VENDOR RISK MANAGEMENT FCC SERVICES
|
|
|
- Rose Gardner
- 6 years ago
- Views:
Transcription
1 VENDOR RISK MANAGEMENT FCC SERVICES
2 Introductions Chris Tait, CISA, CFSA, CCSK, CCSFP Principal, Financial Services Baker Tilly Russ Sommers, CPA, CISA Senior Manager, Financial Services Baker Tilly
3 Agenda Section one Section two Section three The value of vendor management Current state and key drivers for action Vendor risk management (VRM) lifecycle Key stages and activities Implementing a successful program Challenges, best practices and lessons learned
4 Section one The value of vendor management Current state and key drivers for action
5 Background Third party: Any business partner that is not under direct control of the organization that engages them. Type Services These entities may include but are not limited to: Vendors or suppliers Providers of service (e.g., advertising / marketing, licensees, document services, administrators or processors) Joint venture or alliance partners Companies utilize third parties in three main ways: To perform functions on the company s behalf (outsourcing) To provide products and services that the company does not originate (makes third party products and services available to customers) To franchise the company s attributes (most risky third party vendors conduct business in company s name)
6 Audience polling question (PollEverywhere) How mature is your organization's vendor risk management program? A. No formal process established B. Just getting started C. Well defined, not consistently followed D. It s a well-oiled machine
7 Third party vendor breaches According to Soha Systems survey: Approximately 63 percent of all data breaches can be attributed to a third party vendor Only 2 percent of IT experts consider third party secure access a top priority Respondents believe their own organizations are secure from third party data breaches but think their competitors are vulnerable to them *Soha Systems Survey on Third Party Risk Management
8 In the news April 6 April 10 March 27
9 Audience polling question (PollEverywhere) A. Yes B. No Does your organization conduct a formal vendor risk / third party risk management assessment?
10 In the numbers 63% of companies do not have a fully mature method to control and track sensitive data. In fact, 19 percent don t have a method at all 4 33% of companies have not commissioned a vendor risk assessment4 58% of companies use thirdparties to manage sensitive data, but 48 percent of them do not have a third party management program in place 4 88% of executives are confident that their companies can defend against a cyberattack. Yet, 822 million records were compromised in
11 Key risk factors Information security and privacy Financial reporting IT continuity Regulatory compliance Potential risks Data integrity Customer service Outsourcing business operations or using third parties does not absolve organizations of their responsibilities to manage risk!
12 Section two Vendor risk management lifecycle Key stages and activities Planning Due diligence and selection Contract negation Ongoing monitoring Termination
13 Vendor risk management lifecycle When and how does your organization conduct third-party due diligence?
14 Vendor risk management lifecycle How third-parties are monitored after the initial screening (due diligence)? 40% 6% 13% % of Respondents 6 13% Other We Use an outsourced 3P provider for Continuous Monitoring We do not Monitor 3Ps after an Initial Screening 40% 14% We get Regular KPI Reporting from Our 3Ps We Monitor only Select, High-Risk 3Ps after Initial Screening We Continuously Monitor Our 3P Engagements Ourselves
15 Vendor risk management lifecycle Planning Due diligence and selection Contract negation Ongoing monitoring Termination Key tasks in planning include: Identify business need (requires stakeholder involvement) Define detailed solution requirements Establish top selection criteria (i.e., vendor evaluation factors that will hold the most weight in the selection process) Develop inherent risk profile based on the services to be provided Obtain appropriate approvals to proceed with request for proposal (RFP) Understand data flow (input process output)
16 Vendor risk management lifecycle Planning Due diligence and selection Contract negation Ongoing monitoring Termination Key tasks in due diligence and selection include: Identify vendors to solicit for proposal Determine proposal format / content requirements, timeline to submit questions / proposals and issue the RFP Obtain organizational information for each vendor Company history, reputation and financial standing Description of key programs and policies (e.g., risk management, information security, disaster recovery / business continuity) Any use of sub-contractors ( fourth-party vendors ) Evaluate due diligence materials and proposals, select provider
17 Vendor risk management lifecycle Planning Due diligence and selection Contract negation Ongoing monitoring Termination Key tasks in contract negotiation include: Determine contract composition (e.g., which party s contract template to start with, who will complete initial draft, etc.) Include language to address: Roles and responsibilities Scope, timing and key milestones General business terms (GBTs, also T&C) Fees
18 Vendor risk management lifecycle Planning Due diligence and selection Contract negation Ongoing monitoring Termination Key tasks in contract negotiation cont.: Include language to address cont.: Confidentiality (e.g., NDA, handling of customer data) Performance measurements Internal control / audit requirements (e.g., SOC) Termination rights Ownership and return of data Negotiate contract language and obtain necessary approvals on revisions Execute agreement
19 Vendor risk management lifecycle Planning Due diligence and selection Contract negation Ongoing monitoring Termination Key tasks in ongoing monitoring include: Develop a risk based vendor review schedule to guide activities and track progress Define criteria and procedures for escalation for noncompliance Activities to gauge vendor performance may include: Establish performance indicators (similar purpose as top selection criteria) Review of contractual SLAs to performance Leverage existing system data to efficiently generate metrics dashboards Distribute customer satisfaction surveys to organizational stakeholders Keep monitoring simple minimize metrics to most important
20 Vendor risk management lifecycle Planning Due diligence and selection Contract negation Ongoing monitoring Termination Ongoing monitoring: Internal control options Potential activities to obtain assurance over internal controls may include: Issue vendor questionnaires Perform desktop audits: Key program and policy documentation Third-party reports or certifications: SOC report or equivalent (dependent on industry and inherent risks of vendor s services) Onsite audit: By internal resources or a third party contracted on your behalf
21 Ongoing monitoring: SOC reporting options SOC 1 SOC 2 SOC 3 AUP Guidance SSAE 16 AT 101 AT 101 AT 101 AT 201 Scope Controls related to client s financial reporting (ICFR) Controls related to IT operations or Controls compliance: related Security, Controls related to IT operations to IT operations confidentiality, or compliance processing or compliance integrity, availability and / or privacy Controls determined by the requesting party Typical report users Internal / external auditors Vendor management internal / external auditors General use Requesting client only Remember: The best option is subjective, and based on the services performed and related third party risks
22 Vendor risk management lifecycle Planning Due diligence and selection Contract negation Ongoing monitoring Termination Key tasks in termination include: Evaluate reasons for considering termination (e.g., performance issues, wish to bring in-house) Perform cost-benefit analysis: Transition costs vs. benefits of changing Review contract language on original contract term and termination rights Develop plan for termination procedures, responsibilities and timeline Determine appropriate point of contact, designate a liaison for the termination process and deliver termination notice to vendor Manage transfer of assets, data and knowledge
23 Section three Implementing a successful program Challenges, best practices and lessons learned
24 What can undermine program effectiveness? % of Respondents Other Organization unwilling to ask on 3Ps if business impact 51% 51% 16% 4% 20% 23% 29% Leaders do not support 3P risk management Lack of internal skill set Employees do not adhere to 3P risk management processes Lack of governance 31% No clear ownership for the program 43% 36% Poorly defined methodology for managing 3P No central repository for documentation related to 3Ps 42% 37% Gathering, integrating, analyzing, making use of 3P data 40% Reporting on 3P issues is inconsistent Limited resources Difficulty monitoring 3P relationships
25 Role and responsibilities Which model? Decentralized Centralized
26 Audience polling question (PollEverywhere) Do you have a centralized, decentralized or hybrid VRM model? A. Centralized B. Decentralized C. Hybrid
27 Role and responsibilities Who? Business lead Internal audit Executive management Compliance ERM IT Legal VMS
28 Tool sets Which framework? Federal Financial Institutions Examination Council (FFIEC) IT Examination Handbook Vendor and third-party management, outsourcing technology services and supervision of technology service providers Office of the Comptroller of the Currency (OCC) OCC Bulletin Shared assessments SIG Toolset Independently built by cross-functional industry group and is updated on a annual basis
29 Tool sets Which platform? Microsoft Suite SharePoint Vendor management software
30 Audience polling question (PollEverywhere) What tools does your organization use to track third party /vendor risks and conduct an analysis? A. Microsoft Office Docs B. Shared Assessments Framework (SIG) C. GRC Toolset D. Other tools E. We don t track them
31 Limited resources Advocate for dedicated budgets and program resources. Improved compliance reduces any fines or penalties that could impact the bottom line. Tighter focus on specific controls associated with those relationships found to pose the greatest risk made possible through vendor stratification. BUDGET SIMPLIFY Limited resource solutions TARGET STANDARDIZE Reduce cost of managing vendor risk through stratification, process simplification and use of technology. Improved efficiency, timeliness and accuracy stemming from streamlined and standardized processes
32 Create, classify and review How to identify vendors? Follow the money! Look for contracts Meet with business units
33 Create, classify and review How many tiers and review frequency? Tier 1 Critical Tier 2 Essential Tier 3 Operational Mission critical Minimum level of service No critical data Significant risk Critical data Minimal or no customer impact Tier 1 Critical Tier 2 Essential Tier 3 Operational Semi-annual Annual Biennial
34 Vendor stratification Remove categories that don t pose risk Stratify third parties into risk categories Prioritize high risk vendors for review Higher risk: On-site reviews Moderate risk: Lower risk: Desktop reviews Vendor self assessments
35 Questions to ask yourself Are third-party risks considered in the organization s overall approach to enterprise risk management? Do risk managers consider thirdparty risk in their risk assessments? Are appropriate resources allocated to address third-party risks? Are third-party risk management roles and responsibilities clearly defined within the organization? Has an inventory and ranking of third-party risks been performed?
