Training for CSIRT staff
|
|
|
- Megan Lloyd
- 6 years ago
- Views:
Transcription
1 Training for CSIRT staff Andrew Cormack, Jacques Schuurman, Claudia Natanson, Wilfried Woeber, Gareth Price TF-CSIRT
2 CSIRT staff are different Not just sysadmins Not just network techies Though we take both of those for granted Or learn them elsewhere Filling in the gaps is important
3 Target Audience Members of new teams New members of existing teams Assumed already to know how the Internet works Course teaches how it breaks Based in Europe CERT-CC series of 3&4 day courses in USA
4 Course Objectives Students should learn Tasks involved in operating a CSIRT Skills needed by CSIRT staff Tools and techniques of incident response Need for links with other organisations
5 Course Modules Legal Issues Organisational Issues Technical Issues Market Issues Operational Issues Systems Issues
6 Legal Issues Rules & laws Harmonisation Jurisdiction Powers of investigation Contacts with law enforcement Access to and use of restricted tools
7 Organisational Issues Your ISP Your constituency Assets and risks Risk management Security policy templates For your customers For your team RFC2350 Public functions Press contacts Sister organisations FIRST etc. Staffing issues
8 Technical Issues Operating Systems About the OS Network stacks Vulnerabilities & back doors Integrity Forensics & Data mining Networks IP/ICMP TCP/UDP Higher level protocols Masquerading & hijacking Encryption Certificates & PKI
9 Market Issues Vendors Commercial teams Security bulletins Undisclosed vulnerabilities Other sources of information
10 Operational Issues An operational framework Incident response Reporting templates Tracking & Bookkeeping Taxonomy Management reports Other activities Trust brokers Finding contacts Other (reliable) sources of information
11 Systems Issues Recovery Monitor Audit Other activities
12 Back To Basics address and telephone number operating hours (9 to 5, 24 x 7 x 365) publicity for these three items guidance on what to do somewhere for them to work people to react to messages a customer
13 Building Access levels and hours of access Access Control Locks Alarm - intrusion, fire Guard - access control and visitor management Cameras Power
14 Office Lock Alarm Camera Secured area Separate area for servers, backups, forensic, secure store
15 Furniture Locks - key, code or combination Desks, workbenchs, racking Pedestals Filing Cabinets Security tethers for expensive hardware
16 Welfare Heating - working hours Lighting - DSE Health and Safety - arriving, working and leaving Catering - canteen or machines Cleaning - monitored or clear desk
17 - access, using mail, using pgp Multi-user access, audit Connected to local network or standalone Internet connected
18 Telephone Number Free or paid Automatic Call Diversion PBX, DEL backup answer phone, divert incoming and outgoing on separate lines handsfree, wirefree, mobile
19 Reporting Templates Paper for faxing or snail-mailing Scripts/Forms for telephone calls Web-based - to Web-based - direct into database
20 Work Management Off the shelf or custom Get as much automation as you can afford Application - access, admin, using Internet or Local Network only
21 Performance Monitoring And Reports Terms of Reference/Charter/Contract (RFC2350) Reporting agreements Memos of Understanding Service Level Agreements Work monitoring Reports Quality related work
22 Finding Contacts Regular TF-CSIRT FIRST Per Incident ARIN, RIPE, APNIC TF-CSIRT FIRST
23 Trust Brokers TI FIRST
24 Transferring incident information Reporting templates Taxonomy
25 Reliable Information Sources Other (reliable) sources of information
26 Course format Modular to ease delivery and maintenance Modules include Presentations Workshops Discussion Full course takes two days Allows informal discussion in evening
27 Progress and plans Initial development by TF-CSIRT sub-group Draft syllabus for discussion in January 2001 Development of modules by community Perhaps professional advice for legal section! Aim for delivery during 2001
CSIRT Staff and Staffing. October 10 12, Republic of Guinee. By Marcus K. G. Adomey
 CSIRT Staff and Staffing October 10 12, 2016 - Republic of Guinee By Marcus K. G. Adomey OVERVIEW CSIRT Staffing CSIRT Cost and Funding CSIRT Operation CSIRT Staffing CERT STAFFING What type of staff does
CSIRT Staff and Staffing October 10 12, 2016 - Republic of Guinee By Marcus K. G. Adomey OVERVIEW CSIRT Staffing CSIRT Cost and Funding CSIRT Operation CSIRT Staffing CERT STAFFING What type of staff does
Creating a Computer Security Incident Response Team Action Plan
 Creating a Computer Security Incident Response Team CERT Training and Education Networked Systems Survivability Software Engineering Institute Carnegie Mellon University This material is approved for public
Creating a Computer Security Incident Response Team CERT Training and Education Networked Systems Survivability Software Engineering Institute Carnegie Mellon University This material is approved for public
[14] Business Impact Analysis Document - Template
![[14] Business Impact Analysis Document - Template [14] Business Impact Analysis Document - Template](/thumbs/95/122794307.jpg) [14] Business Impact Analysis Document - Template Risk Assessment Descriptors: Use the descriptors below to assess the LIKELIHOOD of a risk occurring Score 5 4 3 2 1 Descriptor Probable Possible Unlikely
[14] Business Impact Analysis Document - Template Risk Assessment Descriptors: Use the descriptors below to assess the LIKELIHOOD of a risk occurring Score 5 4 3 2 1 Descriptor Probable Possible Unlikely
ACCESS CONTROL SOLUTIONS
 ACCESS CONTROL SOLUTIONS ACCESS CONTROL If you need a high level of control over who is entering your building and want to know when people have entered, our state of the art electronic locking systems
ACCESS CONTROL SOLUTIONS ACCESS CONTROL If you need a high level of control over who is entering your building and want to know when people have entered, our state of the art electronic locking systems
YOUR INNOVATIOn
 Dell OEM Industry Solutions YOUR INNOVATIOn Your solution Dell Powered To learn more about how Dell OEM Solutions can help you simplify your OEM operations, visit www.dell.eu/oem or contact our business
Dell OEM Industry Solutions YOUR INNOVATIOn Your solution Dell Powered To learn more about how Dell OEM Solutions can help you simplify your OEM operations, visit www.dell.eu/oem or contact our business
IT Plan Instructions for FY18-FY19
 IT Plan Instructions for FY18-FY19 Introduction and General Instructions The information technology plan for FY18-FY19 is web-enabled. You can navigate to the various sections of your agency s plan by
IT Plan Instructions for FY18-FY19 Introduction and General Instructions The information technology plan for FY18-FY19 is web-enabled. You can navigate to the various sections of your agency s plan by
NIMBUS Security & Surveillance Solutions Designing Solutions That Protect
 Address Suites 6, 2nd Floor, Evacuee Trust Complex, Sir Agha Khan Road, F-5/1, Islamabad Phone & Fax +92 51 999 111 333 +92 51 999 111 333 Email & Website info@companyname.com www.companyname.com Facebook
Address Suites 6, 2nd Floor, Evacuee Trust Complex, Sir Agha Khan Road, F-5/1, Islamabad Phone & Fax +92 51 999 111 333 +92 51 999 111 333 Email & Website info@companyname.com www.companyname.com Facebook
INNLINE HOSPITALITY VOICE MESSAGING
 INNLINE HOSPITALITY VOICE MESSAGING INNLINE VOICE MESSAGING FOR THE HOSPITALITY & LODGING INDUSTRIES Since 1990, InnLine has been the preferred voice messaging solution for lodging properties of all sizes.
