Real Time Enterprise
|
|
|
- Darrell Wilkerson
- 6 years ago
- Views:
Transcription
1 Association for Enterprise Integration Enterprise Integration Expo 2003 eptember 24, 2003 Collaborative Identity Management Real Time Enterprise aundra Throneberry, CIO trategy, Technology & tandards EAB 8/6/03 1
2 Topics Business Drivers and Information ecurity tandards Applied Information ecurity trategy and the Real Time Enterprise EAB 8/6/03 2
3 Information ecurity Business Drivers Business Lockheed Martin s name signifies competence, trust, and excellence. Protect information (internal and external) from abuse or loss providing a confidence to customers and partners. Re-use of previous investments and to ensure new investments prepare for the competitive future. ecurity levels applied according to business needs. Legal/Regulatory Compliance with all applicable regulations, laws, contracts, policies, and mandatory standards Insurance premiums minimized, limited liability to errors, fraud, and malfunction User Information entitled to by the user should be easily found Information should be accurate to a pre-determined range Educated and trained on security issues Easy to use interfaces with neutral interaction LM Intranet Internal Focus Access to Employees and ponsored Users Only Centralized Applications and Data in Fortified IT Bunkers Prevent Losses Minimal Confidentiality Breaches IT Control Administrators decide on access Real Time Enterprise External Focus Access to Customers, Partners, uppliers, Other Prospects Distributed Applications and Data across business units and networks Generate Revenue ecurity is to be an enabler for business Business Control Business units determine levels to grant access EAB 8/6/03 3
4 Business Risk & ecurity Business Attributes User Management Operational Risk Management Legal/ Regulatory Technical trategy Business trategy Accessible Automated Available Access Control Admissible Architecture Name Accurate Change Managed Detectable Accountable Compliant COT Business Enabled Consistent Controlled Error Free Assurable Enforceable Extendible Competent Current Cost Effective Inter Operable Auditable Insurable Flexible Confident Duty egregated Efficient Productive Authenticated Liability trategic Credible Educate & Aware Maintainable Recoverable Authorized Resolvable Legacy Governable Informed Measured Flexibly ecure Time Bound Migratable Custody Motivated upportable Identified Multi ourced Investment ReUse Protected Possession calable Reputable Reliable Integrity tandard upported Non Repudiation Upgradeable Timely Trustworthy Traceable Usable Developing Model to be applied for Risk Assessment and Analysis, Reporting, and Management Framework EAB 8/6/03 4
5 Defense in Depth - IO tandard Policy Training Awareness Audit Compliance Business Continuity Classification And Control Physical Protection Hardware ecurity Operating ystem Layer Application Layer Operations And upport Assets Fortified Layered Protection of Assets Common tandard Framework for Effective ecurity Management, Measurement, and Practice for Industry, Government, and Commerce Gaps Identity and Access Management: Implementation plans for identification into applications and automated provisioning of privileges to allow for role(s) based access Versioning: Client and server versioning to deliver foundation security elements at the infrastructure level. Maintain a similar user experience enhanced with feature upgrades Data Classification: tandardization of data classification elements externally to include application logic processing standards for access and protection EAB 8/6/03 5
6 Integrated Model Applied to the Real Time Enterprise, focusing on external identity and access requirements Public/ Private Key Identity and Access Management extensible Markup Language (XML) Users Roles Permissions Real Time Enterprises EAB 8/6/03 6
7 Public Key Infrastructure Enables a business to ensure that levels and forms of trust that exist in the physical world are implemented in the digital world Authentication Data Confidentiality Fabrication Who am I dealing with? Message Authentication & Integrity Modification Has my communication been altered? Interception Are my communications private? Non-Repudiation? Claims Not ent/not Received Who sent/received it and when? EAB 8/6/03 7
8 Public Key Infrastructure Roadmap Authentication (Who am I dealing with?) Web erver L Certificates Router Certificates Client Certificates VPN Certificates Certificates on Tokens Certificates on martcards Data Confidentiality (Are my communications private?) L Encryption IPec Protocol Encryption Message Authentication/Integrity (Has my communication been altered) PGP Certificates M Exchange Certificates ecure/mime Non-Repudiation (Who sent/received it, and when) PGP Certificates M Exchange Certificates Transaction Phased approach to implementation Implemented Planned Planned w/dependencies Major Milestones Certificate erver in UK, CA & Intl domains External CA for collaboration auth session cert Integrated with Enterprise Active Directory Key archival encryption certificates Certification with the Federal Bridge CA Certificate Authentication for LM Apps Enterprise wide use of Encrypting Files EAB 8/6/03 8
9 Identity Access Management External User (non-employee) Lockheed Martin Provi sion- ing ystem (ITODv1) Microsoft Meta- directory ervices (ITODv1) ITOD - Information Technology Operational Directive Firewall External Directory ervices External Authentication ervices ( iteminder, PKI) Data Application ervices ervices ii ii Data Application ervices ervices i i High Levels of Lockheed Martin External Web erver Complexity EAB 8/6/03 9
10 Real Time Enterprise (RTE) Vision The IT environment will integrate the business processes of the organization in real time (Real Time Enterprise RTE) versus periodic access to functional stovepipe information Aeronautics Value Chain RTE Example Product upport ell-ide Capabilities F-16 pares E-catalog ales C-5 Portal / Decision upport ystem Collaborative Design - Follow the un (or moon?) E-business On Demand Enabled by Common Infrastructure LM Aero Programs ecurity Portal Integration ervice Provisioning Virtual Manufacturing Worldwide teaming Customer Relationship Management FM Customers Depots / Bases Logistics/upport Arms-around support Autonomic Logistics imulation-based Acquisition / Virtual Test and Evaluation Network-based imulations Tests Integrated With Multiple Customers EAB 8/6/03 10
11 3 Dimensions of Real Time Enterprise RTE Capability Envelope ecure Infrastructure Information Access Real Time Enterprise Portal Characteristics Adaptable Real time information Federated Event based Iterative Loosely coupled Knowledge Management Collaboration Content Management earch & Retrieval Configurable (and 24 x 7 re-configurable) ecure hort duration (90 to 180 day projects) EAI J2EE J2EE.NET.NET Directory ervices Evolutionary not revolutionary Identity & Node-enabled legacy systems Access Mgm t Not 1 Dimensional, but 3 Distinct Dimensions That Contribute to Enable the Real Time Enterprise Web Web ervices ervices ervice ervice Oriented Oriented Architecture Architecture Application Integration Many Capabilities Available Today with Combinations of Current Technologies & olutions EAB 8/6/03 11
12 Enabling the Extranet Architecture (RTE Interface) Intrusion Detection Firewall Upgrade Vulnerability cans Public Key EAB 8/6/03 12