36 Cited references Tone at the Top, IIA, April 2014, Issue 67.1 Here s who boardrooms are blaming for data breaches, Fortune Magazine, May 29, 2015, Reputation Risk Leading company Concern in 2015, Forbes, January 5, 2015, Trustwave, 2014 State of Risk Report Note: Adapted from 2015 Ethics & Compliance Third Party Risk Management Benchmark Report by NAVEX Global, retrieved from markreport_web.pdf6
37 Disclosure The information provided here is of a general nature and is not intended to address the specific circumstances of any individual or entity. In specific circumstances, the services of a professional should be sought. Tax information, if any, contained in this communication was not intended or written to be used by any person for the purpose of avoiding penalties, nor should such information be construed as an opinion upon which any person may rely. The intended recipients of this communication and any attachments are not subject to any limitation on the disclosure of the tax treatment or tax structure of any transaction or matter that is the subject of this communication and any attachments. Baker Tilly refers to Baker Tilly Virchow Krause, LLP, an independently owned and managed member of Baker Tilly International Baker Tilly Virchow Krause, LLP
38
VENDOR MANAGEMENT 101
 VENDOR MANAGEMENT 101 Enterprise Risk Management Vendor Management Business Continuity IT GRC Internal Audit Regulatory Compliance Manager Introduction to Vendor Management About Your Presenter Andrea
VENDOR MANAGEMENT 101 Enterprise Risk Management Vendor Management Business Continuity IT GRC Internal Audit Regulatory Compliance Manager Introduction to Vendor Management About Your Presenter Andrea
Best Practices: Vendor Risk Questionnaires PROCESSUNITY WEBINAR SERIES
 Best Practices: Vendor Risk Questionnaires PROCESSUNITY WEBINAR SERIES Today s Presenters Tom Garrubba Senior Director Shared Assessments Bryan Burnhart Head of Strategic Alliances ProcessUnity Ed Thomas
Best Practices: Vendor Risk Questionnaires PROCESSUNITY WEBINAR SERIES Today s Presenters Tom Garrubba Senior Director Shared Assessments Bryan Burnhart Head of Strategic Alliances ProcessUnity Ed Thomas
STRATEGIES FOR EFFECTIVELY WORKING WITH THIRD-PARTIES. September 2017
 STRATEGIES FOR EFFECTIVELY WORKING WITH THIRD-PARTIES September 2017 Your presenters Nancy Aubrey Partner Boston, MA Nancy.aubrey@rsmus.com Rick Shriner Principal McLean, VA Rick.shriner@rsmus.com 2 Agenda
STRATEGIES FOR EFFECTIVELY WORKING WITH THIRD-PARTIES September 2017 Your presenters Nancy Aubrey Partner Boston, MA Nancy.aubrey@rsmus.com Rick Shriner Principal McLean, VA Rick.shriner@rsmus.com 2 Agenda
Third Party Risk Management ( TPRM ) Transformation
 Third Party Risk Management ( TPRM ) Transformation September 20, 2017 Internal use only An introduction to TPRM What is a Third Party relationship? A Third Party relationship is any business arrangement
Third Party Risk Management ( TPRM ) Transformation September 20, 2017 Internal use only An introduction to TPRM What is a Third Party relationship? A Third Party relationship is any business arrangement
Ensuring Organizational & Enterprise Resiliency with Third Parties
 Ensuring Organizational & Enterprise Resiliency with Third Parties Geno Pandolfi Tuesday, May 17, 2016 Room 7&8 (1:30-2:15 PM) Session Review Objectives Approaches to Third Party Risk Management Core Concepts
Ensuring Organizational & Enterprise Resiliency with Third Parties Geno Pandolfi Tuesday, May 17, 2016 Room 7&8 (1:30-2:15 PM) Session Review Objectives Approaches to Third Party Risk Management Core Concepts
THIRD-PARTY RISK MANAGEMENT
 THIRD-PARTY RISK MANAGEMENT Beyond a Regulatory Requirement April 28, 2017 Ken Glascock, CPA, CAMS, CIA, CFSA, CRCM Director kglascock@bkd.com AGENDA Let s Break It Down What Is Third-Party Risk Management?
THIRD-PARTY RISK MANAGEMENT Beyond a Regulatory Requirement April 28, 2017 Ken Glascock, CPA, CAMS, CIA, CFSA, CRCM Director kglascock@bkd.com AGENDA Let s Break It Down What Is Third-Party Risk Management?
