XenMobile Technology Overview
|
|
|
- Jack Carroll
- 6 years ago
- Views:
Transcription
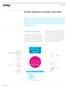
1 XenMobile Technology Overview XenMobile Technology Overview Mobility is a top priority for organizations. Why? Because more employees than ever before are demanding access to the apps and data that will make them productive on the go. But this isn t as easy as it was in the past. Now, employees want this access from any mobile device, including their own personal devices. In addition, the apps that people need to get their jobs done have expanded beyond mobile to include Windows, datacenter, web and native mobile apps. However, for IT, allowing users to access all of their apps and data from untrusted devices raises significant security and compliance concerns. Until now, there have been two main options for meeting users mobility requirements. IT could either secure and manage all those devices, apps and data with a complex array of point solutions, creating management headaches and security silos, or require people to use different devices for different activities, leading to user frustration. Enterprises needed an integrated approach that would allow people to be fully productive while addressing security and management concerns. Such a solution would enable IT to secure and manage mobile devices, apps and data from one centralized point, and set app and data policies based on device ownership, status or location. Users would be given secure access to , web and documents, and the ability to self-select the rest of their apps from a unified corporate app store all with a beautiful user experience on any device. This solution is XenMobile. XenMobile is a comprehensive solution for managing and protecting mobile devices, apps and data, and giving users the freedom to experience work and life their way. Its features include: Mobile device management (MDM) for configuring, securing, provisioning and supporting mobile devices Mobile app management (MAM) for complete management, security and control over native mobile apps and their associated data Sandboxed , browser and document sharing apps Unified corporate app store with the largest ecosystem of apps built for business Multi-factor single sign-on (SSO) As depicted in Figure 1, XenMobile is an end-to-end enterprise mobility management (EMM) solution. Citrix.com 1
2 Figure 1 End-to-end enterprise mobility management architecture The following sections detail how XenMobile, together with XenDesktop and XenApp, delivers these features and benefits. XenMobile Server/Service XenMobile is available on-prem as XenMobile Server hosted in an enterprise environment on XenServer, VMware ESXi, or Hyper-V hypervisors. It is also available in Citrix Cloud as XenMobile Service. XenMobile Service offers some distinct advantages such as: New features and bug fixes availability prior to on-prem releases Common management dashboard alongside all Citrix Cloud services Assisted web-based on-boarding process can have the XenMobile service up and running in a matter of hours Refocus IT staff time on other projects with upgrades and many operational management tasks offloaded by Citrix Cloud Ops Peace of mind with 99.9% uptime SLA Less infrastructure to implement and maintain Predictable budget with elastic pay-as-yougo SaaS subscription (Opex vs. Capex) Reduced subscription cost when Citrix services are packaged together However, both are from the same code base and ultimately provide the same functionality, therefore they will be referred to as XenMobile Server/Service throughout the paper. XenMobile Server/Service Overview XenMobile Server/Service provides rolebased management, configuration and security of corporate and user-owned devices. IT can enroll and manage devices, blacklist or whitelist apps, detect devices that are jailbroken or out of compliance and block their ActiveSync access, and perform a full or selective wipe of a device that is lost, stolen or out of compliance. With XenMobile Server / Service, IT can perform the following MDM actions: Configure Administrators configure both the XenMobile Server / Service and devices through a webbased administrative console. They can create groups directly or configure the solution to read an LDAP-compliant directory such as Microsoft Active Directory to import groups, user accounts and related properties. Note that LDAP integration is direct, meaning that each device-server interaction (e.g., device authentication, policy deployment) prompts a query to the directory. This is unlike solutions whose on-premises products sit in the DMZ and cache LDAP data in the product. Administrators can also configure XenMobile Server / Service to make requests to a central certificate authority such as Microsoft Certificate Services to enable certificate-based authentication for Wi-Fi, VPN and Exchange ActiveSync profiles. The solution acts as a 2
3 client to Microsoft Certificate Services and requests certificates on behalf of users with enrolled devices. In other environments, the administrator can accomplish this through the solution s Universal PKI mechanism, which will make a web services call to the PKI server. Administrators configure devices via a wizard-based configuration workflow in the administrative console. They can specify (based on operating system type, or version and patch levels, for example) which devices are permitted to enroll and receive policy profiles; designate devices as corporate- or BYOD (and, if they choose, upload corporate asset metadata from an asset or configuration management database); and configure platform- or OS-specific device settings such as passcodes, encryption, ActiveSync , Wi-Fi, VPN and PKI. If they choose, they can also deploy a certificate to the device for automatic access to Wi-Fi and other enterprise resources. IT can also restrict default apps and device resources, as well as blacklist or whitelist apps. Provision Administrators can provision access to users by finalizing and scheduling delivery of the profiles they create during the configuration process. They can make it easy for users to enroll their devices using self-service. They select the enrollment mode and method ( or SMS) to push the enrollment invitation to users. They can send out an invitation URL, enrollment PIN, enrollment password or any combination of the three. They also have the option of enrollment using derived credentials for ios devices. The derived credentials feature allows organizations, that use personal identity verification (PIV) smart cards, to derive a mobile credential and provide a highly secure form of identity with a great password free user experience. They can also specify whether users can use the self-help portal. Users can self-enroll either by downloading Secure Hub, a combined MDM and MAM agent, or upon receiving an invitation from the administrator. The user downloads the agent, accepts the terms and conditions and completes a wizard-based series of profile and certificate acceptances. If given access to the self-help portal, users access it via a web-based console and can perform basic functions such as enroll and locate, lock and wipe a device. Secure Besides configuring device security settings, IT can take further security actions in the event of loss, theft or user departure from the organization. These include the ability to locate, track and geo-fence devices, lock a device if it is lost, wipe a device if it is stolen and selectively wipe a BYO device if the user leaves the organization. The solution maintains an audit trail of administrator actions and integrates with security information and event management systems for threat correlation, forensic analysis and compliance reporting. Support IT can provide help desk functions and troubleshooting for mobile users. These include viewing mobile alerts and information via a one-click, interactive dashboard. IT can drill down into and remedy device issues individually or by group. Monitor and report IT can monitor and report on device and app inventory, device status and security, and compliance status. IT can also integrate log management and security information and event management systems by exporting logs in syslog format to those systems. This integration can be used to pull mobile activity into the threat picture during real-time network event analysis as well as for after-thefact auditing, such as reporting on administrator actions like device wipes. Decommission IT can decommission devices when they are lost, stolen or replaced, or upon user departure, in a secure fashion. The admin can do this either from the dashboard for a group of devices or in the devices tab for a single device. When a device is fully wiped, it is turned back to its factory settings and ready to be re-commissioned. When it is selectively wiped, the corporate profile and all associated apps (such as corporate and other apps that have been pushed or made available via the corporate unified app store) are removed. Besides being secure, this process is fully auditable for compliance purposes. IT can identify inactive devices, fully wipe corporate devices and selectively wipe BYO devices. Secure Hub Available for any mobile device, the Secure Hub app allows IT to enforce mobile settings and security while providing access to a unified app store and live support services. XenMobile communicates with Secure Hub to deliver device-specific policies and MDX-enabled app policies. When used with XenMobile, Secure Hub delivers the following key features: Single app for MDM and MAM Secure Hub is the single app that connects to Xen- Mobile for all MDM and MAM policies and app delivery. Using this single app, IT can secure and manage devices and corporate apps installed on the device. Unified app store With XenMobile Server/Service enumeration capabilities, Secure Hub displays all Windows, web, SaaS and mobile apps and data resources available to each user, subject to access policies (e.g., role within the organization, device type and status, and network conditions). Mobile, web and SaaS apps can be accessed within or outside Secure Hub on the device springboard. Self-service unified app store Users subscribe to individual resources by selecting them from the unified XenMobile app store. Apps appear in the store based on prescribed delivery groups which corresponds to domain group membership. Store apps may be further grouped into categories to easily identify them according to their function. Zero-touch update In the background, Secure Hub periodically checks for new policies, configuration changes and updates, most of which are implemented transparently. 3