13 trategic Model for the Future Integrated Defense... emphasis on attributes/objects controls integrated into data and services Web Web New/Derived Technologies Web ervers Applications Tech Apps Assets Web Cost And Inefficiency ecure Accelerators Load Balancers Proxy Routers/Appliances Application Firewalls XML Extensible Markup Language Digital Rights Directory Integration Time and Performance Integrated Defense is the evolution of Defense In Depth to ervice Orientation/Real Time Enterprise, with Diverse and Adaptable Controls EAB 8/6/03 13
14 ummary Key elements to realize Real Time Enterprise externally accessed Authentication Public Key Infrastructure Identity and Access Management to Resources and ervices Brokering extensible Markup Language (XML) ecurity Risk Management, Business Value, and Return on Investment aligned to secure collaborative objectives and strategies EAB 8/6/03 14
JOURNAL OF OBJECT TECHNOLOGY
 JOURNAL OF OBJECT TECHNOLOGY Online at www.jot.fm. Published by ETH Zurich, Chair of Software Engineering JOT, 2003 Vol. 2, No. 3, May-June 2003 Don t Rip and Replace, Integrate! Mahesh H. Dodani, IBM
JOURNAL OF OBJECT TECHNOLOGY Online at www.jot.fm. Published by ETH Zurich, Chair of Software Engineering JOT, 2003 Vol. 2, No. 3, May-June 2003 Don t Rip and Replace, Integrate! Mahesh H. Dodani, IBM
Believe in a higher level of IT Security SECUDE Business White Paper. How to Improve Business Results through Secure Single Sign-on to SAP
 Believe in a higher level of IT Security SECUDE Business White Paper How to Improve Business Results through Secure Single Sign-on to SAP Executive Summary CIOs and IT managers face tremendous demands
Believe in a higher level of IT Security SECUDE Business White Paper How to Improve Business Results through Secure Single Sign-on to SAP Executive Summary CIOs and IT managers face tremendous demands
Work Product Dependency Diagram
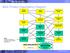 Work Product Dependency Diagram Project Definition System Context Subject Area Model Architectural Decisions Requirements Matrix Use Case Model Service Model Non Functional Requirements Component Model
Work Product Dependency Diagram Project Definition System Context Subject Area Model Architectural Decisions Requirements Matrix Use Case Model Service Model Non Functional Requirements Component Model
I-XCHANGE : TELKOM s Solution towards New Era of Inter-Intra Enterprises Integration
 I-XCHANGE : s Solution towards New Era of Inter-Intra Enterprises Integration INDRA M. UTOYO PT. Telekomunikasi Indonesia, Tbk. IIWAS2002, Bandung, 10-12 September 2002 Background: Business Trigger The
I-XCHANGE : s Solution towards New Era of Inter-Intra Enterprises Integration INDRA M. UTOYO PT. Telekomunikasi Indonesia, Tbk. IIWAS2002, Bandung, 10-12 September 2002 Background: Business Trigger The
Identity & Access Management Unlocking the Business Value
 Identity & Management Unlocking the Business Value Accenture, its logo, and High Performance Delivered are trademarks of Accenture. Unlocking the Value of Identity and Management Defining the IAM challenge
Identity & Management Unlocking the Business Value Accenture, its logo, and High Performance Delivered are trademarks of Accenture. Unlocking the Value of Identity and Management Defining the IAM challenge
Microsoft Dynamics CRM 2011 Installation and Deployment Course 80296A: 2 Days; Instructor-Led
 Microsoft Dynamics CRM 2011 Installation and Deployment Course 80296A: 2 Days; Instructor-Led About this Course This two-day instructor course covers the installation and configuration of Microsoft Dynamics
Microsoft Dynamics CRM 2011 Installation and Deployment Course 80296A: 2 Days; Instructor-Led About this Course This two-day instructor course covers the installation and configuration of Microsoft Dynamics
A Web Services Based Architecture for Improvement of the Transparency and Decision-making in Public Administration
 A Web Services Based Architecture for Improvement of the Transparency and Decision-making in Public Administration Emil Stănescu, stanescu@ici.ro National Institute for R&D in Informatics - ICI, Bucharest
A Web Services Based Architecture for Improvement of the Transparency and Decision-making in Public Administration Emil Stănescu, stanescu@ici.ro National Institute for R&D in Informatics - ICI, Bucharest
CHAPTER 3 ENTERPRISE SYSTEMS ARCHITECTURE
 CHAPTER 3 ENTERPRISE SYSTEMS ARCHITECTURE 1 Learning Objectives Examine in detail the enterprise systems modules and architecture. Understand the effects of a well-designed architecture on ERP implementation.
CHAPTER 3 ENTERPRISE SYSTEMS ARCHITECTURE 1 Learning Objectives Examine in detail the enterprise systems modules and architecture. Understand the effects of a well-designed architecture on ERP implementation.
Oracle Identity und Access Management
 Oracle Identity und Access Management Überblick Klaus Scherbach Principal Sales Consultant BU Identity Management This document is for informational purposes. It is not a commitment to deliver any material,
Oracle Identity und Access Management Überblick Klaus Scherbach Principal Sales Consultant BU Identity Management This document is for informational purposes. It is not a commitment to deliver any material,
Service Oriented Architecture
 Service Oriented Architecture Part I INTRODUCING SOA Service Oriented Architecture- Presented by Hassan.Tanabi@Gmail.com 2 Fundamental SOA 1. The term "service-oriented" has existed for some time, it has
Service Oriented Architecture Part I INTRODUCING SOA Service Oriented Architecture- Presented by Hassan.Tanabi@Gmail.com 2 Fundamental SOA 1. The term "service-oriented" has existed for some time, it has
Architecting an On Demand Enterprise with the Federal Enterprise Architecture (FEA) Andras R. Szakal Chief Architect, IBM Federal Software, S&D
 Architecting an On Demand Enterprise with the Federal Enterprise Architecture (FEA) Andras R. Szakal Chief Architect, IBM Federal Software, S&D Agenda? What is driving organizations toward an On Demand
Architecting an On Demand Enterprise with the Federal Enterprise Architecture (FEA) Andras R. Szakal Chief Architect, IBM Federal Software, S&D Agenda? What is driving organizations toward an On Demand
Aras Innovator Security. Protecting Your Product Assets
 Aras Innovator Security Protecting Your Product Assets ARAS INNOVATOR SECURITY PROTECTING YOUR PRODUCT ASSETS Today s companies face a challenging dilemma. They must be able to share information extensively
Aras Innovator Security Protecting Your Product Assets ARAS INNOVATOR SECURITY PROTECTING YOUR PRODUCT ASSETS Today s companies face a challenging dilemma. They must be able to share information extensively
ARC VIEW. Unlocking Value with Blockchain in Oil & Gas. Keywords. Summary. What Is Blockchain? JANUARY 17, By Ralph Rio and Tim Shea
 ARC VIEW JANUARY 17, 2019 Unlocking Value with Blockchain in Oil & Gas By Ralph Rio and Tim Shea Keywords Blockchain, Asset Tracking, Digital Transformation, Oil & Gas, Supply Chain Optimization, Tata
ARC VIEW JANUARY 17, 2019 Unlocking Value with Blockchain in Oil & Gas By Ralph Rio and Tim Shea Keywords Blockchain, Asset Tracking, Digital Transformation, Oil & Gas, Supply Chain Optimization, Tata
An Introduction to Oracle Identity Management. An Oracle White Paper June 2008
 An Introduction to Oracle Identity Management An Oracle White Paper June 2008 An Introduction to Oracle Identity Management INTRODUCTION Oracle Identity Management's best-in-class suite of identity management
An Introduction to Oracle Identity Management An Oracle White Paper June 2008 An Introduction to Oracle Identity Management INTRODUCTION Oracle Identity Management's best-in-class suite of identity management
