance Model
 Prediction of User Acceptance and Adoption of Smart Phone for Learning with Technology Acceptance Model 1 Yong-Wee Sek, 2 Siong-Hoe Lau, 2 Kung-Keat Teoh, 3 Check-Yee Law 1 Shahril Bin Parumo 1 Faculty
Prediction of User Acceptance and Adoption of Smart Phone for Learning with Technology Acceptance Model 1 Yong-Wee Sek, 2 Siong-Hoe Lau, 2 Kung-Keat Teoh, 3 Check-Yee Law 1 Shahril Bin Parumo 1 Faculty
An Analysis of Social Networks Usage for Information Communication in Business Organization
 An Analysis of Social Networks Usage for Information Communication in Business Organization Gamonkwan Phuk-intr Chulalongkorn Business School, Chulalongkorn University, Thailand. Kanibhatti Nitirojntanad
An Analysis of Social Networks Usage for Information Communication in Business Organization Gamonkwan Phuk-intr Chulalongkorn Business School, Chulalongkorn University, Thailand. Kanibhatti Nitirojntanad
Seyed Yahya Seyed Danseh 1, Shahram Hashemnia 2, Marayam Rouhi Sefidmazgi 3
 International Research Journal of Applied and Basic Sciences 2012 Available online at www.irjabs.com ISSN 2251-838X / Vol, 3 (11): 2316-2322 Science Explorer Publications a Evaluating effective factors
International Research Journal of Applied and Basic Sciences 2012 Available online at www.irjabs.com ISSN 2251-838X / Vol, 3 (11): 2316-2322 Science Explorer Publications a Evaluating effective factors
The Influence of Shopping Website Design on Consumer s Intention to Buy Online: The Case of 3D vs. 2D Online Book Stores
 Association for Information Systems AIS Electronic Library (AISeL) AMCIS 2011 Proceedings - All Submissions 8-6-2011 The Influence of Shopping Website Design on Consumer s Intention to Buy Online: The
Association for Information Systems AIS Electronic Library (AISeL) AMCIS 2011 Proceedings - All Submissions 8-6-2011 The Influence of Shopping Website Design on Consumer s Intention to Buy Online: The
Mobile Commerce Usage: Application of Theory of Reasoned Action (TRA) and Technology Acceptance Model (TAM)
 World Journal of Social Sciences Vol. 5. No. 2. April 2015 Issue. Pp. 41 50 Mobile Commerce Usage: Application of Theory of Reasoned Action (TRA) and Technology Acceptance Model (TAM) Shalini Wunnava *
World Journal of Social Sciences Vol. 5. No. 2. April 2015 Issue. Pp. 41 50 Mobile Commerce Usage: Application of Theory of Reasoned Action (TRA) and Technology Acceptance Model (TAM) Shalini Wunnava *
USER ACCEPTANCE OF INFORMATION TECHNOLOGY ACROSS CULTURES
 USER ACCEPTANCE OF INFORMATION TECHNOLOGY ACROSS CULTURES Kakoli Bandyopadhyay Lamar University, P.O. Box 10033, Beaumont, TX 77710 Phone: (409) 880-8627, Fax: (409) 880-8235 E-Mail: kakoli.bandyopadhyay@lamar.edu
USER ACCEPTANCE OF INFORMATION TECHNOLOGY ACROSS CULTURES Kakoli Bandyopadhyay Lamar University, P.O. Box 10033, Beaumont, TX 77710 Phone: (409) 880-8627, Fax: (409) 880-8235 E-Mail: kakoli.bandyopadhyay@lamar.edu
Using User-Generated Content when travelers make travel plans: A Theory of Planned Behavior perspective
 Using User-Generated Content when travelers make travel plans: A Theory of Planned Behavior perspective Luiz Augusto Machado Mendes Filho 1 Felix B. Tan 2 Annette Mills 3 Abstract: User-Generated Content
Using User-Generated Content when travelers make travel plans: A Theory of Planned Behavior perspective Luiz Augusto Machado Mendes Filho 1 Felix B. Tan 2 Annette Mills 3 Abstract: User-Generated Content
Expert assessment of organizational cybersecurity programs and development of vignettes to measure cybersecurity countermeasures awareness
 Expert assessment of organizational cybersecurity programs and development of vignettes to measure cybersecurity countermeasures awareness Jodi Goode, Nova Southeastern University, USA, jp1587@mynsu.nova.edu
Expert assessment of organizational cybersecurity programs and development of vignettes to measure cybersecurity countermeasures awareness Jodi Goode, Nova Southeastern University, USA, jp1587@mynsu.nova.edu
Please quote as: Söllner, M.; Pavlou, P. & Leimeister, J. M. (2013): Understanding Trust in IT Artifacts A new Conceptual Approach.