INNLINE HOSPITALITY VOICE MESSAGING INNLINE VOICE MESSAGING FOR THE HOSPITALITY & LODGING INDUSTRIES Since 1990, InnLine has been the preferred voice messaging solution for lodging properties of all sizes.
Comparing Cost of Ownership: Symantec Managed PKI Service vs. On-Premise Software
 Comparing Cost of Ownership: Symantec Managed PKI Service vs. On-Premise Software Who should read this paper Deploying and managing a PKI solution can be a complex undertaking. This is particularly the
Comparing Cost of Ownership: Symantec Managed PKI Service vs. On-Premise Software Who should read this paper Deploying and managing a PKI solution can be a complex undertaking. This is particularly the
IT OPERATIONS ANALYST (12202) ( )
 GENERAL DESCRIPTION OF WORK Positions in this class provide support for a number services which may include distributed platforms, mainframe, and network. Those services include monitoring distributed
GENERAL DESCRIPTION OF WORK Positions in this class provide support for a number services which may include distributed platforms, mainframe, and network. Those services include monitoring distributed
Cyber Security Programme Outline for Apprenticeships at Level 4
 Cyber Security Programme Outline for Apprenticeships at Level 4 2018 Who we are ELATT is one of the top Tech apprenticeship providers in Greater London, bringing the best quality training into existing
Cyber Security Programme Outline for Apprenticeships at Level 4 2018 Who we are ELATT is one of the top Tech apprenticeship providers in Greater London, bringing the best quality training into existing
Benefits by user. Security Manager. Facilities Manager. Administrator. Occupants and Visitors
 Protect & Detect What we do We provide all of the elements you need for a risk free environment. Our access control and CCTV systems offer the convenience of installation, billing and maintenance, from
Protect & Detect What we do We provide all of the elements you need for a risk free environment. Our access control and CCTV systems offer the convenience of installation, billing and maintenance, from
FDS Service Catalogue
 FDS Service Catalogue Document Number: 33-03-007 Version Version Date Revised By Description Filename 1.0 01-04-2017 Adrie Kreder Final release Service Catalogue FDS-DXC 1.0.docx FDS Netherlands FDS-DXC
FDS Service Catalogue Document Number: 33-03-007 Version Version Date Revised By Description Filename 1.0 01-04-2017 Adrie Kreder Final release Service Catalogue FDS-DXC 1.0.docx FDS Netherlands FDS-DXC
IT Managed Services. Agenda
 IT Managed Services Agenda Introduction IT Challenges Problems with Traditional Approaches What is Managed Services The Benefits of Managed Services How it Works Q & A 517.323.7500 1 IT Challenges No Structured
IT Managed Services Agenda Introduction IT Challenges Problems with Traditional Approaches What is Managed Services The Benefits of Managed Services How it Works Q & A 517.323.7500 1 IT Challenges No Structured
ITEM REMOVED PDA023 DATE REMOVED 14:08:14 TIME REMOVED 9:30AM FAULT CODE NONE. Intelligent Lockers. Solutions for total asset management
 ITEM REMOVED PDA023 USER D.SMITH DATE REMOVED 14:08:14 TIME REMOVED 9:30AM FAULT CODE NONE Intelligent Lockers Solutions for total asset management Innovative Management Solutions Recognized as global
ITEM REMOVED PDA023 USER D.SMITH DATE REMOVED 14:08:14 TIME REMOVED 9:30AM FAULT CODE NONE Intelligent Lockers Solutions for total asset management Innovative Management Solutions Recognized as global
: Integrating MDM and Cloud Services with System Center Configuration Manager
 20703-2: Integrating MDM and Cloud Services with System Center Configuration Manager Overview This is a three-day Instructor Led Training (ILT) course that describes mobile device management (MDM) technologies
20703-2: Integrating MDM and Cloud Services with System Center Configuration Manager Overview This is a three-day Instructor Led Training (ILT) course that describes mobile device management (MDM) technologies
As an example of an IT consultant career we are going to have a short look at business systems analysts.