Secure Extended-Enterprise Collaboration
 Secure Extended-Enterprise Collaboration Exostar Collaboration solutions for Aerospace & Defense Jean-Paul Buu-Sao, Information System Architect Email: Jean-Paul.Buu-Sao@exostar.com 17 March 2009 Microsoft
Secure Extended-Enterprise Collaboration Exostar Collaboration solutions for Aerospace & Defense Jean-Paul Buu-Sao, Information System Architect Email: Jean-Paul.Buu-Sao@exostar.com 17 March 2009 Microsoft
Service Oriented Architecture
 2 Service Oriented Architecture An Overview for the Enterprise Architect 2006 IBM Corporation Agenda IBM SOA Architect Summit Introduction SOA Reference Architecture SOA Roadmap SOA Governance Summary
2 Service Oriented Architecture An Overview for the Enterprise Architect 2006 IBM Corporation Agenda IBM SOA Architect Summit Introduction SOA Reference Architecture SOA Roadmap SOA Governance Summary
Evolving a Stovepipe Set Of Systems Into An Enterprise Architecture. Renzo Bianchi, Lockheed Martin
 Evolving a Stovepipe Set Of Systems Into An Enterprise Architecture Association For Enterprise Integration EXPO 2003 Renzo Bianchi, Lockheed Martin (renzo.bianchi@lmco.com) b Defining The Tenants For Developing
Evolving a Stovepipe Set Of Systems Into An Enterprise Architecture Association For Enterprise Integration EXPO 2003 Renzo Bianchi, Lockheed Martin (renzo.bianchi@lmco.com) b Defining The Tenants For Developing
PTC s Windchill Product Lifecycle Management (PLM) System Facilitates Part 11 / Annex 11 Compliance
 PTC s Product Lifecycle Management (PLM) ystem Facilitates Part 11 / Annex 11 Compliance A White Paper by: Diane Gleinser, r. VP olutions and ervices, UDM Life ciences Michael Prudhomme, olution Director,
PTC s Product Lifecycle Management (PLM) ystem Facilitates Part 11 / Annex 11 Compliance A White Paper by: Diane Gleinser, r. VP olutions and ervices, UDM Life ciences Michael Prudhomme, olution Director,
Digital & Technology Solutions Specialist Integrated Degree Apprenticeship (Level 7)
 Digital & Technology Solutions Specialist Integrated Degree Apprenticeship (Level 7) Role Profile A Digital & Technology Solutions Specialist maintains digital and technology strategies through technology
Digital & Technology Solutions Specialist Integrated Degree Apprenticeship (Level 7) Role Profile A Digital & Technology Solutions Specialist maintains digital and technology strategies through technology
Providing Information to Drive the Sustainment Value Chain
 Providing Information to Drive the ustainment Value Chain DoD Maintenance ymposium 2006 Dennis Wightman Vision Generating and leveraging information throughout the sustainment value chain to improve operations
Providing Information to Drive the ustainment Value Chain DoD Maintenance ymposium 2006 Dennis Wightman Vision Generating and leveraging information throughout the sustainment value chain to improve operations
Driving XML Standards Convergence and Interoperability
 Driving XML Standards Convergence and Interoperability Jackson He, Ph.D. Intel Corporation Chair of BIC XML Convergence WG December 06, 2001 Orlando, Florida Interop Summit 2001 1 Agenda Why convergence
Driving XML Standards Convergence and Interoperability Jackson He, Ph.D. Intel Corporation Chair of BIC XML Convergence WG December 06, 2001 Orlando, Florida Interop Summit 2001 1 Agenda Why convergence
Srinivasan Sundara Rajan MASTER Architect / Cloud Evangelist / Cloud Computing Journal Author
 Architecting The Cloud Srinivasan Sundara Rajan MASTER Architect / Cloud Evangelist / Cloud Computing Journal Author Cloud Definition Definition Cloud Computing is a model for enabling convenient, on-demand
Architecting The Cloud Srinivasan Sundara Rajan MASTER Architect / Cloud Evangelist / Cloud Computing Journal Author Cloud Definition Definition Cloud Computing is a model for enabling convenient, on-demand
Automating the Collaborative Enterprise
 Automating the Collaborative Enterprise Achieving strategic corporate advantage by applying model driven techniques to a web services architecture Cory Casanave, President Data Access Technologies www.enterprise-component.com
Automating the Collaborative Enterprise Achieving strategic corporate advantage by applying model driven techniques to a web services architecture Cory Casanave, President Data Access Technologies www.enterprise-component.com
Security solutions White paper. Effectively manage access to systems and information to help optimize integrity and facilitate compliance.
 Security solutions White paper Effectively manage access to systems and information to help optimize integrity and facilitate compliance. March 2007 Contents 2 Overview 3 Answer key questions related to
Security solutions White paper Effectively manage access to systems and information to help optimize integrity and facilitate compliance. March 2007 Contents 2 Overview 3 Answer key questions related to
XtraNet Technologies Private Limited
 XtraNet Technologies Private Limited CMMi Level 3 Certified ISO 9001:2015 Certified ISO/IEC 27001:2013 Certified ISO/IEC 20000-1:2011 Certified Corporate Profile January, 2019 About Us Who We Are What
XtraNet Technologies Private Limited CMMi Level 3 Certified ISO 9001:2015 Certified ISO/IEC 27001:2013 Certified ISO/IEC 20000-1:2011 Certified Corporate Profile January, 2019 About Us Who We Are What
FINACLE SERVICES: API MANAGEMENT USING CA API GATEWAY
 FINACLE SERVICES: API MANAGEMENT USING CA API GATEWAY Executive Summary Banks embarking on a digital transformation in today s connected world need to thrive, compete and evolve. To accelerate this transformation,
FINACLE SERVICES: API MANAGEMENT USING CA API GATEWAY Executive Summary Banks embarking on a digital transformation in today s connected world need to thrive, compete and evolve. To accelerate this transformation,
CTERA Enterprise File Sync and Share (EFSS) - CTERA Overview
 PRODUCT DESCRIPTIONS CTERA Enterprise File Sync and Share (EFSS) - CTERA Overview CTERA s Enterprise File Sync and Share (EFSS) lets state workers store and access their files with the convenience of the
PRODUCT DESCRIPTIONS CTERA Enterprise File Sync and Share (EFSS) - CTERA Overview CTERA s Enterprise File Sync and Share (EFSS) lets state workers store and access their files with the convenience of the
The Benefits of Running JD Edwards EnterpriseOne on the Oracle Technology Stack. A.J. Schifano Principal Product Manager Oracle
 The Benefits of Running JD Edwards EnterpriseOne on the Technology Stack A.J. Schifano Principal Product Manager The following is intended to outline our general product direction. It is intended for information
The Benefits of Running JD Edwards EnterpriseOne on the Technology Stack A.J. Schifano Principal Product Manager The following is intended to outline our general product direction. It is intended for information
Andrew Macdonald ILOG Technical Professional 2010 IBM Corporation
 The value of IBM WebSphere ILOG BRMS Understanding the value of IBM WebSphere ILOG Business Rule Management Systems (BRMS). BRMS can be used to implement and manage change in a safe and predictable way
The value of IBM WebSphere ILOG BRMS Understanding the value of IBM WebSphere ILOG Business Rule Management Systems (BRMS). BRMS can be used to implement and manage change in a safe and predictable way
IBM Content Manager OnDemand on Cloud
 IBM Terms of Use SaaS Specific Offering Terms IBM Content Manager OnDemand on Cloud The Terms of Use ( ToU ) is composed of this IBM Terms of Use - SaaS Specific Offering Terms ( SaaS Specific Offering