Third Party Vendor Management and FDR Compliance
 Smart decisions. Lasting value. Third Party Vendor Management and FDR Compliance Healthcare Summit 2018: Simplifying Healthcare September 18, 2018 Jason Lackey, Cigna-HealthSpring Scott Gerard, Crowe Matt
Smart decisions. Lasting value. Third Party Vendor Management and FDR Compliance Healthcare Summit 2018: Simplifying Healthcare September 18, 2018 Jason Lackey, Cigna-HealthSpring Scott Gerard, Crowe Matt
Vendor Management Challenges and Expectations An Open Discussion April 13, 2017
 1 Practical solutions driving tangible results Vendor Management Challenges and Expectations An Open Discussion April 13, 2017 Agenda Common Themes Discussion Expectations Overcoming Obstacles Common Comments
1 Practical solutions driving tangible results Vendor Management Challenges and Expectations An Open Discussion April 13, 2017 Agenda Common Themes Discussion Expectations Overcoming Obstacles Common Comments
Lessons Learned in Streamlining the Third-party Risk Assessment Process
 Lessons Learned in Streamlining the Third-party Risk Assessment Process Agenda Welcome & Introductions Overview of the Third Party Risk Management Lifecycle Three Unique Perspectives on: Third Party Inventories
Lessons Learned in Streamlining the Third-party Risk Assessment Process Agenda Welcome & Introductions Overview of the Third Party Risk Management Lifecycle Three Unique Perspectives on: Third Party Inventories
IT Service Delivery And Support Week Seven: SLA. IT Auditing and Cyber Security Fall 2016 Instructor: Liang Yao
 IT Service Delivery And Support Week Seven: SLA IT Auditing and Cyber Security Fall 2016 Instructor: Liang Yao 1 Outsourcing Drivers Outsourced IT Works Outsourced IT Activity Samples Top Three Outsourcing
IT Service Delivery And Support Week Seven: SLA IT Auditing and Cyber Security Fall 2016 Instructor: Liang Yao 1 Outsourcing Drivers Outsourced IT Works Outsourced IT Activity Samples Top Three Outsourcing
Strengthening Vendor Risk Management Program
 Strengthening Vendor Risk Management Program ACUIA Region 5 Fall Meeting Portsmouth, N.H. October 2017 PKF O Connor Davies Risk Advisory Services Governance & Regulations Cyber-Security Risk Management
Strengthening Vendor Risk Management Program ACUIA Region 5 Fall Meeting Portsmouth, N.H. October 2017 PKF O Connor Davies Risk Advisory Services Governance & Regulations Cyber-Security Risk Management
Extended Enterprise Risk Management
 Extended Enterprise Risk Management Driving performance through the extended enterprise October 2015 A network within a network The Extended Enterprise is the concept that an organization does not operate
Extended Enterprise Risk Management Driving performance through the extended enterprise October 2015 A network within a network The Extended Enterprise is the concept that an organization does not operate
Rick Ensenbach, CISSP-ISSMP, CISA, CISM, CCSFP Senior Manager, Wipfli Risk Advisory Services OBJECTIVES
 Rick Ensenbach, CISSP-ISSMP, CISA, CISM, CCSFP Senior Manager, Wipfli Risk Advisory Services 1 OBJECTIVES What should be done before you sign a contract with a vendor Your responsibilities throughout the
Rick Ensenbach, CISSP-ISSMP, CISA, CISM, CCSFP Senior Manager, Wipfli Risk Advisory Services 1 OBJECTIVES What should be done before you sign a contract with a vendor Your responsibilities throughout the
Risk Assessment - Balancing Risk While Enhancing Controls
 Risk Assessment - Balancing Risk While Enhancing Controls cliftonlarsonallen.com Session Objectives Define risk and risk assessment. Execution of assessment and approach Impact on controls and future state
Risk Assessment - Balancing Risk While Enhancing Controls cliftonlarsonallen.com Session Objectives Define risk and risk assessment. Execution of assessment and approach Impact on controls and future state
ERP Is it for me? American Public Power Association Business & Financial Conference September 17, 2018
 ERP Is it for me? American Public Power Association Business & Financial Conference September 17, 2018 About your instructor Amanda Lasinski, Consulting Manager > Energy and Utilities Team > 12 years of
ERP Is it for me? American Public Power Association Business & Financial Conference September 17, 2018 About your instructor Amanda Lasinski, Consulting Manager > Energy and Utilities Team > 12 years of
Risk Advisory SERVICES. A holistic approach to implementing effective governance, managing risk and maintaining compliance
 Risk Advisory SERVICES A holistic approach to implementing effective governance, managing risk and maintaining compliance Contents Weaver's Risk Advisory Services 1 Enterprise Risk Management 4 Assessing
Risk Advisory SERVICES A holistic approach to implementing effective governance, managing risk and maintaining compliance Contents Weaver's Risk Advisory Services 1 Enterprise Risk Management 4 Assessing
REGULATORY HOT TOPIC Third Party IT Vendor Management
 REGULATORY HOT TOPIC Third Party IT Vendor Management 1 Todays Outsourced Technology Services Core Processing Internet Banking Mobile Banking Managed Security Services Managed Data Center Services And
REGULATORY HOT TOPIC Third Party IT Vendor Management 1 Todays Outsourced Technology Services Core Processing Internet Banking Mobile Banking Managed Security Services Managed Data Center Services And
Q1 Please select the primary industry in which your company operates.
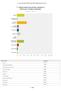 Q Please select the primary industry in which your company operates. Answered: 9 Skipped: Banking Construction & Real Estate Financial Services &... Food & Commodities Government Healthcare Higher Education
Q Please select the primary industry in which your company operates. Answered: 9 Skipped: Banking Construction & Real Estate Financial Services &... Food & Commodities Government Healthcare Higher Education
Article from: CompAct. April 2013 Issue No. 47
 Article from: CompAct April 2013 Issue No. 47 Overview of Programmatic Framework and Key Considerations Key elements Description Items to consider Definition and identification of EUCs The statement that
Article from: CompAct April 2013 Issue No. 47 Overview of Programmatic Framework and Key Considerations Key elements Description Items to consider Definition and identification of EUCs The statement that
Internal Audit Challenges & Opportunities Speaker: Laurie Shen, Director, Grant Thornton LLP
 Internal Audit Challenges & Opportunities Speaker: Laurie Shen, Director, Grant Thornton LLP March 28, 2012-1 - Speaker Introduction Laurie Shen is a Director at Grant Thornton's Northeast Internal Audit
Internal Audit Challenges & Opportunities Speaker: Laurie Shen, Director, Grant Thornton LLP March 28, 2012-1 - Speaker Introduction Laurie Shen is a Director at Grant Thornton's Northeast Internal Audit
An Executive Guide to Third Party Management
 An Executive Guide to SIG Global Summit October 14 16, 2014 Executive Summary Companies... should take a hard look at the agents conducting business on their behalf. Kara Brockmeyer, chief of the SEC Enforcement
An Executive Guide to SIG Global Summit October 14 16, 2014 Executive Summary Companies... should take a hard look at the agents conducting business on their behalf. Kara Brockmeyer, chief of the SEC Enforcement
Internal audit insights High-impact areas of focus
 Internal audit insights High-impact areas of focus Introduction In any organization, there are numerous areas where Internal Audit s objectivity, perspective, and skills can assist stakeholders and provide