 1 An Information Technology consultant or analyst is someone who partners with clients to help them use information technology to improve the structure and efficiency of their IT systems, in order to meet
1 An Information Technology consultant or analyst is someone who partners with clients to help them use information technology to improve the structure and efficiency of their IT systems, in order to meet
Data Protection Workshop FSSU Training June 2016 by Bernadette Kinsella, JMB
 Data Protection Workshop FSSU Training June 2016 by Bernadette Kinsella, JMB The presentation material remains the intellectual property of the Joint Managerial Body. For further use/distribution, please
Data Protection Workshop FSSU Training June 2016 by Bernadette Kinsella, JMB The presentation material remains the intellectual property of the Joint Managerial Body. For further use/distribution, please
DISASTER MANAGEMENT AND RECOVERY
 DISASTER MANAGEMENT AND RECOVERY BUSINESS CONTINUITY AND DISASTER MANAGEMENT PLANNING TEMPLATE TO RESPOND EFFECTIVELY TO COMMUNITY NEEDS, COMMUNITY-BASED ORGANISATIONS (CBOS) NEED TO FOCUS ON BUSINESS
DISASTER MANAGEMENT AND RECOVERY BUSINESS CONTINUITY AND DISASTER MANAGEMENT PLANNING TEMPLATE TO RESPOND EFFECTIVELY TO COMMUNITY NEEDS, COMMUNITY-BASED ORGANISATIONS (CBOS) NEED TO FOCUS ON BUSINESS
PERSONAL DATA SECURITY GUIDANCE FOR MICROENTERPRISES UNDER THE GDPR
 PERSONAL DATA SECURITY GUIDANCE FOR MICROENTERPRISES UNDER THE GDPR The General Data Protection Regulation ( the GDPR ) significantly increases the obligations and responsibilities of organisations and
PERSONAL DATA SECURITY GUIDANCE FOR MICROENTERPRISES UNDER THE GDPR The General Data Protection Regulation ( the GDPR ) significantly increases the obligations and responsibilities of organisations and
Information, Privacy and Archives Division. Government of Ontario Function-Based Common Records Series: Information Technology
 Information, Privacy and Archives Division Government of Ontario Function-Based Common Records Series: Information Technology December 2014 December 2014 Page 2 of 22 INFORMATION TECHNOLOGY FUNCTION ACRONYM:
Information, Privacy and Archives Division Government of Ontario Function-Based Common Records Series: Information Technology December 2014 December 2014 Page 2 of 22 INFORMATION TECHNOLOGY FUNCTION ACRONYM:
Food Defense Supplier Guidelines
 Food Defense Supplier Guidelines Revised: May 2015 Table of Contents Introduction 3 1. Program administration 3 a. Plan management 3 b. Roles and responsibilities 3 c. Reporting procedures 3 d. Self-assessments
Food Defense Supplier Guidelines Revised: May 2015 Table of Contents Introduction 3 1. Program administration 3 a. Plan management 3 b. Roles and responsibilities 3 c. Reporting procedures 3 d. Self-assessments
IT OPERATIONS ANALYST (12202) ( )
 GENERAL DESCRIPTION OF WORK Positions in this class provide support for a number services which may include distributed platforms, mainframe, and network. Those services include monitoring distributed
GENERAL DESCRIPTION OF WORK Positions in this class provide support for a number services which may include distributed platforms, mainframe, and network. Those services include monitoring distributed
Security solutions White paper. Effectively manage access to systems and information to help optimize integrity and facilitate compliance.
 Security solutions White paper Effectively manage access to systems and information to help optimize integrity and facilitate compliance. March 2007 Contents 2 Overview 3 Answer key questions related to
Security solutions White paper Effectively manage access to systems and information to help optimize integrity and facilitate compliance. March 2007 Contents 2 Overview 3 Answer key questions related to
Administering System Center Configuration Manager and Intune (NI114) 40 Hours
 Administering System Center Configuration Manager and Intune (NI114) 40 Hours Outline Get expert instruction and hands-on practice configuring and managing clients and devices by using Microsoft System
Administering System Center Configuration Manager and Intune (NI114) 40 Hours Outline Get expert instruction and hands-on practice configuring and managing clients and devices by using Microsoft System
INFORMATION TECHNOLOGY PROGRAM DESCRIPTIONS OPERATIONAL INVESTMENTS
 EB-00-0 Exhibit D Tab Schedule - Page of INFORMATION TECHNOLOGY PROGRAM DESCRIPTIONS OPERATIONAL INVESTMENTS 0 INFRASTRUCTURE PRODUCTIVITY PROGRAM Program Overview Productivity projects enhance or enable
EB-00-0 Exhibit D Tab Schedule - Page of INFORMATION TECHNOLOGY PROGRAM DESCRIPTIONS OPERATIONAL INVESTMENTS 0 INFRASTRUCTURE PRODUCTIVITY PROGRAM Program Overview Productivity projects enhance or enable
Simplification is in our DNA We are dedicated to helping you reclaim your time and resources through IT simplification.
 FULLY INTEGRATED COMMUNICATIONS UNIFIED COMMUNICATIONS, THE DELL WAY SIMPLIFYING IT Simplifying your data center can help transform your organization. By reducing cost and complexity, you can devote more
FULLY INTEGRATED COMMUNICATIONS UNIFIED COMMUNICATIONS, THE DELL WAY SIMPLIFYING IT Simplifying your data center can help transform your organization. By reducing cost and complexity, you can devote more
Sarbanes-Oxley Compliance Kit
 Kit February 2018 This product is NOT FOR RESALE or REDISTRIBUTION in any physical or electronic format. The purchaser of this template has acquired the rights to use it for a SINGLE Disaster Recovery
Kit February 2018 This product is NOT FOR RESALE or REDISTRIBUTION in any physical or electronic format. The purchaser of this template has acquired the rights to use it for a SINGLE Disaster Recovery
UnifiedIT Solutions for Corporateorganisation. May 2007
 1 UnifiedIT Solutions for Corporateorganisation May 2007 2 Introduction Challenges of Corporate organisation today Communicate in real time Make sure communications are always secured and operational Centralise
1 UnifiedIT Solutions for Corporateorganisation May 2007 2 Introduction Challenges of Corporate organisation today Communicate in real time Make sure communications are always secured and operational Centralise
TELESTE S-AWARE. Situational awareness and incident management solution
 TELESTE S-AWARE Situational awareness and incident management solution TELESTE S-AWARE YOUR KEY TO SHARPER DECISION-MAKING Security and operations control systems, such as video surveillance systems, are
TELESTE S-AWARE Situational awareness and incident management solution TELESTE S-AWARE YOUR KEY TO SHARPER DECISION-MAKING Security and operations control systems, such as video surveillance systems, are
Action List for Developing a Computer Security Incident Response Team (CSIRT)
 Action List for Developing a Computer Security Incident Response Team (CSIRT) This document provides a high-level overview of actions to take and topics to address when planning and implementing a Computer
Action List for Developing a Computer Security Incident Response Team (CSIRT) This document provides a high-level overview of actions to take and topics to address when planning and implementing a Computer
Sine Qua Non. Jennifer Bayuk, CISA, CISM, CGEIT Independent Information Security Consultant Jennifer L Bayuk LLC 1
 Sine Qua Non Jennifer Bayuk, CISA, CISM, CGEIT Independent Information Security Consultant www.bayuk.com Jennifer L Bayuk LLC 1 Security Metrics Security Goals Security Process Information and LAN Systems