IBM Terms of Use SaaS Specific Offering Terms IBM Content Manager OnDemand on Cloud The Terms of Use ( ToU ) is composed of this IBM Terms of Use - SaaS Specific Offering Terms ( SaaS Specific Offering
FIRST NAME LAST NAME Issuing Agency - SECURITY CLEARANCE ADDRESS CITY STATE
 NETWORK ENGINEER : MESSAGING SPECIALTY Self-directed Information Technology professional with over twelve years progressive experience in the areas of technical support, network operations and electronic
NETWORK ENGINEER : MESSAGING SPECIALTY Self-directed Information Technology professional with over twelve years progressive experience in the areas of technical support, network operations and electronic
Oracle s Hyperion System 9 Strategic Finance
 Oracle s Hyperion System 9 Strategic Finance June 2007 Light Use... 3 Heavy Use... 3 Client Machine... 3 Server Machine... 3 Client Machine... 3 Server Machine... 3 Data Integration... 3 The Hyperion System
Oracle s Hyperion System 9 Strategic Finance June 2007 Light Use... 3 Heavy Use... 3 Client Machine... 3 Server Machine... 3 Client Machine... 3 Server Machine... 3 Data Integration... 3 The Hyperion System
IDENTITY AND ACCESS MANAGEMENT SOLUTIONS
 IDENTITY AND ACCESS MANAGEMENT SOLUTIONS Help Ensure Success in Moving from a Tactical to Strategic IAM Program Overview While identity and access management (IAM) provides many benefits to your organization
IDENTITY AND ACCESS MANAGEMENT SOLUTIONS Help Ensure Success in Moving from a Tactical to Strategic IAM Program Overview While identity and access management (IAM) provides many benefits to your organization
Why Enterprise Architecture is must for One-Stop e-government?
 Why Enterprise Architecture is must for One-Stop e-government? Ajay Ahuja 1* and Neena Ahuja 2 ABSTRACT Lack of well-defined and understandable Enterprise Architecture for the Government is a roadblock
Why Enterprise Architecture is must for One-Stop e-government? Ajay Ahuja 1* and Neena Ahuja 2 ABSTRACT Lack of well-defined and understandable Enterprise Architecture for the Government is a roadblock
"Charting the Course... MOC B Planning for and Managing Devices in the Enterprise: Enterprise Mobility Suite (EMS) and On-Premises Tools
 Description Course Summary This course teaches IT professionals how to use the Enterprise Mobility Suite to manage devices, users, and data. In addition, this course teaches students how to use other technologies,
Description Course Summary This course teaches IT professionals how to use the Enterprise Mobility Suite to manage devices, users, and data. In addition, this course teaches students how to use other technologies,
14. E-Commerce Applications and Infrastructures
 14. (Contents) E-Commerce Applications and Infrastructures Contents 14. E-Commerce Applications and Infrastructures Building E-Commerce Applications and Infrastructures Code: 166140-01+02 Course: Electronic
14. (Contents) E-Commerce Applications and Infrastructures Contents 14. E-Commerce Applications and Infrastructures Building E-Commerce Applications and Infrastructures Code: 166140-01+02 Course: Electronic
Remote Access Virtual Environment (RAVE)
 Remote Access Virtual Environment (RAVE) A VPN Knowledge Grid Joseph A. Sprute, Founder 33 Westbury Dr. Bella Vista, Arkansas 72714 479-876-6255 Office info@cyberrave.com http://www.cyberrave.com - 1 -
Remote Access Virtual Environment (RAVE) A VPN Knowledge Grid Joseph A. Sprute, Founder 33 Westbury Dr. Bella Vista, Arkansas 72714 479-876-6255 Office info@cyberrave.com http://www.cyberrave.com - 1 -
Application Architecture: Reusing Existing Applications in SOA-Based Business Processes
 Application Architecture: Reusing Existing Applications in SOA-Based Processes Braden Flowers Worldwide WebSphere Integration Solution Architect 2007 IBM Corporation SOA Architect Summit Roadmap What is
Application Architecture: Reusing Existing Applications in SOA-Based Processes Braden Flowers Worldwide WebSphere Integration Solution Architect 2007 IBM Corporation SOA Architect Summit Roadmap What is
Utilizing Oracle Standard Functionality and other Oracle tools to comply with Sarbanes- Oxley By Olga Johnson City of Detroit
 Utilizing Oracle Standard Functionality and other Oracle tools to comply with Sarbanes- Oxley By Olga Johnson City of Detroit Information on Speaker Olga Johnson Title is Business System Support Specialist
Utilizing Oracle Standard Functionality and other Oracle tools to comply with Sarbanes- Oxley By Olga Johnson City of Detroit Information on Speaker Olga Johnson Title is Business System Support Specialist
Organizing IT for Success
 Organizing IT for Success Leveraging IT As A 9 th October 2012 Nick Weinrib - Advisory Solutions Principal EMC Consulting 1 Agenda Why Organizations Are Transforming Transformational Drivers Why IT Must
Organizing IT for Success Leveraging IT As A 9 th October 2012 Nick Weinrib - Advisory Solutions Principal EMC Consulting 1 Agenda Why Organizations Are Transforming Transformational Drivers Why IT Must
EMC Documentum. Insurance. Solutions for. Solutions for Life, Property & Casualty, Health and Reinsurance
 Solutions for Solutions for Life, Property & Casualty, Health and Solutions For Back Office Support Life, Property & Casualty, Health, Legal & Claims Marketing & New Product Creation Underwriting & Sales
Solutions for Solutions for Life, Property & Casualty, Health and Solutions For Back Office Support Life, Property & Casualty, Health, Legal & Claims Marketing & New Product Creation Underwriting & Sales
INTEGRATING PING IDENTITY SOLUTIONS WITH GOOGLE IDENTITY SERVICES
 INTEGRATING PING IDENTITY SOLUTIONS WITH GOOGLE IDENTITY SERVICES How two technologies work together to add more value to your enterprise TABLE OF CONTENTS 03 04 05 06 07 08 08 08 EXECUTIVE SUMMARY INTEGRATION
INTEGRATING PING IDENTITY SOLUTIONS WITH GOOGLE IDENTITY SERVICES How two technologies work together to add more value to your enterprise TABLE OF CONTENTS 03 04 05 06 07 08 08 08 EXECUTIVE SUMMARY INTEGRATION
Recommendation: Directory Services Architecture and Future IAM Governance Model
 Recommendation: Directory Services Architecture and Future IAM Governance Model I. EXECUTIVE SUMMARY Identity and access management (IAM) is a broad administrative function that identifies individuals
Recommendation: Directory Services Architecture and Future IAM Governance Model I. EXECUTIVE SUMMARY Identity and access management (IAM) is a broad administrative function that identifies individuals
Designing a Microsoft SharePoint 2010 Infrastructure
 Course 10231B: Designing a Microsoft SharePoint 2010 Infrastructure Course Details Course Outline Module 1: Designing a Logical Architecture This module describes the function, components, and creation
Course 10231B: Designing a Microsoft SharePoint 2010 Infrastructure Course Details Course Outline Module 1: Designing a Logical Architecture This module describes the function, components, and creation
Processes and Techniques
 Methods (AM) Processes and Techniques Noting those in Architect training It is illegal to copy, share or show this document (or other document published at http://avancier.co.uk) without the written permission
Methods (AM) Processes and Techniques Noting those in Architect training It is illegal to copy, share or show this document (or other document published at http://avancier.co.uk) without the written permission
Setting the Vision p. 1 Market Predictions p. 1 Defining Vision p. 3 Traditional Business Vision vs. E-Vision p. 5 Rethink Your Revenue p.