 Please quote as: Söllner, M.; Pavlou, P. & Leimeister, J. M. (2013): Understanding Trust in IT Artifacts A new Conceptual Approach. In: Academy of Management Annual Meeting, Orlando, Florida, USA. 1 UNDERSTANDING
Please quote as: Söllner, M.; Pavlou, P. & Leimeister, J. M. (2013): Understanding Trust in IT Artifacts A new Conceptual Approach. In: Academy of Management Annual Meeting, Orlando, Florida, USA. 1 UNDERSTANDING
Information Technology Change and the Effects on User Behavior and Cyber Security
 Information Technology Change and the Effects on User Behavior and Cyber Security Introduction Emergent Research Forum New technology implementation can have a critical effect on the user behavior and
Information Technology Change and the Effects on User Behavior and Cyber Security Introduction Emergent Research Forum New technology implementation can have a critical effect on the user behavior and
Journal of Internet Banking and Commerce An open access Internet journal (http://www.arraydev.com/commerce/jibc/)
 Journal of Internet Banking and Commerce An open access Internet journal (http://www.arraydev.com/commerce/jibc/) Journal of Internet Banking and Commerce, December 2007, vol. 12, no.3 (http://www.arraydev.com/commerce/jibc/)
Journal of Internet Banking and Commerce An open access Internet journal (http://www.arraydev.com/commerce/jibc/) Journal of Internet Banking and Commerce, December 2007, vol. 12, no.3 (http://www.arraydev.com/commerce/jibc/)
How Loyal are You? Continuance Intention and Word of Mouth in Free/Libre Open Source Software
 Association for Information Systems AIS Electronic Library (AISeL) AMCIS 2009 Doctoral Consortium Americas Conference on Information Systems (AMCIS) 2009 How Loyal are You? Continuance Intention and Word
Association for Information Systems AIS Electronic Library (AISeL) AMCIS 2009 Doctoral Consortium Americas Conference on Information Systems (AMCIS) 2009 How Loyal are You? Continuance Intention and Word
An Empirical Assessment of the Impact of ERP Task-Technology Fit on Decision Quality
 An Empirical Assessment of the Impact of ERP Task-Technology Fit on Decision Quality Arun Madapusi Department of Decision Sciences LeBow College of Business Drexel University 204 Academic Building Philadelphia,
An Empirical Assessment of the Impact of ERP Task-Technology Fit on Decision Quality Arun Madapusi Department of Decision Sciences LeBow College of Business Drexel University 204 Academic Building Philadelphia,
INVESTIGATING USER RESISTANCE TO INFORMATION SYSTEMS IMPLEMENTATION: A STATUS QUO BIAS PERSPECTIVE 1
 RESEARCH NOTE INVESTIGATING USER RESISTANCE TO INFORMATION SYSTEMS IMPLEMENTATION: A STATUS QUO BIAS PERSPECTIVE 1 By: Hee-Woong Kim Graduate School of Information Yonsei University Seoul 120 749 KOREA
RESEARCH NOTE INVESTIGATING USER RESISTANCE TO INFORMATION SYSTEMS IMPLEMENTATION: A STATUS QUO BIAS PERSPECTIVE 1 By: Hee-Woong Kim Graduate School of Information Yonsei University Seoul 120 749 KOREA
INTENTION TO USE OF SMART PHONE IN BANGKOK EXTENDED UTAUT MODEL BY PERCEIVED VALUE
 INTENTION TO USE OF SMART PHONE IN BANGKOK EXTENDED UTAUT MODEL BY PERCEIVED VALUE Krittipat Pitchayadejanant 1 * ABSTRACT Smart phones, iphone and Black Berry, are very popular among new generation people