Sine Qua Non Jennifer Bayuk, CISA, CISM, CGEIT Independent Information Security Consultant www.bayuk.com Jennifer L Bayuk LLC 1 Security Metrics Security Goals Security Process Information and LAN Systems
Creating a Computer Security Incident Response Team Attendee Workbook
 Creating a Computer Security Incident Response Team Attendee Workbook CERT Training and Education Networked Systems Survivability Software Engineering Institute Carnegie Mellon University This material
Creating a Computer Security Incident Response Team Attendee Workbook CERT Training and Education Networked Systems Survivability Software Engineering Institute Carnegie Mellon University This material
Position Description. Senior Systems Administrator. Purpose and Scope
 Position Description Senior Systems Administrator Purpose and Scope The Senior Systems Administrator - is responsible for effective provisioning, installation, configuration, operation, and maintenance
Position Description Senior Systems Administrator Purpose and Scope The Senior Systems Administrator - is responsible for effective provisioning, installation, configuration, operation, and maintenance
icharge PMS Middleware, Integration and Call Accounting
 icharge PMS Middleware, Integration and Call Accounting Superior communication is at the heart of every successful hotel. MITEL CONNECTED GUESTS The class leading Hospitality Applications Suite is transforming
icharge PMS Middleware, Integration and Call Accounting Superior communication is at the heart of every successful hotel. MITEL CONNECTED GUESTS The class leading Hospitality Applications Suite is transforming
Procurement of FM Services
 Next Generation FM Services Procurement of FM Services 22nd June 2017 Presented by Mark French Procurement of FM Services Introducing Crown Commercial Service (CCS) We re one of the biggest public procurement
Next Generation FM Services Procurement of FM Services 22nd June 2017 Presented by Mark French Procurement of FM Services Introducing Crown Commercial Service (CCS) We re one of the biggest public procurement
EUROPEAN COMMISSION ENTERPRISE AND INDUSTRY DIRECTORATE-GENERAL. EudraLex The Rules Governing Medicinal Products in the European Union
 EUROPEAN COMMISSION ENTERPRISE AND INDUSTRY DIRECTORATE-GENERAL Consumer goods Pharmaceuticals Brussels, 08 April 2008 EudraLex The Rules Governing Medicinal Products in the European Union Volume 4 EU
EUROPEAN COMMISSION ENTERPRISE AND INDUSTRY DIRECTORATE-GENERAL Consumer goods Pharmaceuticals Brussels, 08 April 2008 EudraLex The Rules Governing Medicinal Products in the European Union Volume 4 EU
Developing an Effective Key Control Program. Laura Quick, Omaha Steaks Cita Doyle, InstaKey Security Systems
 Developing an Effective Key Control Program Laura Quick, Omaha Steaks Cita Doyle, InstaKey Security Systems Developing an Effective Key Control Program Today, Restauranteur's are challenged by constantly
Developing an Effective Key Control Program Laura Quick, Omaha Steaks Cita Doyle, InstaKey Security Systems Developing an Effective Key Control Program Today, Restauranteur's are challenged by constantly
Decision Maker s Guide
 Decision Maker s Guide Evaluation Checklist for ITSM Solutions High Level Requirements Ability to support a 24x7 service desk operation Ability to provide workflow capabilities for efficient incident,
Decision Maker s Guide Evaluation Checklist for ITSM Solutions High Level Requirements Ability to support a 24x7 service desk operation Ability to provide workflow capabilities for efficient incident,
CONTINUITY OF OPERATIONS (COOP) WORKSHEETS
 CONTINUITY OF OPERATIONS (COOP) WORKSHEETS Martin O Malley, Governor Richard Muth, Director June 2009 Version 2.0 COOP WORKSHEETS These worksheets are tools to help you gather the raw data needed to develop
CONTINUITY OF OPERATIONS (COOP) WORKSHEETS Martin O Malley, Governor Richard Muth, Director June 2009 Version 2.0 COOP WORKSHEETS These worksheets are tools to help you gather the raw data needed to develop
1. Describe the staffing levels maintained in the IT department (change titles as needed): Administrative Analyst II To be hired in August 2007/1
 Page 1 of 15 Chabot-Las Positas Community College District Reference: T500 Information System Memo Prepared by: Jeannine Methe June 30, 2007 Date: 6/28/07 Reviewed by: Instructions: This memo is designed
Page 1 of 15 Chabot-Las Positas Community College District Reference: T500 Information System Memo Prepared by: Jeannine Methe June 30, 2007 Date: 6/28/07 Reviewed by: Instructions: This memo is designed
CHRIST CHURCH YOUTH AND COMMUNITY CENTRE LONE WORKING POLICY & GUIDANCE
 CHRIST CHURCH YOUTH AND COMMUNITY CENTRE LONE WORKING CONTENTS 1. Introduction 2. Identifying Lone Workers 3. Risk Assessment 3.1 Identifying those at risk 3.2 Assessing the risks LONE WORKING POLICY &
CHRIST CHURCH YOUTH AND COMMUNITY CENTRE LONE WORKING CONTENTS 1. Introduction 2. Identifying Lone Workers 3. Risk Assessment 3.1 Identifying those at risk 3.2 Assessing the risks LONE WORKING POLICY &
Availability = Uptime/ Total Operating Time
 1.1.4.11 TPRP Threshold for Performance Restoration Period (TPRP) is the period of time during which the contractor shall restore the operational capability PRS# 1 The contractor shall provide restoration
1.1.4.11 TPRP Threshold for Performance Restoration Period (TPRP) is the period of time during which the contractor shall restore the operational capability PRS# 1 The contractor shall provide restoration
AGILENT SPECIFICATIONS INFORMATICS SOFTWARE SUPPORT AND SERVICES SILVER-LEVEL
 AGILENT SPECIFICATIONS INFORMATICS SOFTWARE SUPPORT AND SERVICES SILVER-LEVEL The following terms set forth the specifications under which Agilent will provide support and services to customers who are
AGILENT SPECIFICATIONS INFORMATICS SOFTWARE SUPPORT AND SERVICES SILVER-LEVEL The following terms set forth the specifications under which Agilent will provide support and services to customers who are
IT EXAMS TOP 5 CITATIONS. Top 5 citations LOUISIANA BANKERS ASSOCIATION TECHNOLOGY CONFERENCE Policy and Risk Assessment 2.
 IT EXAMS LOUISIANA BANKERS ASSOCIATION TECHNOLOGY CONFERENCE 2015 @TrainaCPA TOP 5 CITATIONS Top 5 citations 1. Policy and Risk Assessment 2. ACH/CATO 3. Disaster planning 4. Audit 5. Oversight 1. POLICY
IT EXAMS LOUISIANA BANKERS ASSOCIATION TECHNOLOGY CONFERENCE 2015 @TrainaCPA TOP 5 CITATIONS Top 5 citations 1. Policy and Risk Assessment 2. ACH/CATO 3. Disaster planning 4. Audit 5. Oversight 1. POLICY
Comparing Cost of Ownership: Symantec Managed PKI Service vs. On- Premise Software
 WHITE PAPER: COMPARING TCO: SYMANTEC MANAGED PKI SERVICE........ VS..... ON-PREMISE........... SOFTWARE................. Comparing Cost of Ownership: Symantec Managed PKI Service vs. On- Premise Software
WHITE PAPER: COMPARING TCO: SYMANTEC MANAGED PKI SERVICE........ VS..... ON-PREMISE........... SOFTWARE................. Comparing Cost of Ownership: Symantec Managed PKI Service vs. On- Premise Software
PREDICTIVE INTELLIGENCE SECURITY, PRIVACY, AND ARCHITECTURE
 PREDICTIVE INTELLIGENCE SECURITY, PRIVACY, AND ARCHITECTURE Last Updated: May 6, 2016 Salesforce s Corporate Trust Commitment Salesforce is committed to achieving and maintaining the trust of our customers.