 Preface p. xiii Setting the Vision p. 1 Market Predictions p. 1 Defining Vision p. 3 Traditional Business Vision vs. E-Vision p. 5 Rethink Your Revenue p. 6 Reengineer Your Business p. 8 Empower Your Customers
Preface p. xiii Setting the Vision p. 1 Market Predictions p. 1 Defining Vision p. 3 Traditional Business Vision vs. E-Vision p. 5 Rethink Your Revenue p. 6 Reengineer Your Business p. 8 Empower Your Customers
Enterprise Security Architecture A Top-down Approach. Contextual Security Architecture. Logical Security Architecture. Physical Security Architecture
 featu eature feature Enterprise Security A Top-down Approach Implementing security architecture is often a confusing process in enterprises. Traditionally, security architecture consists of some preventive,
featu eature feature Enterprise Security A Top-down Approach Implementing security architecture is often a confusing process in enterprises. Traditionally, security architecture consists of some preventive,
1 Building an Identity Management Business Case. 2 Agenda. 3 Business Challenges
 1 Building an Identity Management Business Case Managing the User Lifecycle Across On-Premises and Cloud-Hosted Applications Justifying investment in identity management automation. 2 Agenda Business challenges
1 Building an Identity Management Business Case Managing the User Lifecycle Across On-Premises and Cloud-Hosted Applications Justifying investment in identity management automation. 2 Agenda Business challenges
EXTENDING. THE DIGITAL THREAD WITH BLOCKCHAIN in Aerospace and Defense
 EXTENDING THE DIGITAL THREAD WITH BLOCKCHAIN in Aerospace and Defense The aerospace and defense industry has been a trailblazer in the use of digital twins to drive innovation through product design. A
EXTENDING THE DIGITAL THREAD WITH BLOCKCHAIN in Aerospace and Defense The aerospace and defense industry has been a trailblazer in the use of digital twins to drive innovation through product design. A
Architecting Web Service Applications for the Enterprise
 Architecting Web Service Applications for the Enterprise Michael Rosen Chief Enterprise Architect mike.rosen@iona.com March 5, 2002 Copyright IONA Technologies 2002 Slide 1 END 2 ANYWHERE Basic Web Service
Architecting Web Service Applications for the Enterprise Michael Rosen Chief Enterprise Architect mike.rosen@iona.com March 5, 2002 Copyright IONA Technologies 2002 Slide 1 END 2 ANYWHERE Basic Web Service
Governance, Policies / Principles Specific Topic: ESB versus Broker
 Dr. Hans-Peter Hoidn Distinguished IT Architect (Open Group certified) Enterprise IT Architectures Governance, Policies / Principles Specific Topic: ESB versus Broker Agenda of Governance (50 Minutes)
Dr. Hans-Peter Hoidn Distinguished IT Architect (Open Group certified) Enterprise IT Architectures Governance, Policies / Principles Specific Topic: ESB versus Broker Agenda of Governance (50 Minutes)
Back-End Management for E-Business Portals: A Workflow-Based Approach
 Back-End Management for E-Business Portals: A Workflow-Based Approach Giacomo Piccinelli Hewlett-Packard Labs, Bristol (UK) (giacomo_piccinelli@hp.com) Abstract In the E-Business world, a Web portal represents
Back-End Management for E-Business Portals: A Workflow-Based Approach Giacomo Piccinelli Hewlett-Packard Labs, Bristol (UK) (giacomo_piccinelli@hp.com) Abstract In the E-Business world, a Web portal represents
DHS Enterprise Architecture. The Open Group Conference Boundaryless Information Flow October 20, 2003
 DHS Enterprise Architecture The Open Group Conference Boundaryless Information Flow October 20, 2003 Our EA Challenge Support the FY05 budget formulation process Develop high-level, conceptual Homeland
DHS Enterprise Architecture The Open Group Conference Boundaryless Information Flow October 20, 2003 Our EA Challenge Support the FY05 budget formulation process Develop high-level, conceptual Homeland
JOB FAMILY DESCRIPTIONS
 JOB FAMILY: APPLICATIONS DEVELOPMENT Director, Systems and Programming Job#: 1200 Responsible for the full systems development life cycle management of projects/programs. Provides direction for technical
JOB FAMILY: APPLICATIONS DEVELOPMENT Director, Systems and Programming Job#: 1200 Responsible for the full systems development life cycle management of projects/programs. Provides direction for technical
At the Heart of Quality Assurance
 www.niit-tech.com At the Heart of Quality Assurance Driving Software Quality and Improving Efficiencies for Wealth Growing competition, global user base, and emerging technology convergence are some of
www.niit-tech.com At the Heart of Quality Assurance Driving Software Quality and Improving Efficiencies for Wealth Growing competition, global user base, and emerging technology convergence are some of
Demystifying and Applying the DHS Continuous Diagnostic Mitigation (CDM) Program for Physical Security. Mark Steffler and Ross Foard
 Demystifying and Applying the DHS Continuous Diagnostic Mitigation (CDM) Program for Physical Security Mark Steffler and Ross Foard Mark Steffler VP Government Practice for Quantum Secure, part of HID
Demystifying and Applying the DHS Continuous Diagnostic Mitigation (CDM) Program for Physical Security Mark Steffler and Ross Foard Mark Steffler VP Government Practice for Quantum Secure, part of HID
Infor CloudSuite solutions Flexible, proven solutions designed for your industry. Infor CloudSuite
 solutions Flexible, proven solutions designed for your industry 1 Unlock your full potential with Cloud technologies can offer your business a degree of agility and path to rapid growth that simply wasn
solutions Flexible, proven solutions designed for your industry 1 Unlock your full potential with Cloud technologies can offer your business a degree of agility and path to rapid growth that simply wasn
IMPLEMENTING MICROSOFT AZURE INFRASTRUCTURE SOLUTIONS
 IMPLEMENTING MICROSOFT AZURE INFRASTRUCTURE SOLUTIONS Course Duration: 5 Days About this course This course is aimed at experienced IT professionals who currently administer their on-premise infrastructure.