4 Mobile app management XenMobile Server/Service also serves as the content provider/controller for an organization s ios, Android and HTML5 native mobile applications (including homegrown apps and those sourced from third parties). From a XenMobile perspective, this means that the SSO, app enumeration, user self-service and follow-me app capabilities will work for native mobile apps just as they do for a user s other resources. For instance, mobile apps will be displayed in Secure Hub alongside all of the user s virtualized Windows, web and SaaS apps. Additional new XenMobile Server/Service capabilities account for other unique characteristics of native mobile apps. For example, the enumeration process includes making Secure Hub aware of essential information related to the specified app, such as relevant policy data, the URL for package download and min/ max platform and device type requirements. Apps also may be containerized by wrapping them before being published. This wrapping process injects the code required to support management tasks and policy enforcement into mobile apps. It can be applied before compiling via the XenMobile App SDK delivered to the app developer. In this case, the developer would add two lines of code that allow XenMobile Server/Service to deliver a policy wrapper that the IT admin can configure to intercept app system calls, thereby enforcing policy at runtime. Alternatively, it can be applied to the app after compiling, which would create a new app. The former approach is more practical for third-party apps offered on public app stores, while the latter is better for non-public custom apps that have already been developed. XenMobile Server/Service is powered by MDX technologies, which enable complete management, security and control over native mobile apps and their associated data. With MDX, corporate apps and data reside in a container, separated from personal apps and data, on the user s mobile device. This containerization allows IT to secure any MDX-enabled application, such as custom developed, third-party or BYO mobile apps, with comprehensive policy-based controls, including mobile DLP and the ability to remote lock, wipe and encrypt apps and data. The XenMobile App SDX with MDX allows IT to: Separate business and personal apps and data in a mobile container where they can be secured with encryption and other mobile DLP technologies and can be remotely locked and wiped by IT. Provide seamless integration between MDX-enabled apps while controlling all communication policies, such as ensuring that data only is accessible by MDX-enabled apps. Provide granular, policy-based controls and management for HTML5 and native mobile apps, including an application-specific micro-vpn for accessing an organization s internal network. A micro-vpn avoids the need for a device-wide VPN that can compromise security. Following are examples of the control that can be exerted at common checkpoints during the lifecycle of the app (e.g., start-up, transition from background to foreground): Authentication forces logon via Secure Hub if the user is online and is not already logged on, or at the end of the application s lease when operating offline Authorization checks for user entitlement prior to app launch; wipes data and locks the app if the user is not entitled to it Offline lease policy controls duration (typically days) that an app can be used offline before the user must re-establish a connection with the app store App update policy forces an available app update to be performed or allows it to be deferred for a specified time Jailbroken policy specifies whether an app is allowed to run on a jailbroken device Data control policy controls what users can and can t do with data resident in the app, such as copy/paste Interaction between Secure Hub and MDX-enabled apps The XenMobile App SDK library is loaded by the MDX-enabled application to enforce the management tasks and policies listed above. Communications between the wrapped app and Secure Hub are as shown in Figure 2. Both the MDX-enabled app and Secure Hub share information, such as app policies, through the common authorization data store. This data is refreshed by Secure Hub after each successful app enumeration from XenMobile Server/Service, and remains persistent across reboot of the device. Secure mobile and browser applications Secure Mail and Secure Web native mobile apps are included in XenMobile Advanced and Enterprise Editions. Both apps can be wrapped and provisioned with an enterprise certificate and are also available on the Apple Store or Google Play Store. These apps respectively provide users with a secure native , calendar and contacts solution and a secure browser that can be encrypted and used based on IT-defined policies. Secure Mail and Secure Web give IT the assurance that corporate , web content and user data are secured within a container on the mobile device and can be wiped remotely at any time. An app-specific micro-vpn facilitates intranet connectivity for both Secure Mail and Secure Web. Citrix offers multiple options. While Secure Mail is the most secure option because it is fully contained. Secure Mail integrates seamlessly with Microsoft Exchange on-prem or with Office 365 in the cloud. XenMobile offers other productivity apps: Secure Notes - provide a business-class secure note taking application with and 4
5 calendar integration for streamlined mobile workflows ShareFile QuickEdit Provide an easy-touse editing tool on mobile devices, allowing employees to edit documents, spreadsheets and presentations Secure Tasks Provides an easy and secure way of tracking, managing, and editing your business to do list from a mobile device ShareConnect - Provide a secure remote access app that allows employees to access their desktops from mobile devices ShareFile integration ShareFile, which is included and seamlessly integrated with XenMobile Enterprise Edition, enables organizations to securely store, sync and share data within and outside the organization. Using ShareFile with XenMobile provides IT with enterprise directory (e.g., Active Directory) integration capabilities for easy, enterprise-wide provisioning and deployment of user accounts. The combined power of XenMobile and ShareFile enhances authentication and data security while giving users the freedom and flexibility to access, share and sync data on multiple devices. Additional user benefits include: Easy SSO access to corporate applications and data with Secure Hub Ability to view, edit, and annotate content with editors available on the device or with Windows applications hosted by XenApp for a rich content editing experience Seamless mobile access to enterprise data in the cloud or on-premises, including corporate network shares and Microsoft SharePoint Complete mobility with offline access to corporate data How ShareFile works ShareFile is an IT-managed, secure data sharing service that delivers enterprise-class capabilities. ShareFile provides robust reporting functionality that enables IT to perform Figure 2 Mobile application delivery via Secure Hub 5
6 comprehensive logging of user activity, downloads and usage notifications, as well as granular folder permissions to control and monitor how data is accessed and shared. The secure product architecture (Figure 3) is comprised of two components: Control Plane This system is responsible for maintaining user account information and brokering functions. This information is completely protected, encrypted and stored in the cloud StorageZones: This is where the data is hosted and is completely separate from the location of the control plane. The innovative ShareFile StorageZones feature gives IT the control and flexibility to securely store data on premises, in the cloud or a mixture of both. Cloud-based storage is hosted on Amazon Web Services (AWS) or Microsoft Azure with an option to use multiple datacenters in the United States, Canada, Ireland, Brazil, Japan, Australia and Singapore. The storage servers run on Amazon EC2 while the backend storage resides in Amazon S3. All files are encrypted in transit and at rest via SSL. The on-premises option allows IT to store data locally (entirely or partially) to meet unique compliance requirements, enhance performance by storing data in close proximity to the user and to build the most cost-effective solution. With the on-premises option, Citrix can support any CIFS based network storage system and enable access to existing on-premises file stores, such as Windows network shares and SharePoint, to eliminate the need for data migration. StorageZones can also be setup on an on-premises object store that supports AWS compatible S3 APIs. Additionally customers can also setup StorageZones on an AWS or Azure location that they manage themselves with a local cache residing on-premises. Using ShareFile with XenMobile While ShareFile and XenMobile can be sold separately, Citrix is delivering increasing levels of ShareFile functionality with each XenMobile edition. Using the two together delivers a mobile, collaborative and secure enterprise. Most importantly, using Share- File with XenMobile provides IT with Active Figure 3 ShareFile architecture with StorageZones 6