PREDICTIVE INTELLIGENCE SECURITY, PRIVACY, AND ARCHITECTURE Last Updated: May 6, 2016 Salesforce s Corporate Trust Commitment Salesforce is committed to achieving and maintaining the trust of our customers.
LEVERAGING YOUR VENDORS TO SUPPORT DATA INTEGRITY:
 LEVERAGING YOUR VENDORS TO SUPPORT DATA INTEGRITY: QUESTIONS TO ASK AND RESPONSIBILITIES TO DOCUMENT Heather Longden Boston Chapter Educational Meeting April 2018 About Waters Lab Informatics Separations
LEVERAGING YOUR VENDORS TO SUPPORT DATA INTEGRITY: QUESTIONS TO ASK AND RESPONSIBILITIES TO DOCUMENT Heather Longden Boston Chapter Educational Meeting April 2018 About Waters Lab Informatics Separations
Administering Microsoft System Center Configuration Manager and Cloud Services Integration (beta) (703)
 Administering Microsoft System Center Configuration Manager and Cloud Services Integration (beta) (703) Configure and Maintain a Configuration Manager Management Infrastructure Configure the management
Administering Microsoft System Center Configuration Manager and Cloud Services Integration (beta) (703) Configure and Maintain a Configuration Manager Management Infrastructure Configure the management
SKF Digitalization. Building a Digital Platform for an Enterprise Company. Jens Greiner Global Manager IoT Development
 SKF Digitalization Building a Digital Platform for an Enterprise Company Jens Greiner Global Manager IoT Development 2017-05-18 2016, Amazon Web Services, Inc. or its Affiliates. All rights reserved. SKF
SKF Digitalization Building a Digital Platform for an Enterprise Company Jens Greiner Global Manager IoT Development 2017-05-18 2016, Amazon Web Services, Inc. or its Affiliates. All rights reserved. SKF
FY2016/17 Approved Budget. SECTION 17 Information Technology
 17 SECTION 17 Information Technology 189 Information Technology The Department of Information Technology (IT) is committed to ensuring IT investments and strategic business technologies deliver the highest
17 SECTION 17 Information Technology 189 Information Technology The Department of Information Technology (IT) is committed to ensuring IT investments and strategic business technologies deliver the highest
Guide: On-premise vs hosted VoIP telephone systems
 Guide: On-premise vs hosted VoIP telephone systems What s the difference? Introduction In essence, there is no one-size fits all approach to telecoms as the reality is that it is more a case of what s
Guide: On-premise vs hosted VoIP telephone systems What s the difference? Introduction In essence, there is no one-size fits all approach to telecoms as the reality is that it is more a case of what s
Building Security Worldwide. Enterprise Security Management System
 Building Security Worldwide Enterprise Security Management System Dynamic Mapping Access Control Enterprise Security Management System Bringing together different aspects of security management can be
Building Security Worldwide Enterprise Security Management System Dynamic Mapping Access Control Enterprise Security Management System Bringing together different aspects of security management can be
HOW SOFTWARE-AS-A-SERVICE (SAAS) LOWERS THE TOTAL COST OF OWNERSHIP (TCO) FOR PHYSICAL SECURITY SYSTEMS
 HOW SOFTWARE-AS-A-SERVICE (SAAS) LOWERS THE TOTAL COST OF OWNERSHIP (TCO) FOR PHYSICAL SECURITY SYSTEMS www.brivo.com Table of Contents EXECUTIVE SUMMARY... 3 INTRODUCTION... 4 HOW SAAS IS A GAME CHANGER...
HOW SOFTWARE-AS-A-SERVICE (SAAS) LOWERS THE TOTAL COST OF OWNERSHIP (TCO) FOR PHYSICAL SECURITY SYSTEMS www.brivo.com Table of Contents EXECUTIVE SUMMARY... 3 INTRODUCTION... 4 HOW SAAS IS A GAME CHANGER...