IMPLEMENTING MICROSOFT AZURE INFRASTRUCTURE SOLUTIONS Course Duration: 5 Days About this course This course is aimed at experienced IT professionals who currently administer their on-premise infrastructure.
More time for people!
 More time for people! Middleware Technologies and Trends Pekka Puhakka ICOPER Meeting 27.09.2000, Brussels Agenda Brief Introduction to Middleware and EAI The Possibilities and the Problems Middleware
More time for people! Middleware Technologies and Trends Pekka Puhakka ICOPER Meeting 27.09.2000, Brussels Agenda Brief Introduction to Middleware and EAI The Possibilities and the Problems Middleware
Information Architecture: Leveraging Information in an SOA Environment. David McCarty IBM Software IT Architect. IBM SOA Architect Summit
 Information Architecture: Leveraging Information in an SOA Environment David McCarty IBM Software IT Architect 2008 IBM Corporation SOA Architect Summit Roadmap What is the impact of SOA on current Enterprise
Information Architecture: Leveraging Information in an SOA Environment David McCarty IBM Software IT Architect 2008 IBM Corporation SOA Architect Summit Roadmap What is the impact of SOA on current Enterprise
DESIGNING A MICROSOFT SHAREPOINT 2010 INFRASTRUCTURE. Course: 10231B Duration: 5 Days; Instructor-led
 CENTER OF KNOWLEDGE, PATH TO SUCCESS Website: DESIGNING A MICROSOFT SHAREPOINT INFRASTRUCTURE Course: 10231B Duration: 5 Days; Instructor-led WHAT YOU WILL LEARN This 5 day ILT course teaches IT Professionals
CENTER OF KNOWLEDGE, PATH TO SUCCESS Website: DESIGNING A MICROSOFT SHAREPOINT INFRASTRUCTURE Course: 10231B Duration: 5 Days; Instructor-led WHAT YOU WILL LEARN This 5 day ILT course teaches IT Professionals
The following is intended to outline our general product direction. It is intended for information purposes only, and may not be incorporated into
 The following is intended to outline our general product direction. It is intended for information purposes only, and may not be incorporated into any contract. It is not a commitment to deliver any material,
The following is intended to outline our general product direction. It is intended for information purposes only, and may not be incorporated into any contract. It is not a commitment to deliver any material,
Accenture Software for Health and Public Service. Accenture Public Service Platform. Taking SOA from the Whiteboard to the Data Center and Beyond
 Accenture Software for Health and Public Service Accenture Public Service Platform Taking SOA from the Whiteboard to the Data Center and Beyond The Accenture Public Service Platform The Accenture Public
Accenture Software for Health and Public Service Accenture Public Service Platform Taking SOA from the Whiteboard to the Data Center and Beyond The Accenture Public Service Platform The Accenture Public
Department of Defense Fiscal Year (FY) 2013 IT President's Budget Request Defense Contract Audit Agency Overview
 Mission Area Department of Defense Overview Business System Breakout Appropriation PROCUREMENT 1.486 All Other Resources 29.357 EIEMA 29.357 OPERATIONS 27.871 FY 2013 ($M) FY 2013 ($M) FY 2013 ($M) FY12
Mission Area Department of Defense Overview Business System Breakout Appropriation PROCUREMENT 1.486 All Other Resources 29.357 EIEMA 29.357 OPERATIONS 27.871 FY 2013 ($M) FY 2013 ($M) FY 2013 ($M) FY12
Transformation. Ease of use. Number of built-in functions. XML support
 Decision Framework, J. Thompson Research Note 18 September 2002 Integration Broker Selection: Technical Criteria Selecting an integration broker is a costly, time-consuming activity; you must consider
Decision Framework, J. Thompson Research Note 18 September 2002 Integration Broker Selection: Technical Criteria Selecting an integration broker is a costly, time-consuming activity; you must consider
GOVERNANCE AES 2012 INFORMATION TECHNOLOGY GENERAL COMPUTING CONTROLS (ITGC) CATALOG. Aut. / Man. Control ID # Key SOX Control. Prev. / Det.
 GOVERNANCE 8.A.1 - Objective: Information Technology strategies, plans, personnel and budgets are consistent with AES' business and strategic requirements and goals. Objective Risk Statement(s): - IT Projects,
GOVERNANCE 8.A.1 - Objective: Information Technology strategies, plans, personnel and budgets are consistent with AES' business and strategic requirements and goals. Objective Risk Statement(s): - IT Projects,
IT. 1. Carry out trouble-shooting strategies for resolving an identified end-user IT problem.
 ACM CCECC Serving computing education communities since 1991. Information Technology Metrics IT. 1. Carry out trouble-shooting strategies for resolving an identified end-user IT problem. Lists appropriate
ACM CCECC Serving computing education communities since 1991. Information Technology Metrics IT. 1. Carry out trouble-shooting strategies for resolving an identified end-user IT problem. Lists appropriate
Think Enterprise: Delivering Culture Change. Mr. Bob Fecteau US Army INSCOM CIO
 This Briefing is UNCLASSIFIED This Briefing is UNCLASSIFIED Think Enterprise: Delivering Culture Change Presented to: Enterprise Integration Expo 23 September 2003 Mr. Bob Fecteau US Army INSCOM CIO 703-428-4613
This Briefing is UNCLASSIFIED This Briefing is UNCLASSIFIED Think Enterprise: Delivering Culture Change Presented to: Enterprise Integration Expo 23 September 2003 Mr. Bob Fecteau US Army INSCOM CIO 703-428-4613
Topics. Background Approach Status
 16 th September 2014 Topics Background Approach Status Background e-governance in India National e-governance Plan 2006 31 Mission Mode Projects Quality Assurance in e-governance Quality Assessment of
16 th September 2014 Topics Background Approach Status Background e-governance in India National e-governance Plan 2006 31 Mission Mode Projects Quality Assurance in e-governance Quality Assessment of
Lequinox platform. Empowering digital interactions and automating compliance. Platform overview. Lequinox platform - Product brochure
 Lequinox platform Empowering digital interactions and automating compliance Platform overview 1 HARNESS THE POWER OF LEQUINOX PLATFORM Start your transition from a technology-driven to a policy-driven
Lequinox platform Empowering digital interactions and automating compliance Platform overview 1 HARNESS THE POWER OF LEQUINOX PLATFORM Start your transition from a technology-driven to a policy-driven
Streamline Physical Identity and Access Management
 Streamline Physical Identity and Access Management Quantum Secure s SAFE Software Suite automates key processes and empowers IT teams to implement, streamline and manage physical access Table of Contents
Streamline Physical Identity and Access Management Quantum Secure s SAFE Software Suite automates key processes and empowers IT teams to implement, streamline and manage physical access Table of Contents
Accelerate OSS/BSS Agility Using XML and Web Services
 Accelerate OSS/BSS Agility Using XML and Web Services Pieter Knook Senior Vice President Microsoft Corporation 2002 Microsoft. All rights reserved. The Roles of a Service Provider Before Network Focus
Accelerate OSS/BSS Agility Using XML and Web Services Pieter Knook Senior Vice President Microsoft Corporation 2002 Microsoft. All rights reserved. The Roles of a Service Provider Before Network Focus
CIM Forum Charter Dated
 CIM Forum Charter Dated 2018-12-18 The information provided below is subject to change and reflects the current state of the CIM Forum charter within the DMTF. Management Problem(s) and Environment The
CIM Forum Charter Dated 2018-12-18 The information provided below is subject to change and reflects the current state of the CIM Forum charter within the DMTF. Management Problem(s) and Environment The
IT Services Management
 RL Information Consulting LLC IT Services Management INFRASTRUCTURE ARCHITECTURE PLANNING Service Brief Prepared by: Rick Leopoldi August 4, 2009 Copyright 2009 RL Information Consulting LLC. All rights
RL Information Consulting LLC IT Services Management INFRASTRUCTURE ARCHITECTURE PLANNING Service Brief Prepared by: Rick Leopoldi August 4, 2009 Copyright 2009 RL Information Consulting LLC. All rights
A Examcollection.Premium.Exam.35q
 A2030-280.Examcollection.Premium.Exam.35q Number: A2030-280 Passing Score: 800 Time Limit: 120 min File Version: 32.2 http://www.gratisexam.com/ Exam Code: A2030-280 Exam Name: IBM Cloud Computing Infrastructure
A2030-280.Examcollection.Premium.Exam.35q Number: A2030-280 Passing Score: 800 Time Limit: 120 min File Version: 32.2 http://www.gratisexam.com/ Exam Code: A2030-280 Exam Name: IBM Cloud Computing Infrastructure
Oracle s Service-Oriented Architecture Strategy
 Pierre Fricke VP and Lead Analyst, Web Application Infrastructure web-infra@dhbrown.com Business velocity refers to a company s ability to generate operational speed while heading in the right direction.