7 Directory integration capabilities for easy enterprise-wide provisioning, management and de-provisioning (including remote wipe) of ShareFile accounts and data. Additionally, users can log in to Secure Hub with their usual credentials (single- or multi-factor authentication) and access all their documents, in addition to their apps, in a single place. ShareFile Enteprise is included with XenMobile Enterprise. NetScaler Gateway NetScaler Gateway is a secure application and data access solution that gives administrators granular application- and data-level control while empowering users with remote access from anywhere. It provides a single point for managing access control and limiting actions within sessions based on both user identity and the endpoint device, leading to better application security, data protection and compliance. StoreFront XenMobile can utilize apps from XenApp and XenDesktop and make them available to mobile device users in the XenMobile Store. Users subscribe to the apps directly inside XenMobile Store and launch them from Secure Hub. Citrix Receiver must be installed on users' devices to launch the apps, but it does not need to be configured. To configure this setting, you need the fully qualified domain name (FQDN) or IP address and port number for the StoreFront server/(s). StoreFront manages the delivery of desktops and applications from XenApp, XenDesktop to users' devices. StoreFront enumerates and aggregates available desktops and applications into stores. Users access StoreFront stores through Citrix Receiver. StoreFront keeps a record of each user's applications and automatically updates their devices, ensuring users have a consistent experience as they roam between their smartphones, tablets, laptops, and desktop computers. StoreFront is an integral component of XenApp 7.x and XenDesktop 7.x but can be used with several versions of XenApp and XenDesktop. Conclusion XenMobile is a comprehensive solution for managing mobile devices, apps and data. Users receive single-touch access to all of their mobile, SaaS and Windows apps, including seamlessly integrated , browser, data sharing and support apps, from a unified corporate app store. IT gains control over mobile devices with full configuration, security, provisioning and support capabilities. In addition, XenMobile securely delivers XenMobile Apps, which are built for business. With XenMobile, IT can meet compliance requirements and control mobility needs while users enjoy the freedom to experience work and life their way. To learn more about how Citrix helps organizations balance employees desire for flexibility and a consistent experience with the security and control requirements of IT, access additional XenMobile resources on our website: Enterprise Sales North America Worldwide Locations Corporate Headquarters 851 Cypress Creek Road Fort Lauderdale, FL United States Silicon Valley 4988 Great America Parkway Santa Clara, CA United States Copyright 2016 Inc. All rights reserved. Citrix, the Citrix logo, and other marks appearing herein are property of Citrix Systems, Inc. and/or one or more of its subsidiaries, and may be registered with the U.S. Patent and Trademark Office and in other countries. All other marks are the property of their respective owner/s. 7
Secure app and data delivery for a mobile financial services workforce
 Secure app and data delivery for a mobile financial services workforce Secure, anywhere, any device productivity to transform the customer experience. Mobility can enable greater productivity for financial
Secure app and data delivery for a mobile financial services workforce Secure, anywhere, any device productivity to transform the customer experience. Mobility can enable greater productivity for financial
Citrix XenMobile. Rade Švraka MDS Informatički inženjering
 Citrix XenMobile Rade Švraka rsvraka@mds.rs www.mds.rs MDS Informatički inženjering EMM Enterprise Mobility Management Productivity and Collaboration Data Management App Management Device Management EMM
Citrix XenMobile Rade Švraka rsvraka@mds.rs www.mds.rs MDS Informatički inženjering EMM Enterprise Mobility Management Productivity and Collaboration Data Management App Management Device Management EMM
VMWARE WORKSPACE ONE + MICROSOFT OFFICE 365 : ENABLING MORE SECURE COLLABORATION. A Solution for Balancing Productivity with Protection
 WHITE PAPER JULY 2016 VMWARE WORKSPACE ONE + MICROSOFT OFFICE 365 : ENABLING MORE SECURE COLLABORATION A Solution for Balancing Productivity with Protection Table of Contents Introduction 3 The Evolution
WHITE PAPER JULY 2016 VMWARE WORKSPACE ONE + MICROSOFT OFFICE 365 : ENABLING MORE SECURE COLLABORATION A Solution for Balancing Productivity with Protection Table of Contents Introduction 3 The Evolution
INTEGRATING HORIZON AND CITRIX APPS IN A DIGITAL WORKSPACE
 INTEGRATING HORIZON AND CITRIX APPS IN A DIGITAL WORKSPACE Aligning Your Windows-Based Infrastructure for a Digital Workspace In today s enterprise, applications come in many different shapes and sizes.
INTEGRATING HORIZON AND CITRIX APPS IN A DIGITAL WORKSPACE Aligning Your Windows-Based Infrastructure for a Digital Workspace In today s enterprise, applications come in many different shapes and sizes.
AN EMM CHECKLIST FOR CIOs. Factors to Consider When Choosing an EMM Solution. Whitepaper
 1 AN EMM CHECKLIST FOR CIOs Factors to Consider When Choosing an EMM Solution Whitepaper 2 An EMM Checklist for CIOs As you decide on an Enterprise Mobility Management (EMM) solution, there are dozens,
1 AN EMM CHECKLIST FOR CIOs Factors to Consider When Choosing an EMM Solution Whitepaper 2 An EMM Checklist for CIOs As you decide on an Enterprise Mobility Management (EMM) solution, there are dozens,
IBM MaaS360 (SaaS) 1.1 IBM MaaS360 Mobile Device Management (SaaS) and IBM MaaS360 Mobile Device Management (SaaS) Step up for existing customers
 Service Description IBM MaaS360 (SaaS) This Service Description describes the Cloud Service IBM provides to Client. Client means the contracting party and its authorized users and recipients of the Cloud
Service Description IBM MaaS360 (SaaS) This Service Description describes the Cloud Service IBM provides to Client. Client means the contracting party and its authorized users and recipients of the Cloud
Workspace ONE. Insert Presenter Name. Empowering a Digital Workspace. Insert Presenter Title
 Workspace ONE Empowering a Digital Workspace Insert Presenter Name Insert Presenter Title Every dimension of our lives is GOING DIGITAL 2 Consumerization is driving DIGITAL TRANSFORMATION Modern Workforce
Workspace ONE Empowering a Digital Workspace Insert Presenter Name Insert Presenter Title Every dimension of our lives is GOING DIGITAL 2 Consumerization is driving DIGITAL TRANSFORMATION Modern Workforce
Top. Reasons Enterprises Select kiteworks by Accellion
 Top 10 Reasons Enterprises Select kiteworks by Accellion Accellion Enterprise Customers Include: Top 10 Reasons Enterprises Select kiteworks kiteworks by Accellion is the leading private cloud content
Top 10 Reasons Enterprises Select kiteworks by Accellion Accellion Enterprise Customers Include: Top 10 Reasons Enterprises Select kiteworks kiteworks by Accellion is the leading private cloud content
A Secure, IT-approved Alternative to Personal File Sharing Services in the Enterprise
 White Paper A Secure, IT-approved Alternative to Personal File Sharing Services in the Enterprise Protect business data. Gain secure IT oversight. Provide single point of access to enterprise data for
White Paper A Secure, IT-approved Alternative to Personal File Sharing Services in the Enterprise Protect business data. Gain secure IT oversight. Provide single point of access to enterprise data for
IT Enterprise Services
 IT Enterprise Services Enterprise Mobility Management...in the cloud. Powered by Is your enterprise mobile ready? The mobility challenge is on. By 2020 Gartner predict that 26 billion devices will be connected
IT Enterprise Services Enterprise Mobility Management...in the cloud. Powered by Is your enterprise mobile ready? The mobility challenge is on. By 2020 Gartner predict that 26 billion devices will be connected
Whitepaper Enterprise Mobile Manager
 Whitepaper Enterprise Mobile Manager OVERVIEW OnPremise or Cloud Based Mobile Management Solution The AppTec cloud based mobile management solution with its very intuitively operable management console
Whitepaper Enterprise Mobile Manager OVERVIEW OnPremise or Cloud Based Mobile Management Solution The AppTec cloud based mobile management solution with its very intuitively operable management console
SOLUTION BRIEF CA MANAGEMENT CLOUD FOR MOBILITY. Overview of CA Management Cloud for Mobility