Administering System Center Configuration Manager and Intune (20696C)
 Administering System Center Configuration Manager and Intune (20696C) Overview Get expert instruction and hands-on practice configuring and managing clients and devices by using Microsoft System Center
Administering System Center Configuration Manager and Intune (20696C) Overview Get expert instruction and hands-on practice configuring and managing clients and devices by using Microsoft System Center
Welcome to the webinar NHSmail migration options
 Welcome to the webinar NHSmail migration options The webinar will begin at 10.00am Please synchronise your web and phone presence by inputting your Attendee ID into the phone Participant lines will be
Welcome to the webinar NHSmail migration options The webinar will begin at 10.00am Please synchronise your web and phone presence by inputting your Attendee ID into the phone Participant lines will be
Job Description. Salary: AOC Point ,671 29,147
 Job Description Post title: Responsible to: IT Technician IT Manager Salary: OC Point 26 29 26,671 29,147 Purpose of Job: The IT technician is responsible for the update and maintenance of all the IT infrastructure,
Job Description Post title: Responsible to: IT Technician IT Manager Salary: OC Point 26 29 26,671 29,147 Purpose of Job: The IT technician is responsible for the update and maintenance of all the IT infrastructure,
International Standards Reference
 Consult IT (Pty) Ltd International Standards Reference Pontsho C Pusoetsile Presentation Agenda 1. Overview of Standards and Guidelines 2. Benefits of Each Standard or Guideline 3. Practical considerations
Consult IT (Pty) Ltd International Standards Reference Pontsho C Pusoetsile Presentation Agenda 1. Overview of Standards and Guidelines 2. Benefits of Each Standard or Guideline 3. Practical considerations
ALWIN S System. The very modern Alwin system is based on the SOA (Service Oriented Architecture) concept and provides the following features:
 ALWIN S FP ALCEA ALWIN S eng V3 03.13 - p. 1 / 10 The complete supervision tool The Alwin system is an integrated, flexible and modular management and supervision software package, designed to meet all
ALWIN S FP ALCEA ALWIN S eng V3 03.13 - p. 1 / 10 The complete supervision tool The Alwin system is an integrated, flexible and modular management and supervision software package, designed to meet all
Integrating MDM and Cloud Services with System Center Configuration Manager
 Integrating MDM and Cloud Services with System Center Configuration Course 20703-2A 3 Days Instructor-led, Hands on Course Information This is a three-day Instructor Led Training (ILT) course that describes
Integrating MDM and Cloud Services with System Center Configuration Course 20703-2A 3 Days Instructor-led, Hands on Course Information This is a three-day Instructor Led Training (ILT) course that describes
MOVE PLANNING CHECKLIST
 MOVE PLANNG CHECKLIST PRELIMARY Finalize Lease for new location Notify present Landlord of termination date Advise staff of date and location of move Engage designer for new premises (if required) Create
MOVE PLANNG CHECKLIST PRELIMARY Finalize Lease for new location Notify present Landlord of termination date Advise staff of date and location of move Engage designer for new premises (if required) Create
Challenges for National CSIRTs in Europe in 2016: Study on CSIRT Maturity
 Challenges for National CSIRTs in Europe in 2016: FINAL VERSION 1.0 EXTERNAL DECEMBER 2016 www.enisa.europa.eu European Union Agency For Network And Information Security About ENISA The European Union
Challenges for National CSIRTs in Europe in 2016: FINAL VERSION 1.0 EXTERNAL DECEMBER 2016 www.enisa.europa.eu European Union Agency For Network And Information Security About ENISA The European Union
Microsoft 365 Business Services
 The Partner Financial Opportunity March 2018 Copyright information 2018 Microsoft Corporation. All rights reserved. This document is provided "as-is." Information and views expressed in this document,
The Partner Financial Opportunity March 2018 Copyright information 2018 Microsoft Corporation. All rights reserved. This document is provided "as-is." Information and views expressed in this document,
Infor CloudSuite Flexible and proven solutions for your industry
 TM Flexible and proven solutions for your industry 1 Unlock your potential with There s no question that technology is an essential part of running your business. You wouldn t be able to function without
TM Flexible and proven solutions for your industry 1 Unlock your potential with There s no question that technology is an essential part of running your business. You wouldn t be able to function without
Market consultation. PSIM Physical Security Information Management. N.V. Nederlandse Gasunie. Gasunie referencenumber : EA-2016.
 Market consultation PSIM Physical Security Information Management N.V. Nederlandse Gasunie Gasunie referencenumber : EA-2016.25/AW Date: 2016-12-12 Version: 1.1 Some additional questions relating to Video
Market consultation PSIM Physical Security Information Management N.V. Nederlandse Gasunie Gasunie referencenumber : EA-2016.25/AW Date: 2016-12-12 Version: 1.1 Some additional questions relating to Video
FRAMEWORK OVERVIEW. The framework will enable trusts to procure cabinet locking devices either by direct award or through mini competition.
 FRAMEWORK OVERVIEW HealthTrust Europe (HTE) s Cabinet Locking Devices framework provides high security access and key management solutions for medicine cabinets and restricted access areas. The framework
FRAMEWORK OVERVIEW HealthTrust Europe (HTE) s Cabinet Locking Devices framework provides high security access and key management solutions for medicine cabinets and restricted access areas. The framework
UNC School of Medicine IT. Service Level Agreement
 UNC School of Medicine IT Service Level Agreement 1 Table of Contents Purpose... 2 Scope of Agreement... 2 Services Provided under this Agreement... 2 Service Catalog... 2 Changes to Service Level Agreement...
UNC School of Medicine IT Service Level Agreement 1 Table of Contents Purpose... 2 Scope of Agreement... 2 Services Provided under this Agreement... 2 Service Catalog... 2 Changes to Service Level Agreement...
SUPPLY CHAIN SECURITY PROGRAMS. Customs-Trade Partnership Against Terrorism. Partners In Protection
 Customs Brokers Limited Global Logistics SERVICES OFFERED Customs-Trade Partnership Against Terrorism U.S. Customs and Border Protection Partners In Protection Contact: training@affiliated.ca TRAINING:
Customs Brokers Limited Global Logistics SERVICES OFFERED Customs-Trade Partnership Against Terrorism U.S. Customs and Border Protection Partners In Protection Contact: training@affiliated.ca TRAINING:
Mitel 400 Hospitality Package
 Mitel 400 Hospitality Package For hotels, guest houses and care homes Customer satisfaction is of prime importance for hotels, guest houses, care homes and any business offering guest management services.
Mitel 400 Hospitality Package For hotels, guest houses and care homes Customer satisfaction is of prime importance for hotels, guest houses, care homes and any business offering guest management services.
An integrated sustainability platform
 An integrated sustainability platform Solving business mission critical problems Monitising the Industrial Internet of Things Buildings, Assets, People Why Saamsol See Built for scale Stakeholder collaboration
An integrated sustainability platform Solving business mission critical problems Monitising the Industrial Internet of Things Buildings, Assets, People Why Saamsol See Built for scale Stakeholder collaboration
Choosing a Managed Print Service Provider
 Choosing a Managed Print Service Provider A Managed Print Service or MPS, has become the primary vehicle that business has used to control its cost of print. This white paper is aimed at senior management
Choosing a Managed Print Service Provider A Managed Print Service or MPS, has become the primary vehicle that business has used to control its cost of print. This white paper is aimed at senior management
Traffic Systems.