Internal audit insights High-impact areas of focus Introduction In any organization, there are numerous areas where Internal Audit s objectivity, perspective, and skills can assist stakeholders and provide
Hot Topics in Third Party Management. April 5, 2018 MEMBER OF ALLINIAL GLOBAL, AN ASSOCIATION OF LEGALLY INDEPENDENT FIRMS
 Hot Topics in Third Party Management April 5, 2018 MEMBER OF ALLINIAL GLOBAL, AN ASSOCIATION OF LEGALLY INDEPENDENT FIRMS 2018 Wolf & Company, P.C. Before we get started Today s presentation slides can
Hot Topics in Third Party Management April 5, 2018 MEMBER OF ALLINIAL GLOBAL, AN ASSOCIATION OF LEGALLY INDEPENDENT FIRMS 2018 Wolf & Company, P.C. Before we get started Today s presentation slides can
Outsourcing Transparency Evolution: Creating Value Across the Third-Party Extended Enterprise
 Outsourcing Transparency Evolution: Creating Value Across the Third-Party Extended Enterprise @ComplianceWeek #CW2017 Release for answers to polling questions I understand that any data or information
Outsourcing Transparency Evolution: Creating Value Across the Third-Party Extended Enterprise @ComplianceWeek #CW2017 Release for answers to polling questions I understand that any data or information
A Guide to IT Risk Assessment for Financial Institutions. March 2, 2011
 A Guide to IT Risk Assessment for Financial Institutions March 2, 2011 Welcome! Housekeeping Control panel on the right side of your screen. Audio Telephone VoIP Submit Questions in the pane on the control
A Guide to IT Risk Assessment for Financial Institutions March 2, 2011 Welcome! Housekeeping Control panel on the right side of your screen. Audio Telephone VoIP Submit Questions in the pane on the control
Internal Audit s Role in Third Party Risk Management (TPRM)
 www.pwc.com Internal Audit s Role in Third (TPRM) Jon Pastore, Nick Fullmer Third (TPRM) Framework What is Third? Third Party risk management is focused on understanding and managing risks associated with
www.pwc.com Internal Audit s Role in Third (TPRM) Jon Pastore, Nick Fullmer Third (TPRM) Framework What is Third? Third Party risk management is focused on understanding and managing risks associated with
HOW TO AVOID THE DANGER OF WEAK CONTROLS IN THIRD-PARTY RISK MANAGEMENT
 E-Guide HOW TO AVOID THE DANGER OF WEAK CONTROLS IN THIRD-PARTY RISK MANAGEMENT SearchSecurity S ecurity expert Michael Cobb explains how to put in place additional safeguards to protect the system and
E-Guide HOW TO AVOID THE DANGER OF WEAK CONTROLS IN THIRD-PARTY RISK MANAGEMENT SearchSecurity S ecurity expert Michael Cobb explains how to put in place additional safeguards to protect the system and
Vendor Management 101
 Vendor Management 101 January 18, 2018 Presented by Branan Cooper Chief Risk Officer at Venminder branan.cooper@venminder.com (502) 909-0325 Session Agenda Vendor risk management why it s required today
Vendor Management 101 January 18, 2018 Presented by Branan Cooper Chief Risk Officer at Venminder branan.cooper@venminder.com (502) 909-0325 Session Agenda Vendor risk management why it s required today
Effects of GDPR and NY DFS on your Third Party Risk Management Program
 Effects of GDPR and NY DFS on your Third Party Risk Management Program Please disable popup blocking software before viewing this webcast June 27, 2017 Grant Thornton LLP. All rights reserved. 1 CPE Reminders
Effects of GDPR and NY DFS on your Third Party Risk Management Program Please disable popup blocking software before viewing this webcast June 27, 2017 Grant Thornton LLP. All rights reserved. 1 CPE Reminders
Using a Compliance Program Assessment to Elevate Institutional Compliance Effectiveness
 Using a Compliance Program Assessment to Elevate Institutional Compliance Effectiveness Kevin Robinson Associate Vice President, Office of Audit, Compliance & Privacy Auburn University Michael Somich Executive
Using a Compliance Program Assessment to Elevate Institutional Compliance Effectiveness Kevin Robinson Associate Vice President, Office of Audit, Compliance & Privacy Auburn University Michael Somich Executive
Effective Vendor Risk Management. April 21, Mario A. Mosse. This Training is Brought to you by ComplianceOnline. Presenter:
 This Training is Brought to you by ComplianceOnline. Effective Vendor Risk Management Presenter: Mario A. Mosse April 21, 2017 This training session is sponsored by 2014 ComplianceOnline www.complianceonlie.com
This Training is Brought to you by ComplianceOnline. Effective Vendor Risk Management Presenter: Mario A. Mosse April 21, 2017 This training session is sponsored by 2014 ComplianceOnline www.complianceonlie.com
The IIA toolbox.
 The IIA toolbox www.theiia.org Agenda 1. International Professional Practices Framework (IPPF) 2. The Professional Issues Committee (PIC) 3. IIA Guidance 4. The GTAG s! 5. Questions 2 Who am I? Background
The IIA toolbox www.theiia.org Agenda 1. International Professional Practices Framework (IPPF) 2. The Professional Issues Committee (PIC) 3. IIA Guidance 4. The GTAG s! 5. Questions 2 Who am I? Background
Implementing and maintaining ISAE 3402
 Implementing and maintaining ISAE 3402 2 Implementing and maintaining ISAE 3402 Contents Introduction 4 Purpose and background 5 Benefits to the service organization 7 How Ernst & Young helps 8 Successful
Implementing and maintaining ISAE 3402 2 Implementing and maintaining ISAE 3402 Contents Introduction 4 Purpose and background 5 Benefits to the service organization 7 How Ernst & Young helps 8 Successful
ISACA San Francisco Chapter
 ISACA San Francisco Chapter The 2007 Privacy Panel Rena Mears, CISSP, CIPP, CPA, CISA Partner, Deloitte & Touche LLP March 23, 2007 San Francisco 0 What is Privacy and Why Now? Definition of PII The definition
ISACA San Francisco Chapter The 2007 Privacy Panel Rena Mears, CISSP, CIPP, CPA, CISA Partner, Deloitte & Touche LLP March 23, 2007 San Francisco 0 What is Privacy and Why Now? Definition of PII The definition
Starting a Vendor Assessment Program
 Starting a Vendor Assessment Program Kevin Brandt, CBCP Agenda Why? Wait Really Why? Overview Policies and Procedures Implementation Work Effort Assessment Tips Special Case What About? Looking Forward
Starting a Vendor Assessment Program Kevin Brandt, CBCP Agenda Why? Wait Really Why? Overview Policies and Procedures Implementation Work Effort Assessment Tips Special Case What About? Looking Forward
Drive Your Business. Four Ways to Improve Your Vendor Risk Program
 Drive Your Business Four Ways to Improve Your Vendor Risk Program Introduction Risk-management professionals often find the creation of a vendor risk management (VRM) program to be a challenging task,
Drive Your Business Four Ways to Improve Your Vendor Risk Program Introduction Risk-management professionals often find the creation of a vendor risk management (VRM) program to be a challenging task,
The Case for Outsourcing Accounts Payable
 Presented by Lynn Belletti BNY Mellon Transaction Processing Director The & Procure-To-Pay Conference & Expo is produced by: The world is changing. How will you respond to the new pressures of regulatory
Presented by Lynn Belletti BNY Mellon Transaction Processing Director The & Procure-To-Pay Conference & Expo is produced by: The world is changing. How will you respond to the new pressures of regulatory
Why Is Third Party Risk Management Important?