 SOLUTION BRIEF CA MANAGEMENT CLOUD FOR MOBILITY Overview of CA Management Cloud for Mobility CA Management Cloud for Mobility from CA Technologies enables companies to create and manage their mobile environments,
SOLUTION BRIEF CA MANAGEMENT CLOUD FOR MOBILITY Overview of CA Management Cloud for Mobility CA Management Cloud for Mobility from CA Technologies enables companies to create and manage their mobile environments,
VMware AirWatch Enterprise Integration Service Guide EIS Server Installation and Integration
 VMware AirWatch Enterprise Integration Service Guide EIS Server Installation and Integration Workspace ONE UEM v9.5 Have documentation feedback? Submit a Documentation Feedback support ticket using the
VMware AirWatch Enterprise Integration Service Guide EIS Server Installation and Integration Workspace ONE UEM v9.5 Have documentation feedback? Submit a Documentation Feedback support ticket using the
VMware AirWatch Enterprise Integration Service Guide EIS Server Installation and Integration
 VMware AirWatch Enterprise Integration Service Guide EIS Server Installation and Integration Workspace ONE UEM v9.6 Have documentation feedback? Submit a Documentation Feedback support ticket using the
VMware AirWatch Enterprise Integration Service Guide EIS Server Installation and Integration Workspace ONE UEM v9.6 Have documentation feedback? Submit a Documentation Feedback support ticket using the
NetScaler Management and Analytics System (MAS)
 Data Sheet NetScaler Management and Analytics System (MAS) NetScaler MAS provides centralized network management, analytics, automation, and orchestration to support applications deployed across hybrid
Data Sheet NetScaler Management and Analytics System (MAS) NetScaler MAS provides centralized network management, analytics, automation, and orchestration to support applications deployed across hybrid
Sean P. McDonough National Office 365 Solution Manager Cardinal Solutions Group
 Sean P. McDonough National Office 365 Solution Manager Cardinal Solutions Group 2 A little about me Sean P. McDonough National Office 365 Solution Manager Responsible for business productivity (primarily
Sean P. McDonough National Office 365 Solution Manager Cardinal Solutions Group 2 A little about me Sean P. McDonough National Office 365 Solution Manager Responsible for business productivity (primarily
ENTERPRISE MOBILITY MANAGEMENT: REAL BENEFITS IN TODAY S MOBILE WORLD
 ENTERPRISE MOBILITY MANAGEMENT: REAL BENEFITS IN TODAY S MOBILE WORLD i TABLE OF CONTENTS Meeting the Challenges of Today s Mobile Business Imperative...1 Enterprise Mobility Management 1. Enables End
ENTERPRISE MOBILITY MANAGEMENT: REAL BENEFITS IN TODAY S MOBILE WORLD i TABLE OF CONTENTS Meeting the Challenges of Today s Mobile Business Imperative...1 Enterprise Mobility Management 1. Enables End
IBM United States Software Announcement , dated July 26, 2016
 IBM United States Software Announcement 216-013, dated July 26, 2016 IBM MaaS360 launches four new suites, offering key enterprise mobility management capabilities in purpose-focused bundles to improve
IBM United States Software Announcement 216-013, dated July 26, 2016 IBM MaaS360 launches four new suites, offering key enterprise mobility management capabilities in purpose-focused bundles to improve
GO BEYOND MOBILE DEVICE MANAGEMENT WITH A DIGITAL WORKSPACE WHITE PAPER
 GO BEYOND MOBILE DEVICE MANAGEMENT WITH A DIGITAL WORKSPACE WHITE PAPER Table of Contents On Its Own, Mobile Device Management Can t Deliver on Modern Demands 3 Two Challenges, Two Solutions 3 Mobile Device
GO BEYOND MOBILE DEVICE MANAGEMENT WITH A DIGITAL WORKSPACE WHITE PAPER Table of Contents On Its Own, Mobile Device Management Can t Deliver on Modern Demands 3 Two Challenges, Two Solutions 3 Mobile Device
IBM Terms of Use SaaS Specific Offering Terms. IBM MaaS360 (SaaS) 1. IBM SaaS
 IBM Terms of Use SaaS Specific Offering Terms IBM MaaS360 (SaaS) The Terms of Use ( ToU ) is composed of this IBM Terms of Use - SaaS Specific Offering Terms ( SaaS Specific Offering Terms ) and a document
IBM Terms of Use SaaS Specific Offering Terms IBM MaaS360 (SaaS) The Terms of Use ( ToU ) is composed of this IBM Terms of Use - SaaS Specific Offering Terms ( SaaS Specific Offering Terms ) and a document
Enterprise Mobility: Are You Ready?
 Enterprise Mobility: Are You Ready? of time, money and labor in deploying web-based, business-critical desktop applications. In recent years, the IT landscape has expanded to include a multitude of mobile
Enterprise Mobility: Are You Ready? of time, money and labor in deploying web-based, business-critical desktop applications. In recent years, the IT landscape has expanded to include a multitude of mobile
Future-proof your mobility strategy with Dell Enterprise Mobility Management
 Future-proof your mobility strategy with Dell Enterprise Mobility Management Change is the only constant in the mobile workforce landscape. Changes in mobile device technology are leading the way. Smartphone,
Future-proof your mobility strategy with Dell Enterprise Mobility Management Change is the only constant in the mobile workforce landscape. Changes in mobile device technology are leading the way. Smartphone,
BlackBerry Offerings for Desktop Windows 10 and macos
 BlackBerry Offerings for Desktop Windows 10 and macos Enable secure remote connectivity from any computer. Securely browse intranets and web apps. Email, calendar, contacts, files including offline availability.
BlackBerry Offerings for Desktop Windows 10 and macos Enable secure remote connectivity from any computer. Securely browse intranets and web apps. Email, calendar, contacts, files including offline availability.
IT Management, Simplified. Real-&me IT management solu&ons for the new speed of business
 IT Management, Simplified Real-&me IT management solu&ons for the new speed of business IT Management, Simplified Enterprise IT management so:ware division of Zoho Corpora&on Founded in 1996 as AdventNet
IT Management, Simplified Real-&me IT management solu&ons for the new speed of business IT Management, Simplified Enterprise IT management so:ware division of Zoho Corpora&on Founded in 1996 as AdventNet
VDI. Citrix Cloud Services Adrian Fish
 VDI Citrix Cloud Services 1 Citrix Cloud Services & How this changes how you deliver IT 2 About Citrix Cloud Citrix Cloud is a delivery and management platform that enables faster set up and time-to-value
VDI Citrix Cloud Services 1 Citrix Cloud Services & How this changes how you deliver IT 2 About Citrix Cloud Citrix Cloud is a delivery and management platform that enables faster set up and time-to-value
Anywhere Access to ERP Applications with Parallels RAS. White Paper Parallels Remote Application Server 2018
 Anywhere Access to ERP Applications with Parallels RAS White Paper Parallels Remote Application Server 2018 Table of Contents Introduction... 3... 3 Centralized Management Reduces Cost and Complexity...
Anywhere Access to ERP Applications with Parallels RAS White Paper Parallels Remote Application Server 2018 Table of Contents Introduction... 3... 3 Centralized Management Reduces Cost and Complexity...
INTEGRATING PING IDENTITY SOLUTIONS WITH GOOGLE IDENTITY SERVICES
 INTEGRATING PING IDENTITY SOLUTIONS WITH GOOGLE IDENTITY SERVICES How two technologies work together to add more value to your enterprise TABLE OF CONTENTS 03 04 05 06 07 08 08 08 EXECUTIVE SUMMARY INTEGRATION
INTEGRATING PING IDENTITY SOLUTIONS WITH GOOGLE IDENTITY SERVICES How two technologies work together to add more value to your enterprise TABLE OF CONTENTS 03 04 05 06 07 08 08 08 EXECUTIVE SUMMARY INTEGRATION
"Charting the Course... MOC B Planning for and Managing Devices in the Enterprise: Enterprise Mobility Suite (EMS) and On-Premises Tools
 Description Course Summary This course teaches IT professionals how to use the Enterprise Mobility Suite to manage devices, users, and data. In addition, this course teaches students how to use other technologies,
Description Course Summary This course teaches IT professionals how to use the Enterprise Mobility Suite to manage devices, users, and data. In addition, this course teaches students how to use other technologies,
Administering System Center Configuration Manager and Intune (696)
 Administering System Center Configuration Manager and Intune (696) Deploy and manage virtual applications Prepare virtual applications Sequence applications, install and configure the sequencer environment,
Administering System Center Configuration Manager and Intune (696) Deploy and manage virtual applications Prepare virtual applications Sequence applications, install and configure the sequencer environment,
IBM Canada Ltd. Software Announcement A , dated July 26, 2016
 IBM Canada Ltd. Software Announcement A16-0026, dated July 26, 2016 IBM MaaS360 launches four new suites, offering key enterprise mobility management capabilities in purpose-focused bundles to improve
IBM Canada Ltd. Software Announcement A16-0026, dated July 26, 2016 IBM MaaS360 launches four new suites, offering key enterprise mobility management capabilities in purpose-focused bundles to improve
Mobile Application Management
 Kony Write Once, Run Everywhere Mobile Technology WHITE PAPER July 2012 Meeting the BYOD challenge with next-generation application and device management Overview... 3 The Challenge... 4 MAM Functions...
Kony Write Once, Run Everywhere Mobile Technology WHITE PAPER July 2012 Meeting the BYOD challenge with next-generation application and device management Overview... 3 The Challenge... 4 MAM Functions...