INTENTION TO USE OF SMART PHONE IN BANGKOK EXTENDED UTAUT MODEL BY PERCEIVED VALUE Krittipat Pitchayadejanant 1 * ABSTRACT Smart phones, iphone and Black Berry, are very popular among new generation people
Top Management Support of SISP: Creating Competitive Advantage with Information Technology
 Association for Information Systems AIS Electronic Library (AISeL) AMCIS 2000 Proceedings Americas Conference on Information Systems (AMCIS) 2000 Top Management Support of SISP: Creating Competitive Advantage
Association for Information Systems AIS Electronic Library (AISeL) AMCIS 2000 Proceedings Americas Conference on Information Systems (AMCIS) 2000 Top Management Support of SISP: Creating Competitive Advantage
Factors that Differentiate between Adopters and Non-adopters of E-Commerce: An Empirical Study of Small and Medium Sized Businesses
 Association for Information Systems AIS Electronic Library (AISeL) AMCIS 2004 Proceedings Americas Conference on Information Systems (AMCIS) December 2004 Factors that Differentiate between Adopters and
Association for Information Systems AIS Electronic Library (AISeL) AMCIS 2004 Proceedings Americas Conference on Information Systems (AMCIS) December 2004 Factors that Differentiate between Adopters and
Chapter-II RESEARCH GAPS, OBJECTIVES, MODEL AND HYPOTHESIS
 Chapter-II RESEARCH GAPS, OBJECTIVES, MODEL AND HYPOTHESIS 2.1 Problem Identification and Research Gaps Researchers have widely applied the above models and theories for exploring internet shopping. The
Chapter-II RESEARCH GAPS, OBJECTIVES, MODEL AND HYPOTHESIS 2.1 Problem Identification and Research Gaps Researchers have widely applied the above models and theories for exploring internet shopping. The
Issues in Information Systems Volume 16, Issue IV, pp , 2015
 ANTECEDENT DETERMINANTS OF BELIEFS UNDERPINNING THE INTENTION TO ACCEPT AND USE BUSINESS INTELLIGENCE SYSTEMS: THE IMPORTANCE OF ORGANIZATIONAL FACTORS Tanja Grublješič, Faculty of Economics, University
ANTECEDENT DETERMINANTS OF BELIEFS UNDERPINNING THE INTENTION TO ACCEPT AND USE BUSINESS INTELLIGENCE SYSTEMS: THE IMPORTANCE OF ORGANIZATIONAL FACTORS Tanja Grublješič, Faculty of Economics, University
Information Security Governance and Internal Audits: A Processual Model
 Association for Information Systems AIS Electronic Library (AISeL) SAIS 2007 Proceedings Southern (SAIS) 3-1-2007 Information Security Governance and Internal Audits: A Processual Model Sushma Mishra mishras@vcu.edu
Association for Information Systems AIS Electronic Library (AISeL) SAIS 2007 Proceedings Southern (SAIS) 3-1-2007 Information Security Governance and Internal Audits: A Processual Model Sushma Mishra mishras@vcu.edu
Applying Theory of Perceived Risk and Technology Acceptance Model in the Online Shopping Channel
 Applying Theory of Perceived Risk and Technology Acceptance Model in the Online Shopping Channel Yong-Hui Li, Jing-Wen Huang Abstract As the advancement of technology, online shopping channel develops
Applying Theory of Perceived Risk and Technology Acceptance Model in the Online Shopping Channel Yong-Hui Li, Jing-Wen Huang Abstract As the advancement of technology, online shopping channel develops