 Traffic Systems www.aselsan.com.tr Traffic Management Systems Aselsan offers complete traffic management solutions in a modular manner according to specific customer needs. ASELSAN offers complete traffic
Traffic Systems www.aselsan.com.tr Traffic Management Systems Aselsan offers complete traffic management solutions in a modular manner according to specific customer needs. ASELSAN offers complete traffic
CTS Group Ltd Ahead through technology
 CTS Group Ltd Ahead through technology 99 Milton Park, Abingdon, Oxfordshire, OX14 4RY Tel: 01235 432000 Fax: 0845 1665 322 E-Mail:karen.ogden@cts-group.co.uk Reg. No: 3068108 United Kingdom Privacy Notice
CTS Group Ltd Ahead through technology 99 Milton Park, Abingdon, Oxfordshire, OX14 4RY Tel: 01235 432000 Fax: 0845 1665 322 E-Mail:karen.ogden@cts-group.co.uk Reg. No: 3068108 United Kingdom Privacy Notice
nddprint MPS White Paper - Print Management Service
 White Paper - Print Management Service nddprint MPS nddprint MPS is the most complete cloud-based architecture solution, developed to meet the needs of print outsourcing operations. The service goal is
White Paper - Print Management Service nddprint MPS nddprint MPS is the most complete cloud-based architecture solution, developed to meet the needs of print outsourcing operations. The service goal is
SECTION 18. INFORMATION TECHNOLOGY AND COMMUNICATION SYSTEMS RECORDS
 SECTION 18. INFORMATION TECHNOLOGY AND COMMUNICATION SYSTEMS RECORDS s relating to the County s information technology and communications systems operations. General Instructions The minimum retention
SECTION 18. INFORMATION TECHNOLOGY AND COMMUNICATION SYSTEMS RECORDS s relating to the County s information technology and communications systems operations. General Instructions The minimum retention
A MANAGEMENT MODEL FOR BUILDING A COMPUTER SECURITY INCIDENT RESPONSE CAPABILITY
 78 SOUTH AFRICAN INSTITUTE OF ELECTRICAL ENGINEERS Vol.107 (2) June 2016 A MANAGEMENT MODEL FOR BUILDING A COMPUTER SECURITY INCIDENT RESPONSE CAPABILITY Roderick D. Mooi and Reinhardt A. Botha Meraka
78 SOUTH AFRICAN INSTITUTE OF ELECTRICAL ENGINEERS Vol.107 (2) June 2016 A MANAGEMENT MODEL FOR BUILDING A COMPUTER SECURITY INCIDENT RESPONSE CAPABILITY Roderick D. Mooi and Reinhardt A. Botha Meraka
Avigilon Open Security Platforms
 Avigilon Open Security Platforms Our open platform promotes easy integration of trusted security solutions Avigilon solutions are built on an open platform for easy integration with third-party software
Avigilon Open Security Platforms Our open platform promotes easy integration of trusted security solutions Avigilon solutions are built on an open platform for easy integration with third-party software
Purchasing Office Policy & Procedure Manual
 Purchasing Office Policy & Procedure Manual Page 1 A. GENERAL INFORMATION 1. The purchasing policies and procedures shown herein are required by the State of Wisconsin Department of Administration, and
Purchasing Office Policy & Procedure Manual Page 1 A. GENERAL INFORMATION 1. The purchasing policies and procedures shown herein are required by the State of Wisconsin Department of Administration, and
COMPANY PROFILE.
 COMPANY PROFILE www.itgility.co.za Contact anyone of our consultants: Vision Minesh +27 (0) 83 441 0745 Andre +27 (0) 83 357 5729 Francois +27 (0) 82 579 1705 Jacques +27 (0) 83 357 5659 ITgility is an
COMPANY PROFILE www.itgility.co.za Contact anyone of our consultants: Vision Minesh +27 (0) 83 441 0745 Andre +27 (0) 83 357 5729 Francois +27 (0) 82 579 1705 Jacques +27 (0) 83 357 5659 ITgility is an
1. Describe the staffing levels maintained in the IT department (change titles as needed):
 Page 1 of 16 Chabot-Las Positas Community College District Reference: T500 Information System ICQ Prepared by: Jeannine Methe July 18, 2008 Date: 7/18/08 Reviewed by: XG 8/30/07 Updated by client for 06-07.
Page 1 of 16 Chabot-Las Positas Community College District Reference: T500 Information System ICQ Prepared by: Jeannine Methe July 18, 2008 Date: 7/18/08 Reviewed by: XG 8/30/07 Updated by client for 06-07.
Millennium ULTRA. Software Guide
 Millennium ULTRA Software Guide Millennium Ultra is our flagship state of the art web browser-capable access control platform designed with a highly scalable architecture capable of supporting one door,
Millennium ULTRA Software Guide Millennium Ultra is our flagship state of the art web browser-capable access control platform designed with a highly scalable architecture capable of supporting one door,
Access Control Intruder Detection Security Management
 Access Control Intruder Detection Security Management Customer Brochure 17 Inner Range began designing and manufacturing integrated Security and Access Control systems in 1988. Today there are more than
Access Control Intruder Detection Security Management Customer Brochure 17 Inner Range began designing and manufacturing integrated Security and Access Control systems in 1988. Today there are more than
WHITE PAPER. Applying Remote Monitoring Solutions to improve Compliance and Efficiency in the Mining Industry
 WHITE PAPER Applying Remote Monitoring Solutions to improve Compliance and Efficiency in the Mining Industry How new technologies can dramatically improve your ability to manage while significantly lowering
WHITE PAPER Applying Remote Monitoring Solutions to improve Compliance and Efficiency in the Mining Industry How new technologies can dramatically improve your ability to manage while significantly lowering
NOTICE TO VENDORS PAY STATION DEMONSTRATION PROJECT
 PORT OF SAN FRANCISCO PIER 1 SAN FRANCISCO, CA 94111 NOTICE TO VENDORS PAY STATION DEMONSTRATION PROJECT July 28, 2006 The Port of San Francisco is inviting distributors and vendors of multi-space pay
PORT OF SAN FRANCISCO PIER 1 SAN FRANCISCO, CA 94111 NOTICE TO VENDORS PAY STATION DEMONSTRATION PROJECT July 28, 2006 The Port of San Francisco is inviting distributors and vendors of multi-space pay
Lamproom Management 1
 Lamproom Management 1 2 Lamproom Management Schauenburg Advanced Technical Services Schauenburg s Advanced Technical Services (SATS), a division of Schauenburg Systems (Pty) Ltd, identified the need in
Lamproom Management 1 2 Lamproom Management Schauenburg Advanced Technical Services Schauenburg s Advanced Technical Services (SATS), a division of Schauenburg Systems (Pty) Ltd, identified the need in
SIMPLE FUND 360: AN AUDITORS GUIDE. Australia s leading cloud SMSF admin solution AN AUDITORS GUIDE.