Reduce the time & labor to process and archive documents. Reduce document cycle times. Create audit trails of document handling activities
 NashuaDocs NashuaDocs works for you: Reduce costs Reduce the time & labor to process and archive documents Minimise shipping costs Enhance productivity Reduce document cycle times Improve accuracy Ensure
NashuaDocs NashuaDocs works for you: Reduce costs Reduce the time & labor to process and archive documents Minimise shipping costs Enhance productivity Reduce document cycle times Improve accuracy Ensure
SOLUTION BRIEF MOBILE SECURITY. Securely Accelerate Your Mobile Business
 SOLUTION BRIEF MOBILE SECURITY Securely Accelerate Your Mobile Business SOLUTION BRIEF CA DATABASE MANAGEMENT FOR DB2 FOR z/os DRAFT CA Technologies allows you to accelerate mobile innovation for customers
SOLUTION BRIEF MOBILE SECURITY Securely Accelerate Your Mobile Business SOLUTION BRIEF CA DATABASE MANAGEMENT FOR DB2 FOR z/os DRAFT CA Technologies allows you to accelerate mobile innovation for customers
VMWARE WORKSPACE ONE. Consumer Simple. Enterprise Secure. APPS AND IDENTITY DESKTOP MOBILE MANAGEMENT AND SECURITY.
 DATASHEET VMWARE WORKSPACE ONE Consumer Simple. Enterprise Secure. AT A GLANCE VMware Workspace ONE is the enterprise platform that enables IT to deliver a digital workspace that empowers the workforce
DATASHEET VMWARE WORKSPACE ONE Consumer Simple. Enterprise Secure. AT A GLANCE VMware Workspace ONE is the enterprise platform that enables IT to deliver a digital workspace that empowers the workforce
Why EMS? What benefit does EMS provide O365 customers. Manage Mobile Productivity. deployment. SaaS Apps. LOB Apps. Mobility Management
 Why EMS? What benefit does EMS provide O365 customers LOB Apps SaaS Apps Mobility Management Simplify app delivery and deployment Manage Mobile Productivity Increase IT Productivity Consistent experience
Why EMS? What benefit does EMS provide O365 customers LOB Apps SaaS Apps Mobility Management Simplify app delivery and deployment Manage Mobile Productivity Increase IT Productivity Consistent experience
Best-of-Breed Enterprise Mac Management
 WHITE PAPER Best-of-Breed Enterprise Mac Management Choose the right tool for the job. A decade ago, Mac was an uncommon sight in many businesses and routinely ignored by corporate IT but times have changed.
WHITE PAPER Best-of-Breed Enterprise Mac Management Choose the right tool for the job. A decade ago, Mac was an uncommon sight in many businesses and routinely ignored by corporate IT but times have changed.
Remote Monitoring and Management
 Remote Monitoring and Management Continuum RMM dramatically increases your operational efficiency. Our intuitive, SaaS-based management portal allows you to easily backup, monitor, troubleshoot, and maintain
Remote Monitoring and Management Continuum RMM dramatically increases your operational efficiency. Our intuitive, SaaS-based management portal allows you to easily backup, monitor, troubleshoot, and maintain
IBM MaaS360 Content Suite
 IBM MaaS360 Content Suite Distribute, protect and edit documents on mobile devices Key benefits Protect corporate documents from data leaks with containerization Safely suppport BYOD and increase employee
IBM MaaS360 Content Suite Distribute, protect and edit documents on mobile devices Key benefits Protect corporate documents from data leaks with containerization Safely suppport BYOD and increase employee
BUSINESS DRIVERS AND USE CASES REVISED 5 NOVEMBER 2018
 BUSINESS DRIVERS AND USE CASES REVISED 5 NOVEMBER 2018 Table of Contents Business Drivers and Use Cases Addressing Business Requirements Use Cases GUIDE 2 VMware Workspace ONE Cloud-Based Reference Architecture
BUSINESS DRIVERS AND USE CASES REVISED 5 NOVEMBER 2018 Table of Contents Business Drivers and Use Cases Addressing Business Requirements Use Cases GUIDE 2 VMware Workspace ONE Cloud-Based Reference Architecture
Enterprise Mobility Suite
 Enterprise Mobility Suite (EMS) MEEC-Team David Pearlman-Director Enterprise Mobility US Education David.Pearlman@microsoft.com 74% of higher education CIOs say mobility and BYOD has increased as strategic
Enterprise Mobility Suite (EMS) MEEC-Team David Pearlman-Director Enterprise Mobility US Education David.Pearlman@microsoft.com 74% of higher education CIOs say mobility and BYOD has increased as strategic
VMware helps keep employees connected and protected virtually anywhere
 VMware helps keep employees connected and protected virtually anywhere Consumer grade simplicity. Enterprise grade security. Key market trend The rapid adoption of modern applications (SaaS apps, mobile
VMware helps keep employees connected and protected virtually anywhere Consumer grade simplicity. Enterprise grade security. Key market trend The rapid adoption of modern applications (SaaS apps, mobile
x76484 Desk hours - 8:30 AM - 8:00 PM Eastern
 1-800-456-8000 x76484 Citrix-Licensing@ingrammicro.com Desk hours - 8:30 AM - 8:00 PM Eastern www.mycitrix.com Vendor Program Overview Citrix desktop, application and server virtualization, as well as
1-800-456-8000 x76484 Citrix-Licensing@ingrammicro.com Desk hours - 8:30 AM - 8:00 PM Eastern www.mycitrix.com Vendor Program Overview Citrix desktop, application and server virtualization, as well as
Achieving True Enterprise Mobility:
 December 2011 Achieving True Enterprise Mobility: MDM Is Only Half the Battle Sponsored by Fiberlink Contents Introduction 1 Security, Scale, and Simplicity 1 A Tale of Two Mobile Management Paradigms
December 2011 Achieving True Enterprise Mobility: MDM Is Only Half the Battle Sponsored by Fiberlink Contents Introduction 1 Security, Scale, and Simplicity 1 A Tale of Two Mobile Management Paradigms
Disclaimer This presentation may contain product features that are currently under development. This overview of new technology represents no commitme
 UEM1859BU Be a Power Admin: VMware AirWatch Console Tips and Tricks Adarsh Kesari Senior Systems Engineer #VMworld #UEM1859BU Disclaimer This presentation may contain product features that are currently
UEM1859BU Be a Power Admin: VMware AirWatch Console Tips and Tricks Adarsh Kesari Senior Systems Engineer #VMworld #UEM1859BU Disclaimer This presentation may contain product features that are currently
Deliver a cloud strategy that works for your business and your workforce
 Deliver a cloud strategy that works for your business and your workforce Use an integrated, cloud-hosted digital workspace to make users more productive, simplify IT, and ensure the security and agility
Deliver a cloud strategy that works for your business and your workforce Use an integrated, cloud-hosted digital workspace to make users more productive, simplify IT, and ensure the security and agility
VMware helps keep employees connected and protected virtually anywhere
 VMware helps keep employees connected and protected virtually anywhere Consumer grade simplicity. Enterprise grade security. Key market trend The rapid adoption of modern applications (SaaS apps, mobile
VMware helps keep employees connected and protected virtually anywhere Consumer grade simplicity. Enterprise grade security. Key market trend The rapid adoption of modern applications (SaaS apps, mobile
MOBILIZING HEALTHCARE WITH VMWARE AND GOOGLE
 SPONSORED BY WHITE PAPER MOBILIZING HEALTHCARE WITH VMWARE AND GOOGLE Mobility plays a significant role in enabling healthcare organizations to provide excellent patient care and improved financial outcomes.
SPONSORED BY WHITE PAPER MOBILIZING HEALTHCARE WITH VMWARE AND GOOGLE Mobility plays a significant role in enabling healthcare organizations to provide excellent patient care and improved financial outcomes.