 Third Party Risk Management Managing Risks in Your Extended Enterprise Why Is Third Party Risk Management Important? It is not a new concept for organisations to engage with third parties for the provision
Third Party Risk Management Managing Risks in Your Extended Enterprise Why Is Third Party Risk Management Important? It is not a new concept for organisations to engage with third parties for the provision
Agenda. Enterprise Risk Management Defined. The Intersection of Enterprise-wide Risk Management (ERM) and Business Continuity Management (BCM)
 The Intersection of Enterprise-wide Risk (ERM) and Business Continuity (BCM) Marc Dominus 2005 Protiviti Inc. EOE Agenda Terminology and Process Introductions ERM Process Overview BCM Process Overview
The Intersection of Enterprise-wide Risk (ERM) and Business Continuity (BCM) Marc Dominus 2005 Protiviti Inc. EOE Agenda Terminology and Process Introductions ERM Process Overview BCM Process Overview
Model Risk Management (MRM)
 Model Risk Management (MRM) 2015 SEAC Fall Meeting Dwayne Husbands November 20, 2015 Overview Introduction Model risk management framework Common challenges Page 1 Introduction Background Model risk management
Model Risk Management (MRM) 2015 SEAC Fall Meeting Dwayne Husbands November 20, 2015 Overview Introduction Model risk management framework Common challenges Page 1 Introduction Background Model risk management
Data integrity forensics Bring transparency and trust to third-party data use
 Legal, Compliance and Technology Webcast Series Sponsored by EY Forensic & Integrity Services Bring transparency and trust to third-party data use 24 October 2018 Today s speakers Moderator: Eric Derk
Legal, Compliance and Technology Webcast Series Sponsored by EY Forensic & Integrity Services Bring transparency and trust to third-party data use 24 October 2018 Today s speakers Moderator: Eric Derk
Click to edit Master title style
 Click to edit Master title style Click Category to edit Management: Master title style Transformational Change in Federal Procurement Breakout Third Session level #G13 Eric Heffernan, Principal, Grant
Click to edit Master title style Click Category to edit Management: Master title style Transformational Change in Federal Procurement Breakout Third Session level #G13 Eric Heffernan, Principal, Grant
Effective Risk Management With AML Risk Assessment. January 25, 2017
 Effective Risk Management With AML Risk Assessment January 25, 2017 2017 2017 Crowe Crowe Horwath Horwath LLP LLP Agenda Regulatory Trends in Risk Assessment Crowe Approach to Anti-Money Laundering (AML)
Effective Risk Management With AML Risk Assessment January 25, 2017 2017 2017 Crowe Crowe Horwath Horwath LLP LLP Agenda Regulatory Trends in Risk Assessment Crowe Approach to Anti-Money Laundering (AML)
STEPS FOR EFFECTIVE MANAGEMENT OF VENDOR AND SUPPLIER CYBERSECURITY RISKS. April 25, 2018 In-House Counsel Conference
 STEPS FOR EFFECTIVE MANAGEMENT OF VENDOR AND SUPPLIER CYBERSECURITY RISKS April 25, 2018 In-House Counsel Conference Presenters: Daniela Ivancikova, Assistant General Counsel, University of Delaware Evan
STEPS FOR EFFECTIVE MANAGEMENT OF VENDOR AND SUPPLIER CYBERSECURITY RISKS April 25, 2018 In-House Counsel Conference Presenters: Daniela Ivancikova, Assistant General Counsel, University of Delaware Evan
Presented by Russ Hissom and Carol Arneson
 Evidence Standards and Insights for NERC Compliance Audits Presented by Russ Hissom and Carol Arneson Baker Tilly Virchow Krause, LLP March 1, 2010 1 About Baker Tilly Virchow Krause Company Overview Firm
Evidence Standards and Insights for NERC Compliance Audits Presented by Russ Hissom and Carol Arneson Baker Tilly Virchow Krause, LLP March 1, 2010 1 About Baker Tilly Virchow Krause Company Overview Firm
Certified Identity Governance Expert (CIGE) Overview & Curriculum
 Overview Identity and Access Governance (IAG) provides the link between Identity and Access Management (IAM) rules and the policies within a company to protect systems and data from unauthorized access,
Overview Identity and Access Governance (IAG) provides the link between Identity and Access Management (IAM) rules and the policies within a company to protect systems and data from unauthorized access,
Firm Profile TURNING RISKS INTO OPPORTUNITIES
 Firm Profile TURNING RISKS INTO OPPORTUNITIES You can measure opportunity with the same yardstick that measures the risk involved. They go together. Earl Nightingale TRUSTED ADVISORS RiSK Opportunities
Firm Profile TURNING RISKS INTO OPPORTUNITIES You can measure opportunity with the same yardstick that measures the risk involved. They go together. Earl Nightingale TRUSTED ADVISORS RiSK Opportunities
29/11/2017. Risk Management Policy
 1 Purpose APA Group (APA) is Australia s leading energy infrastructure business delivering smart, reliable and safe solutions through our deep industry knowledge and interconnected infrastructure. Risk
1 Purpose APA Group (APA) is Australia s leading energy infrastructure business delivering smart, reliable and safe solutions through our deep industry knowledge and interconnected infrastructure. Risk
How to Stand Up a Privacy Program: Privacy in a Box
 How to Stand Up a Privacy Program: Privacy in a Box Part III of III: Maturing a Privacy Program Presented by the IT, Privacy, & ecommerce global committee of ACC Thanks to: Nick Holland, Fieldfisher (ITPEC
How to Stand Up a Privacy Program: Privacy in a Box Part III of III: Maturing a Privacy Program Presented by the IT, Privacy, & ecommerce global committee of ACC Thanks to: Nick Holland, Fieldfisher (ITPEC
Evolving Core Tasks for Improved Internal Audit Performance. Copyright 2018 AuditBoard Inc. 1
 Evolving Core Tasks for Improved Internal Audit Performance Copyright 2018 AuditBoard Inc. 1 Introductions Built by experienced auditors, AuditBoard allows enterprises to collaborate, manage, analyze and
Evolving Core Tasks for Improved Internal Audit Performance Copyright 2018 AuditBoard Inc. 1 Introductions Built by experienced auditors, AuditBoard allows enterprises to collaborate, manage, analyze and
PMO In A Box. Prepared for UBS
 PMO In A Box Prepared for UBS Roadmap Why PMO In A Box? Establish PMO Governance Standardize Methodology Create a Stakeholder Partnership Plan 2 PMOs Are In Transition 3 CEB PMO Executive Council pmo in
PMO In A Box Prepared for UBS Roadmap Why PMO In A Box? Establish PMO Governance Standardize Methodology Create a Stakeholder Partnership Plan 2 PMOs Are In Transition 3 CEB PMO Executive Council pmo in
RSA ARCHER INSPIRE EVERYONE TO OWN RISK
 RSA ARCHER INSPIRE EVERYONE TO OWN RISK Executive Priorities Growth is the highest priority 54 % 25 % Technology initiatives are second priority Business Growth & Technology Copyright 2016 EMC Corporation.
RSA ARCHER INSPIRE EVERYONE TO OWN RISK Executive Priorities Growth is the highest priority 54 % 25 % Technology initiatives are second priority Business Growth & Technology Copyright 2016 EMC Corporation.