 Australia s leading cloud SMSF admin solution AN AUDITORS GUIDE www.bglcorp.com Prepared by BGL Corporate Solutions Pty Ltd March 2018 CONTENTS 1.0 Overview of BGL s Web Applications 2.0 Data Sources and
Australia s leading cloud SMSF admin solution AN AUDITORS GUIDE www.bglcorp.com Prepared by BGL Corporate Solutions Pty Ltd March 2018 CONTENTS 1.0 Overview of BGL s Web Applications 2.0 Data Sources and
IT Department-as-a-Service
 Agenda!! SMB IT core functions overview!! IT Managed Services (MSP) menu!! Virtual CIO Services (vcio) menu!! ProjexTeam ebusiness platform functions!! Getting started SMB IT Core Functions and Responsibilities
Agenda!! SMB IT core functions overview!! IT Managed Services (MSP) menu!! Virtual CIO Services (vcio) menu!! ProjexTeam ebusiness platform functions!! Getting started SMB IT Core Functions and Responsibilities
Flexible Scalable Complete. Sustainable Future Maximum Investment
 SYSTEM GALAXY SOFTWARE SOLUTIONS SYSTEM GALAXY System Galaxy is a complete, enterprise-class access control and security management solution that offers unsurpassed ability to satisfy the requirements
SYSTEM GALAXY SOFTWARE SOLUTIONS SYSTEM GALAXY System Galaxy is a complete, enterprise-class access control and security management solution that offers unsurpassed ability to satisfy the requirements
STATEMENT OF WORK AND TERMS OF REFERENCE: CCPF TECHNOLOGY UPGRADE
 I. Background II. III. STATEMENT OF WORK AND TERMS OF REFERENCE: CCPF TECHNOLOGY UPGRADE Chipatala Cha Pa Foni (CCPF), or health center by phone, is a program implemented by VillageReach starting in 2011.
I. Background II. III. STATEMENT OF WORK AND TERMS OF REFERENCE: CCPF TECHNOLOGY UPGRADE Chipatala Cha Pa Foni (CCPF), or health center by phone, is a program implemented by VillageReach starting in 2011.
Flexible Scalable Complete. Sustainable Future Maximum Investment
 SYSTEM GALAXY SOFTWARE SOLUTIONS SYSTEM GALAXY System Galaxy is a complete, enterprise-class access control and security management solution that offers unsurpassed ability to satisfy the requirements
SYSTEM GALAXY SOFTWARE SOLUTIONS SYSTEM GALAXY System Galaxy is a complete, enterprise-class access control and security management solution that offers unsurpassed ability to satisfy the requirements
TRUSTED TRADER APPLICATION (C-TPAT AND ISA)
 TRUSTED TRADER APPLICATION (C-TPAT AND ISA) APPLICANT INFORMATION Company Name: Company doing business as: Company Website: Physical Address: City Point of Contact: Phone Number: State/Zip Code Title:
TRUSTED TRADER APPLICATION (C-TPAT AND ISA) APPLICANT INFORMATION Company Name: Company doing business as: Company Website: Physical Address: City Point of Contact: Phone Number: State/Zip Code Title:
RELIABLEIT. How to Choose a Managed Services Provider. Finding Peace of Mind
 IP PATHWAYS RELIABLEIT managed services TM How to Choose a Managed Services Provider Finding Peace of Mind If you re outsourcing your IT services, you need to find a Managed Services Provider you can trust.
IP PATHWAYS RELIABLEIT managed services TM How to Choose a Managed Services Provider Finding Peace of Mind If you re outsourcing your IT services, you need to find a Managed Services Provider you can trust.
Believe in a higher level of IT Security SECUDE Business White Paper. How to Improve Business Results through Secure Single Sign-on to SAP
 Believe in a higher level of IT Security SECUDE Business White Paper How to Improve Business Results through Secure Single Sign-on to SAP Executive Summary CIOs and IT managers face tremendous demands
Believe in a higher level of IT Security SECUDE Business White Paper How to Improve Business Results through Secure Single Sign-on to SAP Executive Summary CIOs and IT managers face tremendous demands
The purpose of the fit-out is to equip the facility as required to enable occupation by the users.
 THE UNIVERSITY of EDINBURGH Estates & Buildings ESTATE DEVELOPMENT ISSUE/REVISION L 1 LAST MODIFIED 02 March 2011 DATE PRINTED RIBA stage L 1 MANAGE UNIVERSITY FIT-OUT 1. DEFINITION The issue of the Certificate
THE UNIVERSITY of EDINBURGH Estates & Buildings ESTATE DEVELOPMENT ISSUE/REVISION L 1 LAST MODIFIED 02 March 2011 DATE PRINTED RIBA stage L 1 MANAGE UNIVERSITY FIT-OUT 1. DEFINITION The issue of the Certificate
ABSS Solutions, Inc. Upper Marlboro, MD 20772
 ABSS Solutions, Inc. Upper Marlboro, MD 20772 1. 1 o State of Maryland o District of Columbia o Washington Metropolitan Area Transit Authority o Prince George s County o Montgomery County o Metropolitan
ABSS Solutions, Inc. Upper Marlboro, MD 20772 1. 1 o State of Maryland o District of Columbia o Washington Metropolitan Area Transit Authority o Prince George s County o Montgomery County o Metropolitan
MEDeRx Feature Comparison
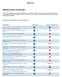 MEDeRx Feature Comparison A client recently asked us to provide a MEDeRx feature comparison to help with their selection of a physician dispensing system. After compiling the information, we felt that
MEDeRx Feature Comparison A client recently asked us to provide a MEDeRx feature comparison to help with their selection of a physician dispensing system. After compiling the information, we felt that
IBM Data Security Services for activity compliance monitoring and reporting log analysis management
 Improving your compliance posture and reducing risk through log analysis management IBM Data Security Services for activity compliance monitoring and reporting log analysis management Highlights Provide
Improving your compliance posture and reducing risk through log analysis management IBM Data Security Services for activity compliance monitoring and reporting log analysis management Highlights Provide
External Supplier Control Obligations. Information Security
 External Supplier Control Obligations Information Security Version 8.0 March 2018 Control Area / Title Control Description Why this is important 1. Roles and Responsibilities The Supplier must define and
External Supplier Control Obligations Information Security Version 8.0 March 2018 Control Area / Title Control Description Why this is important 1. Roles and Responsibilities The Supplier must define and
Migrate with Altiris.
 Migrate with Altiris. ARE YOU PREPARED? Migrating to a new operating system may seem like a daunting task. You want to take advantage of the improved security and reliability of Windows Vista, but how
Migrate with Altiris. ARE YOU PREPARED? Migrating to a new operating system may seem like a daunting task. You want to take advantage of the improved security and reliability of Windows Vista, but how
Fast, Easy to use and On-demand A Content Platform from the 21st Century
 OpenIMS Open Information Management Server Fast, Easy to use and On-demand A Content Platform from the 21st Century Business Process Management Server Whitepaper Open Information Management Server www.openims.com
OpenIMS Open Information Management Server Fast, Easy to use and On-demand A Content Platform from the 21st Century Business Process Management Server Whitepaper Open Information Management Server www.openims.com