VMware helps keep employees connected and protected virtually anywhere
 VMware helps keep employees connected and protected virtually anywhere Consumer grade simplicity. Enterprise grade security. Key market trend The rapid adoption of modern applications (SaaS apps, mobile
VMware helps keep employees connected and protected virtually anywhere Consumer grade simplicity. Enterprise grade security. Key market trend The rapid adoption of modern applications (SaaS apps, mobile
MDM & MAM with. Microsoft Intune. Daanish Antulay Enterprise Mobility Specialist, APAC
 MDM & MAM with Microsoft Intune Daanish Antulay Enterprise Mobility Specialist, APAC 52% 90% >80% 52% of information workers across 17 countries report using three or more devices for work* 90% of enterprises
MDM & MAM with Microsoft Intune Daanish Antulay Enterprise Mobility Specialist, APAC 52% 90% >80% 52% of information workers across 17 countries report using three or more devices for work* 90% of enterprises
Enterprise Mobility Suite
 Enterprise Mobility Suite EMS is a suite of products from Microsoft that allows individuals to work outside of their office with peace of mind for both themselves and their employer that company data is
Enterprise Mobility Suite EMS is a suite of products from Microsoft that allows individuals to work outside of their office with peace of mind for both themselves and their employer that company data is
Embracing the Digital Workplace with Desktop Management Solutions
 Embracing the Digital Workplace with Desktop Management Solutions 1 Contents + INTRODUCTION + MEETING TODAY S ELEVATED SELF-SERVICE EXPECTATIONS + THE FRAMEWORK OF THE MODERN, USER-FOCUSED WORKSPACE +
Embracing the Digital Workplace with Desktop Management Solutions 1 Contents + INTRODUCTION + MEETING TODAY S ELEVATED SELF-SERVICE EXPECTATIONS + THE FRAMEWORK OF THE MODERN, USER-FOCUSED WORKSPACE +
VMWARE HORIZON 7. End-User Computing Today. Horizon 7: Delivering Desktops and Applications as a Service
 DATASHEET VMWARE 7 AT A GLANCE 7 delivers virtualized or hosted desktops and applications through a single platform to end users. These desktop and application services including RDS hosted apps, packaged
DATASHEET VMWARE 7 AT A GLANCE 7 delivers virtualized or hosted desktops and applications through a single platform to end users. These desktop and application services including RDS hosted apps, packaged
Turn your conversations into memorable conversations by learning how to showcase Dynamics CRM Online value proposition to Technical Decision Makers.
 The Technical Brief provides answers to key Technical Decision Maker questions and/or concerns in topics such as: Extensibility Security Deployment and Management Integration Application Architecture Collaboration
The Technical Brief provides answers to key Technical Decision Maker questions and/or concerns in topics such as: Extensibility Security Deployment and Management Integration Application Architecture Collaboration
OneList Approvals Technical Overview
 OneList Approvals Technical Overview V 3.8 April 2015 Contents 1. OneList Approvals... 3 1.1. What is OneList...3 1.2. Key business benefits of OneList...4 1.3. Key features of OneList...5 1.4. How does
OneList Approvals Technical Overview V 3.8 April 2015 Contents 1. OneList Approvals... 3 1.1. What is OneList...3 1.2. Key business benefits of OneList...4 1.3. Key features of OneList...5 1.4. How does
HOW TO UNLOCK EMS. 3 Things You Need to Know to Capitalize on Enterprise Mobility Suite for Manufacturing
 HOW TO UNLOCK EMS 3 Things You Need to Know to Capitalize on Enterprise Mobility Suite for Manufacturing 1. KEY COMPONENTS There are four primary components to the Enterprise Mobility Suite (EMS). EMS
HOW TO UNLOCK EMS 3 Things You Need to Know to Capitalize on Enterprise Mobility Suite for Manufacturing 1. KEY COMPONENTS There are four primary components to the Enterprise Mobility Suite (EMS). EMS
MOBILE DEVICE MANAGEMENT SHOOTOUT AUGUST 31, 2015
 MOBILE DEVICE MANAGEMENT SHOOTOUT AUGUST 31, 2015 Scott Rolf, CIO, Tucker Ellis, LLP Jeff Baslaw, Senior Manager of Network Engineering and Operations, Ropes & Gray Rich Lilly, Cloud & Datacenter Evangelist,
MOBILE DEVICE MANAGEMENT SHOOTOUT AUGUST 31, 2015 Scott Rolf, CIO, Tucker Ellis, LLP Jeff Baslaw, Senior Manager of Network Engineering and Operations, Ropes & Gray Rich Lilly, Cloud & Datacenter Evangelist,
Accelerate Healthcare Transformation and Clinician Workflows with a Secure Digital Workspace
 Accelerate Healthcare Transformation and Clinician Workflows with a Secure Digital Workspace Give clinicians the mobility they need to provide better care without impacting security. Citrix.com White Paper
Accelerate Healthcare Transformation and Clinician Workflows with a Secure Digital Workspace Give clinicians the mobility they need to provide better care without impacting security. Citrix.com White Paper
Designing Enterprise Mobility
 Designing Enterprise Mobility Cortado Corporate Server One Solution for All Enterprise Mobility Challenges Mobile Device Management Based on Active Directory Mobile Application Management for all Apps
Designing Enterprise Mobility Cortado Corporate Server One Solution for All Enterprise Mobility Challenges Mobile Device Management Based on Active Directory Mobile Application Management for all Apps
System and Server Requirements
 System and Server Requirements January 2019 For GreeneStep ERP, CRM, Ecommerce, Customer/Supplier Collaboration, Management Dashboards and Web Access Products Suite ON-PREMISE DEPLOYMENT MODEL & HOSTED
System and Server Requirements January 2019 For GreeneStep ERP, CRM, Ecommerce, Customer/Supplier Collaboration, Management Dashboards and Web Access Products Suite ON-PREMISE DEPLOYMENT MODEL & HOSTED
A Mobile Device Management Comparison: Office 365, Intune, and Enterprise Mobility Suite Tuesday August 11 th 2015
 A Mobile Device Management Comparison: Office 365, Intune, and Enterprise Mobility Suite Tuesday August 11 th 2015 Seven Thousand Two-Hundred and Ninety-Three Companies use MessageOps Software We do business
A Mobile Device Management Comparison: Office 365, Intune, and Enterprise Mobility Suite Tuesday August 11 th 2015 Seven Thousand Two-Hundred and Ninety-Three Companies use MessageOps Software We do business
SysTrack Workspace Analytics
 SysTrack Workspace Analytics The Visibility IT Needs to Enable End-User Productivity Challenge IT executives are under constant pressure to cost-effectively manage complex IT systems. SysTrack enables
SysTrack Workspace Analytics The Visibility IT Needs to Enable End-User Productivity Challenge IT executives are under constant pressure to cost-effectively manage complex IT systems. SysTrack enables
Integrating MDM and Cloud Services with System Center Configuration Manager
 Integrating MDM and Cloud Services with System Center Configuration Course 20703-2A 3 Days Instructor-led, Hands on Course Information This is a three-day Instructor Led Training (ILT) course that describes
Integrating MDM and Cloud Services with System Center Configuration Course 20703-2A 3 Days Instructor-led, Hands on Course Information This is a three-day Instructor Led Training (ILT) course that describes
AppSheet: Design and Architecture
 AppSheet: Design and Architecture ABSTRACT This white paper introduces the design and architecture of the AppSheet platform. Readers will gain an understanding of the AppSheet operating infrastructure,
AppSheet: Design and Architecture ABSTRACT This white paper introduces the design and architecture of the AppSheet platform. Readers will gain an understanding of the AppSheet operating infrastructure,
VDI and Beyond: Addressing Top IT Challenges to Drive Agility and Growth
 VDI and Beyond: Addressing Top IT Challenges to Drive Agility and Growth Citrix XenDesktop with FlexCast mobilizes the modern workforce App and Desktop virtualization can be a powerful driver of business
VDI and Beyond: Addressing Top IT Challenges to Drive Agility and Growth Citrix XenDesktop with FlexCast mobilizes the modern workforce App and Desktop virtualization can be a powerful driver of business
What Do You Need to Ensure a Successful Transition to IoT?
 What Do You Need to Ensure a Successful Transition to IoT? As the business climate grows ever more competitive, industrial companies are looking to the Internet of Things (IoT) to provide the business
What Do You Need to Ensure a Successful Transition to IoT? As the business climate grows ever more competitive, industrial companies are looking to the Internet of Things (IoT) to provide the business
BACSOFT IOT PLATFORM: A COMPLETE SOLUTION FOR ADVANCED IOT AND M2M APPLICATIONS
 BACSOFT IOT PLATFORM: A COMPLETE SOLUTION FOR ADVANCED IOT AND M2M APPLICATIONS What Do You Need to Ensure a Successful Transition to IoT? As the business climate grows ever more competitive, industrial
BACSOFT IOT PLATFORM: A COMPLETE SOLUTION FOR ADVANCED IOT AND M2M APPLICATIONS What Do You Need to Ensure a Successful Transition to IoT? As the business climate grows ever more competitive, industrial
Disclaimer This presentation may contain product features that are currently under development. This overview of new technology represents no commitme
 UEM1798BU The ROI Driver: Transition from Cost Center to Business Driver with AirWatch for Windows 10 VMworld 2017 Content: Not for publication Jason Roszak #VMworld #UEM1798BU Disclaimer This presentation
UEM1798BU The ROI Driver: Transition from Cost Center to Business Driver with AirWatch for Windows 10 VMworld 2017 Content: Not for publication Jason Roszak #VMworld #UEM1798BU Disclaimer This presentation
From... to cloud ready in less than one day with Parallels and ThinPrint
 RAS Solution Guide Parallels Remote Application Server From... to cloud ready in less than one day with Parallels and ThinPrint Business Challenges Mobility, security and compliance, automation, and the
RAS Solution Guide Parallels Remote Application Server From... to cloud ready in less than one day with Parallels and ThinPrint Business Challenges Mobility, security and compliance, automation, and the
Basic. $5/user per mo.