Vendor Management Risk Mitigation:
 Vendor Management Risk Mitigation: The Importance of Having a Formalized Methodology Sun Life Financial Laura Williams AVP, Procurement Opus Sam Mele Vice President Sales sig.org/summit Case Study: Supplier
Vendor Management Risk Mitigation: The Importance of Having a Formalized Methodology Sun Life Financial Laura Williams AVP, Procurement Opus Sam Mele Vice President Sales sig.org/summit Case Study: Supplier
Service Organization Controls (SOC) Reporting Discussion: Perspectives and Opportunities
 IIA Chicago Chapter 53 rd Annual Seminar April 15, 2013, Donald E. Stephens Convention Center @IIAChicago #IIACHI Service Organization Controls (SOC) Reporting Discussion: Perspectives and Opportunities
IIA Chicago Chapter 53 rd Annual Seminar April 15, 2013, Donald E. Stephens Convention Center @IIAChicago #IIACHI Service Organization Controls (SOC) Reporting Discussion: Perspectives and Opportunities
Internal Audit Department 350 South 5 th Street, Suite 302 Minneapolis, MN (612)
 Internal Audit Department 350 South 5 th Street, Suite 302 Minneapolis, MN 55415-1316 (612) 673-2056 Date: July 19, 2016 To: Re: Mayor Betsy Hodges; City Council Members; City Coordinator Cronk; Chief
Internal Audit Department 350 South 5 th Street, Suite 302 Minneapolis, MN 55415-1316 (612) 673-2056 Date: July 19, 2016 To: Re: Mayor Betsy Hodges; City Council Members; City Coordinator Cronk; Chief
Vendor Management from an Auditor s Perspective
 Vendor Management from an Auditor s Perspective Mike Morris Partner mmorris@pkm.com (404) 420-5669 Mary Beth Marchione Systems Manager mmarchione@pkm.com (404) 548-2825 April 25, 2017 Session Agenda Understand
Vendor Management from an Auditor s Perspective Mike Morris Partner mmorris@pkm.com (404) 420-5669 Mary Beth Marchione Systems Manager mmarchione@pkm.com (404) 548-2825 April 25, 2017 Session Agenda Understand
5 Core Must-Haves for Improved Internal Audit Performance. Copyright 2018 AuditBoard Inc. 1
 5 Core Must-Haves for Improved Internal Audit Performance Copyright 2018 AuditBoard Inc. 1 Introductions Built by experienced auditors, AuditBoard allows enterprises to collaborate, manage, analyze and
5 Core Must-Haves for Improved Internal Audit Performance Copyright 2018 AuditBoard Inc. 1 Introductions Built by experienced auditors, AuditBoard allows enterprises to collaborate, manage, analyze and
Efficiency First Program
 Efficiency First Program Short-Term Impact; Long-Term Results Presented to: Discussion Points About AOTMP Your Telecom Environment The Efficiency First Framework Our Approach The Efficiency First Program
Efficiency First Program Short-Term Impact; Long-Term Results Presented to: Discussion Points About AOTMP Your Telecom Environment The Efficiency First Framework Our Approach The Efficiency First Program
B U S I N E S S R I S K M A N A G E M E N T L T D
 B U S I N E S S R I S K M A N A G E M E N T L T D Governance, Risk and Compliance (GRC) After completing this course you will be able to Course Level Understand the requirements and benefits of GRC Develop
B U S I N E S S R I S K M A N A G E M E N T L T D Governance, Risk and Compliance (GRC) After completing this course you will be able to Course Level Understand the requirements and benefits of GRC Develop
Catching Fraud During a Recession Through Superior Internal Controls. FICPA s 25 th Annual Accounting Show. J. Stephen Nouss September 29, 2010
 Catching Fraud During a Recession Through Superior Internal Controls FICPA s 25 th Annual Accounting Show J. Stephen Nouss September 29, 2010 1 Session Objectives Fraud Facts (2008 Association of Certified
Catching Fraud During a Recession Through Superior Internal Controls FICPA s 25 th Annual Accounting Show J. Stephen Nouss September 29, 2010 1 Session Objectives Fraud Facts (2008 Association of Certified
SOLUTION BRIEF EU GENERAL DATA PROTECTION REGULATION COMPLIANCE WITH RSA ARCHER
 EU GENERAL DATA PROTECTION REGULATION COMPLIANCE WITH RSA ARCHER ARRIVAL OF GDPR IN 2018 The European Union (EU) General Data Protection Regulation (GDPR), which takes effect in 2018, will bring changes
EU GENERAL DATA PROTECTION REGULATION COMPLIANCE WITH RSA ARCHER ARRIVAL OF GDPR IN 2018 The European Union (EU) General Data Protection Regulation (GDPR), which takes effect in 2018, will bring changes
Managing Legal and Operational Risk in IT Agreements
 Managing Legal and Operational Risk in IT Agreements Presented by: Donna Pond, Senior Director, Lead Counsel, Shire Pharmaceuticals Evan J. Foster, Partner, Saul Ewing LLP Agenda: Special issues in: Conventional
Managing Legal and Operational Risk in IT Agreements Presented by: Donna Pond, Senior Director, Lead Counsel, Shire Pharmaceuticals Evan J. Foster, Partner, Saul Ewing LLP Agenda: Special issues in: Conventional
Do You Know What Your Business Associates Subcontractors & Vendors Are Doing With Your PHI & ephi?
 Do You Know What Your Business Associates Subcontractors & Vendors Are Doing With Your PHI & ephi? Web Hull Privacy, Data Protection, & Compliance Advisor Web.Hull@icloud.com HCCA 2017 Compliance Institute
Do You Know What Your Business Associates Subcontractors & Vendors Are Doing With Your PHI & ephi? Web Hull Privacy, Data Protection, & Compliance Advisor Web.Hull@icloud.com HCCA 2017 Compliance Institute
Do You Know What Your Business Associates Subcontractors & Vendors Are Doing With Your PHI & ephi?
 Do You Know What Your Business Associates Subcontractors & Vendors Are Doing With Your PHI & ephi? Web Hull Privacy, Data Protection, & Compliance Advisor Web.Hull@icloud.com HCCA 2017 Compliance Institute
Do You Know What Your Business Associates Subcontractors & Vendors Are Doing With Your PHI & ephi? Web Hull Privacy, Data Protection, & Compliance Advisor Web.Hull@icloud.com HCCA 2017 Compliance Institute
Extended enterprise risk management: New perspectives on a growing imperative The Dbriefs Governance, Risk, & Compliance series
 Extended enterprise risk management: New perspectives on a growing imperative The Dbriefs Governance, Risk, & Compliance series Dan Kinsella, Partner, Deloitte & Touche LLP Kristian Park, Partner, Deloitte
Extended enterprise risk management: New perspectives on a growing imperative The Dbriefs Governance, Risk, & Compliance series Dan Kinsella, Partner, Deloitte & Touche LLP Kristian Park, Partner, Deloitte
Sarbanes-Oxley Act of 2002 Can private businesses benefit from it?
 Sarbanes-Oxley Act of 2002 Can private businesses benefit from it? As used in this document, Deloitte means Deloitte Tax LLP, which provides tax services; Deloitte & Touche LLP, which provides assurance
Sarbanes-Oxley Act of 2002 Can private businesses benefit from it? As used in this document, Deloitte means Deloitte Tax LLP, which provides tax services; Deloitte & Touche LLP, which provides assurance
AML model risk management and validation
 AML model risk management and validation Who we are EY s Anti-Money Laundering (AML) and Regulatory Compliance Technology practice is a global team of client-serving, financial services professionals.
AML model risk management and validation Who we are EY s Anti-Money Laundering (AML) and Regulatory Compliance Technology practice is a global team of client-serving, financial services professionals.
This charter defines the purpose, authority and responsibility of News Corporation s (the Company ) Corporate Audit Department.