Pierre Fricke VP and Lead Analyst, Web Application Infrastructure web-infra@dhbrown.com Business velocity refers to a company s ability to generate operational speed while heading in the right direction.
20332B: Advanced Solutions of Microsoft SharePoint Server 2013
 20332B: Advanced Solutions of Microsoft SharePoint Server 2013 Course Overview This course examines how to plan, configure, and manage a Microsoft SharePoint Server 2013 environment. Special areas of focus
20332B: Advanced Solutions of Microsoft SharePoint Server 2013 Course Overview This course examines how to plan, configure, and manage a Microsoft SharePoint Server 2013 environment. Special areas of focus
PLANNING AGILE MODERNIZATION FOR SUCCESS
 PLANNING AGILE MODERNIZATION FOR SUCCESS SANJIB NAYAK Founder and CEO sanjib.nayak@xfusiontech.com (916) 990-6484 STRATEGY. INNOVATION. TRANSFORMATION. AGENDA Patterns of Legacy and Modern Systems Understanding
PLANNING AGILE MODERNIZATION FOR SUCCESS SANJIB NAYAK Founder and CEO sanjib.nayak@xfusiontech.com (916) 990-6484 STRATEGY. INNOVATION. TRANSFORMATION. AGENDA Patterns of Legacy and Modern Systems Understanding
The Open Group Exam OG0-091 TOGAF 9 Part 1 Version: 7.0 [ Total Questions: 234 ]
![The Open Group Exam OG0-091 TOGAF 9 Part 1 Version: 7.0 [ Total Questions: 234 ] The Open Group Exam OG0-091 TOGAF 9 Part 1 Version: 7.0 [ Total Questions: 234 ]](/thumbs/81/82632751.jpg) s@lm@n The Open Group Exam OG0-091 TOGAF 9 Part 1 Version: 7.0 [ Total Questions: 234 ] https://certkill.com Topic break down Topic No. of Questions Topic 1: Volume A 100 Topic 2: Volume B 134 2 https://certkill.com
s@lm@n The Open Group Exam OG0-091 TOGAF 9 Part 1 Version: 7.0 [ Total Questions: 234 ] https://certkill.com Topic break down Topic No. of Questions Topic 1: Volume A 100 Topic 2: Volume B 134 2 https://certkill.com
Software Development Asset. May 11, Chief Technical Officer Daud Santosa Department of Interior
 Software Development sset May 11, 2004 Chief Technical Officer Daud Santosa Department of Interior Reuse Maturity Framework Dimension of Maturity Initial/Chaos (1) Monitored (2) Coordinated (3) Planned
Software Development sset May 11, 2004 Chief Technical Officer Daud Santosa Department of Interior Reuse Maturity Framework Dimension of Maturity Initial/Chaos (1) Monitored (2) Coordinated (3) Planned
REQUEST FOR PROPOSAL FOR SUPPLY & MANAGEMENT OF CLOUD BASED e-learning SOLUTION CONSISTING OF SEARCH ENGINE & e-learning APPLICATION (LMS)
 CORRIGENDUM. 1 dated 21.12.2017 REQUET FOR PROPOAL FOR UPPLY & MANAGEMENT OF CLOUD BAED e-learning OLUTION CONITING OF EARCH ENGINE & e-learning APPLICATION (LM) Ref: BIICM/eL/2017-18/ 60 dated 01.12.2017
CORRIGENDUM. 1 dated 21.12.2017 REQUET FOR PROPOAL FOR UPPLY & MANAGEMENT OF CLOUD BAED e-learning OLUTION CONITING OF EARCH ENGINE & e-learning APPLICATION (LM) Ref: BIICM/eL/2017-18/ 60 dated 01.12.2017
Architecture for Integration
 Architecture for Integration Hans-Peter Hoidn 2 October 2003 Agenda Motivation I. Integration Layer in General II. EAI Environments, Cases III. EAI meets J2EE IV. Enterprise centric view V. References
Architecture for Integration Hans-Peter Hoidn 2 October 2003 Agenda Motivation I. Integration Layer in General II. EAI Environments, Cases III. EAI meets J2EE IV. Enterprise centric view V. References
Policy Administration Transformation
 Financial Services the way we do it Policy Administration Transformation Helping insurers capture dramatic improvements in time-to-market, product or price leadership and operational excellence The insurance
Financial Services the way we do it Policy Administration Transformation Helping insurers capture dramatic improvements in time-to-market, product or price leadership and operational excellence The insurance
Cloud Computing Lectures SOA
 Cloud Computing Lectures SOA 1/17/2012 Service Oriented Architecture Service Oriented Architecture Distributed system characteristics Resource sharing - sharing of hardware and software resources Openness
Cloud Computing Lectures SOA 1/17/2012 Service Oriented Architecture Service Oriented Architecture Distributed system characteristics Resource sharing - sharing of hardware and software resources Openness
Service Provision and Composition in Virtual Business Communities
 Service Provision and Composition in Virtual Business Communities Giacomo Piccinelli Extended Enterprise Laboratory HP Laboratories Bristol HPL-1999-84 16th July, 1999* E-mail: giacomo-piccinelli@hp.com
Service Provision and Composition in Virtual Business Communities Giacomo Piccinelli Extended Enterprise Laboratory HP Laboratories Bristol HPL-1999-84 16th July, 1999* E-mail: giacomo-piccinelli@hp.com
IBM WebSphere Information Integrator Content Edition Version 8.2
 Introducing content-centric federation IBM Content Edition Version 8.2 Highlights Access a broad range of unstructured information sources as if they were stored and managed in one system Unify multiple
Introducing content-centric federation IBM Content Edition Version 8.2 Highlights Access a broad range of unstructured information sources as if they were stored and managed in one system Unify multiple
SAP NetWeaver Service Select for Master Data Management. Tuesday October 26 th 2004
 SAP NetWeaver Service Select for Master Data Management Tuesday October 26 th 2004 SAP Service Select From SAP Consulting Greg Tomb Senior Vice President and General Manager SAP Consulting SAP America
SAP NetWeaver Service Select for Master Data Management Tuesday October 26 th 2004 SAP Service Select From SAP Consulting Greg Tomb Senior Vice President and General Manager SAP Consulting SAP America
CIS 8090 Intro. Setting the stage for the semester Arun Aryal & Tianjie Deng
 CIS 8090 Intro Setting the stage for the semester Arun Aryal & Tianjie Deng Cognitive Map of 8090 IS Architectures as Strategy Books: Weill, Ross & Robertson, Enterprise Architecture as Strategy & Fenix