 Product Suite Intelligent office suite Secure cloud-based file storage per user 30 GB Unlimited Unlimited Access across devices (computer, phone, or tablet) Works without an Internet connection Compatible
Product Suite Intelligent office suite Secure cloud-based file storage per user 30 GB Unlimited Unlimited Access across devices (computer, phone, or tablet) Works without an Internet connection Compatible
Securely Enabling the Enterprise of Things
 Securely Enabling the Enterprise of Things Trust in BlackBerry Almost every product in Blackberry s bag of tricks directly or by extension is addressing the challenges of managing a diverse set of IoT
Securely Enabling the Enterprise of Things Trust in BlackBerry Almost every product in Blackberry s bag of tricks directly or by extension is addressing the challenges of managing a diverse set of IoT
End-User Computing for the Mobile-Cloud Era
 EUC3319-S End-User Computing for the Mobile-Cloud Era Sumit Dhawan, VMware, Inc Kit Colbert, VMware, Inc Ben Goodman, VMware, Inc Harry Labana, VMware, Inc John Marshall, AirWatch by VMware Disclaimer
EUC3319-S End-User Computing for the Mobile-Cloud Era Sumit Dhawan, VMware, Inc Kit Colbert, VMware, Inc Ben Goodman, VMware, Inc Harry Labana, VMware, Inc John Marshall, AirWatch by VMware Disclaimer
FIVE IMPORTANT BUYING CRITERIA TO ENABLE A TOTALLY MOBILE WORKFORCE WHITE PAPER APRIL 2018
 FIVE IMPORTANT BUYING CRITERIA TO ENABLE A TOTALLY MOBILE WORKFORCE WHITE PAPER APRIL 2018 Table of Contents Introduction.... 3 Why This Paper?.... 3 Why a Digital Workspace?.... 4 Buying Criterion 1:
FIVE IMPORTANT BUYING CRITERIA TO ENABLE A TOTALLY MOBILE WORKFORCE WHITE PAPER APRIL 2018 Table of Contents Introduction.... 3 Why This Paper?.... 3 Why a Digital Workspace?.... 4 Buying Criterion 1:
Administering Microsoft System Center Configuration Manager and Cloud Services Integration (beta) (703)
 Administering Microsoft System Center Configuration Manager and Cloud Services Integration (beta) (703) Configure and Maintain a Configuration Manager Management Infrastructure Configure the management
Administering Microsoft System Center Configuration Manager and Cloud Services Integration (beta) (703) Configure and Maintain a Configuration Manager Management Infrastructure Configure the management
Help safeguard your mobile inventories and extend the reach of your workforce.
 Help safeguard your mobile inventories and extend the reach of your workforce. Features Fast user configuration from a single console Policy customization and administration Lock/Wipe lost or stolen devices
Help safeguard your mobile inventories and extend the reach of your workforce. Features Fast user configuration from a single console Policy customization and administration Lock/Wipe lost or stolen devices
VMware Workspace ONE Intelligence Dashboards, Automation, and Reports Integrated Insights, App Analytics, and Automation
 VMware Workspace ONE Intelligence Dashboards, Automation, and Reports Integrated Insights, App Analytics, and Automation Workspace ONE UEM v9.4 Have documentation feedback? Submit a Documentation Feedback
VMware Workspace ONE Intelligence Dashboards, Automation, and Reports Integrated Insights, App Analytics, and Automation Workspace ONE UEM v9.4 Have documentation feedback? Submit a Documentation Feedback
: Integrating MDM and Cloud Services with System Center Configuration Manager
 20703-2: Integrating MDM and Cloud Services with System Center Configuration Manager Overview This is a three-day Instructor Led Training (ILT) course that describes mobile device management (MDM) technologies
20703-2: Integrating MDM and Cloud Services with System Center Configuration Manager Overview This is a three-day Instructor Led Training (ILT) course that describes mobile device management (MDM) technologies
Unlock the benefits of mobility to work faster, better, and smarter
 Unlock the benefits of mobility to work faster, better, and smarter Potential benefits Mac OS, Windows 10, ios, and Android management available Multi-OS Security Effective data security and compliance
Unlock the benefits of mobility to work faster, better, and smarter Potential benefits Mac OS, Windows 10, ios, and Android management available Multi-OS Security Effective data security and compliance
A crash course in Microsoft 365 Business. Achieve more in your business with an integrated security, management and productivity solution all in one.
 A crash course in Microsoft 365 Business Achieve more in your business with an integrated security, management and productivity solution all in one. Introduction You know that your business s growth depends
A crash course in Microsoft 365 Business Achieve more in your business with an integrated security, management and productivity solution all in one. Introduction You know that your business s growth depends
A crash course in Microsoft 365 Business. Achieve more in your business with an integrated security, management and productivity solution all in one.
 A crash course in Microsoft 365 Business Achieve more in your business with an integrated security, management and productivity solution all in one. Introduction You know that your business s growth depends
A crash course in Microsoft 365 Business Achieve more in your business with an integrated security, management and productivity solution all in one. Introduction You know that your business s growth depends
IBM MobileFirst Protect (SaaS)
 IBM Terms of Use SaaS Specific Offering Terms IBM MobileFirst Protect (SaaS) The Terms of Use ( ToU ) is composed of this IBM Terms of Use - SaaS Specific Offering Terms ( SaaS Specific Offering Terms
IBM Terms of Use SaaS Specific Offering Terms IBM MobileFirst Protect (SaaS) The Terms of Use ( ToU ) is composed of this IBM Terms of Use - SaaS Specific Offering Terms ( SaaS Specific Offering Terms
THINK YOU NEED A BYO STRATEGY? THINK AGAIN. Shift to a Digital Workspace Strategy in 5 Steps
 THINK YOU NEED A BYO STRATEGY? THINK AGAIN. Shift to a Digital Workspace Strategy in 5 Steps Your BYO Strategy Isn t Necessary Anymore Bring Your Own Device (BYO) strategies have been common in IT organizations
THINK YOU NEED A BYO STRATEGY? THINK AGAIN. Shift to a Digital Workspace Strategy in 5 Steps Your BYO Strategy Isn t Necessary Anymore Bring Your Own Device (BYO) strategies have been common in IT organizations
iphone and ipad Management
 A COMPREHENSIVE GUIDE iphone and ipad Management FOR BEGINNERS According to a recent survey, when given the choice 3 out of 4 employees choose an ios device over an Android device. 2 As Apple device numbers
A COMPREHENSIVE GUIDE iphone and ipad Management FOR BEGINNERS According to a recent survey, when given the choice 3 out of 4 employees choose an ios device over an Android device. 2 As Apple device numbers
CTERA Enterprise File Sync and Share (EFSS) - CTERA Overview
 PRODUCT DESCRIPTIONS CTERA Enterprise File Sync and Share (EFSS) - CTERA Overview CTERA s Enterprise File Sync and Share (EFSS) lets state workers store and access their files with the convenience of the
PRODUCT DESCRIPTIONS CTERA Enterprise File Sync and Share (EFSS) - CTERA Overview CTERA s Enterprise File Sync and Share (EFSS) lets state workers store and access their files with the convenience of the
Do More with Complete Mobile-Cloud Security from MobileIron Access
 Do More with Complete Mobile-Cloud Security from MobileIron Access MobileIron Access: Complete cloud-based security Comprehensive security. MobileIron Access leverages device and app posture, user identity,
Do More with Complete Mobile-Cloud Security from MobileIron Access MobileIron Access: Complete cloud-based security Comprehensive security. MobileIron Access leverages device and app posture, user identity,
Oracle Cloud for the Enterprise John Mishriky Director, NAS Strategy & Business Development
 % Oracle Cloud for the Enterprise John Mishriky Director, NAS Strategy & Business Development john.mishriky@oracle.com Right Solution. Right Time. What We Built An Enterprise Cloud An integrated platform
% Oracle Cloud for the Enterprise John Mishriky Director, NAS Strategy & Business Development john.mishriky@oracle.com Right Solution. Right Time. What We Built An Enterprise Cloud An integrated platform
REVISED 5 NOVEMBER 2018 SERVICE DEFINITIONS
 REVISED 5 NOVEMBER 2018 Table of Contents Service Definitions Workspace ONE Use Case Services Horizon Cloud Service on Microsoft Azure Use Case Services Recovery Services GUIDE 2 VMware Workspace ONE Cloud-Based
REVISED 5 NOVEMBER 2018 Table of Contents Service Definitions Workspace ONE Use Case Services Horizon Cloud Service on Microsoft Azure Use Case Services Recovery Services GUIDE 2 VMware Workspace ONE Cloud-Based
Empower 3 Feature Release 2. New Features. Mr. Jose Wilson Castro Latin America Informatics Director Waters Corporation 1
 Empower 3 Feature Release 2 New Features Mr. Jose Wilson Castro Latin America Informatics Director 2016 Waters Corporation 1 Agenda : Empower 3 FR2 Branding Refresh Technology updates Feature Updates o
Empower 3 Feature Release 2 New Features Mr. Jose Wilson Castro Latin America Informatics Director 2016 Waters Corporation 1 Agenda : Empower 3 FR2 Branding Refresh Technology updates Feature Updates o
REVISED 6 NOVEMBER 2018 COMPONENT DESIGN: WORKSPACE ONE INTELLIGENCE
 REVISED 6 NOVEMBER 2018 COMPONENT DESIGN: WORKSPACE ONE INTELLIGENCE Table of Contents Component Design: Workspace ONE Intelligence Architecture Scalability and Availability Databases Workspace ONE Intelligence
REVISED 6 NOVEMBER 2018 COMPONENT DESIGN: WORKSPACE ONE INTELLIGENCE Table of Contents Component Design: Workspace ONE Intelligence Architecture Scalability and Availability Databases Workspace ONE Intelligence
Mobility, Smart Devices, BYOD Do You Have a Solution & Strategy?