 CORPORATE AUDIT DEPARTMENT CHARTER PURPOSE This charter defines the purpose, authority and responsibility of News Corporation s (the Company ) Corporate Audit Department. The Institute of Internal Auditors
CORPORATE AUDIT DEPARTMENT CHARTER PURPOSE This charter defines the purpose, authority and responsibility of News Corporation s (the Company ) Corporate Audit Department. The Institute of Internal Auditors
RFQ ATTACHMENT V: RESPONSE TEMPLATE
 Instructions are provided in blue and may be deleted. Please complete your response in the template provided, and indicate clearly where separate documents are provided. Executive Summary 1. Applicant
Instructions are provided in blue and may be deleted. Please complete your response in the template provided, and indicate clearly where separate documents are provided. Executive Summary 1. Applicant
CITIBANK N.A JORDAN. Governance and Management of Information and Related Technologies Guide
 CITIBANK N.A JORDAN Governance and Management of Information and Related Technologies Guide 2018 Table of Contents 1. OVERVIEW... 2 2. Governance of Enterprise IT... 3 3. Principles of Governance of Enterprise
CITIBANK N.A JORDAN Governance and Management of Information and Related Technologies Guide 2018 Table of Contents 1. OVERVIEW... 2 2. Governance of Enterprise IT... 3 3. Principles of Governance of Enterprise
Optiv's Third- Party Risk Management Solution
 Optiv's Third- Party Management Solution Third-Party Relationships Pose Overwhelming To Your Organization. Data Processing 641 Accounting Education 601 Payroll Processing Call Center 452 400 901 Healthcare
Optiv's Third- Party Management Solution Third-Party Relationships Pose Overwhelming To Your Organization. Data Processing 641 Accounting Education 601 Payroll Processing Call Center 452 400 901 Healthcare
7 Key Trends in Enterprise Risk Management
 7 Key Trends in Enterprise Risk Management John Verver, CPA CA, CISA, CMC Kevin Legere, ACDA Presenters John Verver Consultant and Advisor to ACL Kevin Legere Director of Product Design Agenda Excellence
7 Key Trends in Enterprise Risk Management John Verver, CPA CA, CISA, CMC Kevin Legere, ACDA Presenters John Verver Consultant and Advisor to ACL Kevin Legere Director of Product Design Agenda Excellence
Corporate Law Department Information Governance Survey SURVEY RESULTS. hbrconsulting.com
 Corporate Law Department Information Governance Survey SURVEY RESULTS advisory managed services software solutions insights 2017 HBR Consulting LLC. All rights reserved. hbrconsulting.com info@hbrconsulting.com
Corporate Law Department Information Governance Survey SURVEY RESULTS advisory managed services software solutions insights 2017 HBR Consulting LLC. All rights reserved. hbrconsulting.com info@hbrconsulting.com
The Blue Sage Group. Sarbanes-Oxley. 404 Compliance Program. The Blue Sage Group
 The Blue Sage Group Sarbanes-Oxley 404 Compliance Program The Blue Sage Group Agenda The Blue Sage Group 404 Compliance Challenges Meeting the 404 Challenges TBSG 404 Compliance Program Assessment and
The Blue Sage Group Sarbanes-Oxley 404 Compliance Program The Blue Sage Group Agenda The Blue Sage Group 404 Compliance Challenges Meeting the 404 Challenges TBSG 404 Compliance Program Assessment and
Customer Support Group (CSG) Invoicing and Monitoring Arrangements. April 2016
 Internal Audit Customer Support Group (CSG) Invoicing and Monitoring Arrangements April 2016 Distributed to: Chief Operating Officer Commercial Director Director of Resources Head of Finance Partnership
Internal Audit Customer Support Group (CSG) Invoicing and Monitoring Arrangements April 2016 Distributed to: Chief Operating Officer Commercial Director Director of Resources Head of Finance Partnership
Beyond Compliance. Leveraging Internal Control to Build a Better Business: A Response to Sarbanes-Oxley Sections 302 and 404
 Beyond Compliance Leveraging Internal Control to Build a Better Business: A Response to Sarbanes-Oxley Sections 302 and 404 Note to Readers Regarding This First Edition April 2003: This document was published
Beyond Compliance Leveraging Internal Control to Build a Better Business: A Response to Sarbanes-Oxley Sections 302 and 404 Note to Readers Regarding This First Edition April 2003: This document was published
MANAGE RISK IN THE LEGAL DEPARTMENT
 MANAGE RISK IN THE LEGAL DEPARTMENT Legal departments in financial institutions face a unique set of challenges in managing the risks associated with their use of outside counsel and other third-party
MANAGE RISK IN THE LEGAL DEPARTMENT Legal departments in financial institutions face a unique set of challenges in managing the risks associated with their use of outside counsel and other third-party
Internal Auditing 101
 Internal Auditing 101 Presented By: Sam Capuano - Manager of Internal Audit, Wolf & Co. John Gallagher - Director of Internal Audit, SEFCU (NY) Barry Lucas - Internal Auditor, Desco FCU (Ohio) 1 Introductions
Internal Auditing 101 Presented By: Sam Capuano - Manager of Internal Audit, Wolf & Co. John Gallagher - Director of Internal Audit, SEFCU (NY) Barry Lucas - Internal Auditor, Desco FCU (Ohio) 1 Introductions
Intelligent automation and internal audit
 Intelligent automation and internal audit Adding value through governance, risk management, and controls Second article in the series kpmg.ch Contents Governing intelligent automation across the enterprise
Intelligent automation and internal audit Adding value through governance, risk management, and controls Second article in the series kpmg.ch Contents Governing intelligent automation across the enterprise
Performing a Successful Audit. Fundamentals of Auditing ERO Compliance Audit Process Jim Hughes Manager, Audit Assurance and Oversight
 Performing a Successful Audit Fundamentals of Auditing ERO Compliance Audit Process Jim Hughes Manager, Audit Assurance and Oversight Objectives At the end of this session, participants will be able to:
Performing a Successful Audit Fundamentals of Auditing ERO Compliance Audit Process Jim Hughes Manager, Audit Assurance and Oversight Objectives At the end of this session, participants will be able to:
Flying with IT through Market Turbulence
 IT ADVISORY Flying with IT through Market Turbulence ADVISORY Agenda Global Financial Crisis IT Strategies for Global Economic Recession IT Consolidation Software Asset Management 2 The GFC Global Financial
IT ADVISORY Flying with IT through Market Turbulence ADVISORY Agenda Global Financial Crisis IT Strategies for Global Economic Recession IT Consolidation Software Asset Management 2 The GFC Global Financial
Risk Management: Building an Integrated Program to Drive Business Value
 Risk Management: Building an Integrated Program to Drive Business Value Presenter s Name Saturday, September 24, 2011 Agenda Identify key forces impacting risk management Evaluate the maturity of your
Risk Management: Building an Integrated Program to Drive Business Value Presenter s Name Saturday, September 24, 2011 Agenda Identify key forces impacting risk management Evaluate the maturity of your
Case Study Webinar: Vendor Risk Management at Global Lending Services
 Case Study Webinar: Vendor Risk Management at Global Lending Services Al Palmer, SVP Compliance, Global Lending Services LLC (GLS) Melissa Brown, Compliance Manager, Global Lending Services LLC (GLS) John
Case Study Webinar: Vendor Risk Management at Global Lending Services Al Palmer, SVP Compliance, Global Lending Services LLC (GLS) Melissa Brown, Compliance Manager, Global Lending Services LLC (GLS) John
Management Excluded Job Description
 Management Excluded Job Description 1. Position Identification Position Number 993234 Position Title Department Reports to (title) Associate Director, Supply Management Purchasing Services Director, Purchasing
Management Excluded Job Description 1. Position Identification Position Number 993234 Position Title Department Reports to (title) Associate Director, Supply Management Purchasing Services Director, Purchasing
IIROC 2015 Financial Administrators Section Conference
 IIROC 2015 Financial Administrators Section Conference September 11, 2015 kpmg.ca Presenters Chris Cornell KPMG Partner, Financial Services Steven Sharma KPMG Partner, Financial Services 2 Agenda Current
IIROC 2015 Financial Administrators Section Conference September 11, 2015 kpmg.ca Presenters Chris Cornell KPMG Partner, Financial Services Steven Sharma KPMG Partner, Financial Services 2 Agenda Current
2014 Financial Services Supplier Risk Management Survey. Achieving balance
 2014 Financial Services Supplier Risk Management Survey Achieving balance 2 2014 Financial Services Supplier Risk Management Survey Achieving balance Contents About the survey 2 Introduction 3 Key themes
2014 Financial Services Supplier Risk Management Survey Achieving balance 2 2014 Financial Services Supplier Risk Management Survey Achieving balance Contents About the survey 2 Introduction 3 Key themes
CRISC EXAM PREP COURSE: SESSION 4
 CRISC EXAM PREP COURSE: SESSION 4 Job Practice 2 Copyright 2016 ISACA. All rights reserved. DOMAIN 4 RISK AND CONTROL MONITORING AND REPORTING Copyright 2016 ISACA. All rights reserved. Domain 4 Continuously
CRISC EXAM PREP COURSE: SESSION 4 Job Practice 2 Copyright 2016 ISACA. All rights reserved. DOMAIN 4 RISK AND CONTROL MONITORING AND REPORTING Copyright 2016 ISACA. All rights reserved. Domain 4 Continuously
CGEIT ITEM DEVELOPMENT GUIDE
 CGEIT ITEM DEVELOPMENT GUIDE Updated March 2017 TABLE OF CONTENTS Content Page Purpose of the CGEIT Item Development Guide 3 CGEIT Exam Structure 3 Writing Quality Items 3 Multiple-Choice Items 4 Steps
CGEIT ITEM DEVELOPMENT GUIDE Updated March 2017 TABLE OF CONTENTS Content Page Purpose of the CGEIT Item Development Guide 3 CGEIT Exam Structure 3 Writing Quality Items 3 Multiple-Choice Items 4 Steps
Board Audit Committee Training Automation of Audit Function. Anthony Wanyoike TeamMate Consulting East, Central & West Africa
 Board Audit Committee Training Automation of Audit Function Anthony Wanyoike TeamMate Consulting East, Central & West Africa Agenda 1. Automation of Audit Function Steps of developing automated Audit Operational
Board Audit Committee Training Automation of Audit Function Anthony Wanyoike TeamMate Consulting East, Central & West Africa Agenda 1. Automation of Audit Function Steps of developing automated Audit Operational
Translate stakeholder needs into strategy. Governance is about negotiating and deciding amongst different stakeholders value interests.