CIS 8090 Intro Setting the stage for the semester Arun Aryal & Tianjie Deng Cognitive Map of 8090 IS Architectures as Strategy Books: Weill, Ross & Robertson, Enterprise Architecture as Strategy & Fenix
A FEDERATED ARCHITECTURE TO SUPPORT SUPPLY CHAINS
 A FEDERATED ARCHITECTURE TO SUPPORT SUPPLY CHAINS Dr. Bipin Chadha bchadha@atl.lmco.com Lockheed Martin Advanced Technology Laboratories 1 Federal St., A&E 2W, Camden, NJ 08102 Dr. Bipin Chadha is currently
A FEDERATED ARCHITECTURE TO SUPPORT SUPPLY CHAINS Dr. Bipin Chadha bchadha@atl.lmco.com Lockheed Martin Advanced Technology Laboratories 1 Federal St., A&E 2W, Camden, NJ 08102 Dr. Bipin Chadha is currently
Atlant s atwatch CAPA TM. Corrective and Preventive Action System (CAPA) Product & Services Bundle for
 Corrective and Preventive Action System (CAPA) Product & Services Bundle for Atlant s atwatch CAPA TM Atlant Systems, Inc. (781)325-8157 team@atlantsystems.com Effectively Manage CAPAs Globally According
Corrective and Preventive Action System (CAPA) Product & Services Bundle for Atlant s atwatch CAPA TM Atlant Systems, Inc. (781)325-8157 team@atlantsystems.com Effectively Manage CAPAs Globally According
Enterprise Digital Architect
 Enterprise Digital Architect Location: [Asia & Pacific] [Australia] Town/City: Preferred locations: Australia, USA, Malaysia or Manila; or any other jurisdiction (country or US state) where WVI is registered
Enterprise Digital Architect Location: [Asia & Pacific] [Australia] Town/City: Preferred locations: Australia, USA, Malaysia or Manila; or any other jurisdiction (country or US state) where WVI is registered
E-Business & E-Commerce
 Essentials of E-Business & E-Commerce Pokhara University : BBA, BBA-BI, BBA-TT & BCIS Tribhuvan University : BBA & BScCSIT Contents Unit 1 Introduction Background... 1 Introduction to E-Business... 2 Global
Essentials of E-Business & E-Commerce Pokhara University : BBA, BBA-BI, BBA-TT & BCIS Tribhuvan University : BBA & BScCSIT Contents Unit 1 Introduction Background... 1 Introduction to E-Business... 2 Global
Administering System Center Configuration Manager and Intune (20696C)
 Administering System Center Configuration Manager and Intune (20696C) Overview Get expert instruction and hands-on practice configuring and managing clients and devices by using Microsoft System Center
Administering System Center Configuration Manager and Intune (20696C) Overview Get expert instruction and hands-on practice configuring and managing clients and devices by using Microsoft System Center
SMArter Campus Mail Exchange. pad.tz.net
 SMArter Campus Mail Exchange. pad.tz.net Unlike other Locker systems, TZ Campus Locker solutions are customized to suit the work practices of the University or College mail operations including integration
SMArter Campus Mail Exchange. pad.tz.net Unlike other Locker systems, TZ Campus Locker solutions are customized to suit the work practices of the University or College mail operations including integration
At the Heart of Connected Manufacturing
 www.niit-tech.com At the Heart of Connected Manufacturing Transforming Manufacturing Operations to Drive Agility and Profitability The success of the new manufacturing network hinges on the agility of
www.niit-tech.com At the Heart of Connected Manufacturing Transforming Manufacturing Operations to Drive Agility and Profitability The success of the new manufacturing network hinges on the agility of
Is Automation Right for You? Case Study on Cost Reduction through DC Automation, Process and IT Optimization
 Is Automation Right for You? Case tudy on Cost Reduction through DC Automation, Process and IT Optimization ponsored by: Presented by: Rupert Hoecherl enior Consultant, Logistics & upply Chain anagement
Is Automation Right for You? Case tudy on Cost Reduction through DC Automation, Process and IT Optimization ponsored by: Presented by: Rupert Hoecherl enior Consultant, Logistics & upply Chain anagement
On demand operating environment solutions To support your IT objectives Transforming your business to on demand.
 On demand operating environment solutions To support your IT objectives Transforming your business to on demand. IBM s approach to service-oriented architecture Doing business in the on demand era Technological
On demand operating environment solutions To support your IT objectives Transforming your business to on demand. IBM s approach to service-oriented architecture Doing business in the on demand era Technological
1 Building an Identity Management Business Case. 2 Agenda. 3 Business Challenges
 1 Building an Identity Management Business Case Managing the User Lifecycle Across On-Premises and Cloud-Hosted Applications Justifying investment in identity management automation. 2 Agenda Business challenges
1 Building an Identity Management Business Case Managing the User Lifecycle Across On-Premises and Cloud-Hosted Applications Justifying investment in identity management automation. 2 Agenda Business challenges
5 Pitfalls and 5 Payoffs of Conducting Your Business Processes in the Cloud
 5 Pitfalls and 5 Payoffs of Conducting Your Business Processes in the Cloud Keith Swenson VP R&D, Chief Architect Fujitsu America, Inc. April 2014 Fujitsu at a Glance Headquarters: Tokyo, Japan Established:
5 Pitfalls and 5 Payoffs of Conducting Your Business Processes in the Cloud Keith Swenson VP R&D, Chief Architect Fujitsu America, Inc. April 2014 Fujitsu at a Glance Headquarters: Tokyo, Japan Established:
The-Open-Group OG ArchiMate 2 Combined Part 1 and 2 Examination.
 The-Open-Group OG0-023 ArchiMate 2 Combined Part 1 and 2 Examination https://killexams.com/pass4sure/exam-detail/og0-023 QUESTION: 50 Scenario Please read this scenario prior to answering the question
The-Open-Group OG0-023 ArchiMate 2 Combined Part 1 and 2 Examination https://killexams.com/pass4sure/exam-detail/og0-023 QUESTION: 50 Scenario Please read this scenario prior to answering the question