 Steven Scheurmann- Sales Leader, Asia Pacific & Japan, Endpoint & Mobility 스마트보안 Mobility, Smart Devices, BYOD Do You Have a Solution & Strategy? Mobile is an enterprise priority Growth in Internet Connected
Steven Scheurmann- Sales Leader, Asia Pacific & Japan, Endpoint & Mobility 스마트보안 Mobility, Smart Devices, BYOD Do You Have a Solution & Strategy? Mobile is an enterprise priority Growth in Internet Connected
Thru. Secure File Sync And Share - For The Enterprise
 Thru Secure File Sync And Share - For The Enterprise An Introduction Built exclusively for the business user and enterprises, Thru is an end to end file sharing and collaboration solution, that not only
Thru Secure File Sync And Share - For The Enterprise An Introduction Built exclusively for the business user and enterprises, Thru is an end to end file sharing and collaboration solution, that not only
Desktop Activity Intelligence
 Desktop Activity Intelligence Table of Contents Cicero Discovery Delivers Activity Intelligence... 1 Cicero Discovery Modules... 1 System Monitor... 2 Session Monitor... 3 Activity Monitor... 3 Business
Desktop Activity Intelligence Table of Contents Cicero Discovery Delivers Activity Intelligence... 1 Cicero Discovery Modules... 1 System Monitor... 2 Session Monitor... 3 Activity Monitor... 3 Business
Features to meet any requirement
 Storage and Retrieval Find any document instantly Store all of your electronic and scanned documentation in a secure, electronic repository that is accessible anywhere and at any time. Documents can be
Storage and Retrieval Find any document instantly Store all of your electronic and scanned documentation in a secure, electronic repository that is accessible anywhere and at any time. Documents can be
Device and Application Management: Windows 10 versus macos High Sierra and ios 11
 Device and Application Management: Windows 10 versus macos High Sierra and ios 11 Manageability Feature and Functionality Comparison April 2018 THE DEVELOPMENT OF THIS WHITE PAPER WAS SPONSORED BY MICROSOFT.
Device and Application Management: Windows 10 versus macos High Sierra and ios 11 Manageability Feature and Functionality Comparison April 2018 THE DEVELOPMENT OF THIS WHITE PAPER WAS SPONSORED BY MICROSOFT.
The Hybrid Enterprise: Working Across On-premises, IaaS, PaaS and SaaS
 The Hybrid Enterprise: Working Across On-premises, IaaS, PaaS and SaaS Rob Aragao & Stan Wisseman #MicroFocusCyberSummit Primary Goal of Businesses Today Drive Digital Transformation!! 2 For Most Organizations,
The Hybrid Enterprise: Working Across On-premises, IaaS, PaaS and SaaS Rob Aragao & Stan Wisseman #MicroFocusCyberSummit Primary Goal of Businesses Today Drive Digital Transformation!! 2 For Most Organizations,
Cisco Enterprise Mobility Services Platform (EMSP)
 Data Sheet Cisco Enterprise Mobility Services Platform (EMSP) Product Overview The Cisco Enterprise Mobility Services Platform (EMSP) is a holistic mobile software platform. It unifies the development,
Data Sheet Cisco Enterprise Mobility Services Platform (EMSP) Product Overview The Cisco Enterprise Mobility Services Platform (EMSP) is a holistic mobile software platform. It unifies the development,
Five customers deliver virtual desktops and apps to empower a modern workforce
 Five customers deliver virtual desktops and apps to empower a modern workforce Using Citrix XenDesktop with FlexCast technology to deliver the right experience to every user. 2 Application and desktop
Five customers deliver virtual desktops and apps to empower a modern workforce Using Citrix XenDesktop with FlexCast technology to deliver the right experience to every user. 2 Application and desktop
SAP Jam Collaboration, advanced plus edition
 March 2018 Cloud Service Specification Sheet SAP Jam Collaboration, advanced plus edition SAP Jam Collaboration delivers collaboration where you work, connecting customers, partners, and colleagues with
March 2018 Cloud Service Specification Sheet SAP Jam Collaboration, advanced plus edition SAP Jam Collaboration delivers collaboration where you work, connecting customers, partners, and colleagues with
IT MEGATRENDS - PART 3:
 C L O U D IT MEGATRENDS - PART 3: LEVERAGING WORKSPACES TO DELIGHT END USERS, SAVE COST AND CREATE TANGIBLE CUSTOMER VALUE AN ASG WHITE PAPER BY TORSTEN VOLK, ASG VICE PRESIDENT OF PRODUCT MANAGEMENT -
C L O U D IT MEGATRENDS - PART 3: LEVERAGING WORKSPACES TO DELIGHT END USERS, SAVE COST AND CREATE TANGIBLE CUSTOMER VALUE AN ASG WHITE PAPER BY TORSTEN VOLK, ASG VICE PRESIDENT OF PRODUCT MANAGEMENT -
SAP Jam Collaboration, enterprise edition
 Dec 2017 SAP Jam Collaboration, enterprise edition Cloud Service Specification Sheet SAP Jam Collaboration delivers collaboration where you work, connecting customers, partners, and colleagues with information,
Dec 2017 SAP Jam Collaboration, enterprise edition Cloud Service Specification Sheet SAP Jam Collaboration delivers collaboration where you work, connecting customers, partners, and colleagues with information,
BEST PRACTICES: DEPLOYING SPOK MOBILE WITH ENTERPRISE MOBILITY MANAGMENT. spok.com
 SM BEST PRACTICES: DEPLOYING SPOK MOBILE WITH ENTERPRISE MOBILITY MANAGMENT 1 DEPLOYING SPOK MOBILE WITH ENTEPRISE MOBILITY MANAGMENT Scalability and adoption are significant challenges that IT professionals
SM BEST PRACTICES: DEPLOYING SPOK MOBILE WITH ENTERPRISE MOBILITY MANAGMENT 1 DEPLOYING SPOK MOBILE WITH ENTEPRISE MOBILITY MANAGMENT Scalability and adoption are significant challenges that IT professionals