 Principles Principle 1 - Meeting stakeholder needs The governing body is ultimately responsible for setting the direction of the organisation and needs to account to stakeholders specifically owners or
Principles Principle 1 - Meeting stakeholder needs The governing body is ultimately responsible for setting the direction of the organisation and needs to account to stakeholders specifically owners or
See your auditor clearly. Transparency report: How we perform quality audit engagements
 See your auditor clearly. Transparency report: How we perform quality audit engagements February 2014 Table of contents 1) A message from the CEO and Managing Partner Assurance 2 2) Quality control policies
See your auditor clearly. Transparency report: How we perform quality audit engagements February 2014 Table of contents 1) A message from the CEO and Managing Partner Assurance 2 2) Quality control policies
San Francisco Chapter. Presented by Scott Perry - Slalom Consulting
 Presented by Scott Perry - Slalom Consulting Introductions Session Objectives Overview of Enterprise Risk Management The Role Of IT IT Governance Model IT Risk Assessment How IT Auditors Add Value Key
Presented by Scott Perry - Slalom Consulting Introductions Session Objectives Overview of Enterprise Risk Management The Role Of IT IT Governance Model IT Risk Assessment How IT Auditors Add Value Key
SOLUTION BRIEF RSA ARCHER REGULATORY & CORPORATE COMPLIANCE MANAGEMENT
 RSA ARCHER REGULATORY & CORPORATE COMPLIANCE MANAGEMENT INTRODUCTION Your organization s regulatory compliance landscape changes every day. In today s complex regulatory environment, governmental and industry
RSA ARCHER REGULATORY & CORPORATE COMPLIANCE MANAGEMENT INTRODUCTION Your organization s regulatory compliance landscape changes every day. In today s complex regulatory environment, governmental and industry
A PRACTICAL GUIDE TO GDPR BREACH NOTIFICATION AND SECURITY REQUIREMENTS
 SESSION ID: SEM-MO1 A PRACTICAL GUIDE TO GDPR BREACH NOTIFICATION AND SECURITY REQUIREMENTS Mahmood Sher-Jan CEO and President RADAR, Inc. @msherjan Julia Jacobson Partner K&L Gates, LLP Overview Key definitions
SESSION ID: SEM-MO1 A PRACTICAL GUIDE TO GDPR BREACH NOTIFICATION AND SECURITY REQUIREMENTS Mahmood Sher-Jan CEO and President RADAR, Inc. @msherjan Julia Jacobson Partner K&L Gates, LLP Overview Key definitions
External Quality Assurance Review of the Office of the Auditor General Proposed Statement of Work for the Audit Sub- Committee.
 External Quality Assurance Review of the Office of the Auditor General Proposed Statement of Work for the Audit Sub- Committee Proposed Statement of Work City of Ottawa May 17, 2011 Submitted by: PricewaterhouseCoopers
External Quality Assurance Review of the Office of the Auditor General Proposed Statement of Work for the Audit Sub- Committee Proposed Statement of Work City of Ottawa May 17, 2011 Submitted by: PricewaterhouseCoopers
Managing the Business Associate Relationship: From Onboarding to Breaches. March 27, 2016
 Managing the Business Associate Relationship: From Onboarding to Breaches March 27, 2016 HCCA s 21 st Annual Compliance Institute National Harbor, MD Today s Agenda Onboarding: Health care providers and
Managing the Business Associate Relationship: From Onboarding to Breaches March 27, 2016 HCCA s 21 st Annual Compliance Institute National Harbor, MD Today s Agenda Onboarding: Health care providers and
CERT Resilience Management Model, Version 1.2
 CERT Resilience Management Model, Organizational Process Focus (OPF) Richard A. Caralli Julia H. Allen David W. White Lisa R. Young Nader Mehravari Pamela D. Curtis February 2016 CERT Program Unlimited
CERT Resilience Management Model, Organizational Process Focus (OPF) Richard A. Caralli Julia H. Allen David W. White Lisa R. Young Nader Mehravari Pamela D. Curtis February 2016 CERT Program Unlimited
The Role of the VMO in Regulatory Compliance Planning, Due Diligence and Contract Negotiation
 : The Role of the VMO in Regulatory Compliance Planning, Due Diligence and Contract Negotiation David England, Director, ISG ISG WHITE PAPER 2017 Information Services Group, Inc. All Rights Reserved EXECUTIVE
: The Role of the VMO in Regulatory Compliance Planning, Due Diligence and Contract Negotiation David England, Director, ISG ISG WHITE PAPER 2017 Information Services Group, Inc. All Rights Reserved EXECUTIVE
Ohio Public Employees Retirement System. Request for Proposal
 Ohio Public Employees Retirement System For: Consulting Services for Development of the Business Intelligence & Analytics Office Date: 9/11/2017 Project Name: Business Intelligence & Analytics Program
Ohio Public Employees Retirement System For: Consulting Services for Development of the Business Intelligence & Analytics Office Date: 9/11/2017 Project Name: Business Intelligence & Analytics Program
Collaboration with Business Associates on Compliance
 Collaboration with Business Associates on Compliance HCCA Compliance Institute April 19, 2016 Balancing risk management, compliance responsibility and business growth Responsibility of entities as they
Collaboration with Business Associates on Compliance HCCA Compliance Institute April 19, 2016 Balancing risk management, compliance responsibility and business growth Responsibility of entities as they
